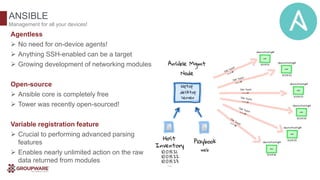
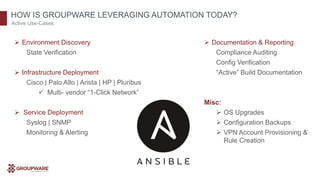
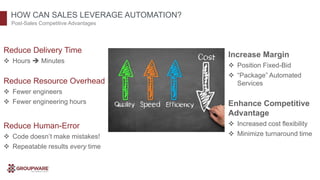
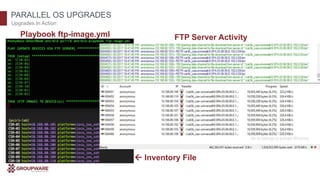
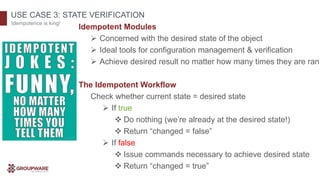
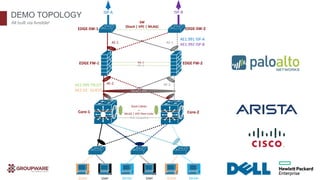
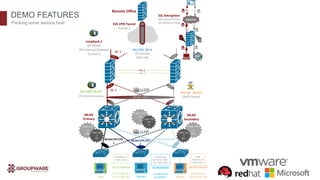
The document discusses the transformative potential of infrastructure automation, focusing on 1-click solutions for network discovery, deployment, verification, and reporting. It highlights the benefits of using automation tools like Ansible to reduce errors, improve efficiency, and enable rapid scaling in network operations. Various use cases are presented, demonstrating how automation can streamline tasks such as configuration management, OS upgrades, and dynamic reporting across multi-vendor environments.