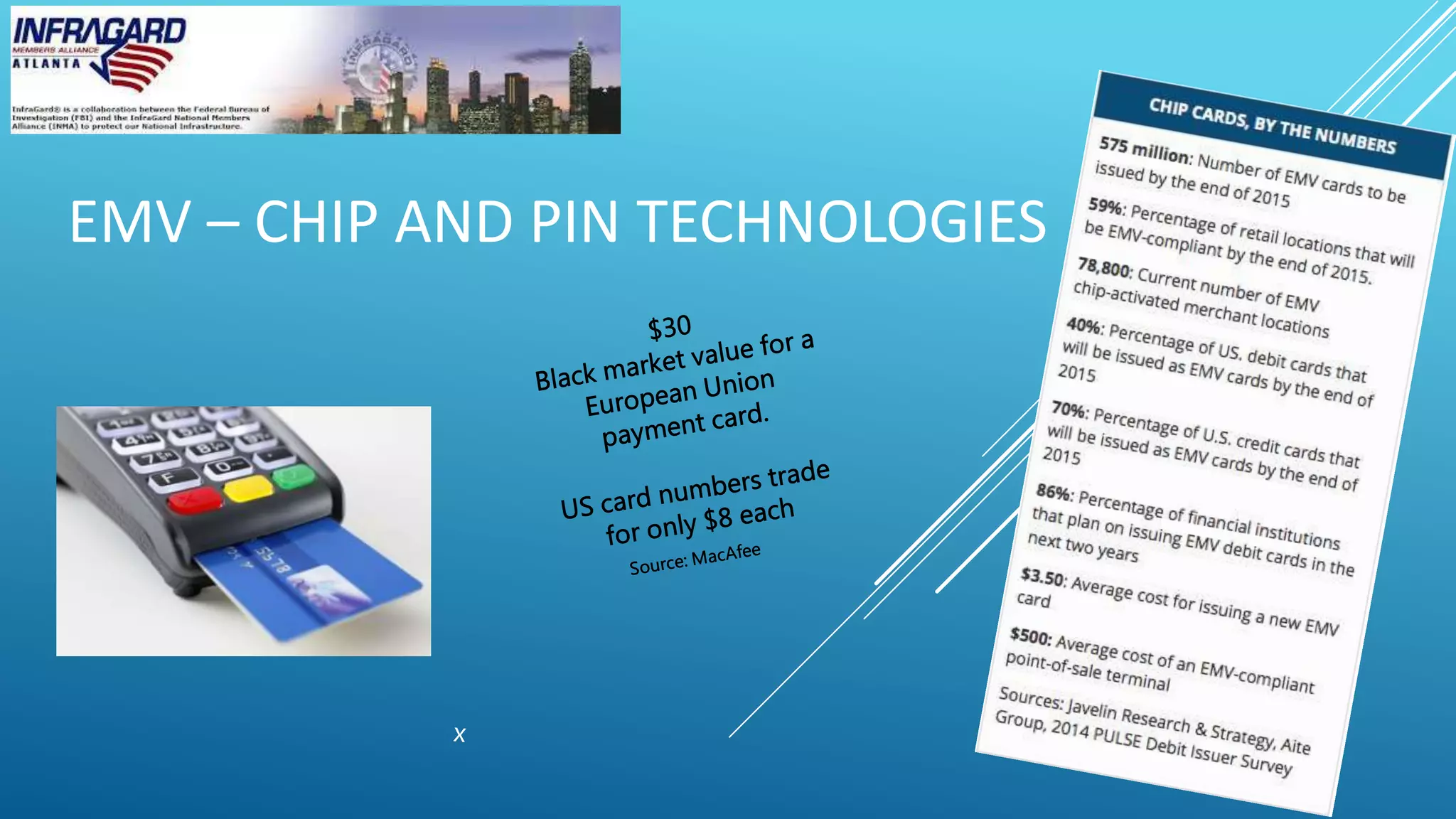
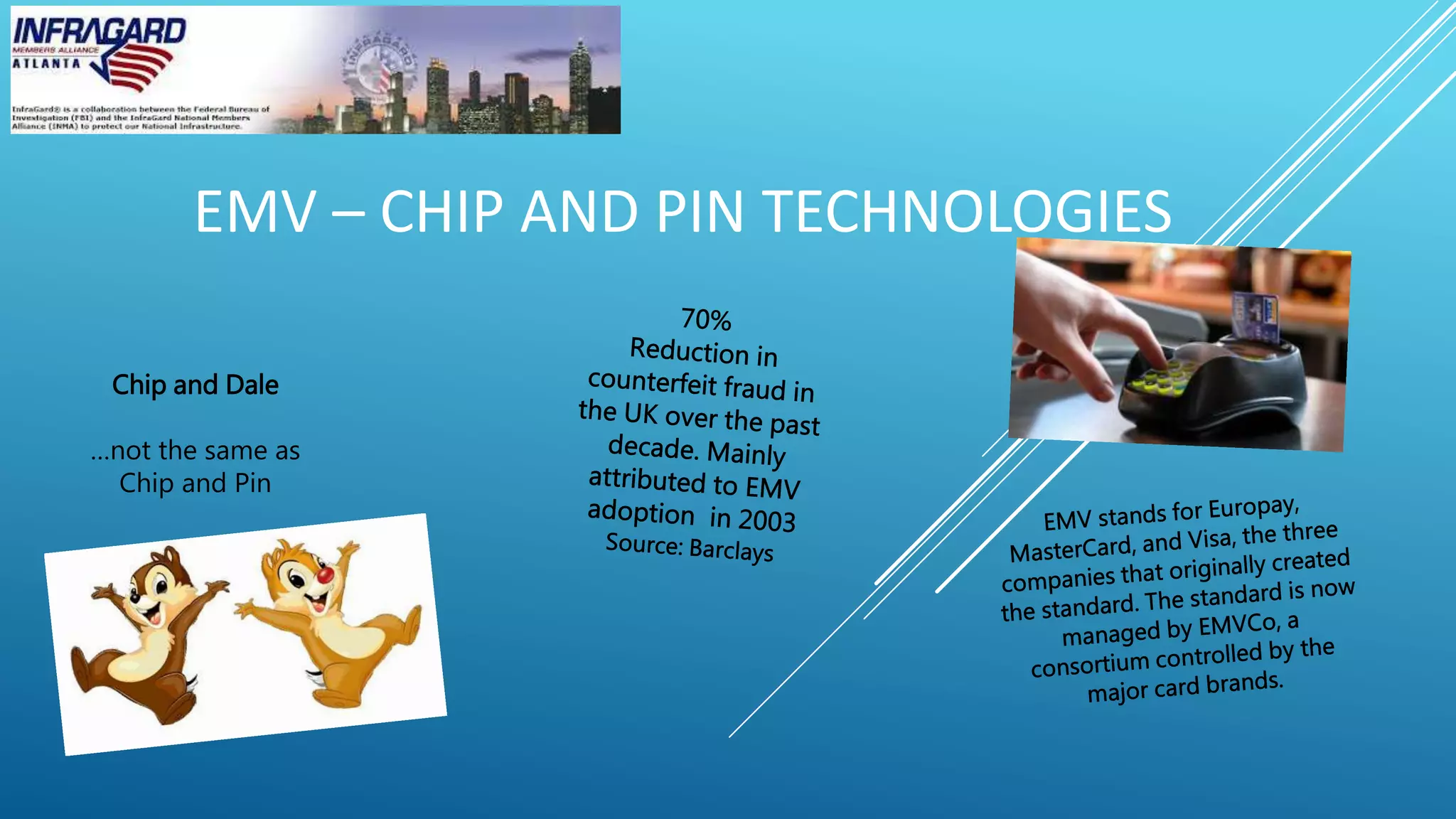
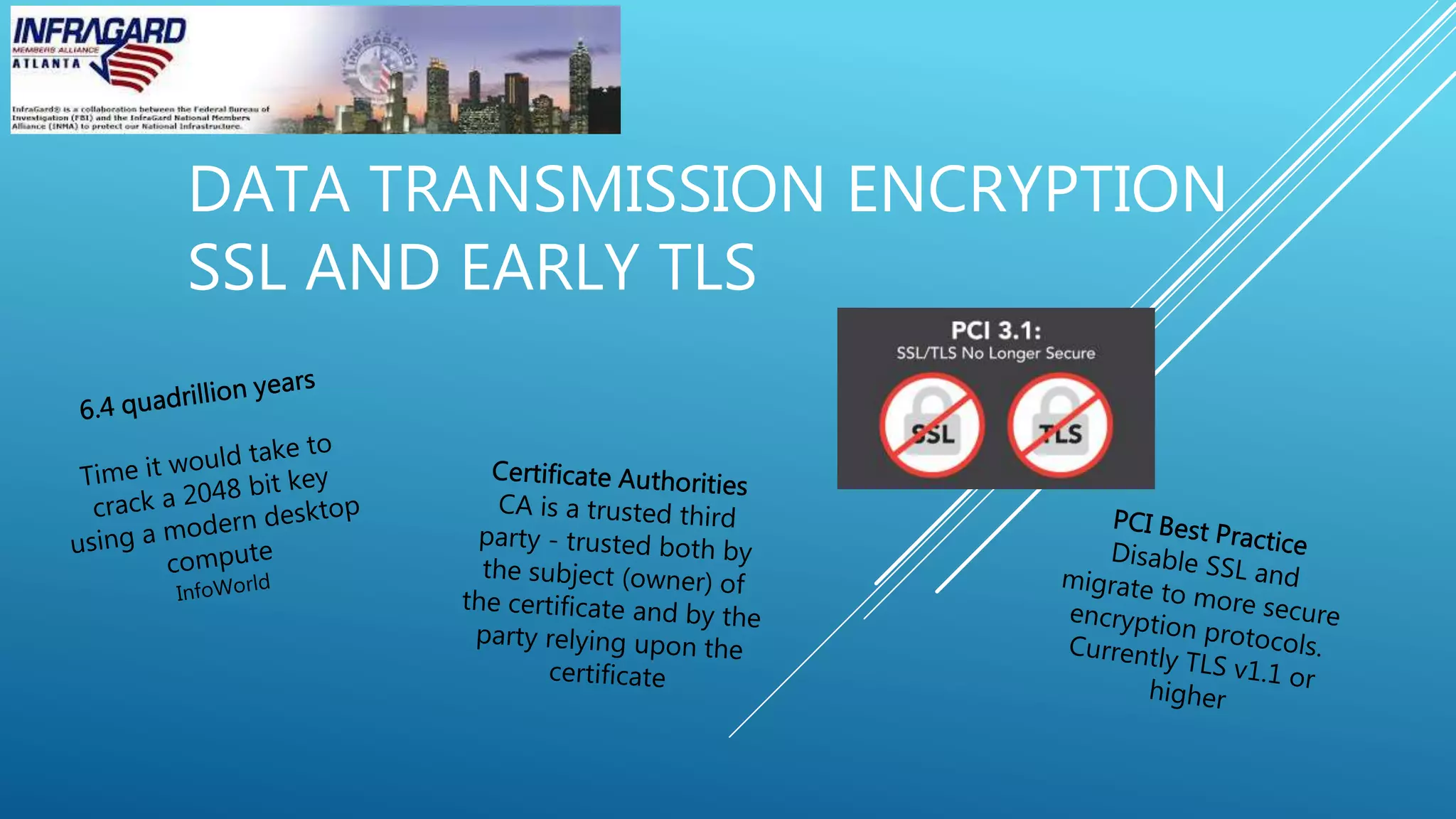
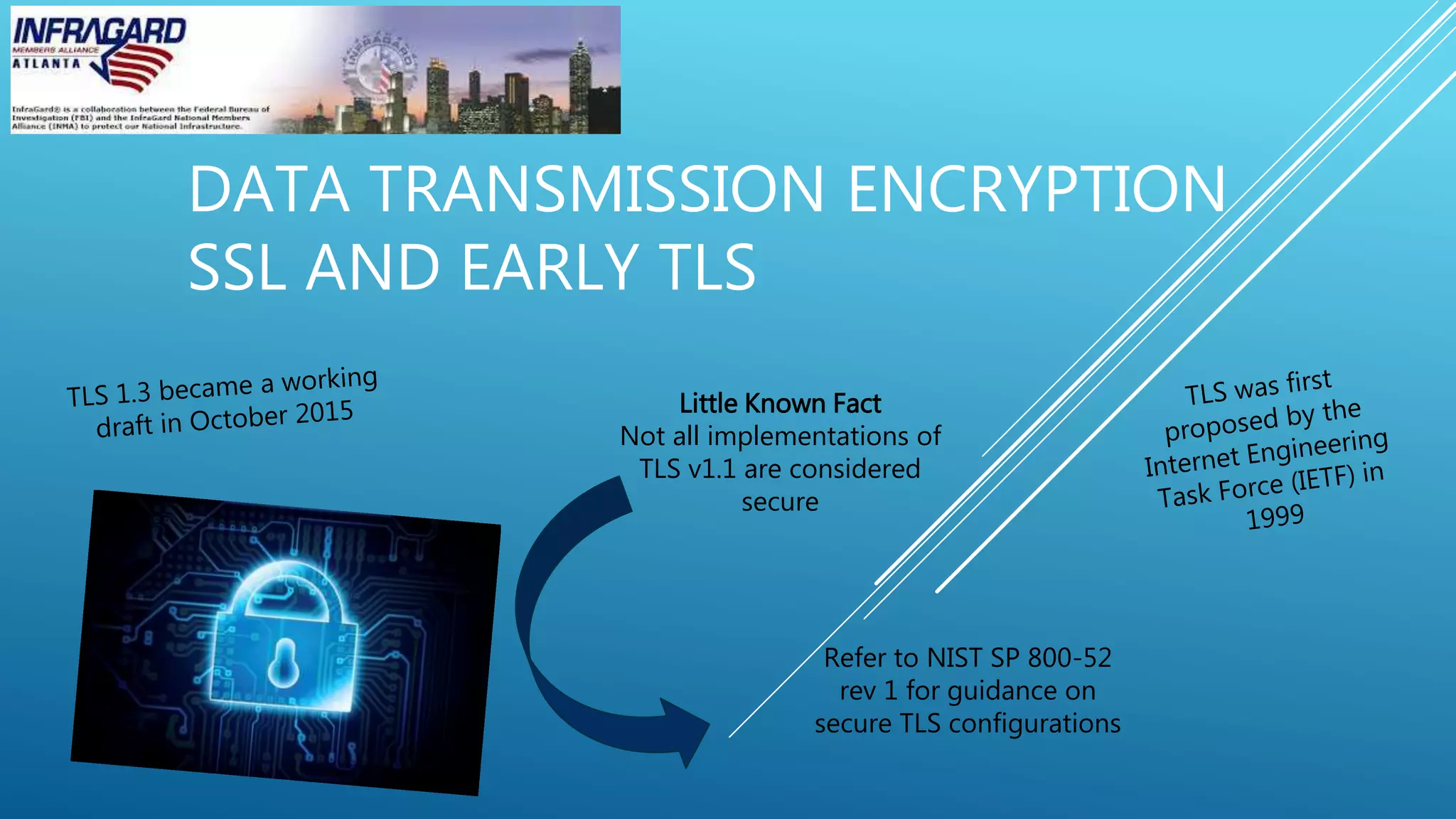
This document summarizes a payment card industry security and compliance round table discussion. It includes an agenda covering topics like EMV chip technologies, mobile payments, data transmission encryption, point-to-point encryption, PCI compliance in the cloud, designated entities, and two-factor authentication. Short biographies are provided for the panelists - Dr. Phillip Hallam-Baker, Trevor Horwitz, and Richard Emrich. The document concludes by advertising the webinar sponsor and providing contact information for the InfraGard Atlanta organization.