Embed presentation
Download to read offline
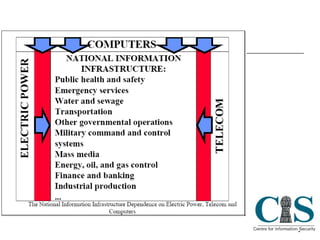
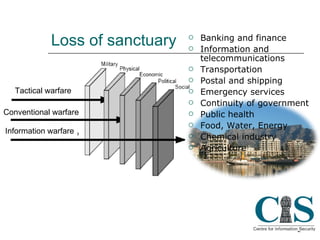
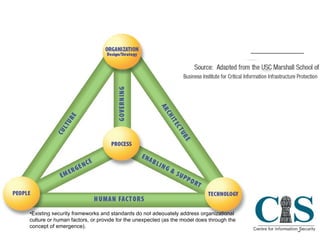
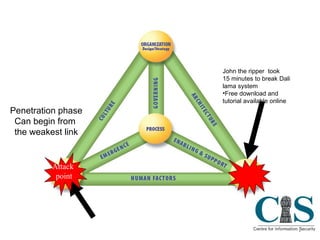
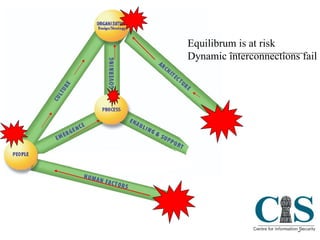
The document discusses threats to critical infrastructure from cyber attacks and information warfare. It notes existing security frameworks do not fully address organizational culture, human factors, or unexpected emergent threats. It also warns that the weakest link can be the starting point for penetration attacks, as tools are freely available online to exploit vulnerabilities. Maintaining security equilibrium is challenging as dynamic interconnections are at risk of failure.




