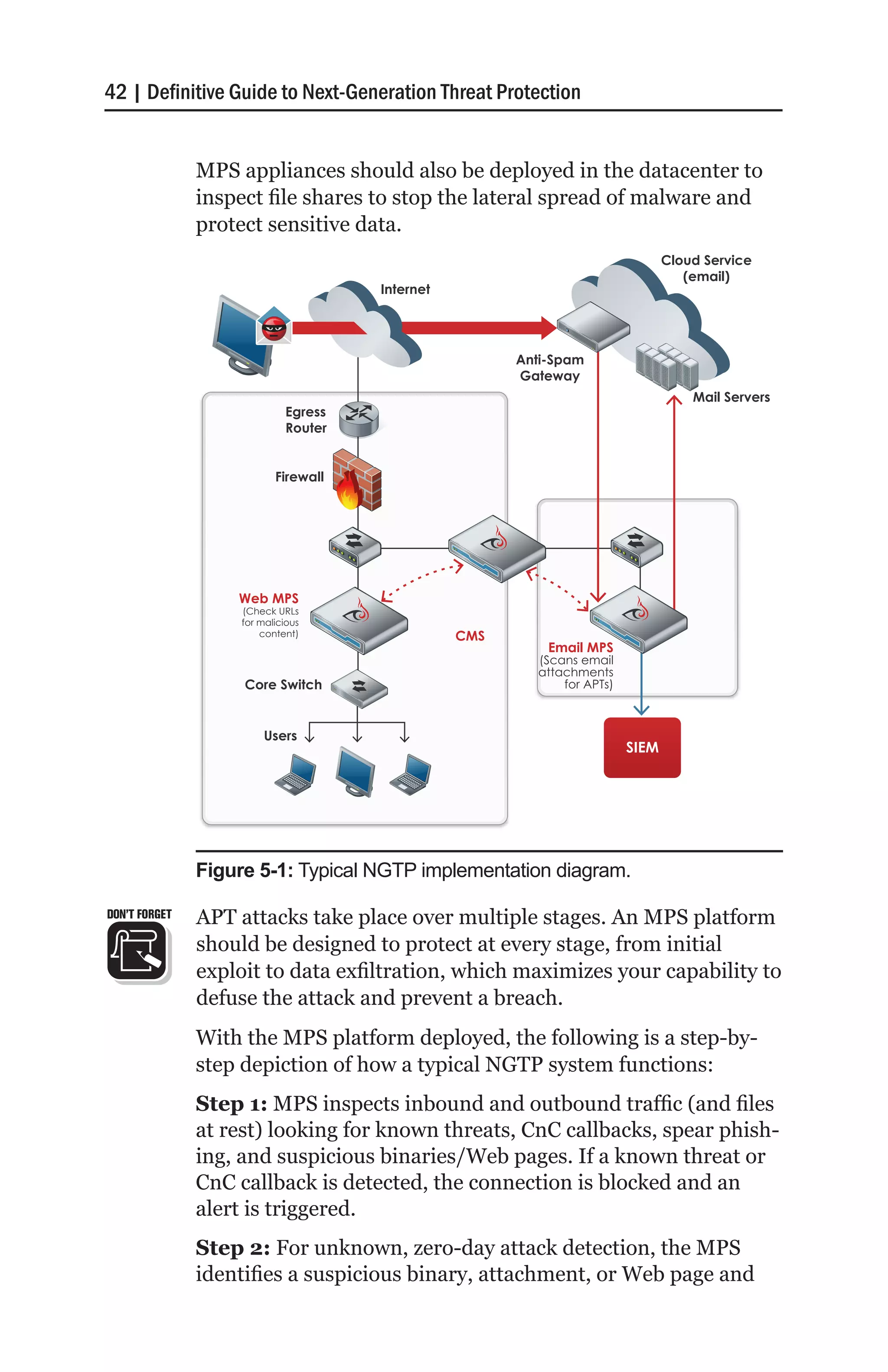
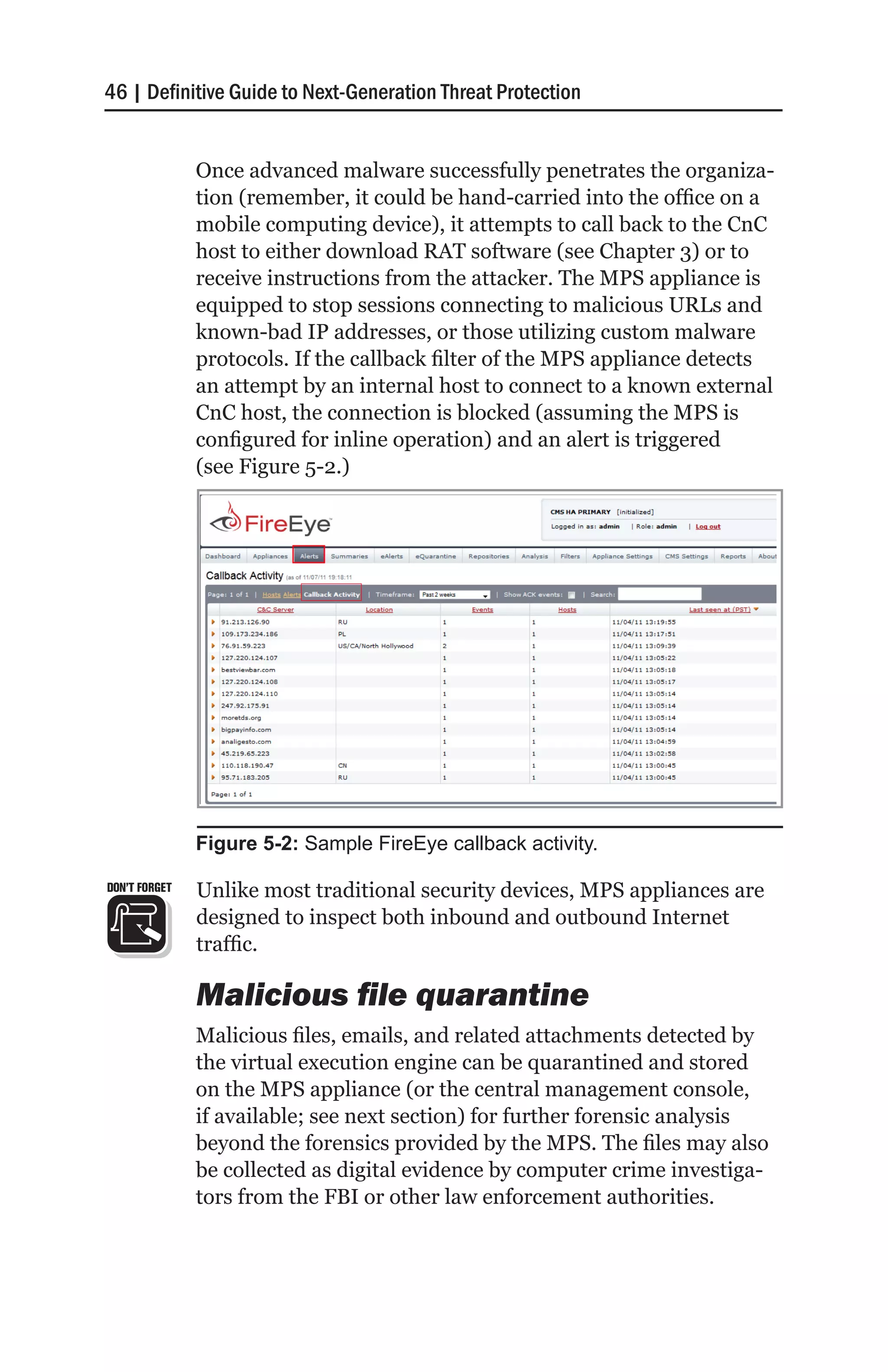
The document discusses next-generation cyber threats, which bypass traditional defenses through sophisticated techniques. It notes staggering statistics on recent data breaches, including that 98% of incidents stemmed from external agents, 85% took weeks to discover, and 81% involved hacking. Major recent attacks on both commercial and government systems are described. The costs of failure and today's threat landscape, including advanced malware, zero-days, and advanced persistent threats (APTs), are also outlined.