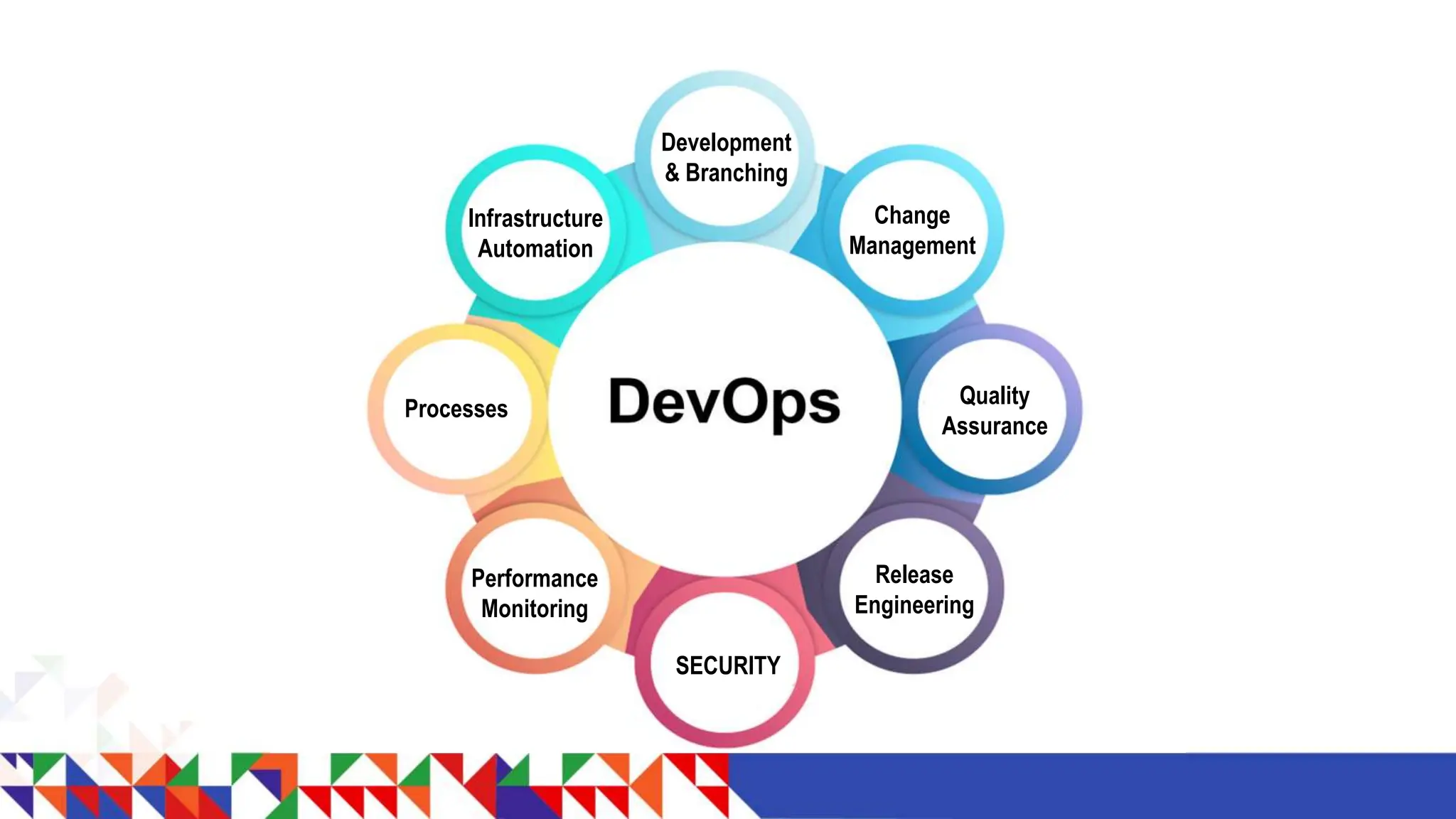
The document discusses the implementation of DevSecOps, highlighting the importance of integrating security throughout the development lifecycle rather than treating it as an afterthought. Key strategies include a shift-left approach, collaborative responsibility for security among all team members, and the use of various tools for effective security operations. It emphasizes that security should be pervasive and user-friendly, ultimately making it a natural part of the DevOps process.