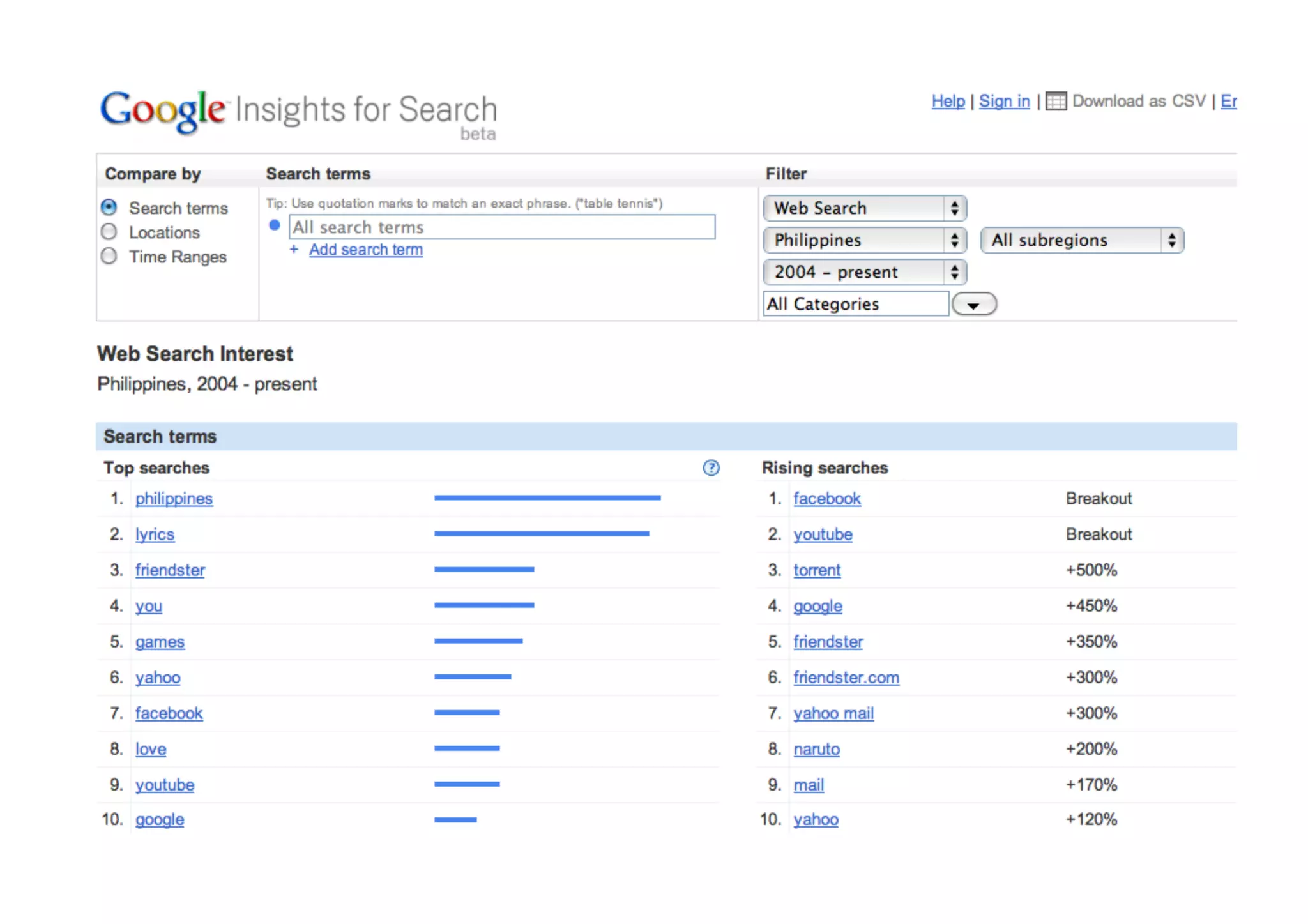
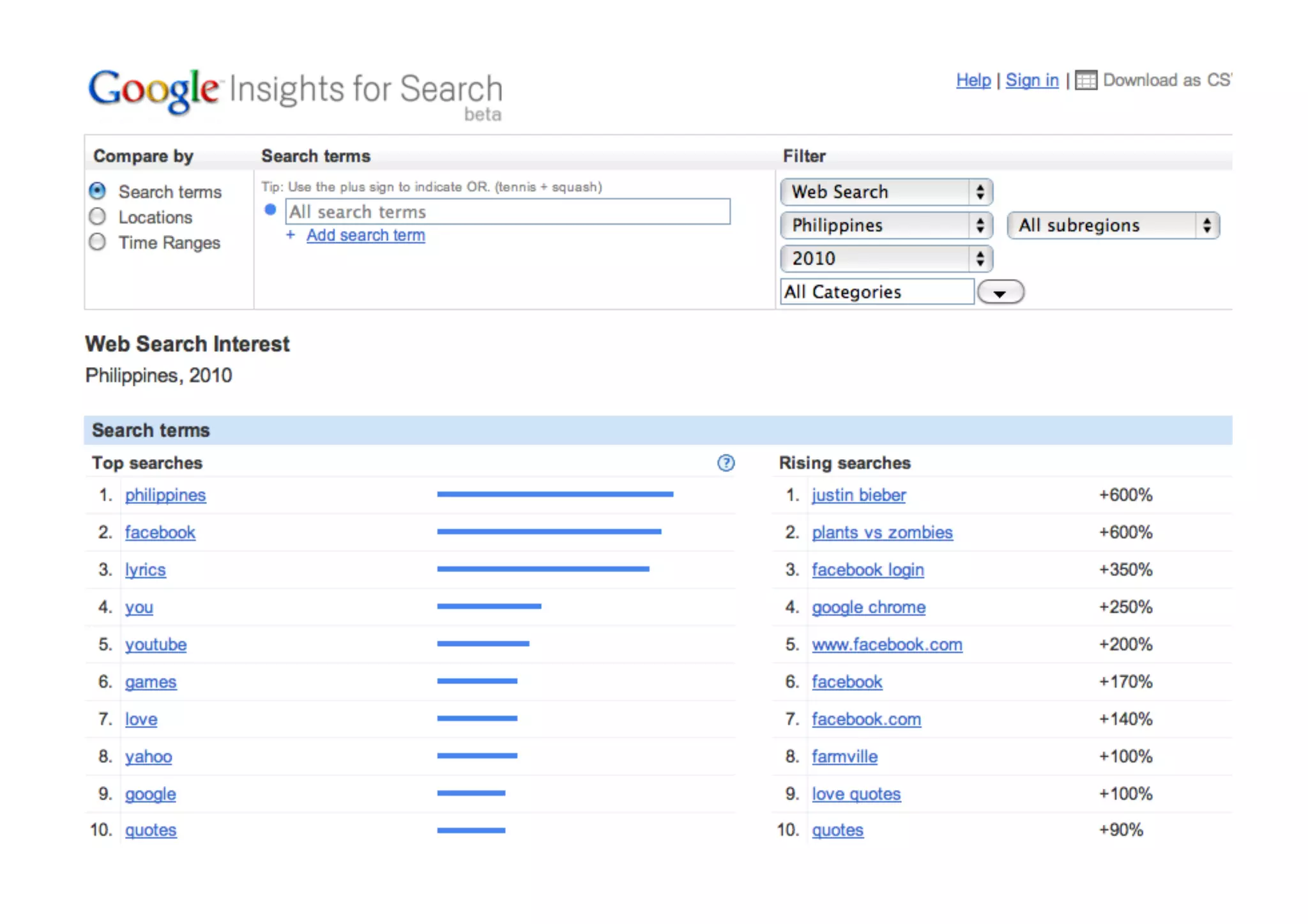
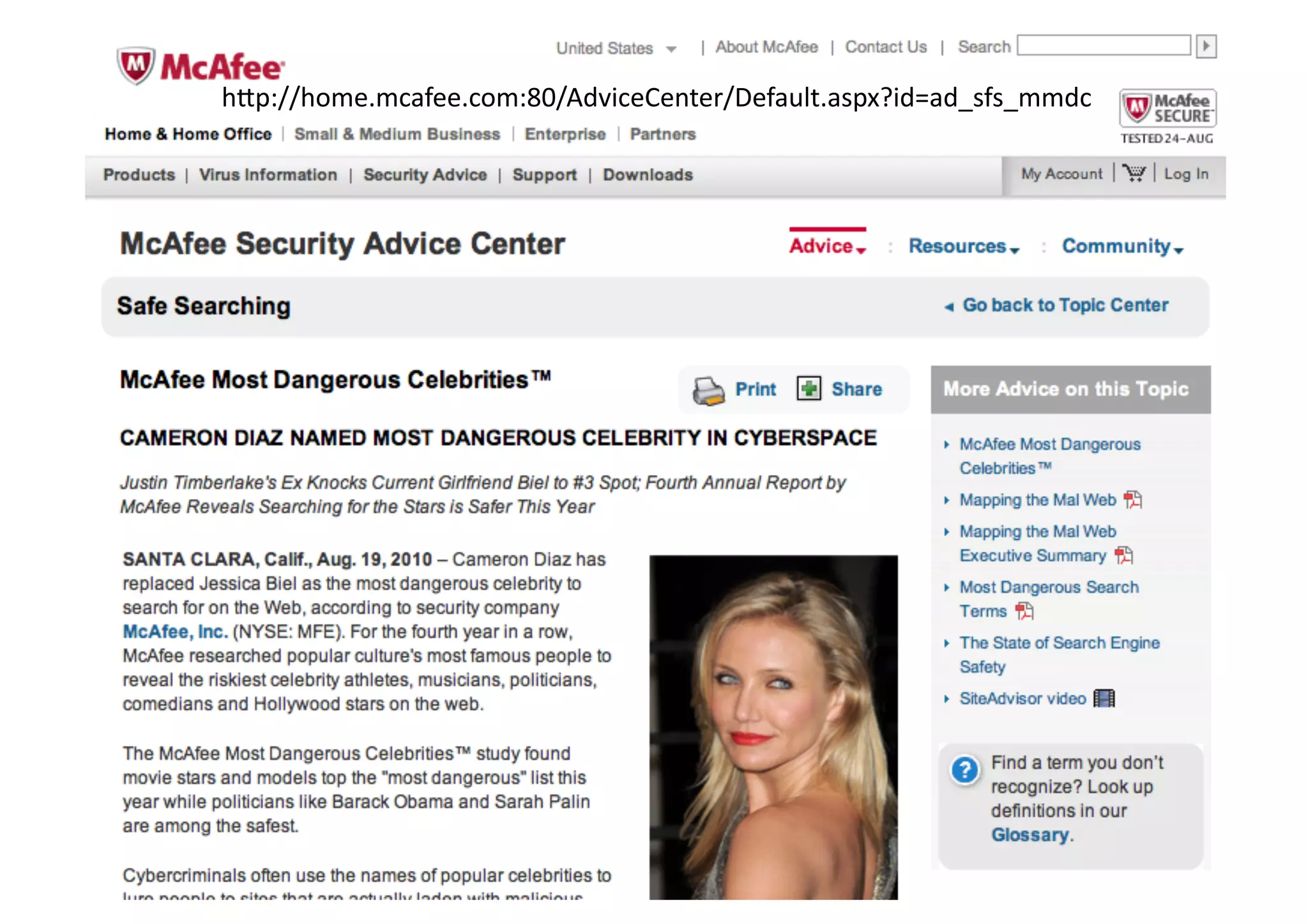
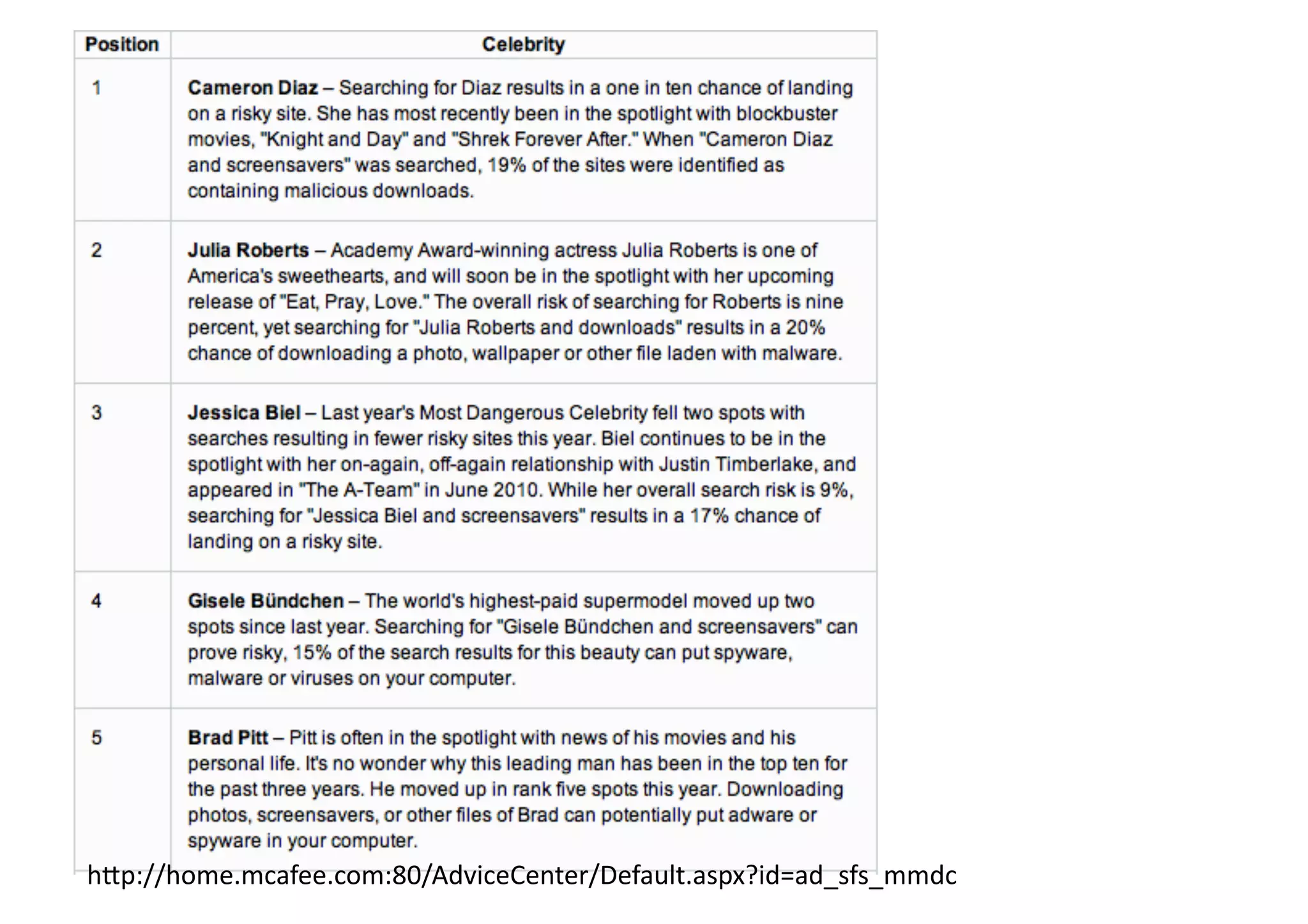
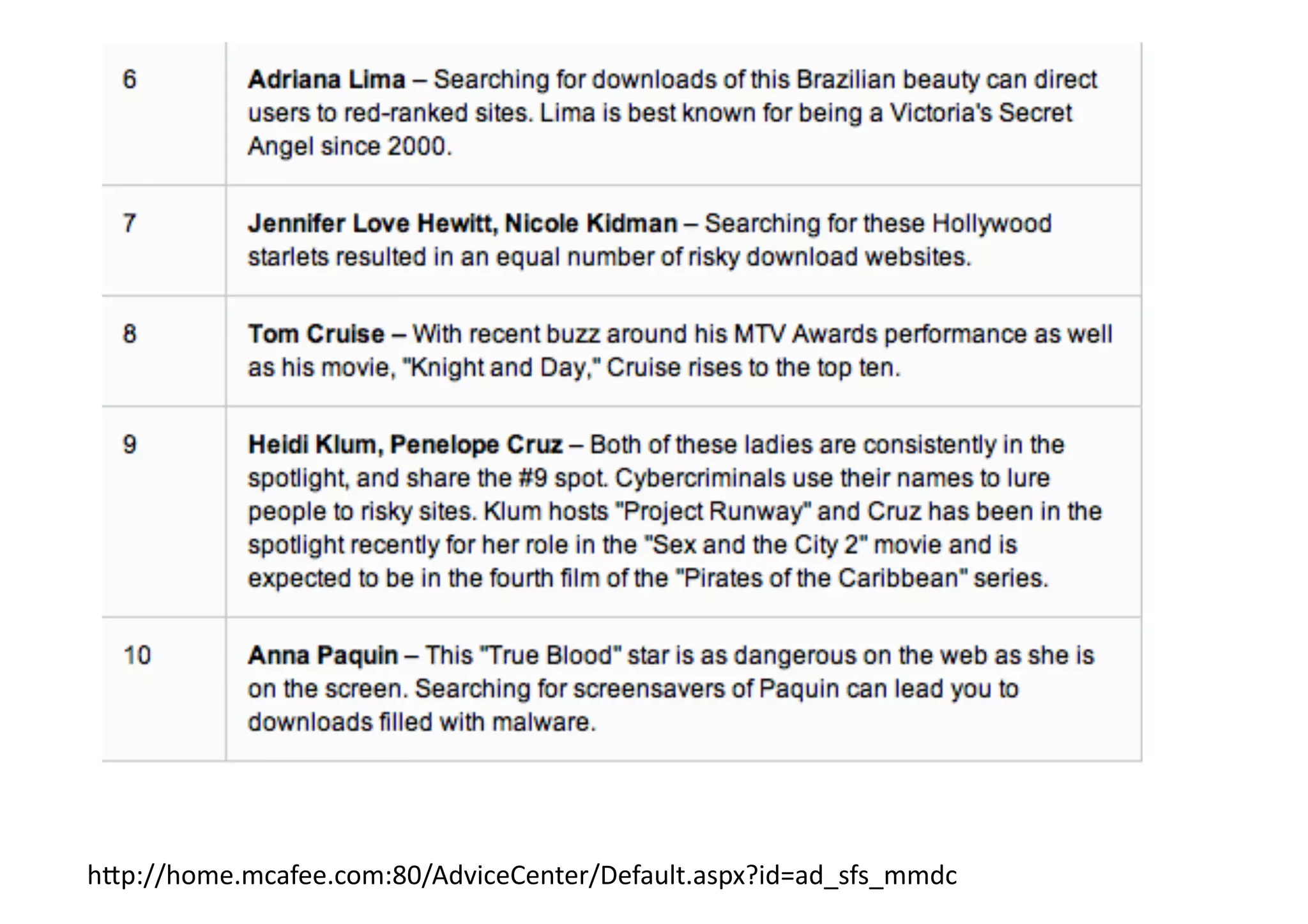
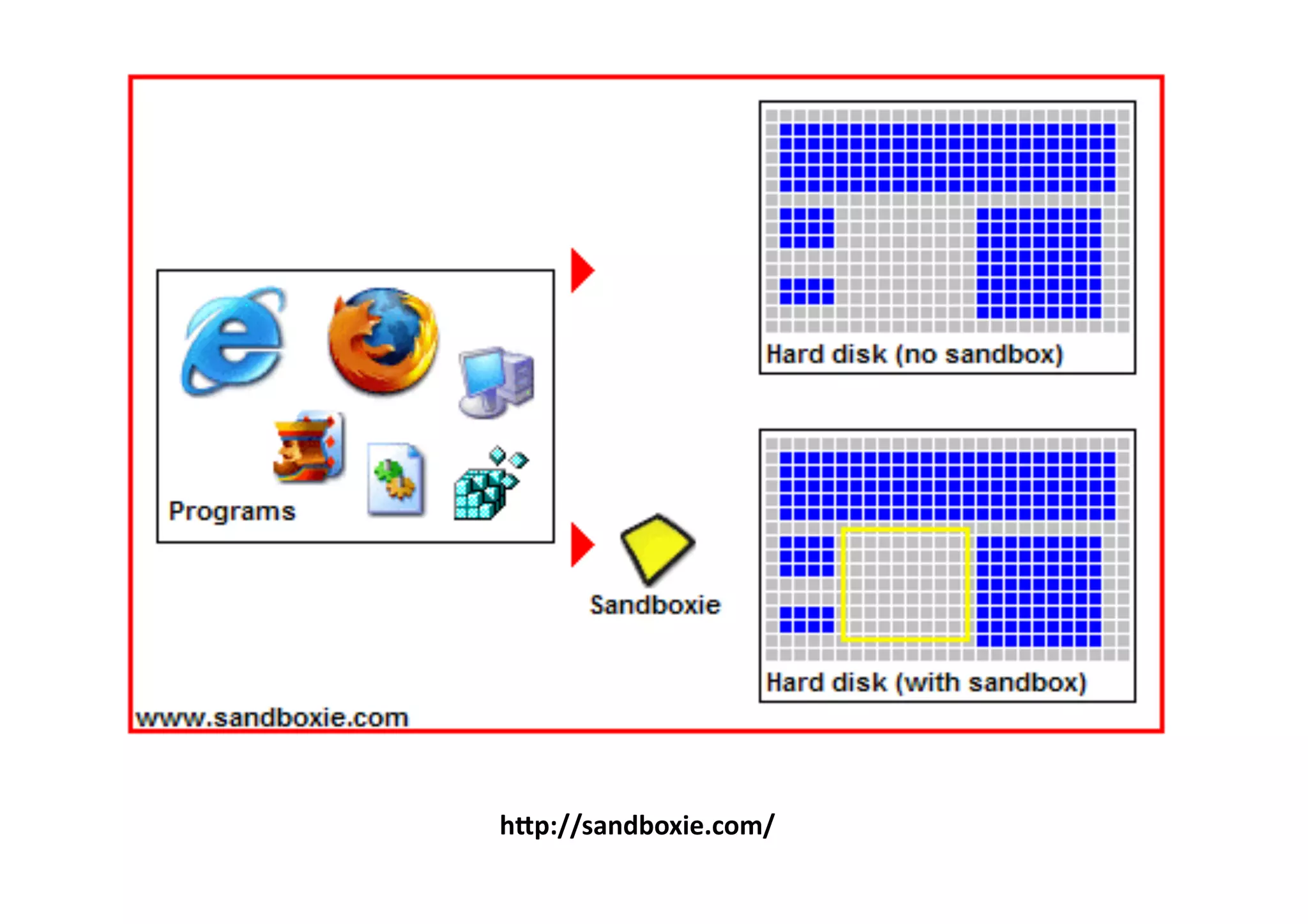
The document provides an overview of ethical hacking, distinguishing it from malicious hacking and outlining the responsibilities and methodologies of ethical hackers. It emphasizes the importance of conducting security tests with a responsible mindset and respecting privacy while providing various resources for learning and research. Ethical hacking commandments include creating a plan, selecting appropriate tools, executing the plan, and evaluating results.