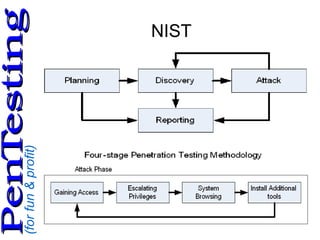
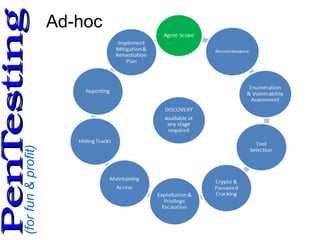
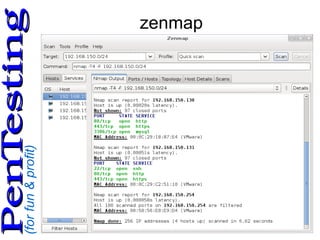
This document discusses web application penetration testing. It begins by introducing the speaker and providing context on working in cyber security and teaching related topics. It then covers why penetration testing is performed, common methodologies and frameworks for testing including NIST and OWASP, as well as tools used like nmap, ZAP and Burp Suite. The document provides guidance on planning a penetration test including profiling the target and creating a risk assessment. It concludes by recommending books and references on penetration testing and ethical hacking.