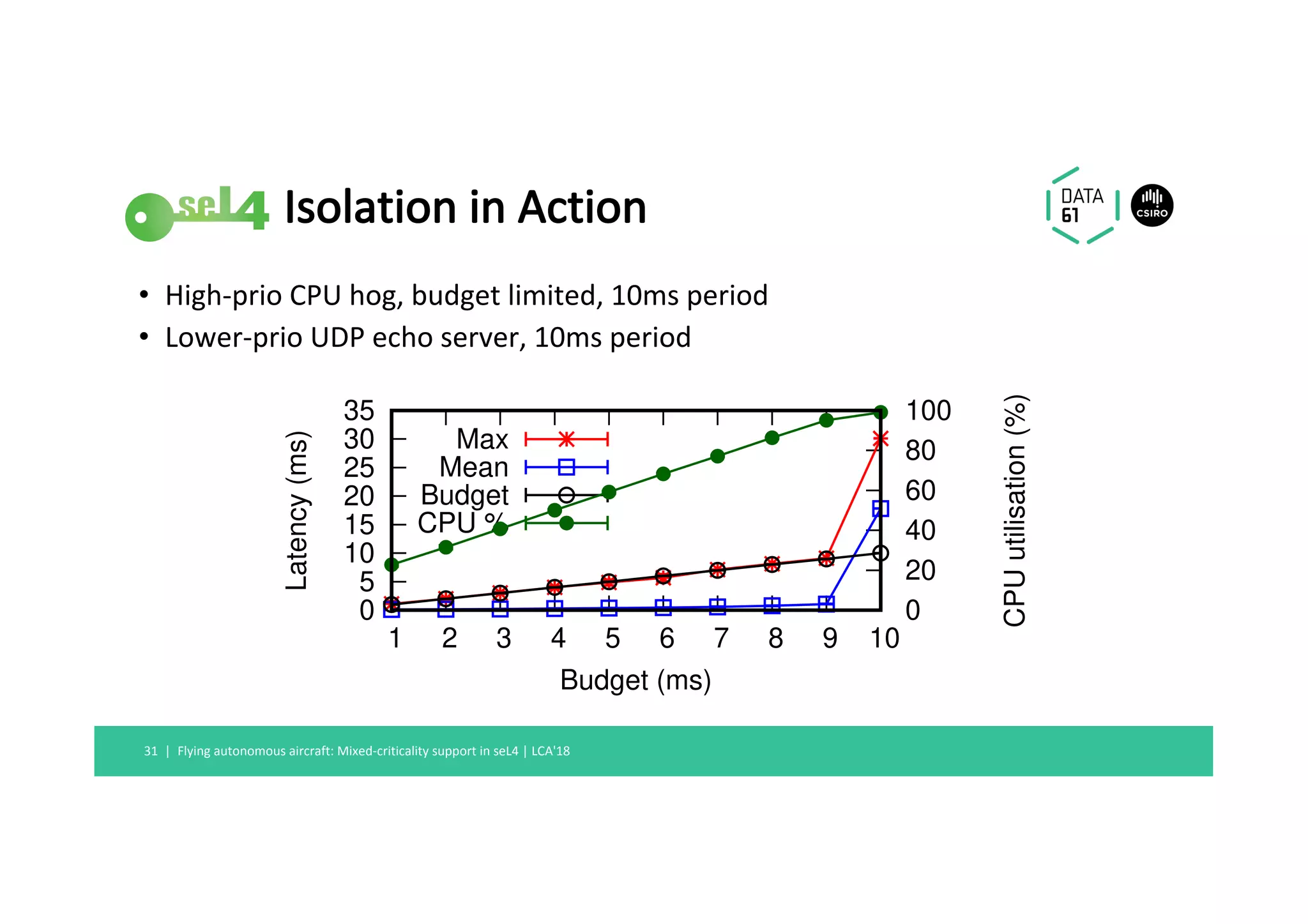
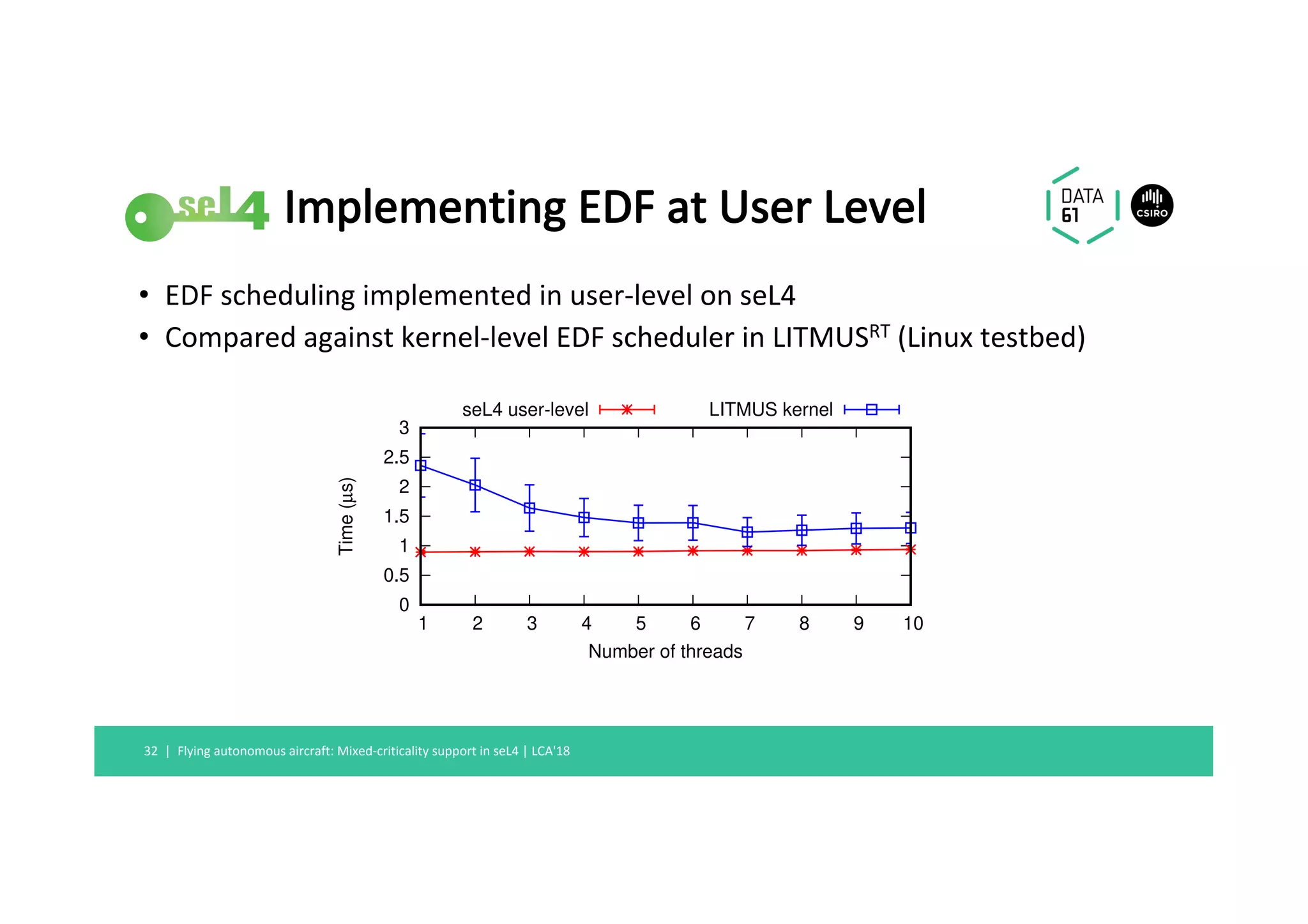
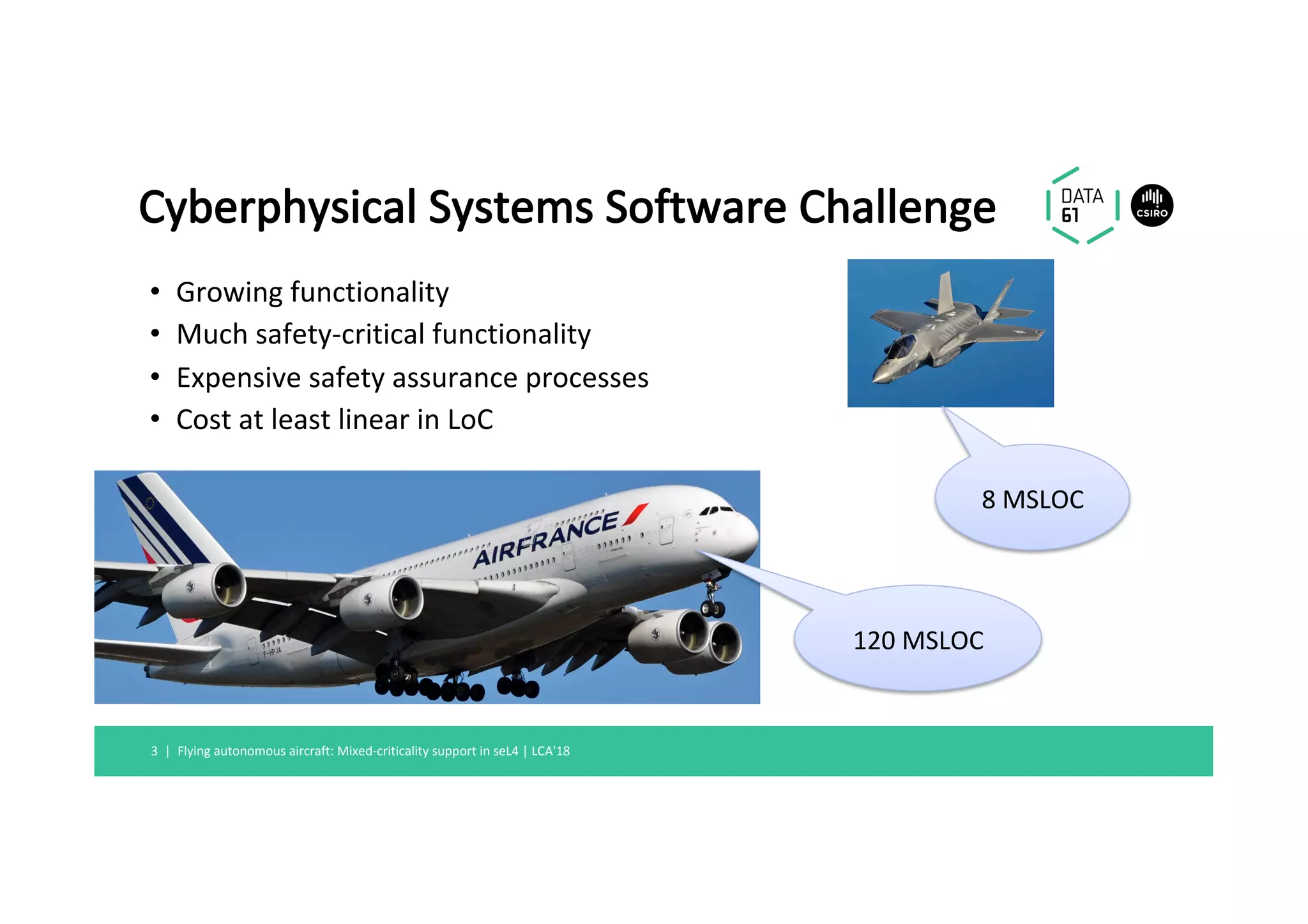
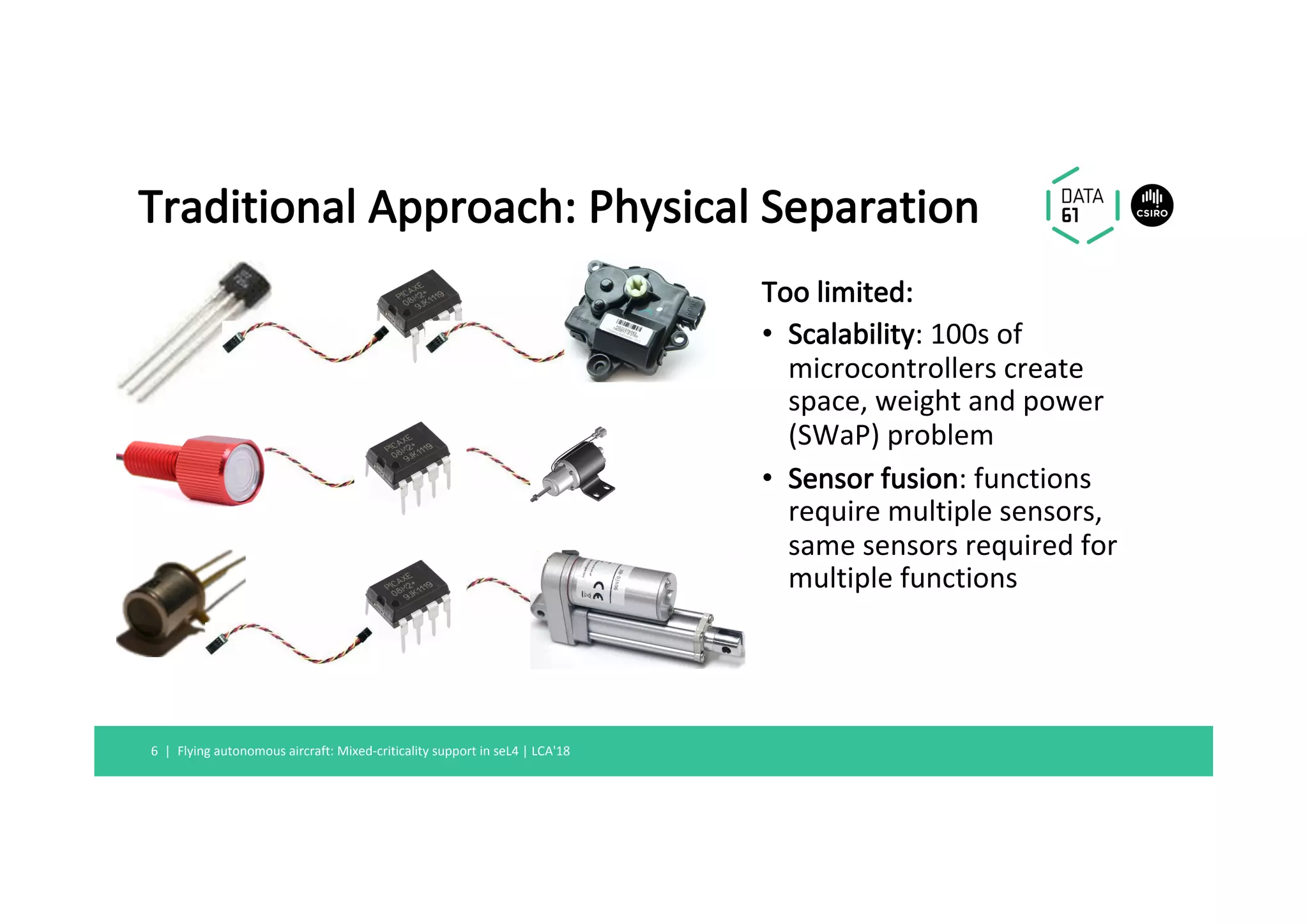
This document summarizes a talk about mixed-criticality systems and how the seL4 microkernel provides support for them. The key points are:
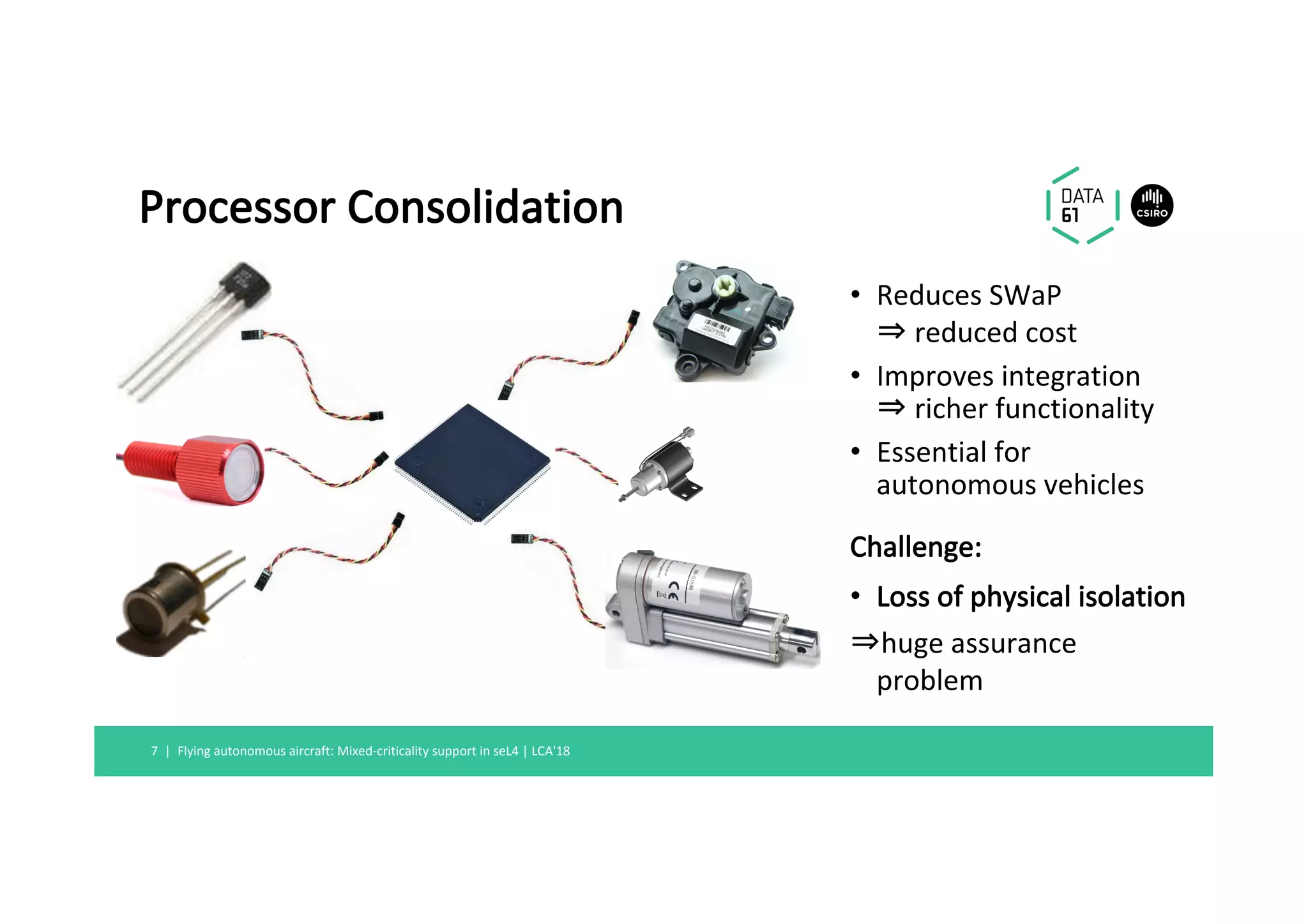
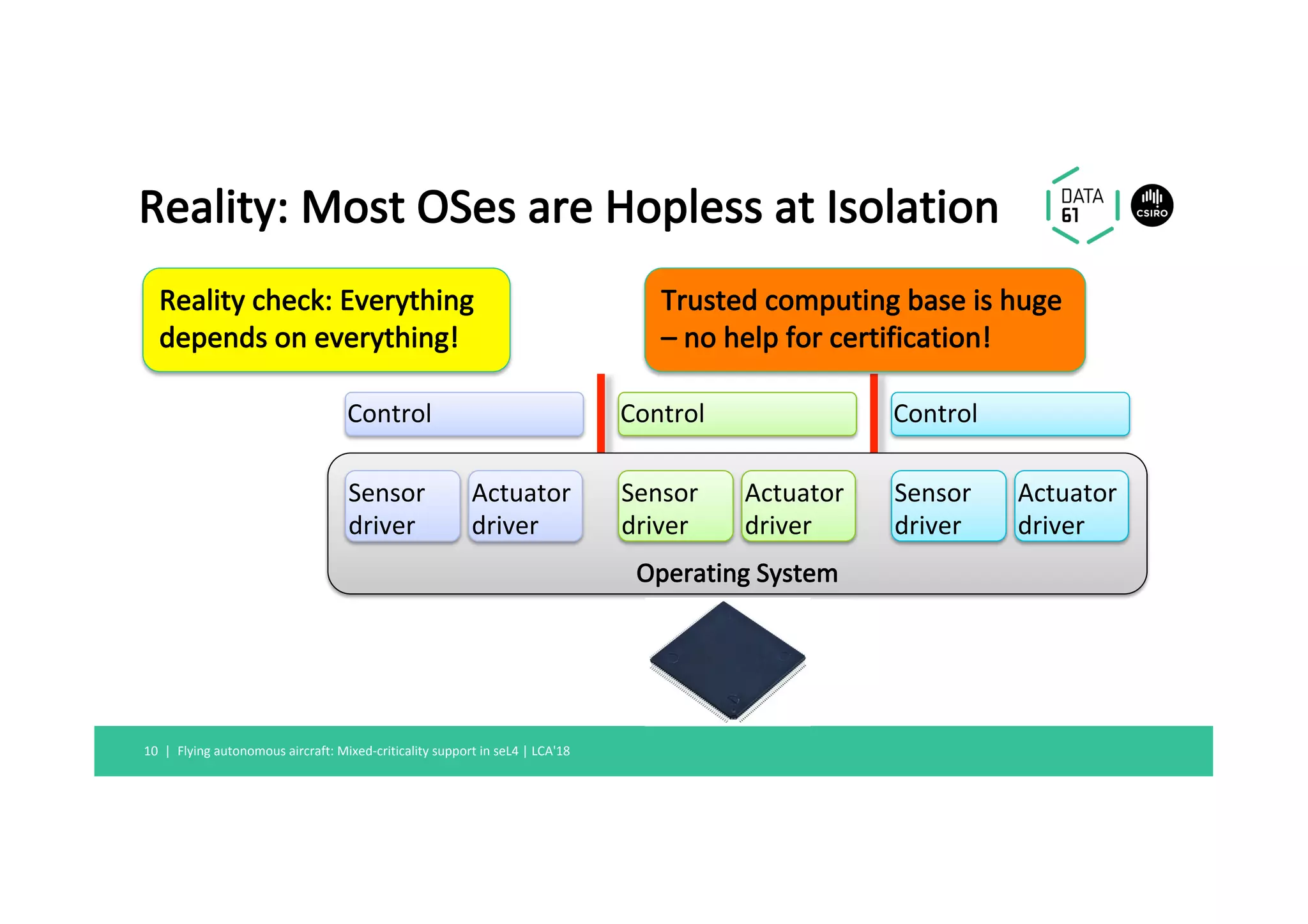
1) Mixed-criticality systems consolidate software with different safety criticalities onto a single processor to reduce costs, but this makes certification difficult without strong isolation.
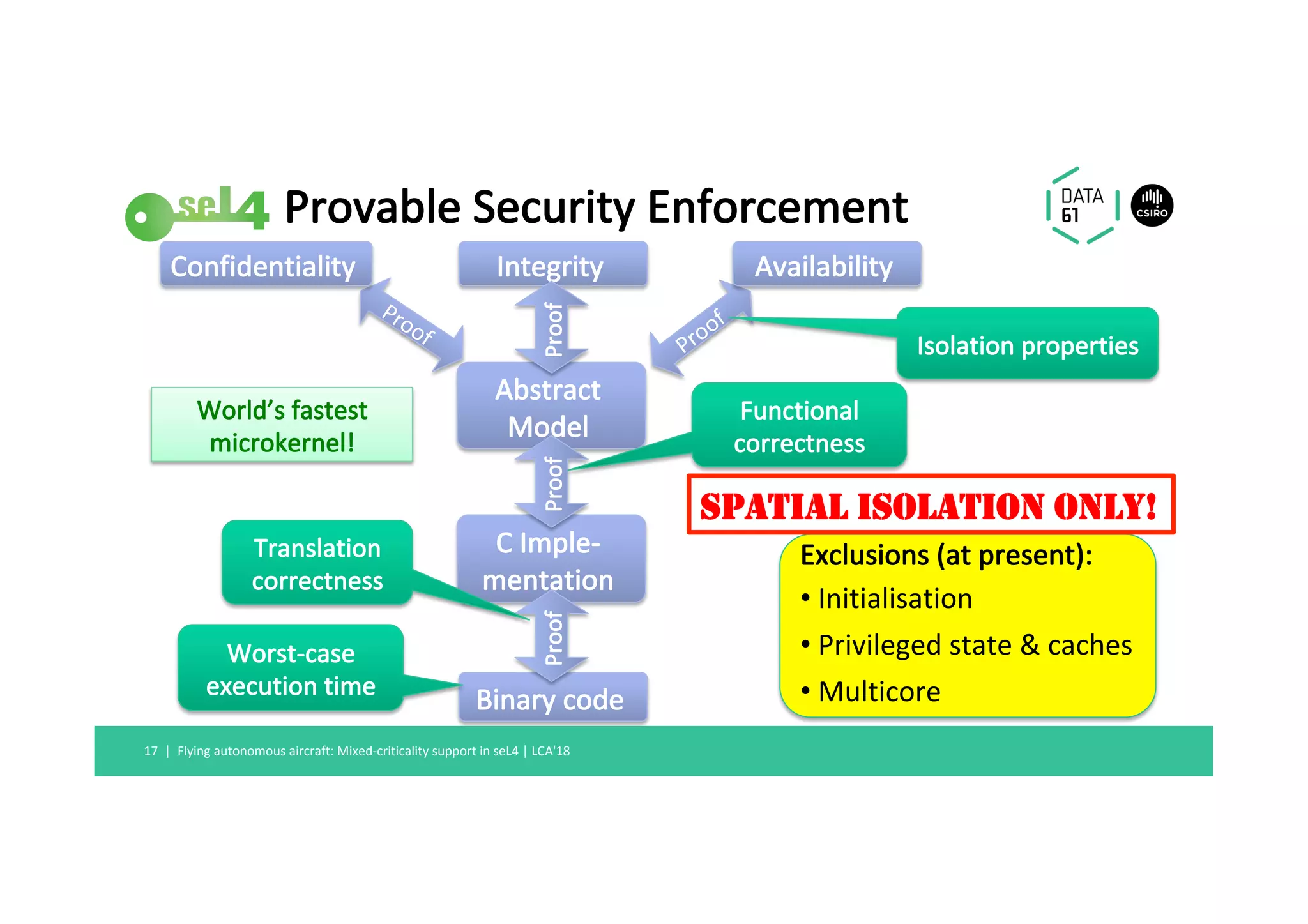
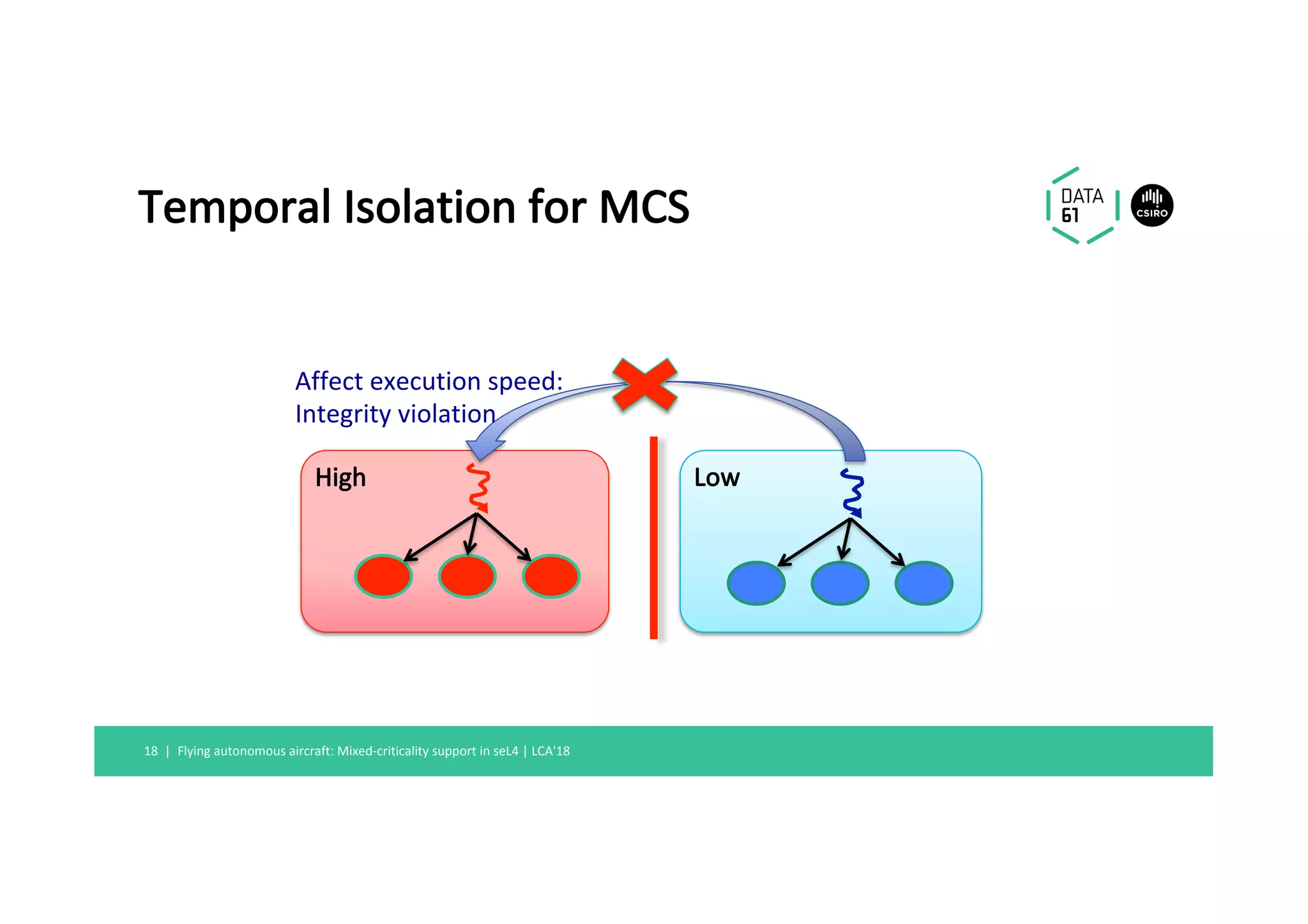
2) seL4 provides both spatial and temporal isolation through fine-grained capabilities and new scheduling contexts that enforce CPU budgets and deadlines.
3) This allows critical software to be certified in isolation even when run alongside less critical software on the same processor, enabling cost-effective consolidation for applications like autonomous aircraft.



















![Budget Expiry Options
• Multi-threaded servers (COMPOSITE [Parmer ‘10])
• Model allows this
• Forcing all servers to be thread-safe is policy !
• Bandwidth inheritance with “helping” (Fiasco [Steinberg ‘10])
• Ugly dependency chains !
• Wrong thread charged for recovery cost !
• Use timeout exceptions to trigger one of several possible actions:
• Provide emergency budget
• Cancel operation & roll-back server
• Change criticality
• Implement priority inheritance (if you must…)
Flying autonomous aircraft: Mixed-criticality support in seL4 | LCA'18 29 |
Mechanism for
implementing other
models, e.g. earliest-
deadline first (EDF)](https://image.slidesharecdn.com/1801-lca-180330012223/75/Flying-Autonomous-Aircraft-Mixed-Criticality-Support-in-seL4-29-2048.jpg)