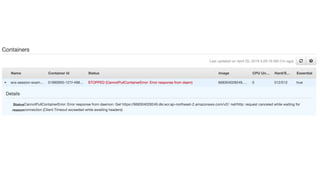
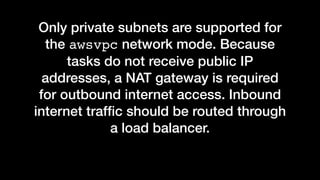
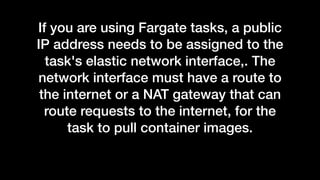
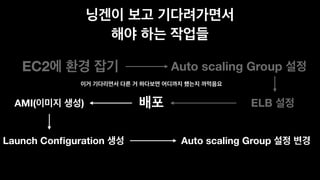
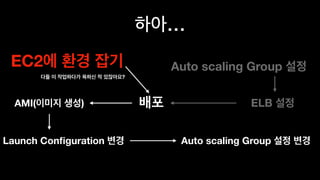
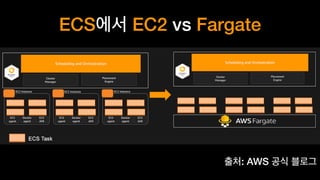
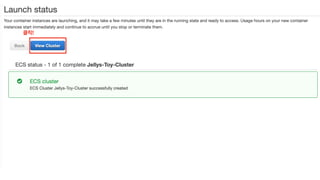
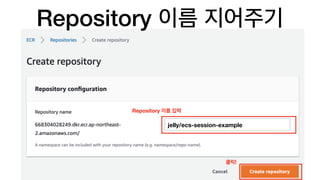
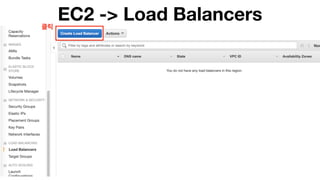
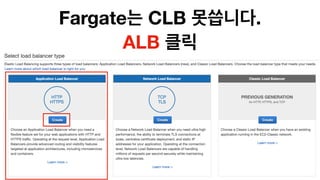
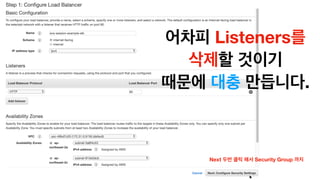
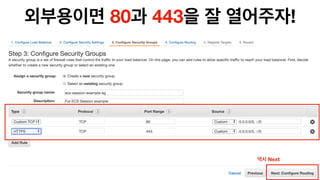
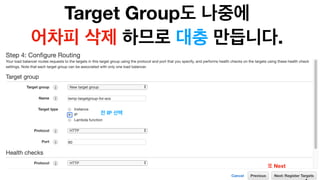
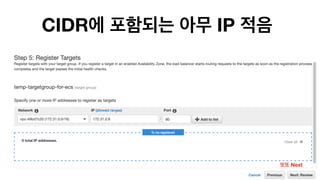
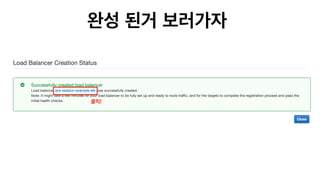
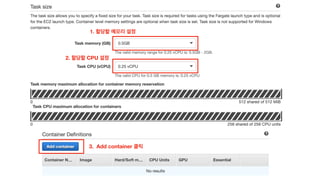
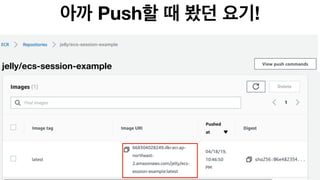
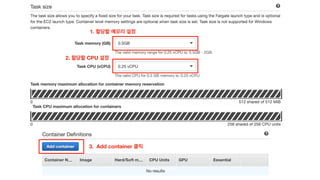
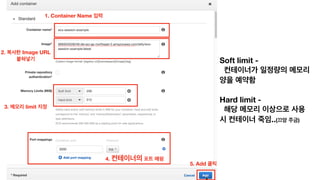
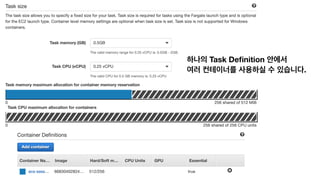
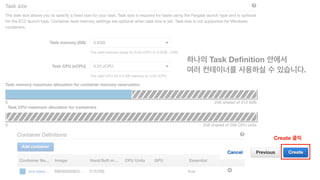
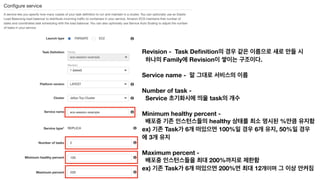
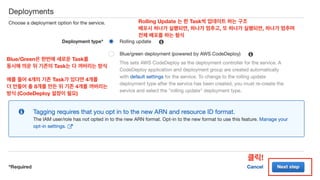
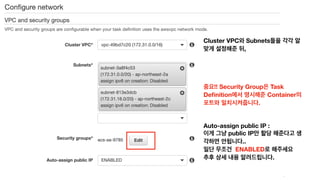
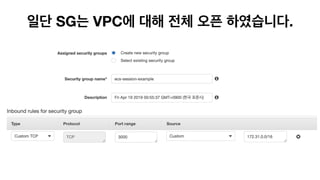
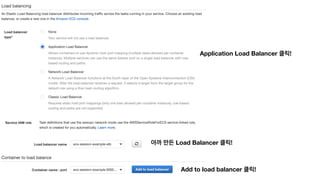
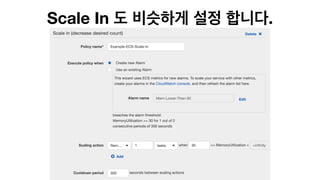
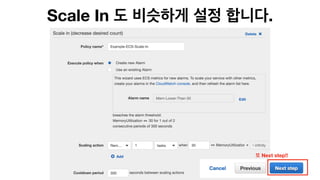
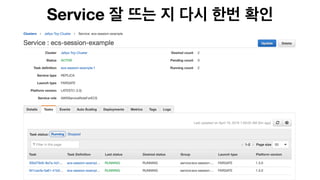
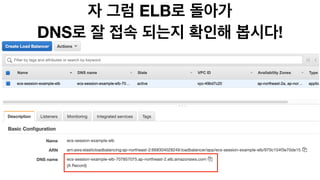
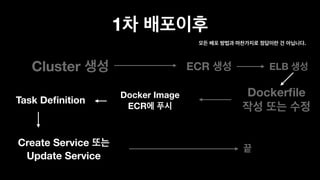
The document discusses the implementation of AWS ECS with Fargate and EC2, focusing on deployment strategies, auto-scaling, and configuring Nginx as a reverse proxy. It includes technical details related to task definitions, load balancers, network configurations, and Docker setup, while providing examples of server configurations. The content also emphasizes the need for proper routing and NAT gateway setups for Fargate tasks to access the internet.

















































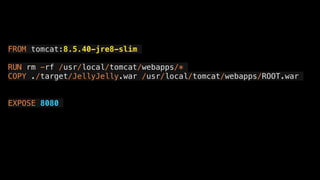

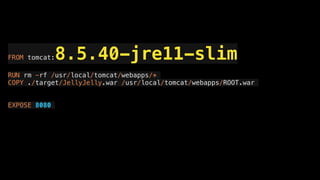







































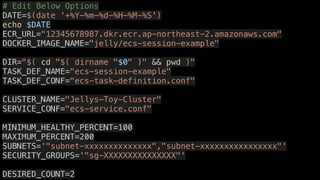
![{
"cluster": "CLUSTER_NAME",
"service": "TASK_DEF_NAME",
"desiredCount": DESIRED_COUNT,
"taskDefinition": "TASK_DEF_NAME",
"deploymentConfiguration": {
"maximumPercent": MAXIMUM_PERCENT,
"minimumHealthyPercent": MINIMUM_HEALTHY_PERCENT
},
"networkConfiguration": {
"awsvpcConfiguration": {
"subnets": [
SUBNETS
],
"securityGroups": [
SECURITY_GROUPS
],
"assignPublicIp": "DISABLED"
}
},
"forceNewDeployment": false,
"healthCheckGracePeriodSeconds": 0
}
{
"executionRoleArn": "arn:aws:iam::*******************
"containerDefinitions": [
{
"logConfiguration": {
"logDriver": "awslogs",
"options": {
"awslogs-group": "/ecs/TASK_DEF_NAME",
"awslogs-region": "ap-northeast-2",
"awslogs-stream-prefix": "ecs"
}
},
"portMappings": [
{
"hostPort": 3000,
"protocol": "tcp",
"containerPort": 3000
}
],
"cpu": 0,
"environment": [],
"mountPoints": [],
"memory": 512,
"memoryReservation": 512,
"volumesFrom": [],
"image": "DOCKER_IMAGE_NAME",
"name": "TASK_DEF_NAME"
}
],
"placementConstraints": [],
"memory": "512",
"family": "TASK_DEF_NAME",
"requiresCompatibilities": [
"FARGATE"
],
"networkMode": "awsvpc",
"cpu": "256",
"volumes": []
}](https://image.slidesharecdn.com/lh9gleecswithvpc1-190420112143/85/Fargate-ECS-with-VPC-1-157-320.jpg)