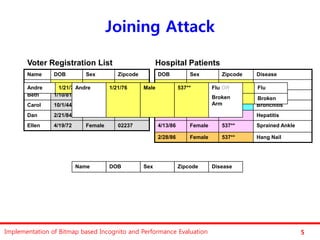
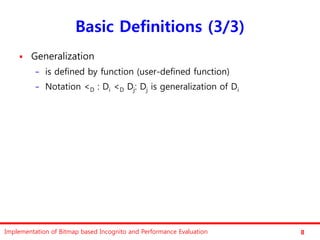
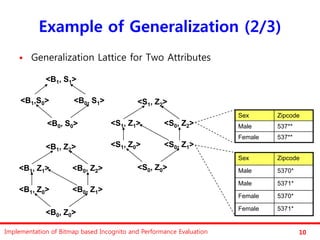
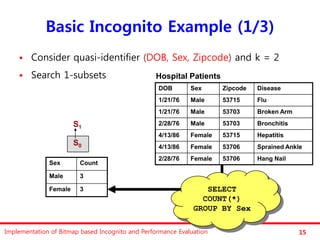
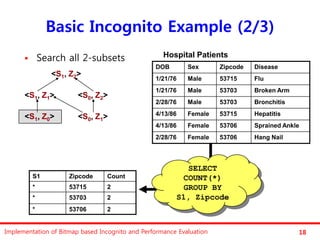
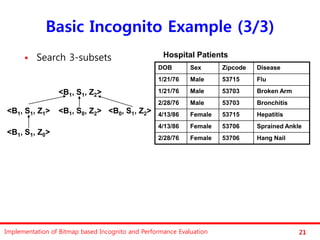
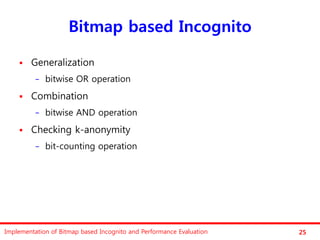
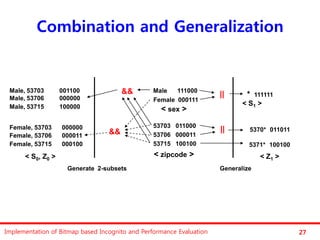
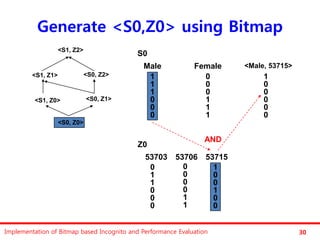
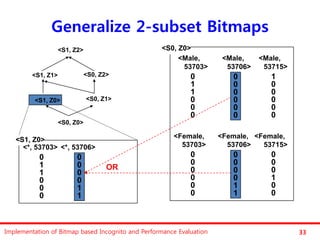
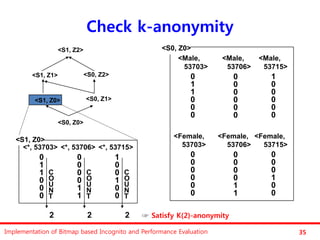
The document discusses the implementation of a bitmap-based incognito algorithm for k-anonymization, addressing privacy concerns related to data re-identification. It introduces optimization techniques that eliminate the need for expensive sorting operations present in traditional algorithms, thereby improving performance. The discussion includes examples, definitions, and properties related to k-anonymity and the bitmap method of data generalization.