(English) XSCAN 브로슈어_Redpensfot 엑스스캔.pdf
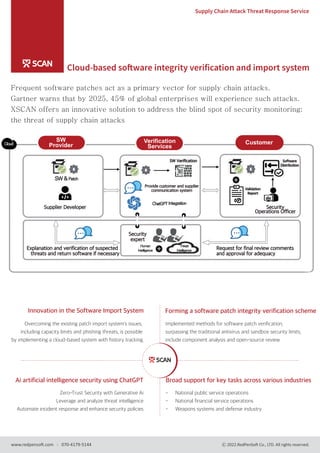
- 1. Ai artificial intelligence security using ChatGPT Zero-Trust Security with Generative Ai Leverage and analyze threat intelligence Automate incident response and enhance security policies Innovation in the Software Import System Overcoming the existing patch import system's issues, including capacity limits and phishing threats, is possible by implementing a cloud-based system with history tracking. Forming a software patch integrity verification scheme Implemented methods for software patch verification, surpassing the traditional antivirus and sandbox security limits, include component analysis and open-source review Broad support for key tasks across various industries - National public service operations - National financial service operations - Weapons systems and defense industry Frequent software patches act as a primary vector for supply chain attacks. Gartner warns that by 2025, 45% of global enterprises will experience such attacks. XSCAN offers an innovative solution to address the blind spot of security monitoring: the threat of supply chain attacks SW Verification Provide customer and supplier communication system Verification Services Customer SW Provider Supplier Developer Security Operations Officer Software Distribution Validation Report Security expert Request for final review comments and approval for adequacy Explanation and verification of suspected threats and return software if necessary
- 2. Dependency Graph Creation of SBOM from the Perspective of the Demand Side Provides rich SBOM data based on binary analysis Provide a Dependency Graph Provision of a Communication Channel with Suppliers Based on Analysis Results CycloneDX / SPDX Extracting Software Components Monitoring of Software Patch Changes Open source dependency detection Creation of SBOM and Justification Features Through binary analysis without source code, it analyzes code signatures and suspected threats, provides various component information, and automatically generates SBOM (Software Bills of Material) The system compares past and present versions to identify changes and entropy shifts, effectively blocking disguised supply chain attacks, including upstrip tampering Binary Analysis Validity and Authenticity Verification Codesgin Component Comparative Analysis Engine Similarity Rate Result Result Altered Added Utilizing a sophisticated fingerprinting algorithm, it detects open-source components used in binary files, along with their vulnerabilities and any license tampering Identifier extraction (string value, function name, variable name, etc.) Cross-referencing of open-source intelligence and identifiers, including scoring based on frequency and value length Generates SBOMs from binary analysis results in CycloneDX and SPDX formats, and offers features for communicating with suppliers about suspicious activities and analysis findings compared to previous versions - New IP (CC Communication) - Privilege Escalation, Persistent Execution, Detection Evasion, Data Exfiltration Key Suspicious Activity Analysis