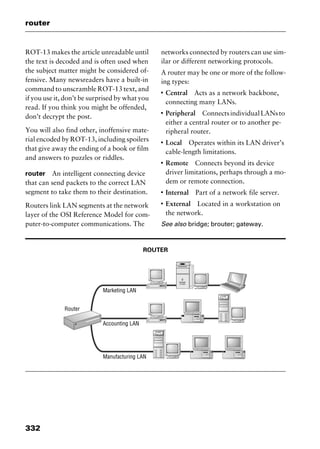
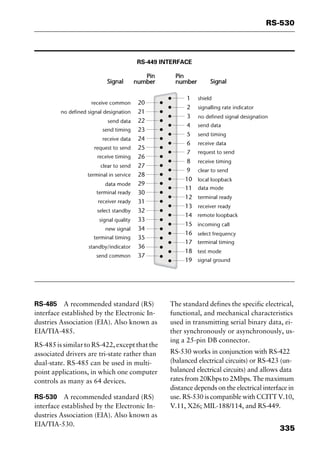
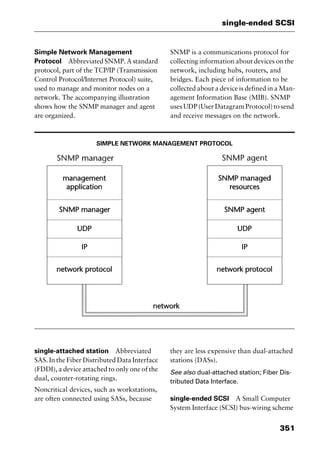
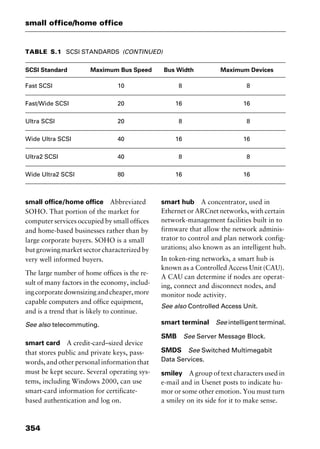
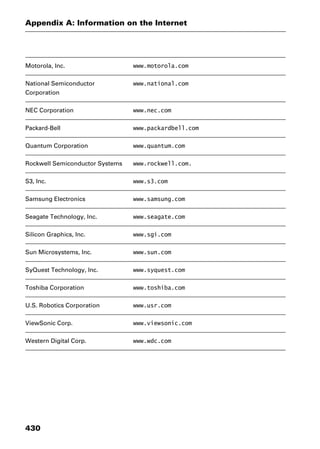
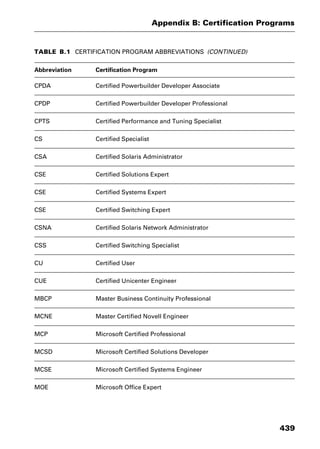
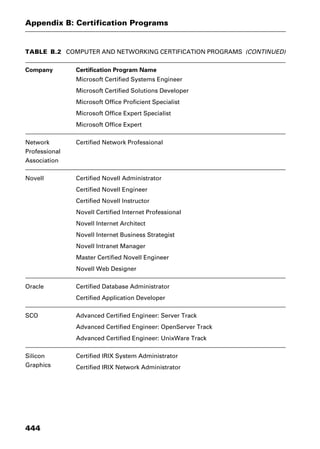
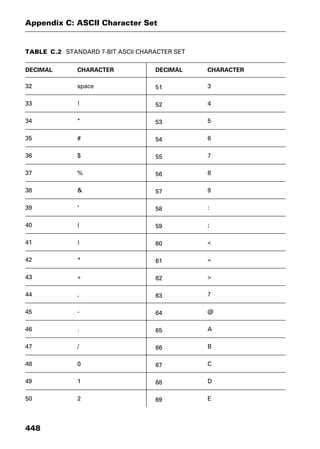
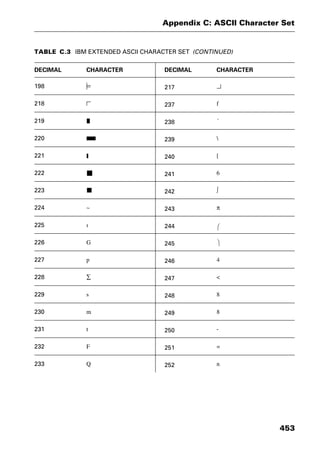
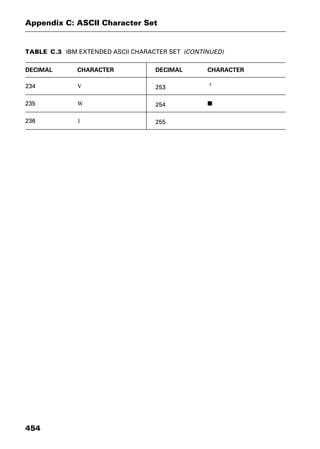
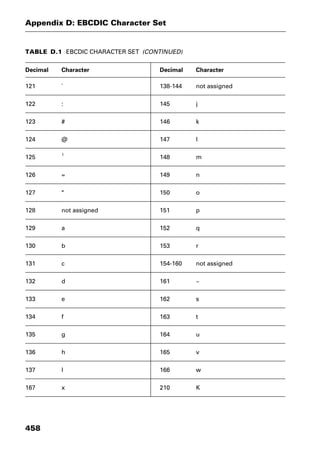
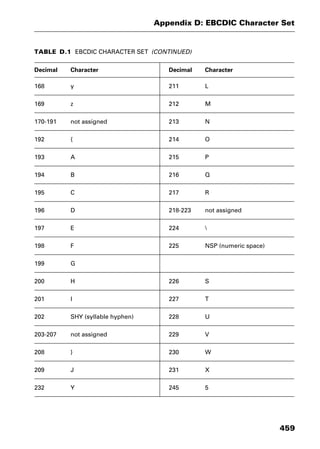
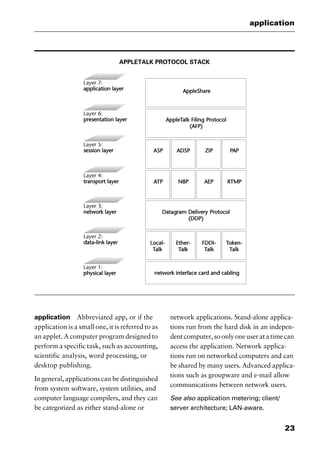
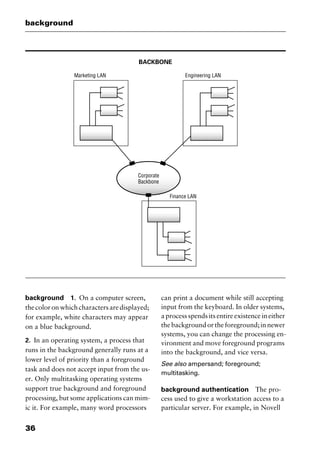
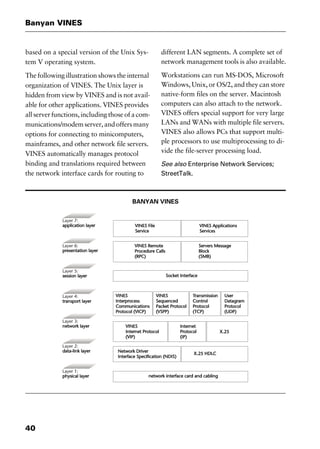
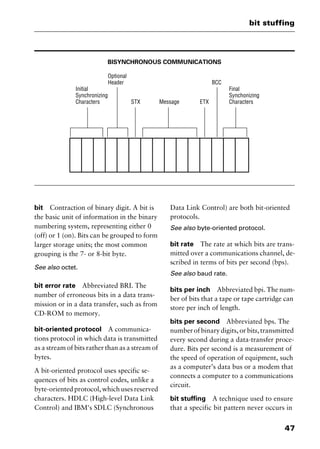
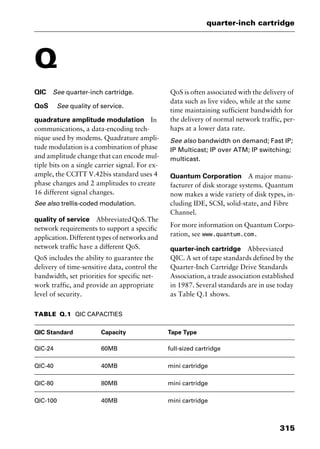
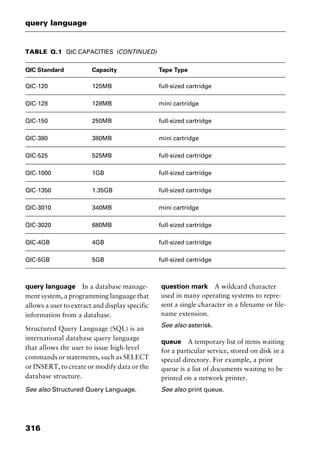
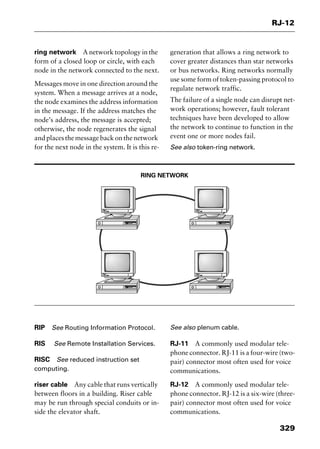
This document provides an introduction and overview of a dictionary of networking terms. It discusses who should use the book, what topics are covered, how entries are organized and defined, and how extensive cross-referencing links related terms. It also includes sample text from entries and describes additional reference materials contained in the appendices.








































































































































































































































































































![reduced instruction set computing
322
printer-sharing services and diverts them to
the file server for action.
See also NetWare shell; NETx.COM;
requester.
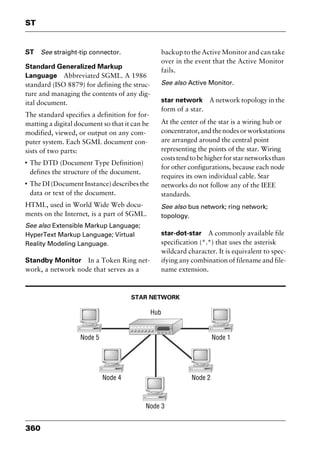
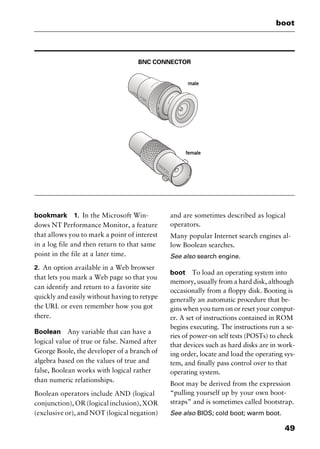
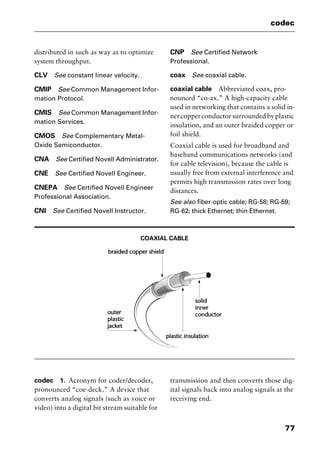
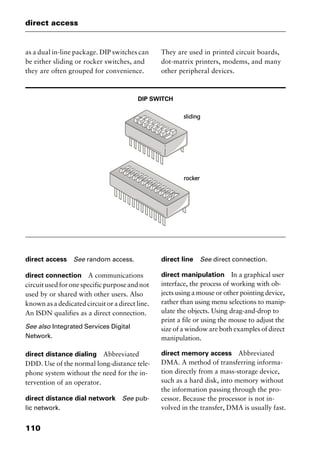
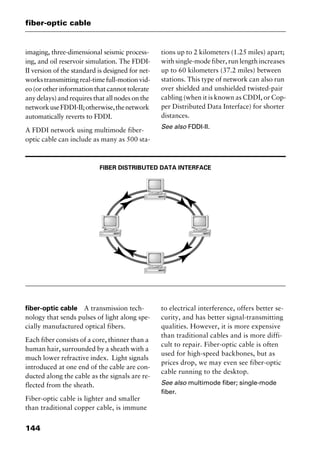
reduced instruction set computing
Abbreviated RISC, pronounced “risk.” A
processor that recognizes only a limited
number of assembly-language instructions.
RISC chips are relatively cheap to produce
and debug because they usually contain
fewer than 128 instructions. RISC proces-
sors are commonly used in workstations,
and they can be designed to run up to 70
percent faster than processors that use com-
plex instruction set computing (CISC).
See also complex instruction set comput-
ing; IBM RS/6000; instruction set.
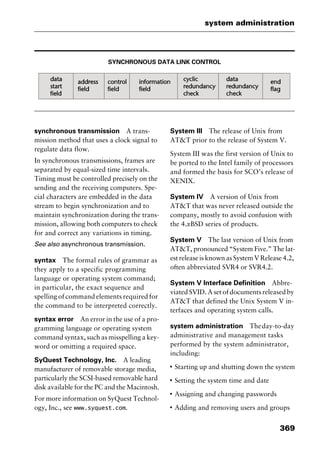
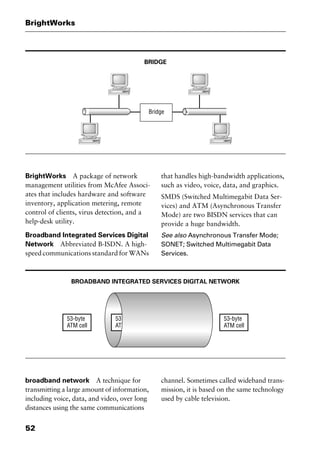
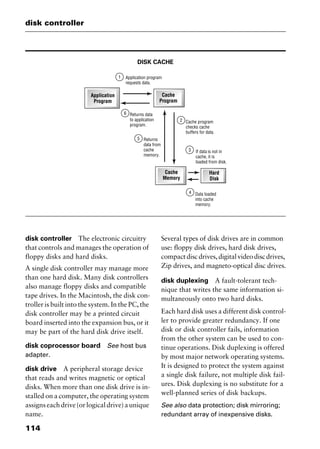
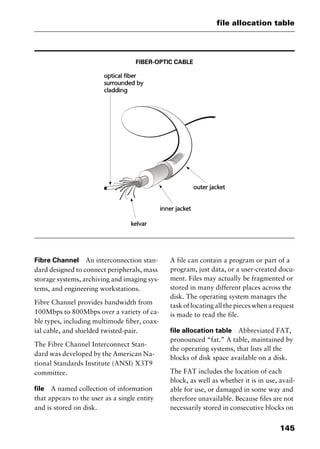
redundant array of inexpensive
disks Abbreviated RAID. In networking
and mission-critical applications, a method
of using several hard disk drives (often SCSI
or Integrated Drive Electronics [IDE] drives)
in an array to provide fault tolerance in the
event that one or more than one drive fails.
Each level of RAID is designed for a specific
use:
I
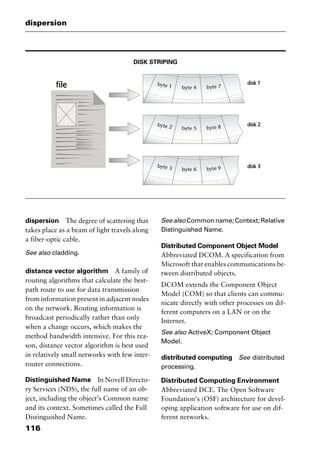
RAID 0 Data is striped over one or more
drives, but there is no redundant drive.
RAID 0 provides no fault tolerance be-
cause the loss of a hard disk means a com-
plete loss of data. Some classification
schemes omit RAID 0 for this reason.
I
RAID 1 Two hard disks of equal capac-
ity duplicate or mirror each other’s con-
tents. One disk continuously and
automaticallybacksuptheotherdisk.This
method is also known as disk mirroring or
disk duplexing, depending on whether one
or two independent hard-disk controllers
are used.
I
RAID 2 Bit-interleaved data is written
across several drives, and then parity and
error-correction information is written to
additional separate drives. The specific
number of error-correction drives de-
pends on the allocation algorithm in use.
I
RAID 3 Bit-interleaved data is written
across several drives, but only one parity
drive is used. If an error is detected, the
data is reread to resolve the problem. The
fact that data is reread in the event of an er-
ror may add a small performance penalty.
I
RAID 4 Data is written across drives by
sectors rather than at the bit level, and a
separate drive is used as a parity drive for
error detection. Reads and writes occur
independently.
I
RAID 5 Data is written across drives in
sectors, and parity information is added
as another sector, just as if it were ordi-
nary data. This level of RAID can provide
faster performance as the parity informa-
tion is written across all the drives, rather
than to a single parity drive.
There is not much difference in speed or
quality among these levels. The appropriate
level of RAID for any particular installation
depends on network usage. RAID levels 1, 3,
and 5 are available commercially, and levels
3 and 5 are proving popular for networks.
Several vendors have created their own
RAID levels, including 6, 7,10, 11, and 35.
Some of these are actually combinations of
existing RAID levels, such as Compaq’s
2461book Page 322 Thursday, May 4, 2000 11:59 AM
Copyright © 2000 SYBEX Inc., Alameda, CA. www.sybex.com](https://image.slidesharecdn.com/dictionaryofnetworking-130426163545-phpapp01/85/Dictionary-of-networking-327-320.jpg)







![331
ROT-13
RJ-45
roll forward The ability of a database
management system to re-create the data in
the database by rerunning all the transac-
tions listed in the transaction log.
See also roll back; transaction processing.
ROM See read-only memory.
ROM BIOS See BIOS.
root 1. In many operating systems, the
name of the directory at the top of the di-
rectory tree from which all other directories
are descended.
2. In Unix, the name of the superuser, user
number 0. The system administrator uses
this account for certain administrative
tasks. One of the main objectives of an in-
truder on a Unix system is to gain root user
status. Once achieved, the intruder has un-
limited access to the system.
See also avatar; root directory.
root domain The top-level Domain
Name Service (DNS) domain on the Inter-
net. Also, in Microsoft Windows 2000
Server, the top-level domain in a Windows
2000 domain tree.
See also child domain; first-layer domain;
parent domain
root directory In a hierarchical direc-
tory structure, such as that used in Unix
and many other operating systems, the di-
rectory from which all other directories
must branch. You cannot delete the root
directory.
See also parent directory; period and
double-period directories.
Root object InNovellDirectoryServices
(NDS), the original container object, creat-
ed when NDS is first installed.
The Root object contains all other NDS ob-
jects and cannot be deleted, renamed, or
moved. Sometimes written [Root].
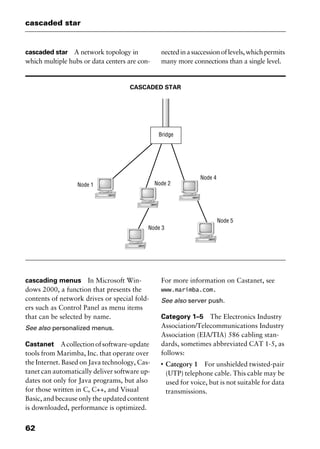
ROT-13 Pronounced “rote-13.”A simple
encoding scheme often used to scramble
posts to Usenet newsgroups.
ROT-13 works by swapping each alphabet-
ic character with another 13 characters re-
moved from its location in the alphabet, so
that a becomes n, and so on; numbers and
punctuation are unaffected.
2461book Page 331 Thursday, May 4, 2000 11:59 AM
Copyright © 2000 SYBEX Inc., Alameda, CA. www.sybex.com](https://image.slidesharecdn.com/dictionaryofnetworking-130426163545-phpapp01/85/Dictionary-of-networking-336-320.jpg)