Recommended
PPTX
panw-cortex-xdr-customer-presentation.pptx
PPTX
Kaspersky Next XDR Expert Product Presentation 1909 EN.pptx
PPTX
EDR vs XDR Understanding the Key Differences and Choosing the Right Solution....
PDF
Cybersecurity leaders guide to xdr for business
PDF
Understanding XDR Solutions: The Future of Cybersecurity
DOCX
Strengthening Security with Extended Detection and Response.docx
PDF
What is network detection and response.pdf
PPTX
ebook - Supercharge your security operations with XDR_AUG 2023_.pptx by Ashis...
PDF
Extended Detection and Response (XDR)�An Overhyped Product Category With Ulti...
PDF
a comparison between SIEM versus XDR.pdf
PDF
Maximizing SOC Benefits with XDR A Game-Changer for Cybersecurity
PDF
What Is Network Detection and Response (NDR)
PDF
Unifica la seguridad de tus operaciones con la plataforma de Cortex XDR
PDF
The Future of Endpoint Detection and Response (EDR) Trends to Watch
PPTX
Detection & Response for Network Security.pptx
PPTX
Understanding Endpoint Security in a SOC
PDF
Top 10 XDR Solutions in India (2025).pdf
PPTX
Understanding Endpoint Detection and Response (EDR)
PDF
Why Should Organizations Consider Extended Detection and Response (XDR)?
PDF
Empowering Cyber Resilience with Seqrite XDR: The Future of Data Privacy & Th...
PDF
xddsfinalGFGSFDGFDGSDFFGFGFGFGFGFGFGFGFGFGFGFG
PDF
Enhancing Cybersecurity with Network Detection and Response (NDR) Technology
PPTX
The Best Just Got Better, Intercept X Now With EDR
PDF
Managed Extended Detection and Response.pdf
PDF
Opentext Managed XDR paves the way for CyberResilience
PDF
Extended Detection & Response Services in India - Senselearner
PDF
2022 APIsecure_Monitoring your APIs for Attacks Using SIEM versus XDR
PDF
A Buyers Guide to Investing in Endpoint Detection and Response for Enterprise...
DOCX
TOXICITY AND ITS MANAGEMENT 6th sem unit 5, PHARMACOLOGY-III B. PHARMACY
PPTX
MACSYMA introduction,working,application
More Related Content
PPTX
panw-cortex-xdr-customer-presentation.pptx
PPTX
Kaspersky Next XDR Expert Product Presentation 1909 EN.pptx
PPTX
EDR vs XDR Understanding the Key Differences and Choosing the Right Solution....
PDF
Cybersecurity leaders guide to xdr for business
PDF
Understanding XDR Solutions: The Future of Cybersecurity
DOCX
Strengthening Security with Extended Detection and Response.docx
PDF
What is network detection and response.pdf
PPTX
ebook - Supercharge your security operations with XDR_AUG 2023_.pptx by Ashis...
Similar to Extending Detection & Response (XDR)V2.pptx
PDF
Extended Detection and Response (XDR)�An Overhyped Product Category With Ulti...
PDF
a comparison between SIEM versus XDR.pdf
PDF
Maximizing SOC Benefits with XDR A Game-Changer for Cybersecurity
PDF
What Is Network Detection and Response (NDR)
PDF
Unifica la seguridad de tus operaciones con la plataforma de Cortex XDR
PDF
The Future of Endpoint Detection and Response (EDR) Trends to Watch
PPTX
Detection & Response for Network Security.pptx
PPTX
Understanding Endpoint Security in a SOC
PDF
Top 10 XDR Solutions in India (2025).pdf
PPTX
Understanding Endpoint Detection and Response (EDR)
PDF
Why Should Organizations Consider Extended Detection and Response (XDR)?
PDF
Empowering Cyber Resilience with Seqrite XDR: The Future of Data Privacy & Th...
PDF
xddsfinalGFGSFDGFDGSDFFGFGFGFGFGFGFGFGFGFGFGFG
PDF
Enhancing Cybersecurity with Network Detection and Response (NDR) Technology
PPTX
The Best Just Got Better, Intercept X Now With EDR
PDF
Managed Extended Detection and Response.pdf
PDF
Opentext Managed XDR paves the way for CyberResilience
PDF
Extended Detection & Response Services in India - Senselearner
PDF
2022 APIsecure_Monitoring your APIs for Attacks Using SIEM versus XDR
PDF
A Buyers Guide to Investing in Endpoint Detection and Response for Enterprise...
Recently uploaded
DOCX
TOXICITY AND ITS MANAGEMENT 6th sem unit 5, PHARMACOLOGY-III B. PHARMACY
PPTX
MACSYMA introduction,working,application
PPTX
CROP RESIDUE MANAGEMANT AND ITS EFFECT ON SOIL HEALTH
PPTX
How to Automate Quality Checks in Odoo 18 Quality App
PDF
Prescription Writing- Elements, Parts, and Exercises
PPTX
CLASS -9 POLITICAL SCIENCE PPT CHAPTER -5 DEMOCRATIC RIGHTS.pptx
PDF
The Pity of War: Form, Fragment, and the Artificial Echo | Understanding War ...
PDF
Projecte de la porta de primer B: L'antic Egipte
PPTX
Unit I — General Physiology: Basic Concepts
PDF
Types of Vegetable Gardens, College of Agriculture Balaghat.pdf
PPTX
SOCIAL SYSTEM.......................pptx
PDF
NAVIGATE PHARMACY CAREER OPPORTUNITIES.pdf
PPTX
15 December 2025 Education for human flourishing Michael Stevenson .pptx
PDF
Projecte de la porta d'i5B: Els animals marins
PDF
FAMILY ASSESSMENT FORMAT - CHN practical
PDF
Principles and Practices of GST 2.0 Study material
PDF
The Drift Principle: When Information Accelerates Faster Than Minds Can Compress
PPTX
Pain. definition, causes, factor influencing pain & pain assessment.pptx
PDF
Unit-III pdf (Basic listening Skill, Effective Writing Communication & Writin...
PDF
Models of Teaching - TNTEU - B.Ed I Semester - Teaching and Learning - BD1TL ...
Extending Detection & Response (XDR)V2.pptx 1. Extending Detection & Response
(XDR)
Driving Cyber Resilience in a Zero
Trust World
Prepared by: [Your Name]
2. The Story Hook
• Current Reality:
• - SOC teams overwhelmed by thousands of
alerts daily
• - Tools are siloed (endpoint, email, cloud,
network)
• - Breach dwell time still averages 200+ days
• Message: Threats slip through the cracks
without context and correlation.
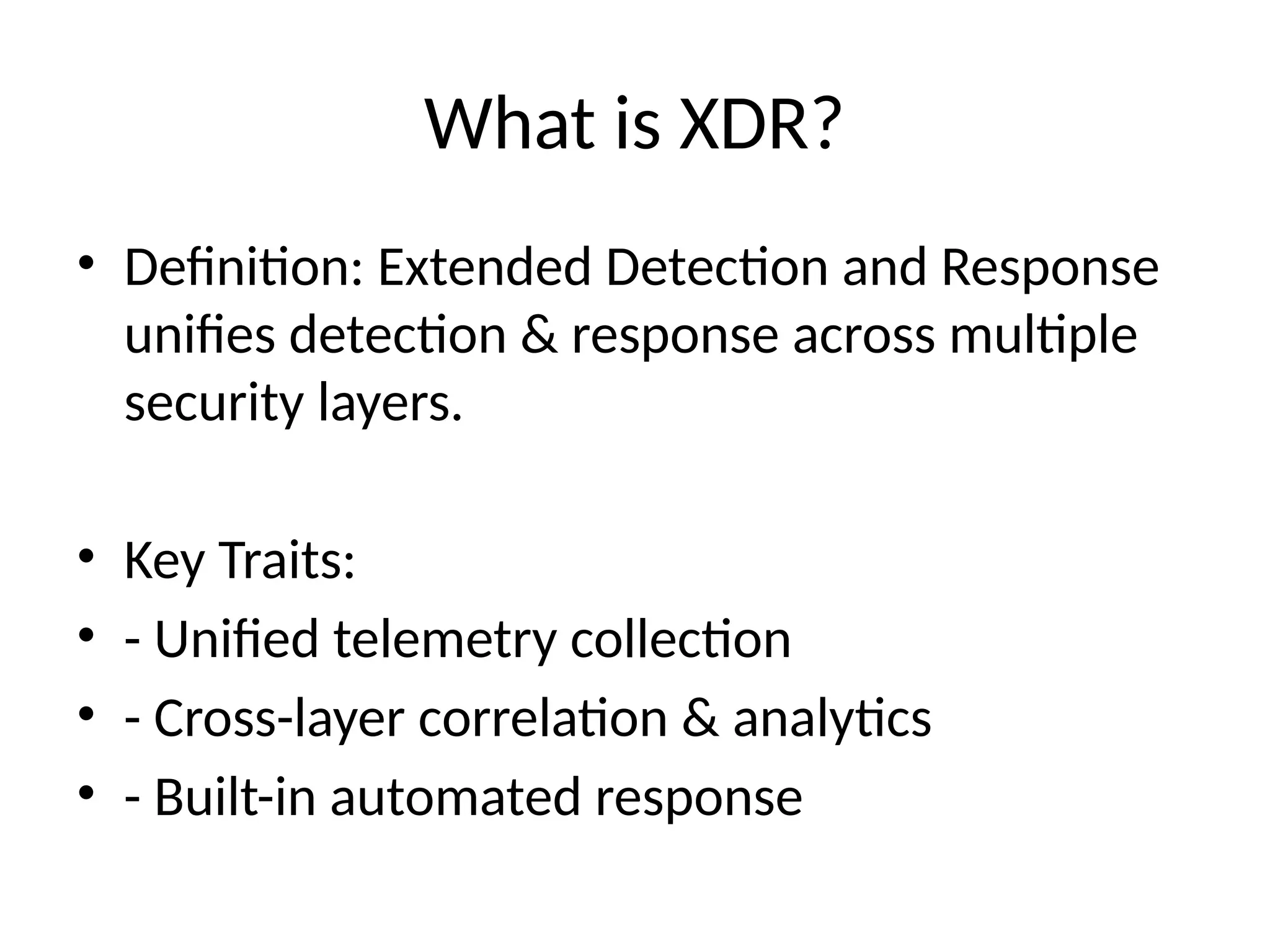
3. What is XDR?
• Definition: Extended Detection and Response
unifies detection & response across multiple
security layers.
• Key Traits:
• - Unified telemetry collection
• - Cross-layer correlation & analytics
• - Built-in automated response
4. Why XDR?
• Customer Challenges:
• - Alert fatigue
• - Lack of visibility across attack vectors
• - Slower detection & response
• XDR Value:
• - 90% faster detection
• - Reduce false positives
• - 360° visibility
5. How XDR Works
• Flow:
• 1. Data sources: Endpoint, Email, Network,
Cloud
• 2. Correlation: AI/ML, threat intel, behavioral
analytics
• 3. Response: Isolation, blocking, automated
playbooks
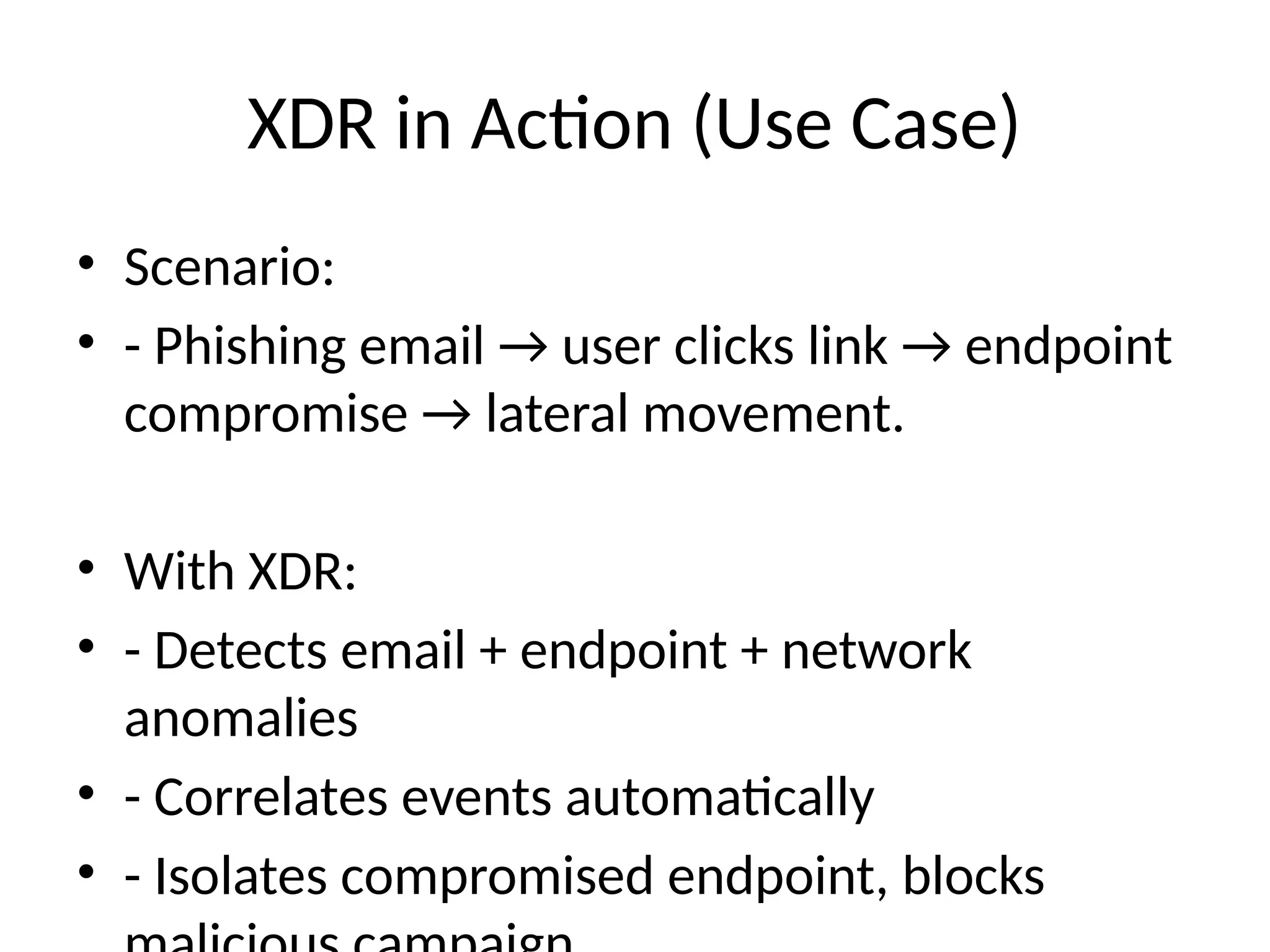
6. XDR in Action (Use Case)
• Scenario:
• - Phishing email → user clicks link → endpoint
compromise → lateral movement.
• With XDR:
• - Detects email + endpoint + network
anomalies
• - Correlates events automatically
• - Isolates compromised endpoint, blocks
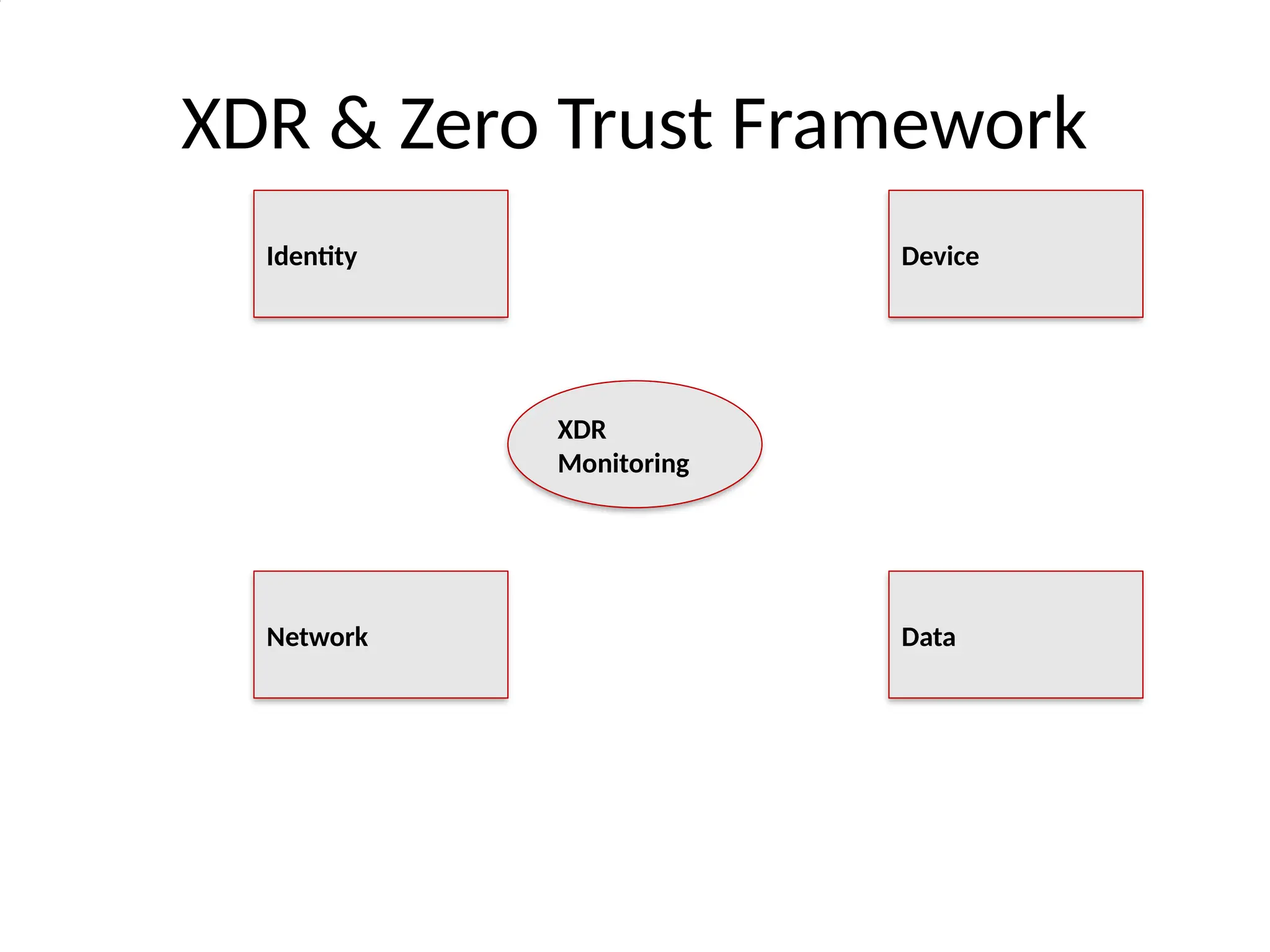
7. XDR & Zero Trust
• Zero Trust Principles:
• - Never trust, always verify
• - Assume breach
• How XDR Supports:
• - Continuous monitoring & verification
• - Cross-vector analytics validate every access
• - Automated containment enforces least
privilege
8. Business Outcomes
• - Reduced dwell time (days → hours)
• - SOC efficiency (alert reduction, context-rich
investigations)
• - Stronger Zero Trust alignment
• - Optimized cost (fewer point products)
9. Call to Action
• Message:
• XDR enables enterprises to move from
reactive firefighting to proactive defense,
accelerating their Zero Trust journey.
• Thank You
• Q&A
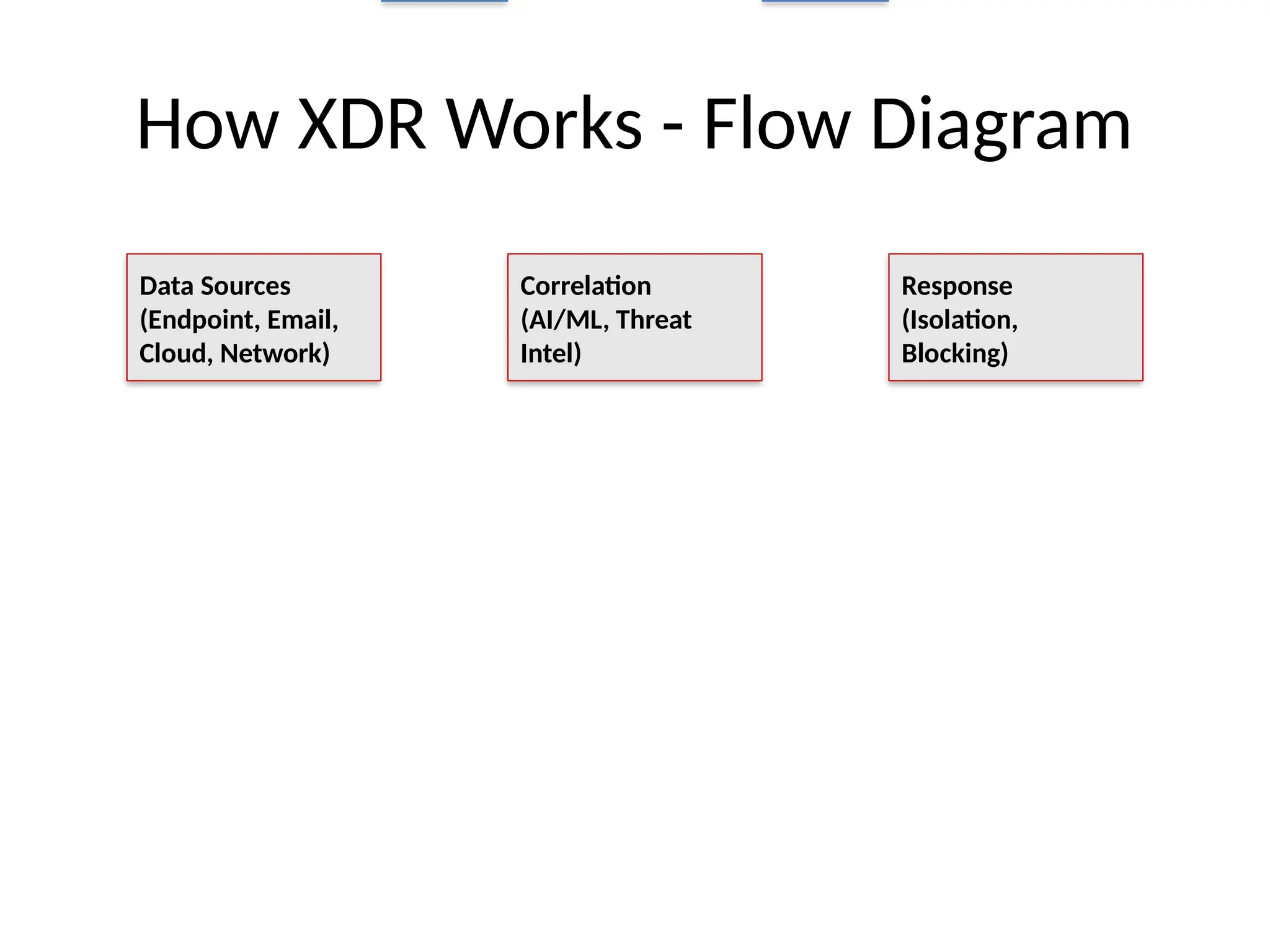
10. How XDR Works - Flow Diagram
Data Sources
(Endpoint, Email,
Cloud, Network)
Correlation
(AI/ML, Threat
Intel)
Response
(Isolation,
Blocking)
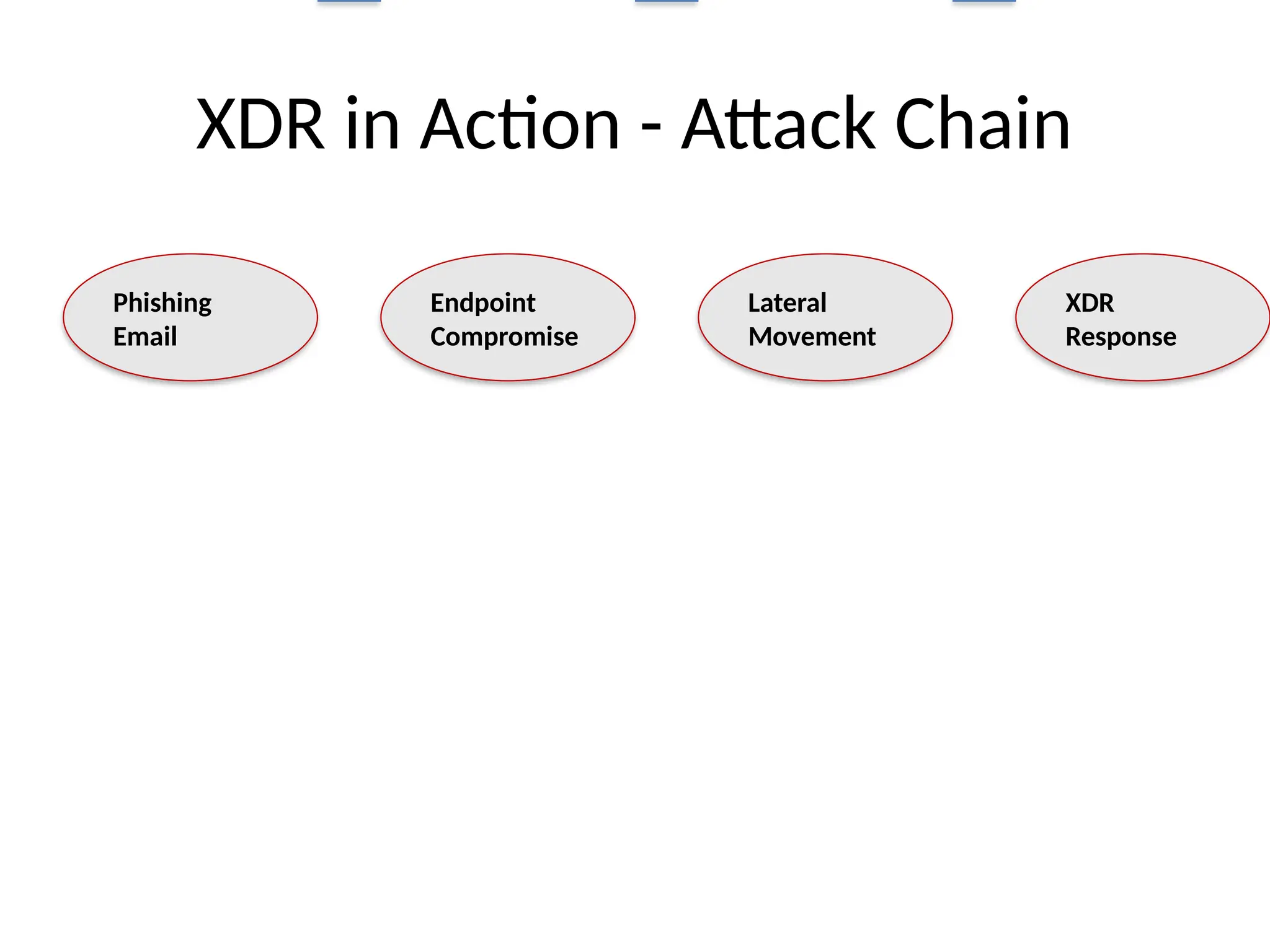
11. XDR in Action - Attack Chain
Phishing
Email
Endpoint
Compromise
Lateral
Movement
XDR
Response
12. XDR & Zero Trust Framework
XDR
Monitoring
Identity Device
Network Data
![Extending Detection & Response
(XDR)
Driving Cyber Resilience in a Zero
Trust World
Prepared by: [Your Name]](https://image.slidesharecdn.com/extendingdetectionresponsexdrv2-250913093117-a7e645fb/75/Extending-Detection-Response-XDR-V2-pptx-1-2048.jpg)