This thesis evaluates metamorphic testing for sensor processing applications on Android platforms. Metamorphic testing builds new test cases by applying mathematical transformations to existing test cases to detect errors without an oracle. The goal is to address issues like the oracle problem in sensor applications where accurate results are difficult to determine. The study designs metamorphic tests for an Android step counting algorithm, seeds faults, and evaluates the technique's ability to detect errors. Results show metamorphic testing was effective at detecting various seeded faults.









![CHAPTER 1 - INTRODUCTION
1.0 Overview
Reducing the cost of software development while improving software quality is an
important objective for the software industry. A study by Tassey estimated the annual cost for
software testing to be between $22.2 to $59.9 billion dollars, with over half of those costs borne
from mitigation activities caused by correcting errors after a software’s release [15]. Checking a
product for faults is standard practice in almost all fields, and is fundamentally important to
product quality. This is especially true in the field of software engineering for two reasons. The
first is the complexity required from many modern software products. The second reason is
due to potential consequences of a software failure. The production of reliable software is one
of the fundamental requirements for applying computers to today's challenging problems [12].
As computer programs grow in size and complexity, testing costs will only increase. More
research is needed to reduce these costs by developing new, more effective testing methods and
approaches.
A novel testing technique that aims to improve upon the state of the practice is
metamorphic testing. It has been used to help improve software accuracy and reliability in several
fields includingBioinformatics, Genetic Sequencing, and MachineLearning. The focus of this thesis
is applying this technique to sensor based application,](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-10-320.jpg)


![CHAPTER 2 – PROBLEM STATEMENT/HYPOTHESIS
2.0 Problem Statement
The conventional method to test software is to examine pairs of expected output data and
input data, then check to see if the expected output has been achieved when a given inputis passed
through the code being tested. If the output is incorrect, then it is safe to say your program has a
bug/error; but what if the output is correct? Is the code now faultless? The answer is no, as even
for a relatively simple program, reliably finding all errors that may exist is a difficult task. As
software increases in complexity, many computer programs are tasked with problems for which
the correct output is difficult to express in all cases or with 100% confidence. This is known as the
oracle problem in software testing. Finding errors, logic mistakes, and general bugs is inherently
difficult if a developer does not know what the final outcome should be once a program’s
computations are complete. As mentioned in the movie “The Hitchhiker’s Guide to the Galaxy” a
computer attempts to compute the meaning of life [21], generating an arbitrary answer of 42. But,
is that answer correct? Perhaps the better question is how someone would test this computer
program for correctness. Metamorphic testing has been shown to be effective by several studies [1]
[1] [18] [19] in a wide range of testing applications, especially testing software that possesses the
oracle problem.
This thesis contains the methods needed to apply metamorphic testing to sensor based
Android applications. The goal is to provide Android developers with a new tool to further test](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-13-320.jpg)

![CHAPTER 3 – BACKGROUND/RELATED WORKS
3.0 Traditional White-Box Testing
The term white-box testing is used to describe a group of methods used for testing a
software’s internal source code by constructing test cases. Also known as clear box testing, or
glass box testing (Beizer, 1995),these connotations indicate that a developer has full visibility of
the internal workings of the software product, specifically, the logic and the structure of the code
[8]. This visibility allows developers to create test cases specifically designed to exercise a
software’s processing path and determine if it has reached an appropriate result. This method is
used to test a variety of source code functions such as data flow, decision statements, networking
connections, and program pathing. All of these examples require the developer to evaluate the
Software Under Test (SUT) using a predefined set of inputs against the expected set of outputs.
There are two central “white-box” testing methods thatcan be applied when creating a test
case for a particular piece of software. The first is known as “Unit Testing”. The most fundamental
testing method of the two, Unit testing is used to test one specific part of a code, usually a function
or family of functions known as modules or units. It has become a good programing practice to
create several separate modular functions to construct an overall piece of software, breaking a large
piece of code down into a bunch of small pieces of code that perform a very specific task that
contribute to the overall program as a whole. The primary goal of unit testing is to take the smallest
piece of](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-15-320.jpg)
![testable software in the application, isolate it from the remainder of the code, and determine
whether it behaves exactly as you expect [7].
The next type of testing method is Integration testing. Just like its name suggests, this tests
the assimilating of smaller pieces of code into a larger piece of code after they have been verified
to be correct through unit testing. This insures that all the modules in the system are working
together as intended [10].
When constructing test cases for error detection, developers can choose to implement them
using a variety of approaches. The best approaches exercise all possible inputs and conditions
within a given program in an attempt to insure no bug is left undetected, this is called “Full
Coverage”. However testing with full coverage approaches my not always be possible or practical.
Methods such as Simulation Testing and Symbolic Extraction allow for deliberate and effective
testing for some software, but not all.
3.0.1 Simulation Testing
Perhaps the most basic form of software testing, simulation testing is the simple process of
feeding a predefined input into a program and evaluating the result for accuracy. These tests are
designed mimic the operation of world scenarios, such as the day-to-day operation of a bank, the
running of an assembly line in a factory, or the staff assignment of a hospital or call center [9].
However simulation testing has a fundamental flaw when it comes to testing software that have
condition statements. Using this method you can only test one condition at a time, if your program
has multiple conditions with several layers of nested conditions the number of possible results
grows very quickly, and testing for each of those results becomes more difficult.
For Example, if your program has an “If Statement” it can execute one of the two possible
7](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-16-320.jpg)

![testing large complex software. Figure 3.2 depicts how simulation testing can only execute
one path at a time with in a complex program.
Figure 3.2 – Simulation Testing Single Path Execution [11]
FSM = Finite State Machine (i.e. Computer Program)
3.0.2 Symbolic Execution
In an attempt to obtain full coverage for complex programs, James King created the first
automatic testing method called Symbolic Execution in 1976.Symbolic Extraction does away with
concreate inputs (i.e. numbers) into a program. Instead it supplies dynamic variables (or
symbols) as inputs into the software being tested; while keeping track of the conditions needed to
travel along each path of the source code [6]. This condition state tracking allows the symbols to
dynamically change in order to meet conditions needed explore and test another part of the
program.
For example if the symbol encountered an “If Statement” the value of the symbol could
change to satisfy the true condition. Since the current condition state is recorded, the symbol
variable can back track through the code, and then change to satisfy the false condition.
Repeating this process over and over this method of testing will ultimately achieve full coverage
as illustrated by figure 3.3 [6].
9](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-18-320.jpg)
![Figure 3.3 – Symbolic Execution Path Execution [11]
Even though Symbolic Execution is able to achieve full coverage, it is only able to do so
for relatively exceedingly large programs. As programs get large, their conditional statements
grow exponentially, costing more memory to track current paths and more time to execute.
This eventually caused the testing method to become unpractical. This phenomenon is known
“Path Explosion”.
3.1 Path Explosion
Symbolic techniques have been shown to be very effective in path-based test case
generation; however, they fail to scale to large programs [16]. This is because the possible
number of execution paths to be considered symbolically is so, eventually only a small part of the
Program path space is actually explored [14]. There have been several studies and projects
dedicated to increasing the number of possible paths methods such as these can handle. Most
notably the field of model checking [17], even winning the Turing Award in 2007 [35]. Todays
most advanced software contains millions of lines of code with billions of possible paths. Only
10](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-19-320.jpg)
![time will tell if new developments in this field will keep up with the path of ever increasing
path explosion, however these methods of testing are optimal for solving other testing hurtles
such as the oracle problem such as those found in machine learning. This is especially true if
these machines contain large decision making processes with billions of possibilities.
3.2 The Oracle Problem
Traditional unit and integration testing methods are great for testing software that have a
known answer. Model testing is even better at automatically generating full coverage tests for
constrained software. Both of these testing metrics still require finding inputs that cause execution
to reveal faults [5]. What if you didn’t know all the possible input combinations or execution paths
a software might take to produce a result? Furthermore, what if you don’t know what the answer
should be? Applying computers to solve for unknown problems is one of the stables of the
industry, but testing such software is incredibly difficult and costly. This is known as the oracle
problem [5], and solving it has been a major issue for several fields of computer science. After all,
answering questions we do not know the answer to is the fundamental requirement for scientific
advancement. Solving the oracle problem involves constructing some sort of test oracle or table of
expected results that can be compared to a given set of inputs [18].Most of these types of
applications fall under the umbrella of machine learning.
3.3 Machine Learning
Thebasic definition ofMachineLearningis gettingcomputers toact withoutbeingexplicitly
programmed,and over the pasttwo decades MachineLearninghasbecomeoneof the mainstays of
information technology[19].Thesealgorithms canbeas simpleas thespamfilterin youremail
learningwhich emailstosend toyour junkfolder, or as complex as the self-drivingcar;butthey
11](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-20-320.jpg)
![all face the same fundamental problem. These computer applications do not start off knowing all
the answers to every problem they may face, hence the name “machine learning”. When
developing these applications, how do programmers know that the software they have written
will instruct a self-driving car to stop at a red light instead of speeding through it? In situations
like these, traditional testing measures cannot be applied due to large number of possible inputs
and execution paths. Many these software also lack a definitive result the computation it is trying
to execute. Here Metamorphic Testing can be applied to the machines known set of rules to
evaluate if the program will react in the desired manner when presented a choice. The idea is
relatively simple, but extremely difficult to execute.
3.4 Metamorphic Testing
The concept of metamorphic testing was formally introduced to the world in 1998 by
three professors from the University of Hong Kong. Dr. Chen, Dr. Cheung, and Dr. Yiu [20].
They observed three fundamental problems with current white-box testing methods. The first
observation made was that software which passes its initial test cases were considered successful
and are seldom investigated further for errors. Second, no matter how much testing is done, a
software will most likely still contain errors. Lastly, obtaining a test oracle to test against in many
software applications (especially in the development phase) is unrealistic in many situations. [20]
Solving the oracle problem allows developers to tackle computing challenges that we do not
know the answer to. Perhaps chief among these is the challenge of machine learning.
However the aim of this thesis is to tackle the second observation made by Dr. Chen and
his colleagues, which states that almost all software contains errors. These errors can either be
logical errors that break the software in general, as well as mathematical or algorithmic errors
that cause the program give an inaccurate or inconsistent result. In order to solve this problem we
12](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-21-320.jpg)




![Applying a transform is relatively simple, but how do you know which transform to
apply? Not every transform is going to fit every problem. As of right now there is no industry
standard for applying data transformations, mainly because the field of computer science
encompasses such a wide range of industries. Many of these individual industries do have a set
frame work for finding software errors, but these methods often cannot be applied to another
industry. To understand how we applied metamorphic testing to our Android application you
must first understand the metamorphic properties of the software itself.
3.5 Step Detection Algorithm
This thesis uses a pedometer application as a test bed to evaluate if metamorphic
testing can be applied to Android sensor data, and if so; it will be used to measure its
effectiveness. In order to do this we will be manipulating the metamorphic properties within
this application’s mathematical and logical algorithms. Exploring and applying the correct
properties requires an understanding of basic human step detection.
Most people are familiar with the basic function of a pedometer, which is to count the
number of steps you take. Nonetheless, how does it count steps? Not to many years ago
pedometers had physical balls that rolled back and forth to determine steps. Every time the ball
made a full back and forth cycle the pedometer registered one step, but this system takes up a lot
of space and does not hold a high threshold of accuracy. Most pedometers today use a
microelectromechanical system or MEMS [22]. MEMS use a series of accelerators to detect and
calculate when a full step cycle has occurred. When running or walking your body moves in
three dimensions. Accelerometers measure the rate acceleration for each of the X, Y, and Z axes
[23]. The Figure below depicts a sample of this data. The next section will explain the math
behind calculatinga human step.
16](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-26-320.jpg)



![The final axis is forward acceleration. Conceptually you might think that this would be
the value that has the highest acceleration, but again if this was a measure of overall movement
then yes the forward axis would have the highest range and thus, the highest peaks on our graph.
However, since acceleration is the measure of change in speed, the X axis has the least “back-and-
forth” motion of the 3 axes. As you run or walk your forward acceleration as you transition from
the kick position to the stride position increases, because you are in the process of bringing your
lead leg out in front of you (commonly called striding out). When your lead leg hits the ground
and starts becoming your trail leg and begins transitioning into the kick position, the forward
acceleration slows down. At the same time the your vertical acceleration increases, because at this
point your body is moving farther up than it is moving forward.
Figure 3.7 – Stride Diagram [23]
3.5.2 Calculating Steps Filter
Filtering the data serves to purposes, the first is to smooth out the accelerometer data,
the second is to cancel out false positives. This is achieved by using Dynamic Precision [24], the
process of continuously updating the average of a data set. In this case we have 3 data sets, the X,
19](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-30-320.jpg)
![Y, and Z axes. In order to find the average we first need to find the minimum value and
maximum values of a predefined subset of the entire axis array, in our case every fifty samples.
The average value is equal to (Max + Min)/2. This average is called the dynamic threshold level. A
step is counted if the original axis line with a negative slope crosses the threshold line. Figure 3.8
below is an example of how this method is applied to the Z axis values.
Figure 3.8 - dynamic threshold leveling [23]
3.6 Fault Seeding and Detection
In order to evaluate the Metamorphic Testing for error detection, we must introduce some
errors to the software under test, otherwise known as fault seeding [26]. In this case the software
under test is an Android pedometer application. The basic concept behind fault seeding is simple.
Insert a logical or mathematical error into a piece of software, than run it through a test case. This
helps a developer determine if his/her test case can effectively detect that particular type of fault.
These faults can either be introduced to the code manually or generated automatically using
techniques such as Dependency Graphs [25].
20](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-31-320.jpg)
![CHAPTER 4 – DESIGN AND APPROACH
4.0 Android Frame Work
The Android Operating system has become one the most popular development platforms
over the last few years due in large part to its robust libraries. Perhaps more importantly, it’s
detailed documentation that provides developers with an in-depth understanding of how to use
its vast library of functions and how to test them, as well as a large suite of built in test cases and
functions. Through this documentation [28] [29], and understanding of java, we were able to
construct not only a metamorphic testing frame work for the Android platform, but also a parsing
algorithm to automatically check Android applications for testing functions, also known as test
case detection. This creation of these two tools was done by carefully taking advantage of some
known Android functions and repurposing them to generate an output that is useful to us.
The Android system inheres to the following frame work: In order for any application to
receive data from any device sensor, that application must ask for permission from the Android
operating system. This is done by calling the “RegisterListener” Function from Android’s API
(Application Programming Interface) [27]. This Function takes two parameters; the first is the name
of the object you would like thatsensor data forwarded back to. This name will be reused elsewhere
in the code to collect that particular type of sensor data. The second parameter is the type of sensor
data your application needs. This is important because smart phones today have a large assortment
of sensors ranging from GPS to microphones, this parameter specifies what senor data the
operating system forwards to the requesting application.](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-32-320.jpg)
![Once an application has sensor permission from the Android operating system we can
then use that object name to receive data. Within that object is another function from the Android
API called “onSensorChanged” [30]. Android uses this function to receive new values every time the
data changes. For example whenever your GPS location changes on your phone that GPS data is
sent to the onSensorChanged functions for all applications that currently have permission to access
the GPS sensor. Since all new sensor data is sent to this function, it is here where applications must
perform any and all computations on sensor data, as well as any tests. These tests and calculations
can either be done by native source code that is within onSensorChanged function itself, or there
may be other modular functions that are called upon to perform the calculation tasks for any given
application. This is also holds true for any tests or test functions that may exist. Figure 6 illustrates
how the Android frame work operates.
Figure 4.1 – Android Frame Work](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-33-320.jpg)

![4.1 Test Case Detection
Now that we understand the frame work that powers sensors, we can repurpose it to
evaluate ifsensor based Android applications are taking advantage of the testing libraries and tools
provided by the Android API. We can alsodetermine if the developers are implementing their own
testing methods; and if so what kind of testing are they implementing. In order to detect Android
tests cases for sensor applications we first need to determine if the app uses any sensor data from
the device itself. Mobile devices contain many sensors, but not all apps make use of them. For
example an application that keeps track of the number of steps you take throughout the day may
use a device’s accelerometer or GPS sensors to calculate steps. Whereas an application that simply
sends or receives messages (FaceBook for example) will make nouse of a device’s onboard sensors.
To extract this information from an application’s source code we used a SrcML.net [31] function
called GetDescendantsAndSelf<MethodCall>() [32]. When used this function parses through a given
source code looking for a specific function by name. In this case we are looking for the Android
function called getDefualtSensor [27]. By searching for this function, SrcML can return the type and
number of sensors any particular application is using. If there is no sensor in use we can skip that
application and continue parsing the next one. The code used to complete this task can be found
in appendix A.
Once we know that an application makes use of a device’s sensors, the next step is to check
if the application performs anyinternal test during or after anycalculations that may be performed
on the incoming inputdata from the sensors. For example the step counting application should test
itself to see if the desired output is being achieved when given a set of input sensor data. There are
two different types of testing scenario’s we are looking for. The first is to determine if any testing
is done utilizing Androids built-in testing library. The Android API comes with a variety of built-
in testing functions that can be used to test a wide range of Android’s functionalities. The second
scenario is locating developer created testing functions.
23](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-35-320.jpg)
![This is when a developer uses either traditional white box testing or some other testing strategy to
create his own test cases. The ultimate goal is to detect both developer created test functions and
Android’s built test functions, however the strategies used for detecting these two types are
drastically different.
4.1.1 Detecting Android API Tests
We will start with the easier of the two scenarios to detect; which is detecting test cases
that have been built into the Android API. Since we already know the names of the Android test
functions and what they do thanks to Android API documentation. From this we can determine
if a developer decides to use one of Android’s built in testing libraries. This is done much the
samewayfind the getDefaultSensor function,simplychangethenameof the keyword you’re
lookingfor duringthe parsingprocess.In this experimentwesearched forsix Android test
functions toseeif developers where takingadvantageofthesebuiltin tools. Thefull listof
Android tests we searched forcan befound below. We hypothesized thatdevelopers would
attempt to usethe provided testingmethods before buildingonefrom scratch.
4.1.2 List of Android API Tests searched for
∑ ActivityUnitTestCase - This class provides isolated testing of a single activity. The
activity under test will be created with minimal connection to the system infrastructure,
and you can inject mocked or nested versions of many of Activity's dependencies [27].
∑ ServiceTestCase - This test case provides a framework in which you can test Service
classes in a controlled environment. It provides basic support for the lifecycle of a
Service, and hooks with which you can inject various dependencies and control the
environment in which your Service is tested [27].
24](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-36-320.jpg)
![∑ ApplicationTestCase - This test case provides a framework in which you can test
Application classes in a controlled environment. It provides basic support for the
lifecycle of an Application, and hooks by which you can inject various dependencies and
control the environment in which your Application is tested [27].
∑ ProviderTestCase2 - This test case class provides a framework for testing a single
Content Provider and for testing your app code with an isolated content provider.
Instead of using the system map of providers that is based on the manifests of other
applications, the test case creates its own internal map. It then uses this map to
resolve providers given an authority. This allows you to inject test providers and to
null out providers that you do not want to use [27].
∑ LoaderTestCase - A convenience class for testing Loaders. This test case provides a
simple way to synchronously get the result from a Loader making it easy to assert that
the Loader returns the expected result [27].
∑ ActivityInstrumentationTestCase2 - this class provides functional testing of a single
activity. The activity under test will be created using the system infrastructure (by calling
InstrumentationTestCase.launchActivity()) and you will then be able to manipulate your
Activity directly [27].
4.1.3 Detecting Developer Created Tests
To find developer created test cases we set the parsing algorithm to search for the
onSensorChanged function, the exact same way we search for the getDefualtSensor function. We
know that the onSensorChanged function is were all Android applications receive incoming sensor
data from the Android operating system, finding this function is the first step in detecting any
developer created tests that may exist.
There are two ways a developer can implement a testing function within the
onSensorChanged function. Either the testing source code and, or testing function, can exist
natively with in the onSensorChanged function itself (referred to as a t1 test case). Or embed into
another function outside of onSensorChanged, which performs the calculations on the sensor data,
and then later called by that calculation function to perfume testing (referred to as a t2 test case).
The t1 test case is the simpler of the two. The calculations are done within
the onSensorChanged function either by performing source code calculations native to
25](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-37-320.jpg)


![Figure 4.4 – Caller Method
4.1.4 Test Case Detection Procedure
We used Microsoft Visual Studio with a SrcML.net plugin to program the source code that
powers our parsingprogram. We then applied the algorithm to a body of thirty sensor driven open
source Android applications downloaded from repositories such as GitHub [33]. The complete list
of applications and their download sources can be found in Appendix B. All applications were
downloaded and stored in a single folder that would serve as a root directory, or starting point, for
our algorithm. To execute the program we used Visual Studios’ “Run Tests” feature, at which time
the program would display sensortypes, implementations of onSensorChanged, as well the children
functions for onSensorChanged for each application stored within the root directory. Figure 4.5 is an
example output displayed after the program has completed.
28](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-40-320.jpg)
![Figure 4.5 – Parsing Algorithm Output
4.2 Data Collection (SenSee)
SenSee is an Android application created by Virginia State staff and students using the
same rules applied for test case detection [34]. The basic principle behind SenSee is to allow a user
to perform a series of actions or tasks using Android sensor data, while at the same time allowing
him or her to record and tag those actions in order to provide some ground truth for the data that
is being collected. We used it to establish the number of steps actually taken by an individual
during our evaluation of a pedometer application. Using the SenSee’s tag feature we were able to
identify where each step or set of steps accrued when evaluating the sensor data, and thus
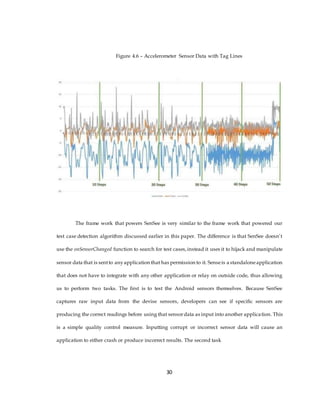
effectively eliminating the oracle problem. Figure 4.6 below illustrates the real world step tags
recorded when collecting sensor data.
29](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-41-320.jpg)









![CHAPTER 5 – EVALUATION
5.0 Study Recap
Over the course of this endeavor he have created several unique tools and methodologies
for Android developers to find and create test cases for any given sensor driven applications.Our
objective was to determine what testing strategies are being deployed by indie developers today,
as well as conclude if metamorphic testing is possible on Android platforms, and if so evaluate is
effectiveness. The final evaluation of these systems is outlined below.
5.1 Test Case Detection Results
After applying our parsing algorithm to a body of thirty open source applications, we
found that all most all of them fail to perform some sort of internal testing. The complete results
sheet of this analysis cabbe found in Appendix C. Only three Android created test casewere found,
as well as 3 user defined test cases. All six of the detected test cases were located amongst three
application. Thus only 10% of the applications we tested contained some sort of internal testing
functionality. This may be due to the fact that our pool of applications are in fact open source. If
we applied out algorithm to a body of paid closed source applications such as “FaceBook” or
“Clash of Clans”, my hypotheses is that we would detect far more internal test case.
To further validate our results we compared our finding to that of a much larger test case
detection study conducted at Singapore Management University [35]. Using a pool of over 600](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-52-320.jpg)
![Android applications collect from 2 online repositories, F-Droid [37] and GitHub [33], these
researchers concluded that only 14% of the applications evaluated contained test cases. These](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-53-320.jpg)








![CHAPTER 6 - SUMMARY
6.0 Summary
As our technological advances increase, new problems will arise for which there is no
current answer. As these problems grow in sizeand complexity, so too will the computer programs
needed to compute them, but with this growth comes the possibility for more software errors.
Developing new tests to detect these errors will become more and more difficult on an exponential
scale, but perhaps Edsger W. Dijkstra but it best by stating “Program testing can be used to show
the presence of bugs, but never to show their absence” [12]. Creating a perfect program is nearly
impossible, but if testing advanced testing metrics like metamorphic testing we can get pretty close.
There has been many advances in the field of static error detection, programs with known inputs
and outputs. These advance include methods like symbolic execution and model checking, even
winning a Turing Award in 2007 [35], but there has be relatively little advancement in dynamic
error detection. As we rely more on computer systems to calculate more complex unknowns, the
testing metrics used to evaluate these systems must also evolve. Problems such as the oracle
problem will be key if we hope to produce reliable independent software.
Our objective was to evaluate and provide a means which Android developers may use
to better their applications through the use of metamorphic testing. This study concluded that
metamorphic testing is not only possible but feasible, and provided a means to universally apply
it to all sensor based Android applications.](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-62-320.jpg)

![APPENDIX A – Parsing Algorithm Code
namespace CodeAnalysisToolkit
{
[TestFixture]
public class SimpleAnalyticsCalculator_Thesis
{
//------Test Case Class---------------------------------------------------
[TestCase]
public void CalculateSimpleProjectStats()
{
int NumOfApps = 30;
//-----------Current Working Method to Get sub directories -----------
// Get list of files in the specific directory.
string[] TopDirectories = Directory.GetDirectories(@"C:SchoolGrad
School (Comp Sci)ThesisApps",
"*.*",
SearchOption.TopDirectoryOnly);
// Display all the files.
//for (int i = 0; i <= NumOfApps; i++)
//{
// Console.WriteLine(TopDirectories[i]);
//}
//Print out all Top Sub Directoies for Specified
Path //foreach (string file in TopDirectories)
//{
// Console.WriteLine(file);
//}
//----------End of Print Sub directory Method-------------------------
for (int i = 0; i < NumOfApps; i++)
{
var dataProject = new
DataProject<CompleteWorkingSet>(TopDirectories[i],
Path.GetFullPath(TopDirectories[i]),
"..//..//..//SrcML");
Console.WriteLine();
Debug.WriteLine("#############################################");
Debug.WriteLine("Parsing " + TopDirectories[i]);
dataProject.UpdateAsync().Wait();
51](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-64-320.jpg)
















![BIBLIOGRAPHY
[1]T. Chen, S. Cheung and S. Yiu, Metamorphic Testing: A New Approach for Generating Next Test
Cases. Hong Kong: Department of Computer Science Hong Kong University, 1998.
[2]G. Kaiser and F. Su, 'Finding Bugs in Machine Learning, Data Mining and Big Data Applications |
Programming Systems Laboratory', Psl.cs.columbia.edu, 2015.[Online]. Available:
http://www.psl.cs.columbia.edu/64/metamorphic-testing/. [Accessed: 17- May- 2015].
[3] Istqbexamcertification.com, 'What is Software Testing?', 2015.[Online]. Available:
http://istqbexamcertification.com/what-is-a-software-testing/. [Accessed: 06- May- 2015].
[4] Istqbexamcertification.com, 'What is Test design? or How to specify test cases?', 2015.[Online].
Available: http://istqbexamcertification.com/what-is-test-design-or-how-to-specify-test-cases/.
[Accessed: 10- May- 2015].
[5]E. Barr, M. Harman, P. McMinn, M. Shahbaz and S. Yoo, The Oracle Problem in Software Testing:
A Survey. IEEE TRANSACTIONS ON SOFTWARE ENG, 2015.
[6]J. King, Symbolic Execution and Program Testing. IBM Thomas J. Watson Research Center, 1976.
[7] Msdn.microsoft.com, 'Unit Testing', 2015. [Online]. Available: https://msdn.microsoft.com/en-
us/library/Aa292197%28v=VS.71%29.aspx.[Accessed:19-May-2015].
[8] agile.csc.ncsu.edu,'White-Box Testing',2015.[Online].Available:
http://agile.csc.ncsu.edu/SEMaterials/WhiteBox.pdf.[Accessed:23-May-2015].
[9]S. Webmaster, 'What is Simulation - Simulation Software Explained', Simul8.com, 2015.[Online].
Available: http://www.simul8.com/products/what_is_simulation.htm. [Accessed: 17- Jul- 2015].
72](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-82-320.jpg)
![[10] Softwaretestinghelp.com, 'What is Integration Testing and How It is Performed? — Software Testing
Help', 2015.[Online]. Available: http://www.softwaretestinghelp.com/what-is-integration-testing.
[Accessed: 20- Jun- 2015].
[11]C. Pasareanu, 'Symbolic Execution and Model Checking for Testing', YouTube, 2015.[Online].
Available: https://www.youtube.com/watch?v=azTVEwxN8zM. [Accessed: 02- Jun- 2015].
[12]E. Dijkstra, 'E.W. Dijkstra Archive: Structured programming (EWD268)', Cs.utexas.edu, 2015. [Online].
Available: https://www.cs.utexas.edu/users/EWD/transcriptions/EWD02xx/EWD268.html. [Accessed:
10- Jun- 2015].
[13]P. Boonstoppel, C. Cadar and D. Engler, Attacking Path Explosion in Constraint-Based Test Generation.
Computer Systems Laboratory, Stanford University.
[14]M. Chair, P. Schaumont and P. Plassmann, Strategies for Scalable Symbolic Execution-based Test
Generation. Blacksburg, Virginia: Virginia Polytechnic Institute and State University Department
of Computer Engineering, 2010.
[15]G. Tassey, The Economic Impacts of Inadequate Infrastructure for Software Testing. Gaithersburg:
National Institute of Standards and Technology, 2002.
[16] J. Burnim and K. Sen, Heuristics for Scalable Dynamic Test Generation," in Automated
Software Engineering, 2008.ASE 2008.23rd IEEE/ACM International Conference on,
pp. 443{446,September 2008.
[17] Cs.cmu.edu, 'Model Checking at CMU', 2015. [Online]. Available:
https://www.cs.cmu.edu/~modelcheck/.[Accessed:20-Jun-2015].
[18]X. Xie, J. Ho, C. Murphy, G. Kaiser, B. Xu and T. Chen, Testing and Validating Machine Learning
Classifiers by Metamorphic Testing. National Institutes of Health, 2011.
[19]A. Smola and S. Vishwanathan, INTRODUCTION TO MACHINE LEARNING. University of
Cambridge, 2008.
73](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-83-320.jpg)
![[20]Z. Zhou, D. Huang, T. Tse, Z. Yang, H. Huang and T. Chen, Metamorphic Testing and Its
Applications. Hong Kong: International Symposium on Future Software Technology, 2004.
[21] The Independent, '42: The answer to life, the universe and everything', 2011. [Online]. Available:
http://www.independent.co.uk/life-style/history/42-the-answer-to-life-the-universe-and-
everything-2205734.html. [Accessed: 20- Jul- 2015].
[22] Compliantmechanisms.byu.edu, 'Introduction to Microelectromechanical Systems (MEMS) |
Compliant Mechanisms', 2015.[Online]. Available:
https://compliantmechanisms.byu.edu/content/introduction-microelectromechanical-systems-mems.
[Accessed: 20- Jul- 2015].
[23]N. Zhoa, Full-Featured Pedometer Design Realized with 3-Axis Digital Accelerometer.
[24]D. Beyer, T. Henzinger and G. Theoduloz, Program Analysis with Dynamic Precision Adjustment. 2015.
[25]M. Harrold, J. Offutt and K. Tewary, An Approach to Fault Modeling and Fault Seeding Using the
Program Dependence Graph.
[26]F. Grigorjev, N. Lascano and J. Staude, A Fault Seeding Experience. Motorola Global Software Group.
[27] Developer.Android.com, 'SensorManager | Android Developers', 2015.[Online]. Available:
http://developer.Android.com/reference/Android/hardware/SensorManager.html. [Accessed: 20-
Jul-2015].
[28]T. Fundamentals, 'Testing Fundamentals | Android Developers', Developer.Android.com, 2015.
[Online]. Available: http://developer.Android.com/tools/testing/testing_Android.html. [Accessed:
23-Jun- 2015].
[29] Vogella.com, 'Android application testing with the Android test framework - Tutorial', 2015.
[Online]. Available: http://www.vogella.com/tutorials/AndroidTesting/article.html. [Accessed:
25-Jun- 2015].
74](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-84-320.jpg)
![[30] Developer.Android.com, 'SensorEventListener | Android Developers', 2015. [Online]. Available:
http://developer.Android.com/reference/Android/hardware/SensorEventListener.html. [Accessed:
20-Jul- 2015].
[31] Srcml.org, 'What is SrcML.Net', 2015.[Online]. Available: http://www.srcml.org/about-srcml.html.
[Accessed: 20- Jul- 2015].
[32] GitHub, 'abb-iss/SrcML.NET', 2014.[Online]. Available: https://github.com/abb-
iss/SrcML.NET/blob/master/ABB.SrcML.Data.Test/CodeParserTests.cs. [Accessed: 20- Jul- 2015].
[33] GitHub, 'Build software better, together', 2015. [Online]. Available: https://github.com/. [Accessed:
20- Jul- 2015].
[34] SenSee Application, 2015.[Online]. Available:
https://play.google.com/store/apps/details?id=sysnetlab.Android.sdc&hl=en. [Accessed: 20-
Mar-2015].
[35] Amturing.acm.org, 'Edmund Clarke - A.M. Turing Award Winner', 2015. [Online]. Available:
http://amturing.acm.org/award_winners/clarke_1167964.cfm.[Accessed:03-Jul-2015].
[36]P. Kochhar, F. Thung, N. Nagappan, T. Zimmermann and D. Lo, Understanding the Test Automation
Culture of App Developers. Singapore Management University, 2015.
[37] F-droid.org, 'F-Droid | Free and Open Source Android App Repository', 2015. [Online]. Available:
https://f-droid.org/. [Accessed: 23- Jul- 2015].
75](https://image.slidesharecdn.com/618feda7-6e9d-434a-8f37-5d343cd980f6-160215012742/85/Final-Draft-3-Thesis-v3-Post-Defense-85-320.jpg)