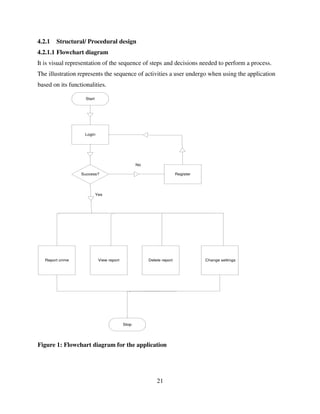
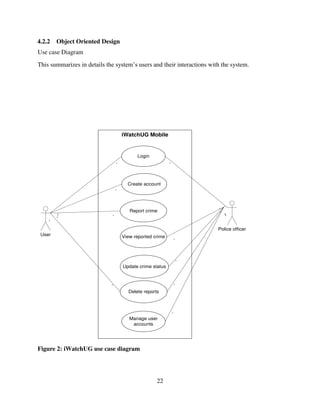
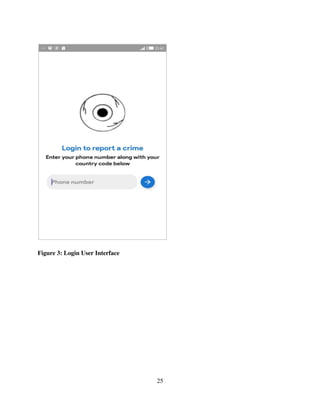
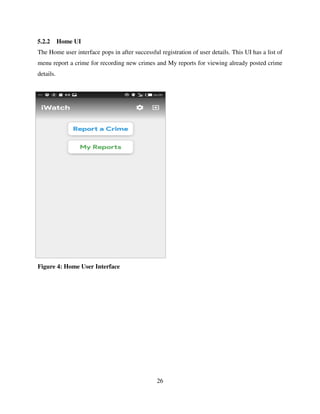
This final year project report presents the design, development, and evaluation of a Community Policing Mobile Application aimed at strengthening public safety and enhancing collaboration between community members and law enforcement agencies. The application provides a user-friendly platform for residents to report incidents, share information, and receive timely alerts, thereby fostering proactive community engagement in crime prevention. By leveraging mobile technology, the project seeks to improve communication, transparency, and responsiveness in community policing efforts. The report documents the entire project lifecycle, including requirements analysis, system design, implementation, testing, and user feedback, demonstrating the practical application of business computing principles to real-world challenges.