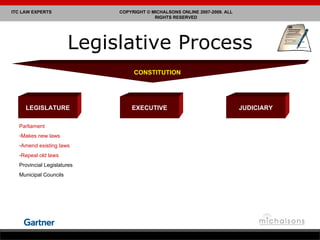
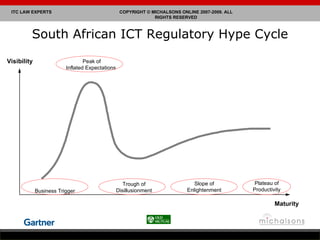
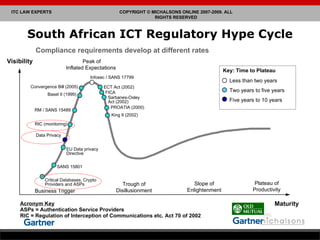
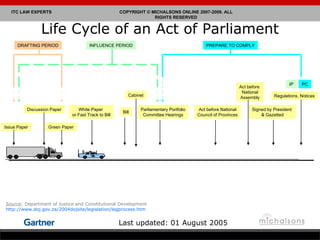
Lance Michalson provides an overview of ICT regulatory compliance in South Africa. He discusses the current legal compliance landscape and examples of compliance issues and technology legal risks. Key pieces of ICT legislation in South Africa are also examined, including the stages of developing an act of parliament. Issues related to privacy, monitoring communications, and critical databases are also summarized.









![THANK YOU FOR YOUR TIME!! Lance Michalson [email_address] “ IT Law with Insight” www.michalsons.com Copyright © Michalsons 2002-2009 The information contained in this presentation is subject to change without notice. Michalsons makes no warranty of any kind with regard to the material, including, but not limited to, the implied warranties of fitness for a particular purpose. Michalsons shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this material. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated to another language without the prior written consent of Michalsons This document is an unpublished work protected by the copyright laws and is proprietary to Michalsons. Disclosure, copying, reproduction, merger, translation, modification, enhancement, or use by any unauthorised person without the prior written consent of Michalsons is prohibited. Contact Lance Michalson at lance@michalsons.com for permission to copy.](https://image.slidesharecdn.com/ictcompliancegartneraugust2005-090226091818-phpapp01/85/Ict-Compliance-Gartner-August-2005-29-320.jpg)