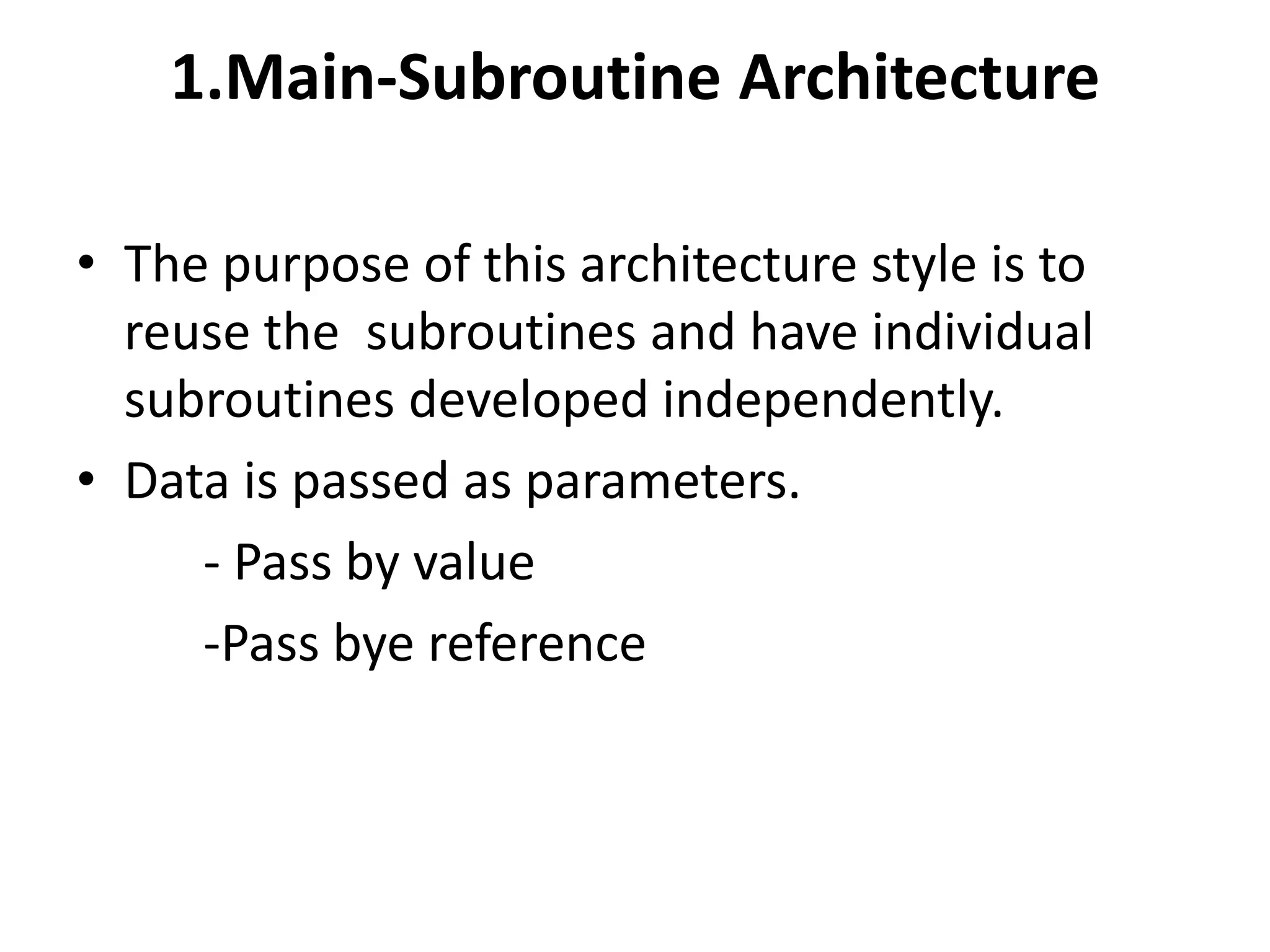
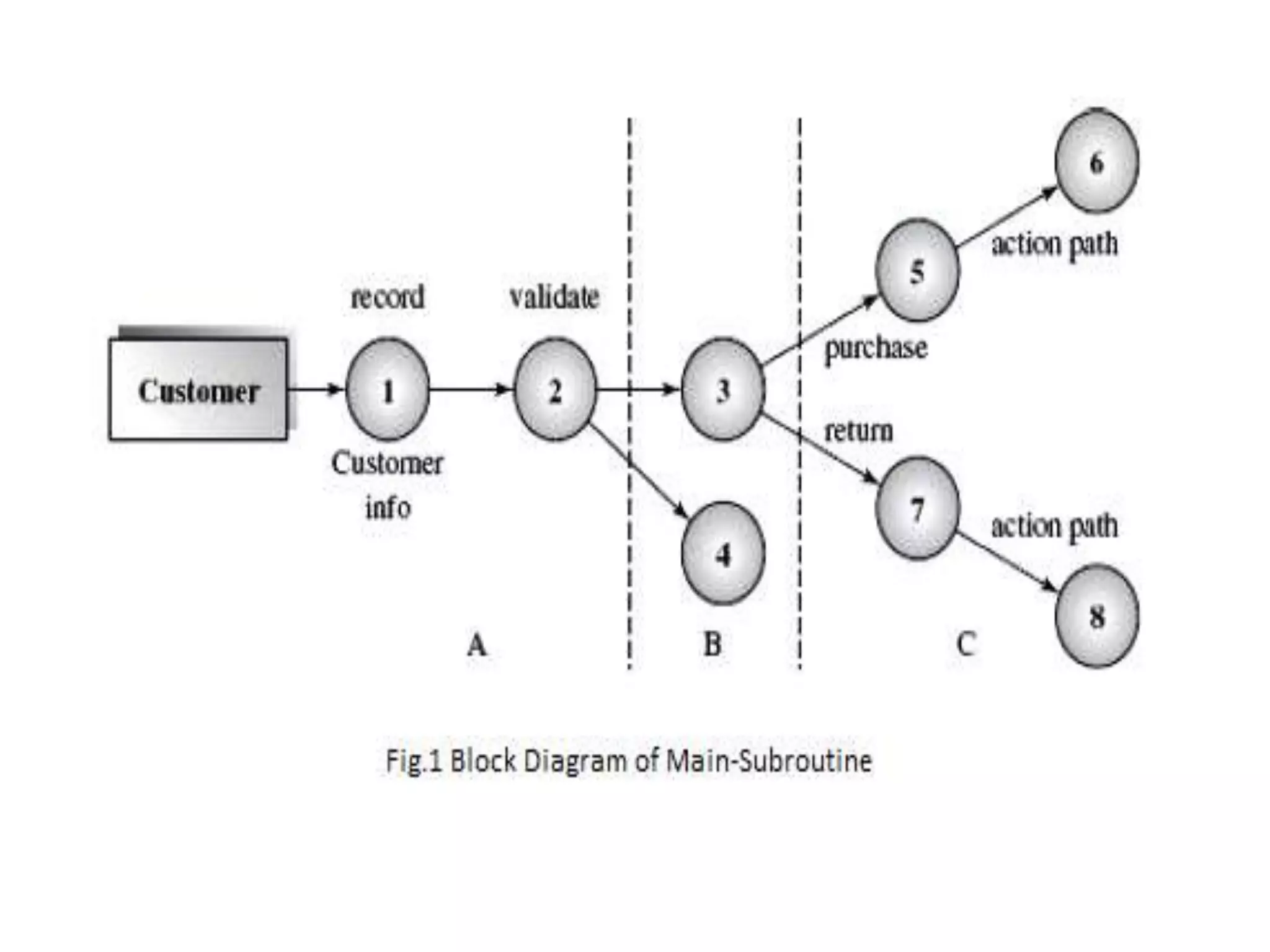
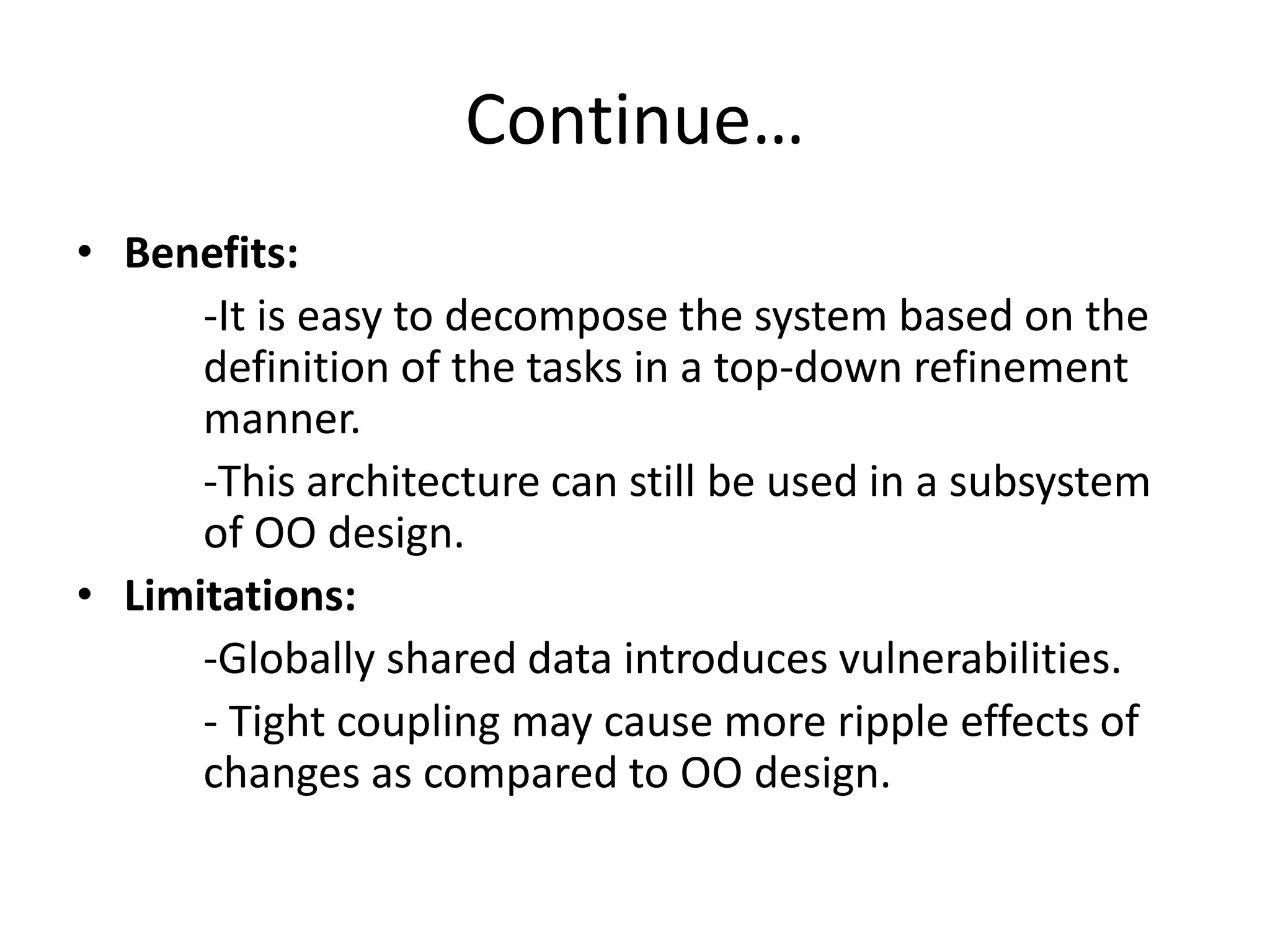
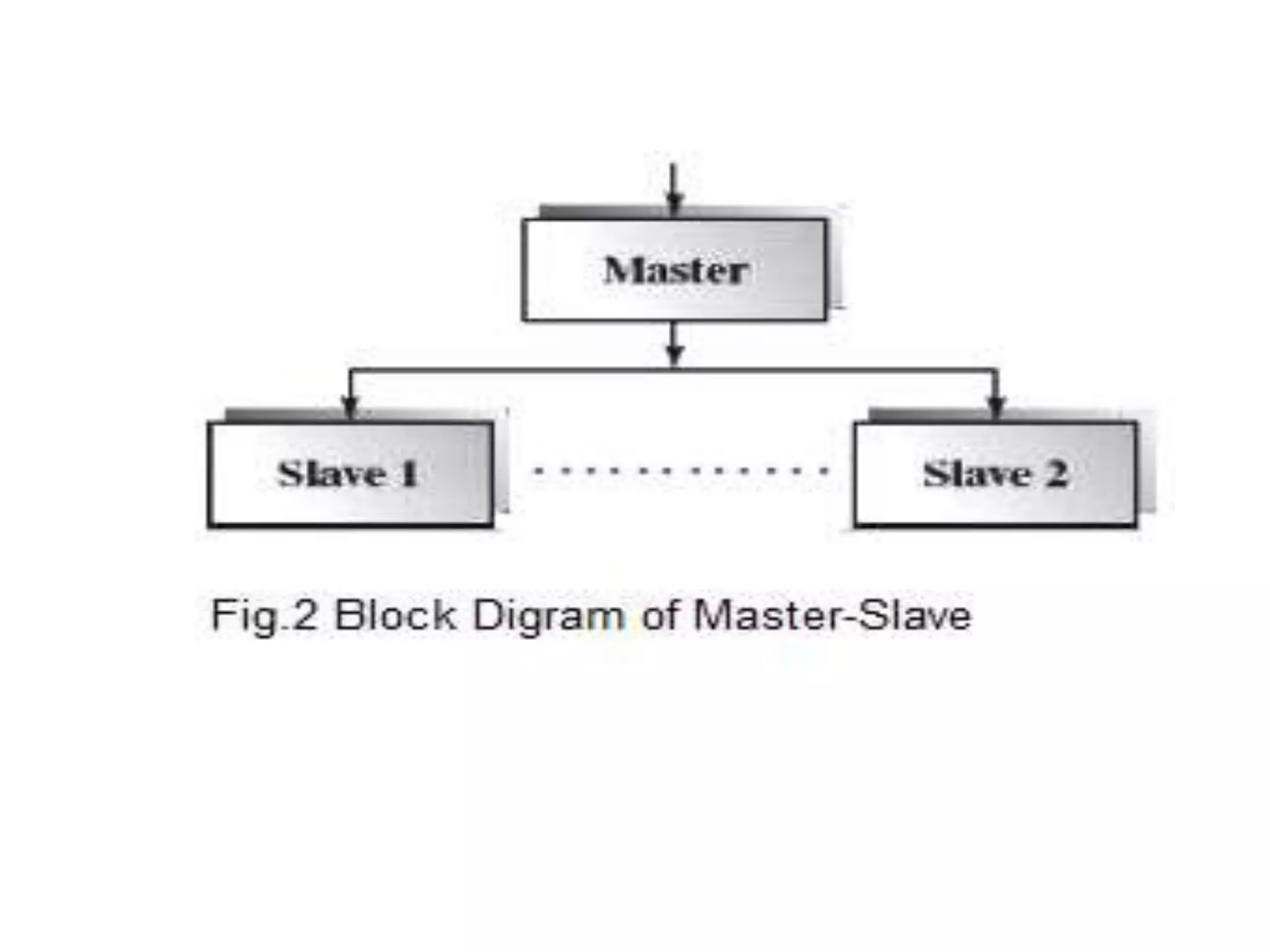
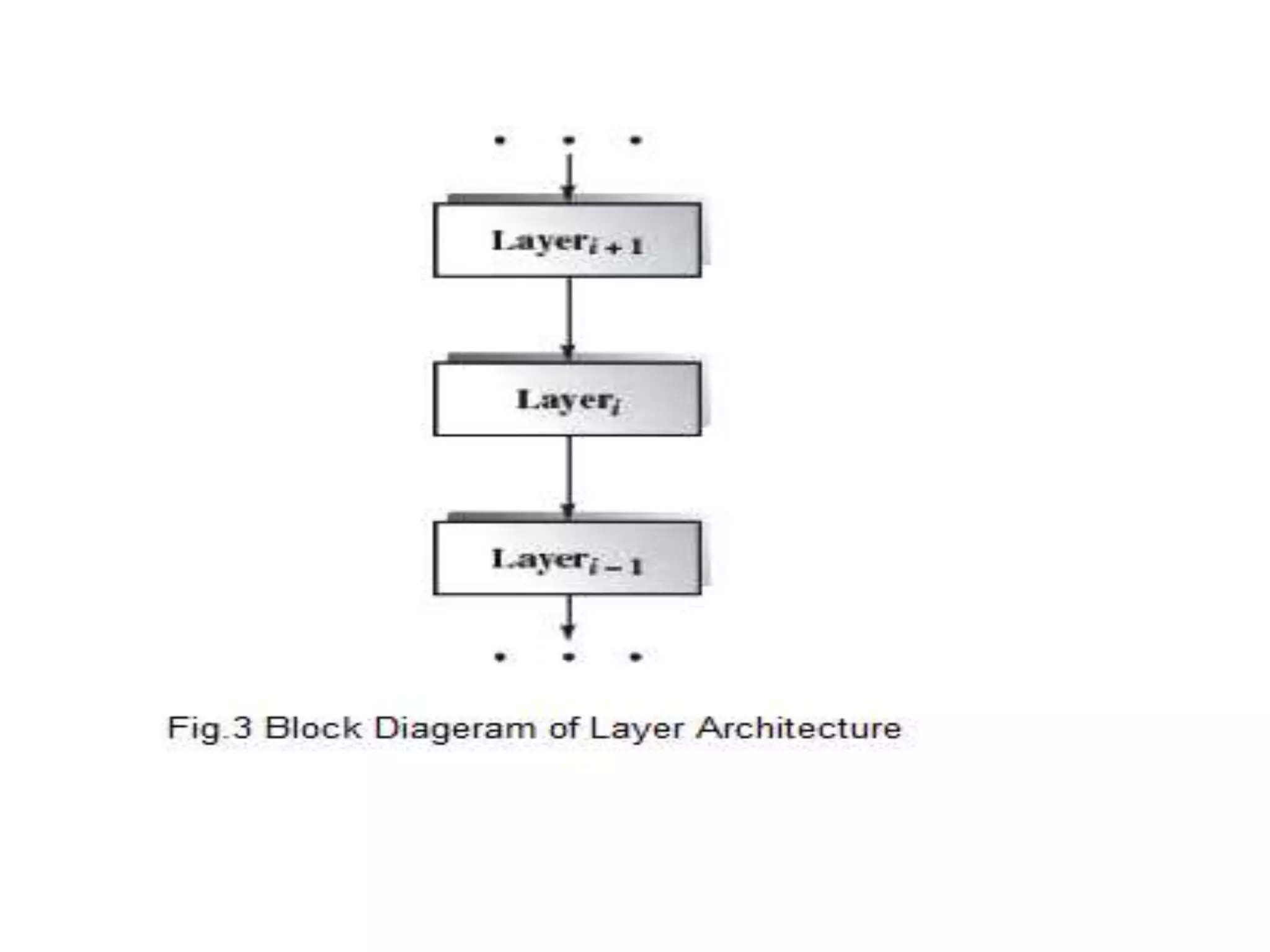
This document discusses four types of hierarchical architecture: main-subroutine architecture, master-slave architecture, layered architecture, and virtual architecture. Main-subroutine architecture reuses subroutines that are developed independently and passed data through parameters. Master-slave architecture supports fault tolerance through slaves providing replicated services to the master. Layered architecture decomposes a system into layers with defined responsibilities and interfaces between layers. Virtual architecture builds upon an existing system to provide virtual abstraction and portability.