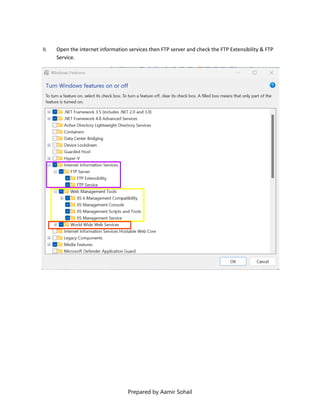
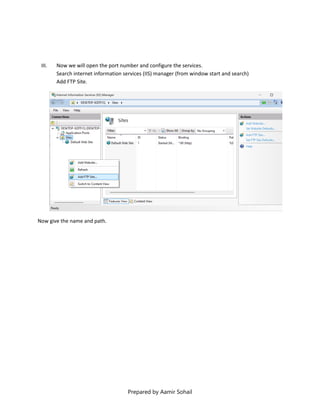
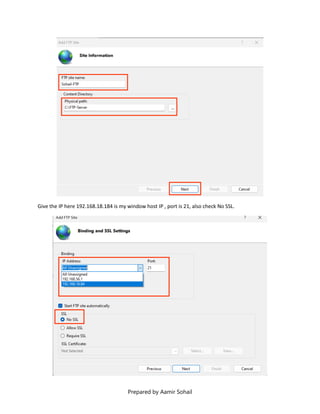
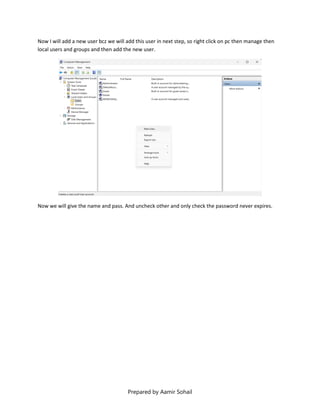
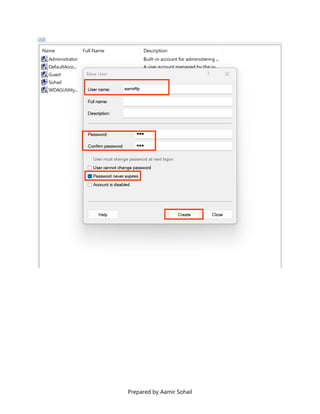
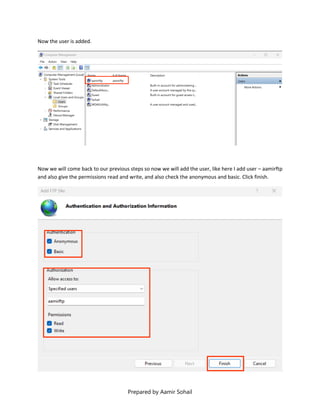
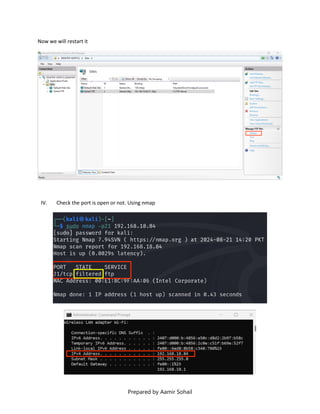
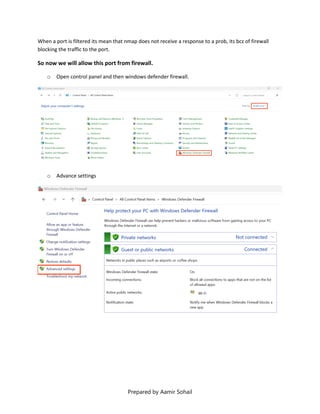
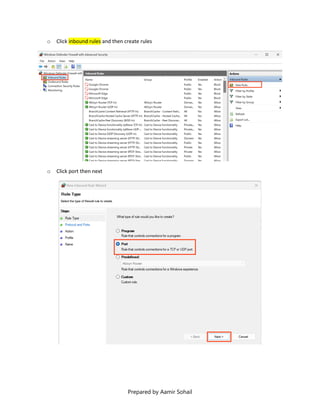
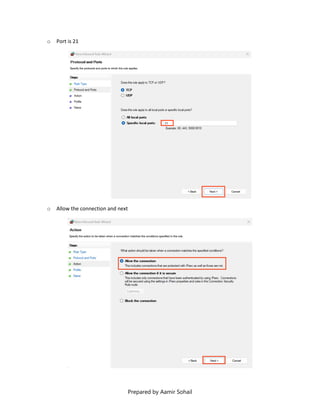
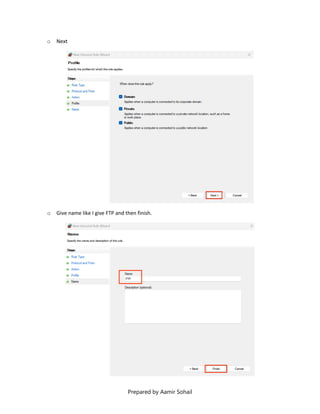
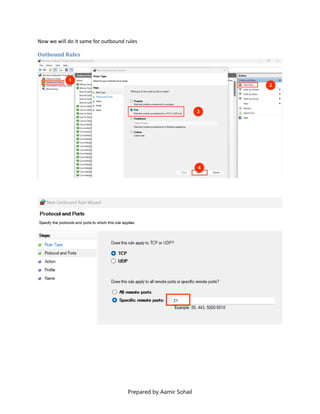
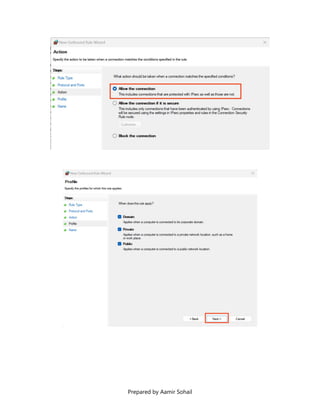
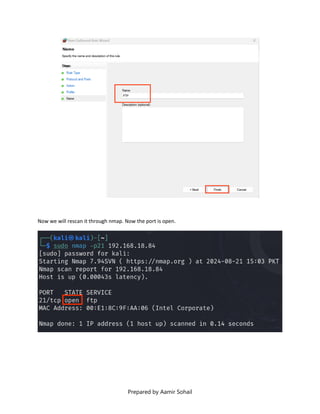
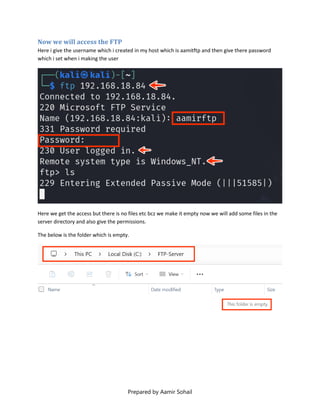
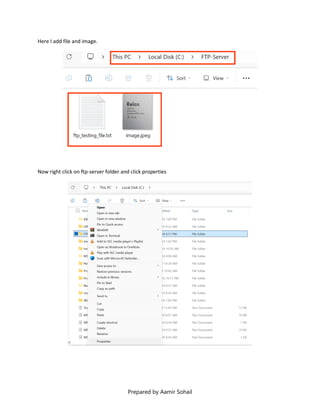
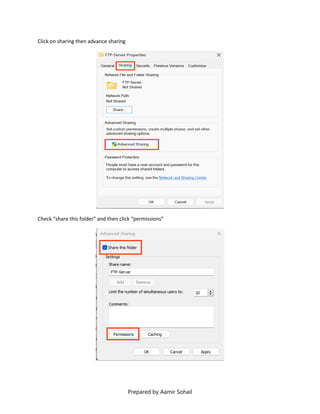
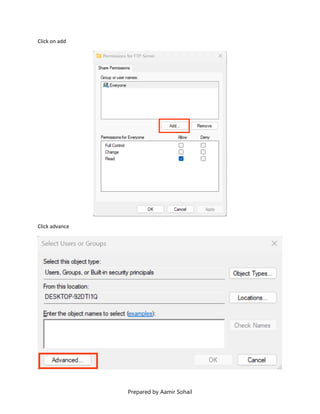
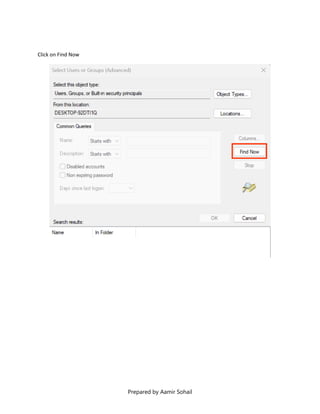
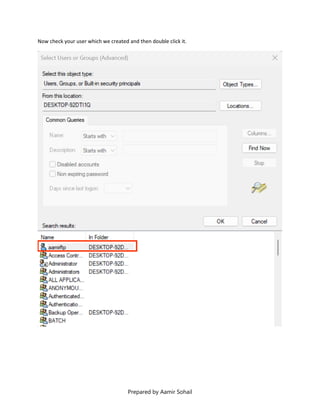
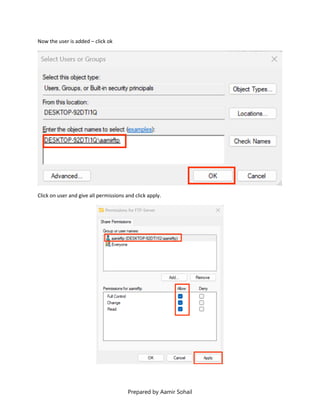
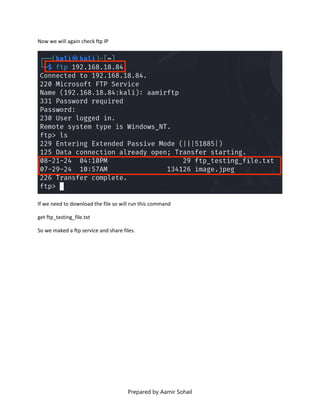
This document outlines the setup and configuration of a basic networking environment for cybersecurity, detailing routing tables, TCP/UDP protocols, and FTP service configuration. It explains the roles of destination IPs, gateways, and the differences between TCP and UDP, emphasizing TCP's reliability versus UDP's speed. Additionally, it provides step-by-step instructions for configuring FTP and firewall settings to share files securely over the network.