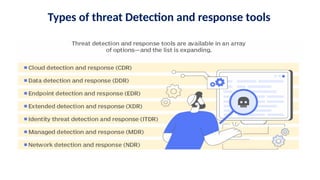
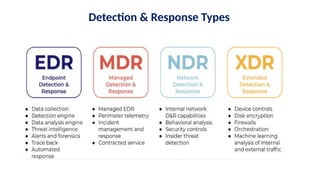
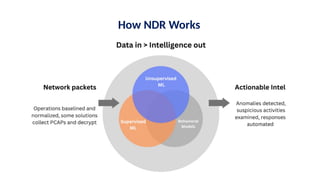
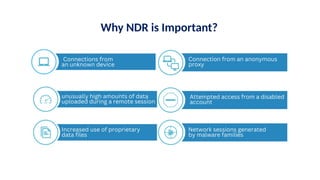
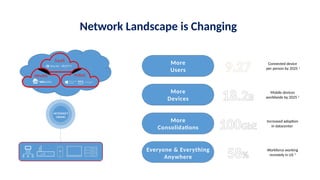
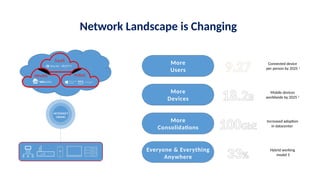
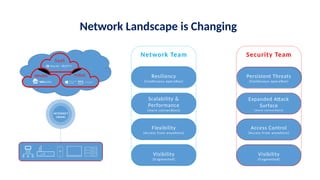
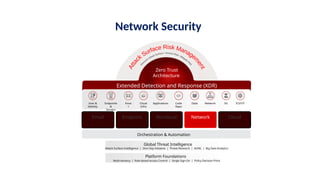
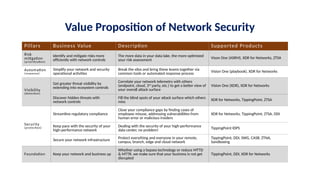
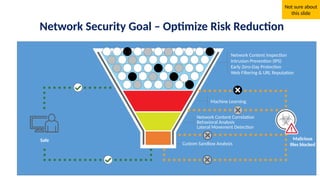
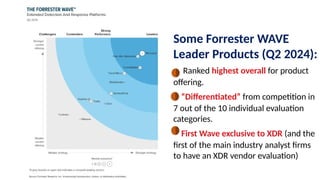
The document discusses the importance and mechanisms of Network Detection and Response (NDR) in addressing cybersecurity threats amidst a rapidly changing network landscape. It emphasizes the need for enhanced visibility, threat detection, and efficient risk mitigation through integrated security solutions. The content also highlights the intricacies of managing security across diverse environments, including on-premises, cloud, and hybrid systems.