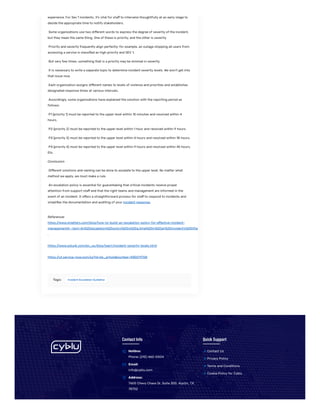
The document outlines an incident escalation guideline designed to instruct team members on proper procedures for escalating incidents within an organization. It emphasizes the importance of defining escalation levels based on severity and the need for clear communication during incidents, especially for critical issues like data breaches. Additionally, it highlights the necessity of establishing a structured escalation policy to ensure timely responses and effective management of incidents.