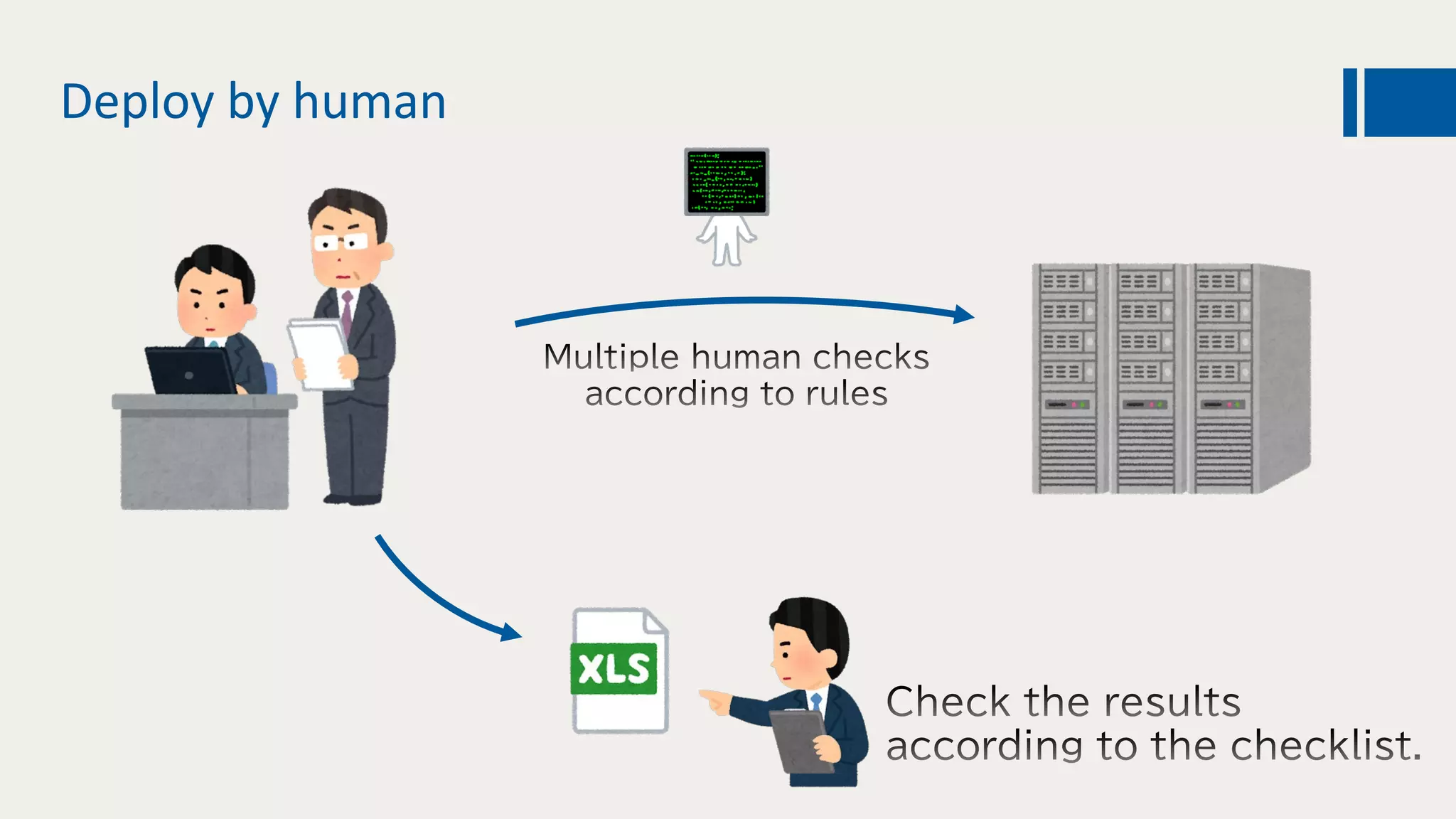
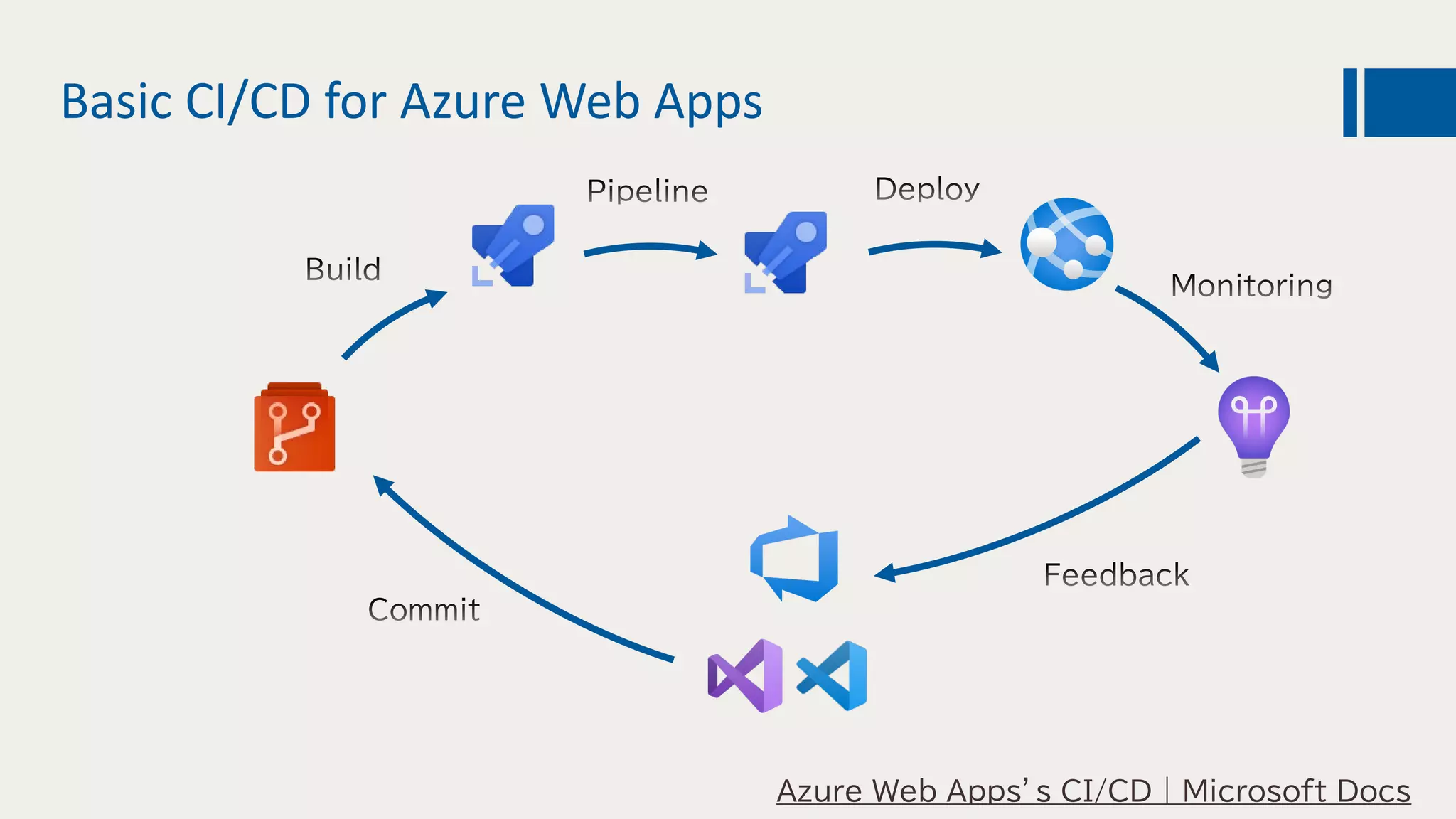
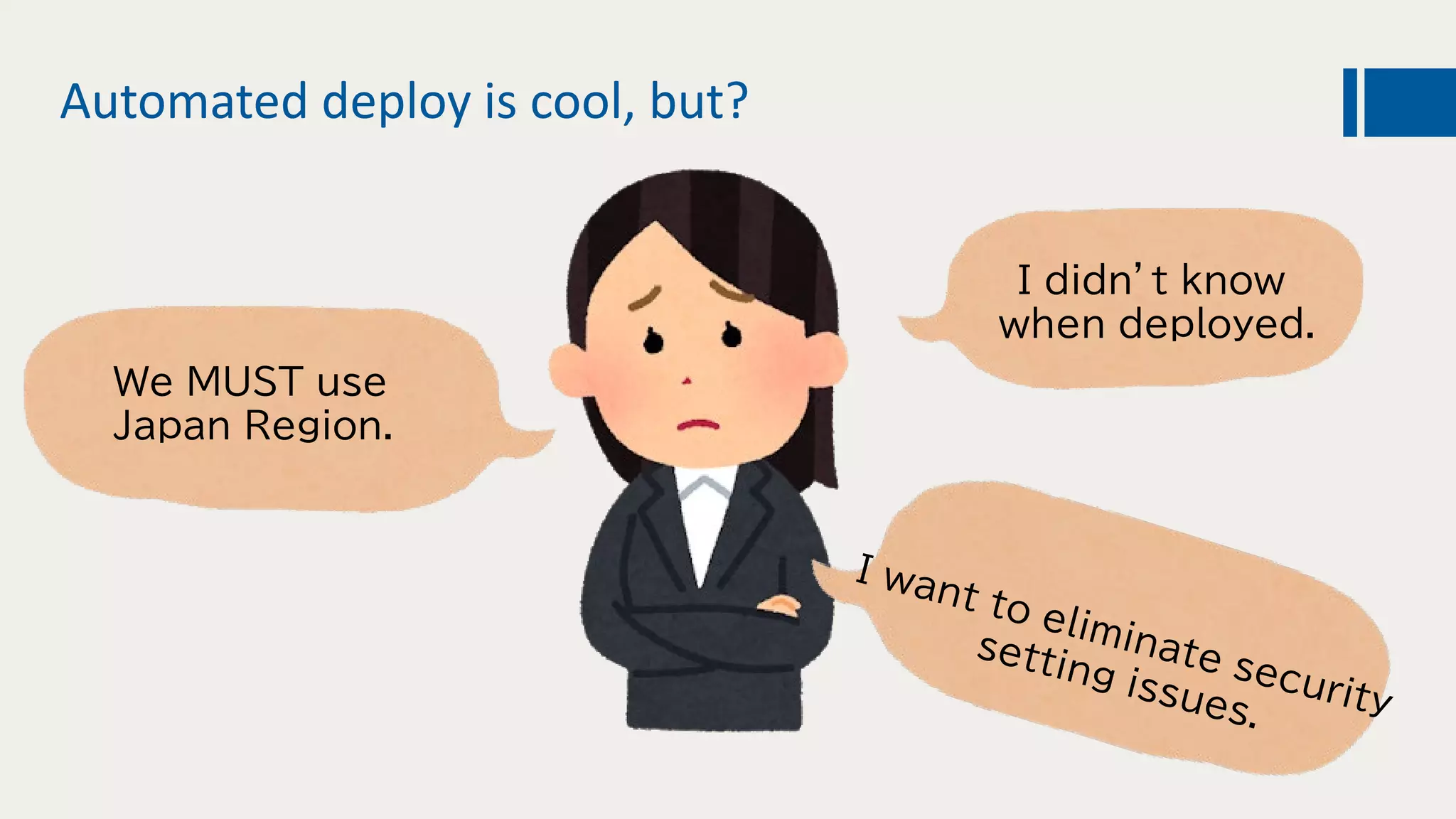
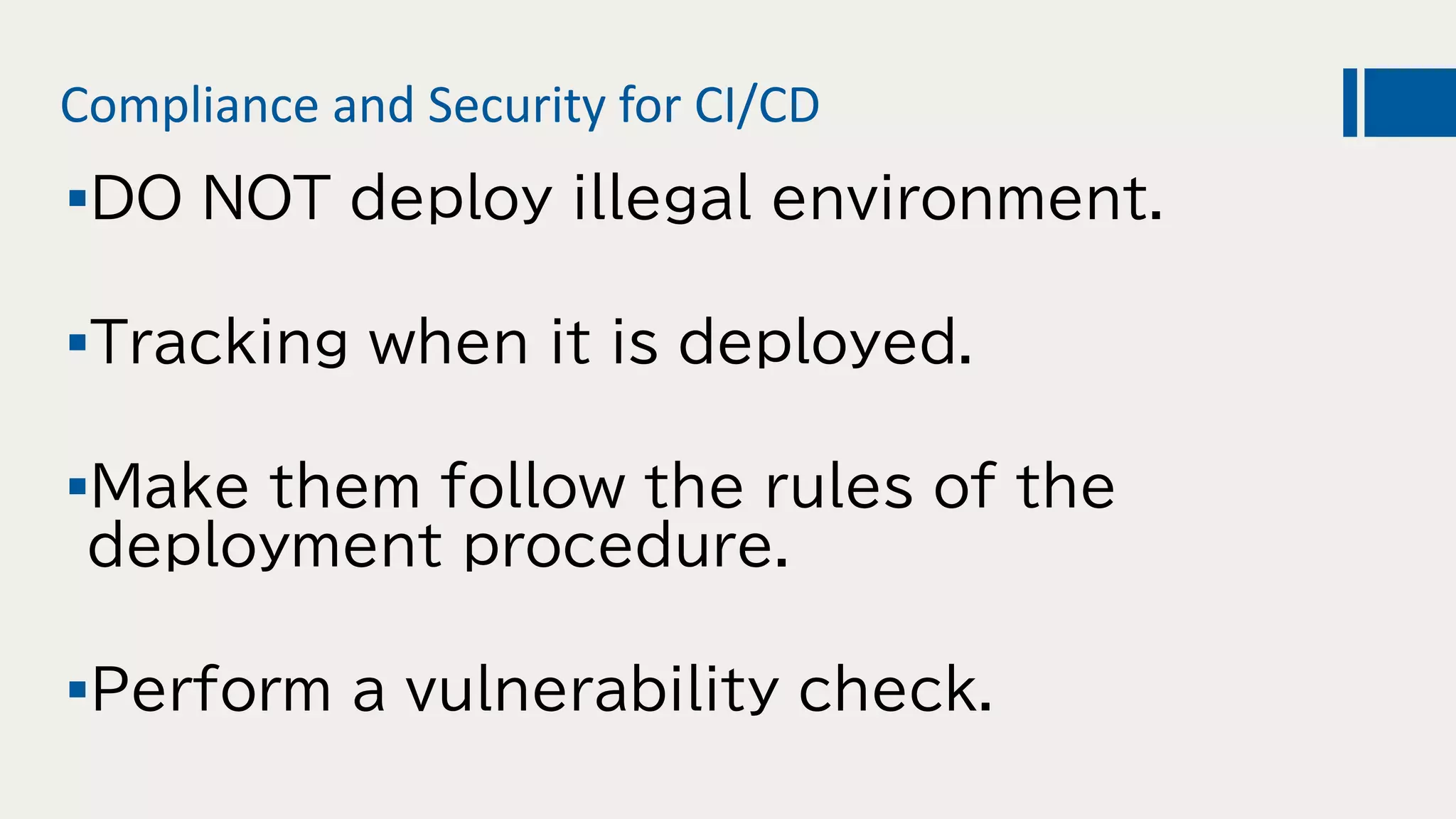
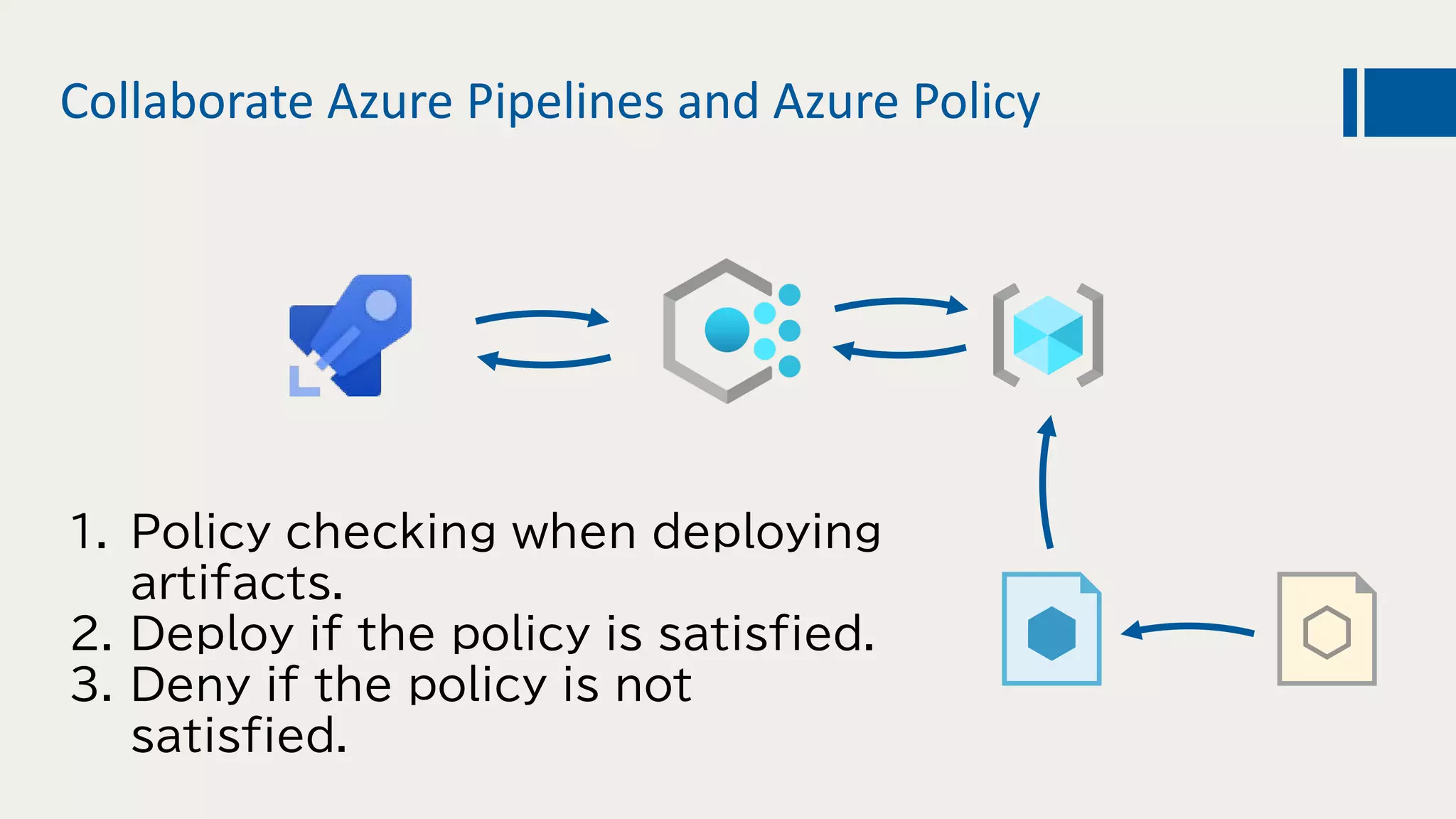
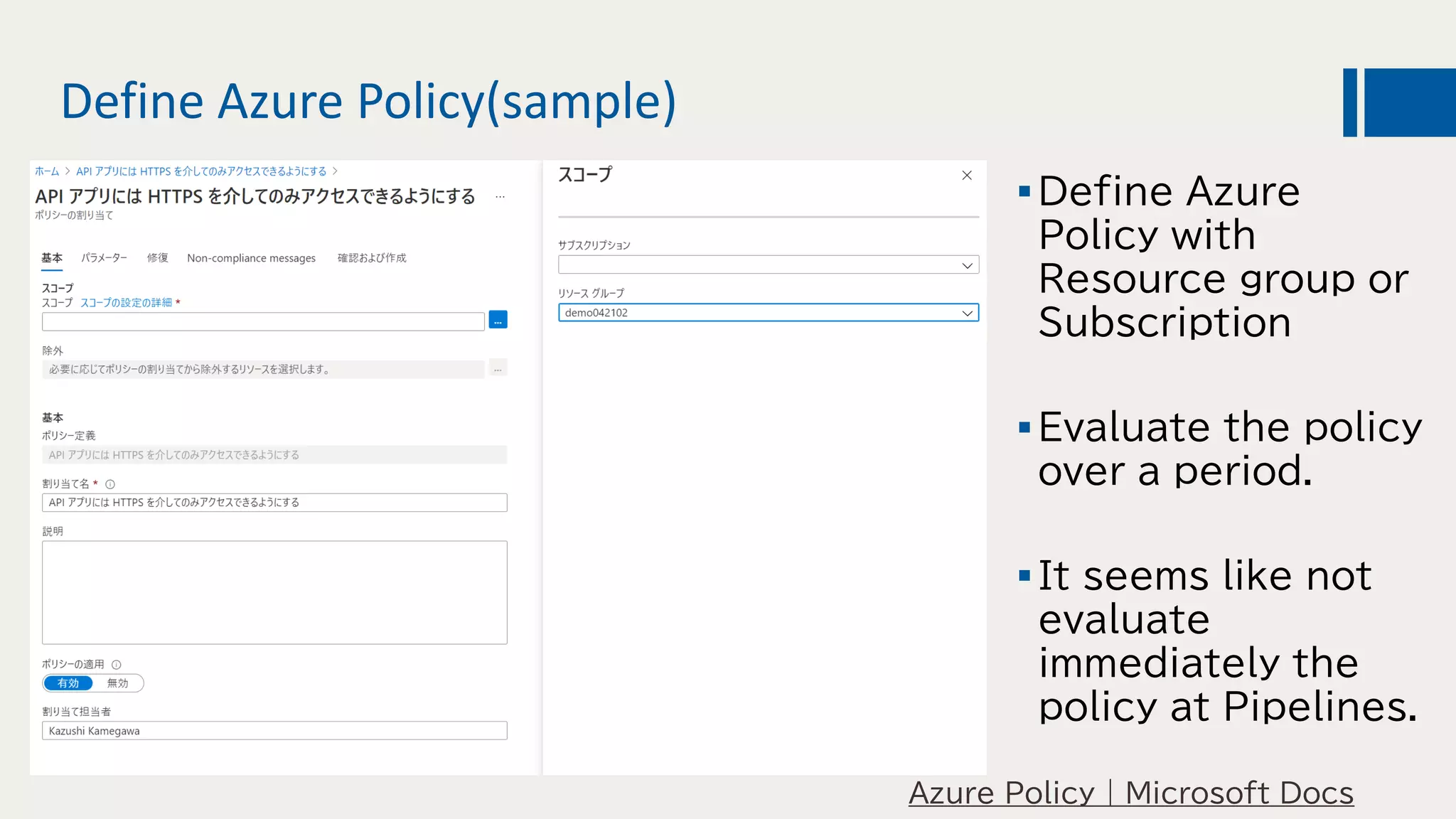
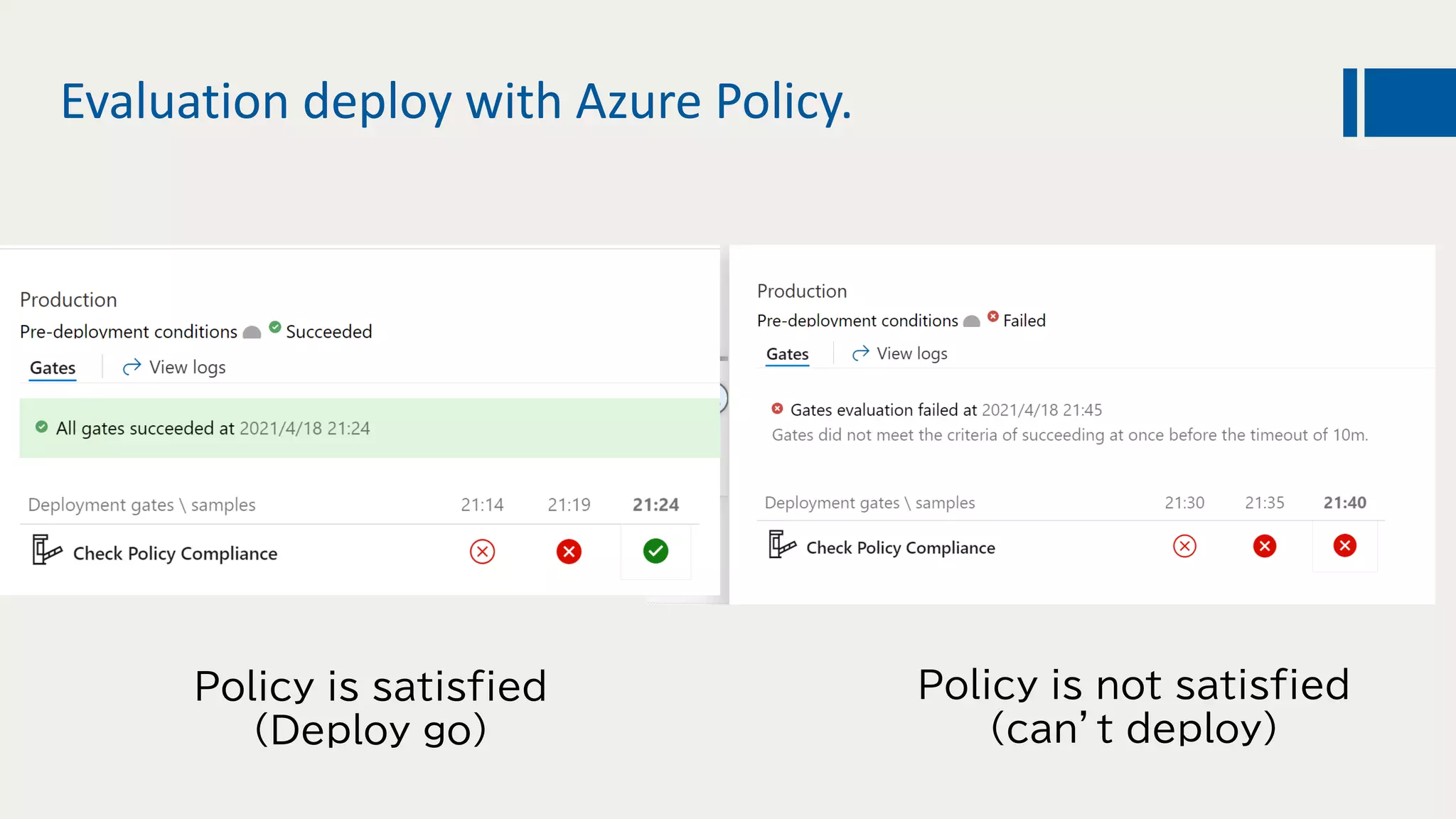
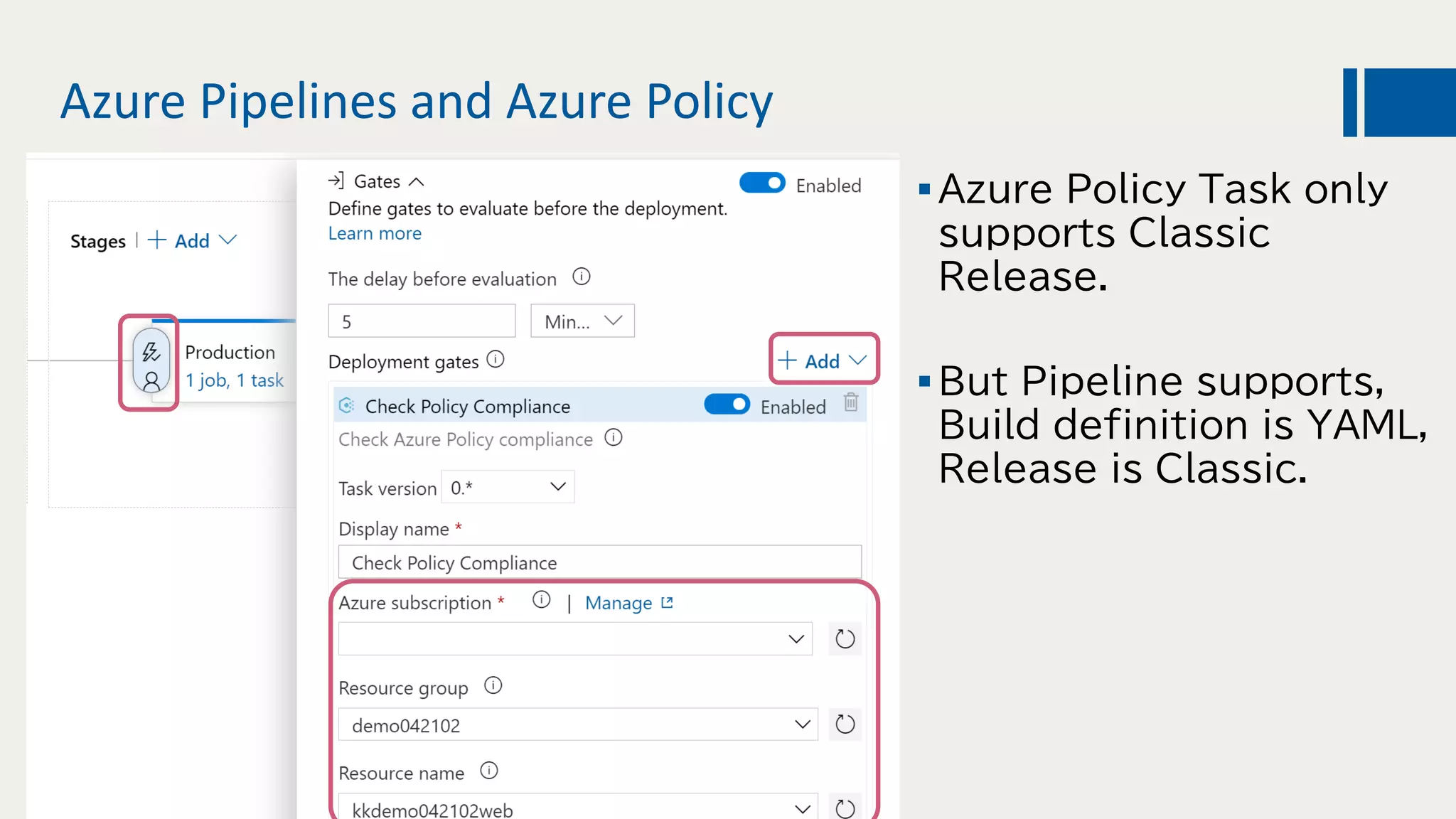
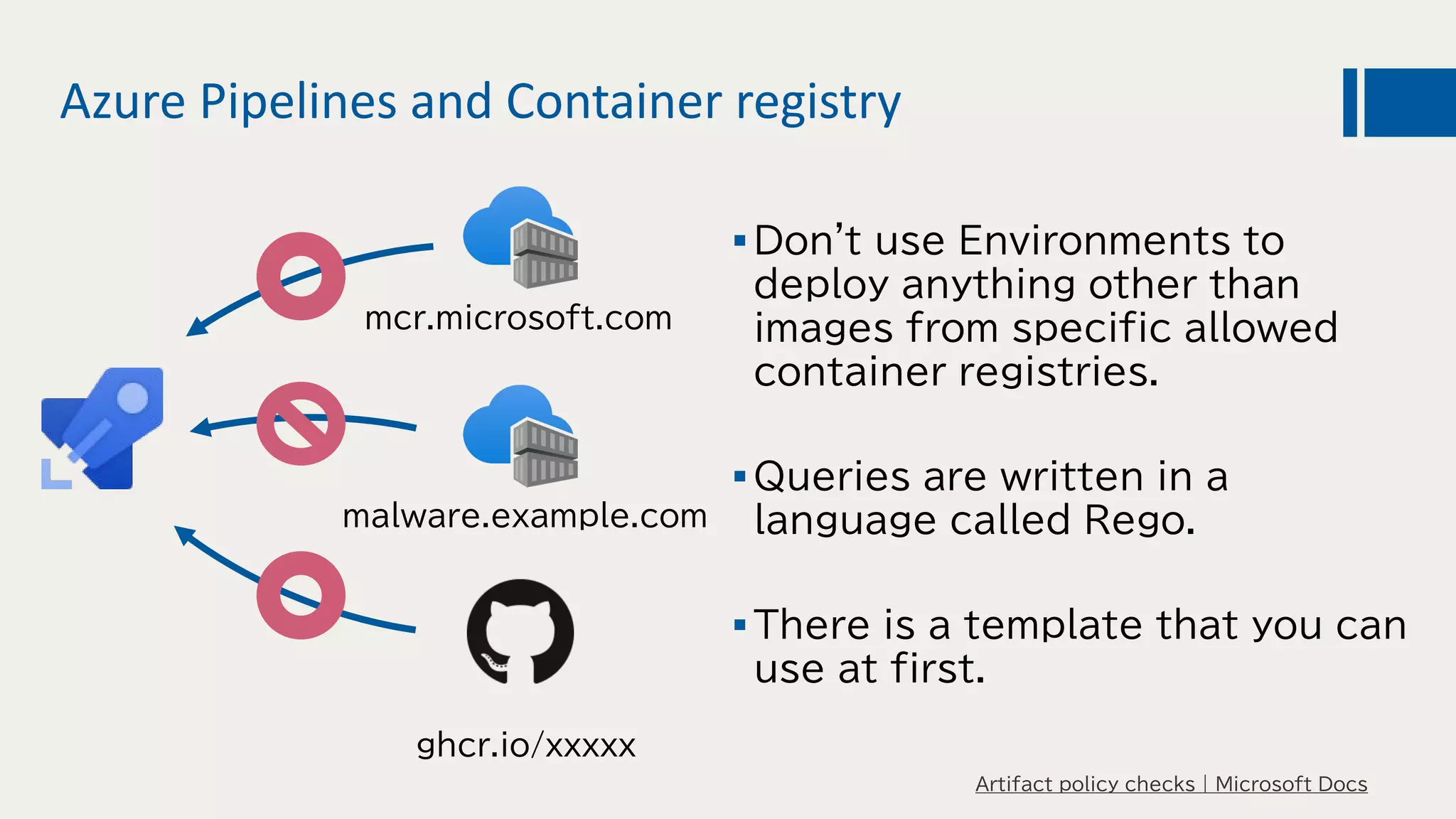
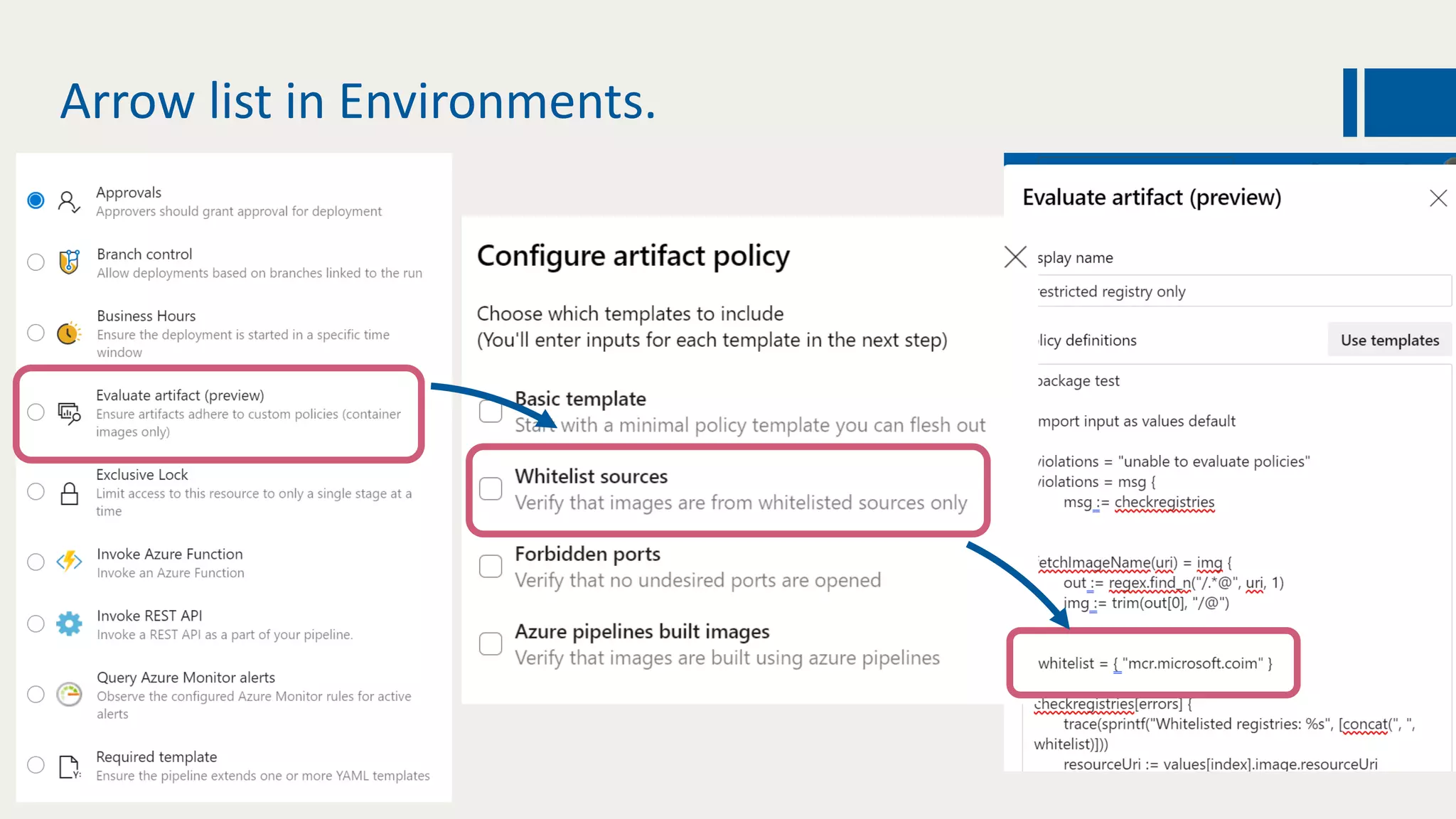
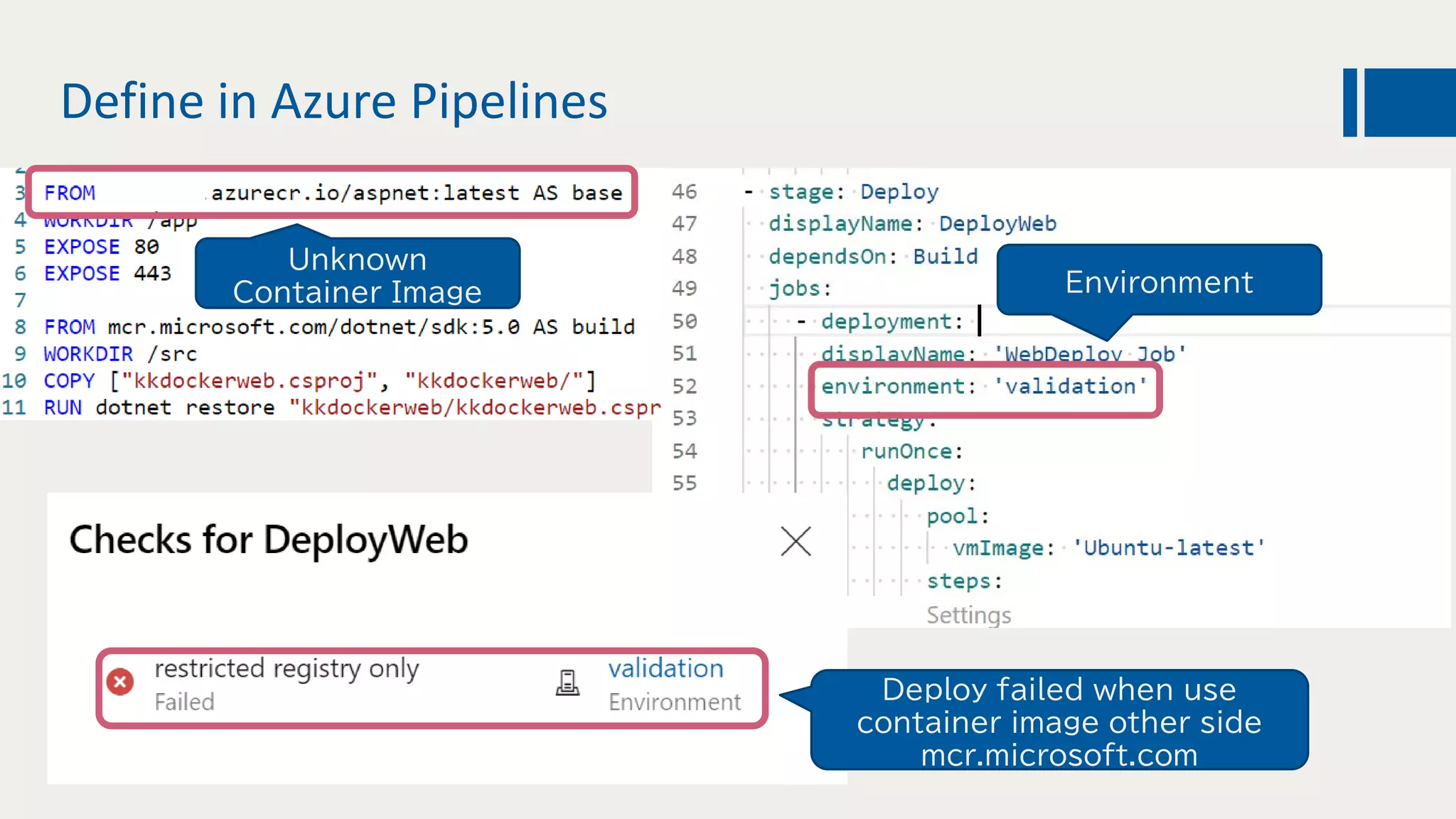
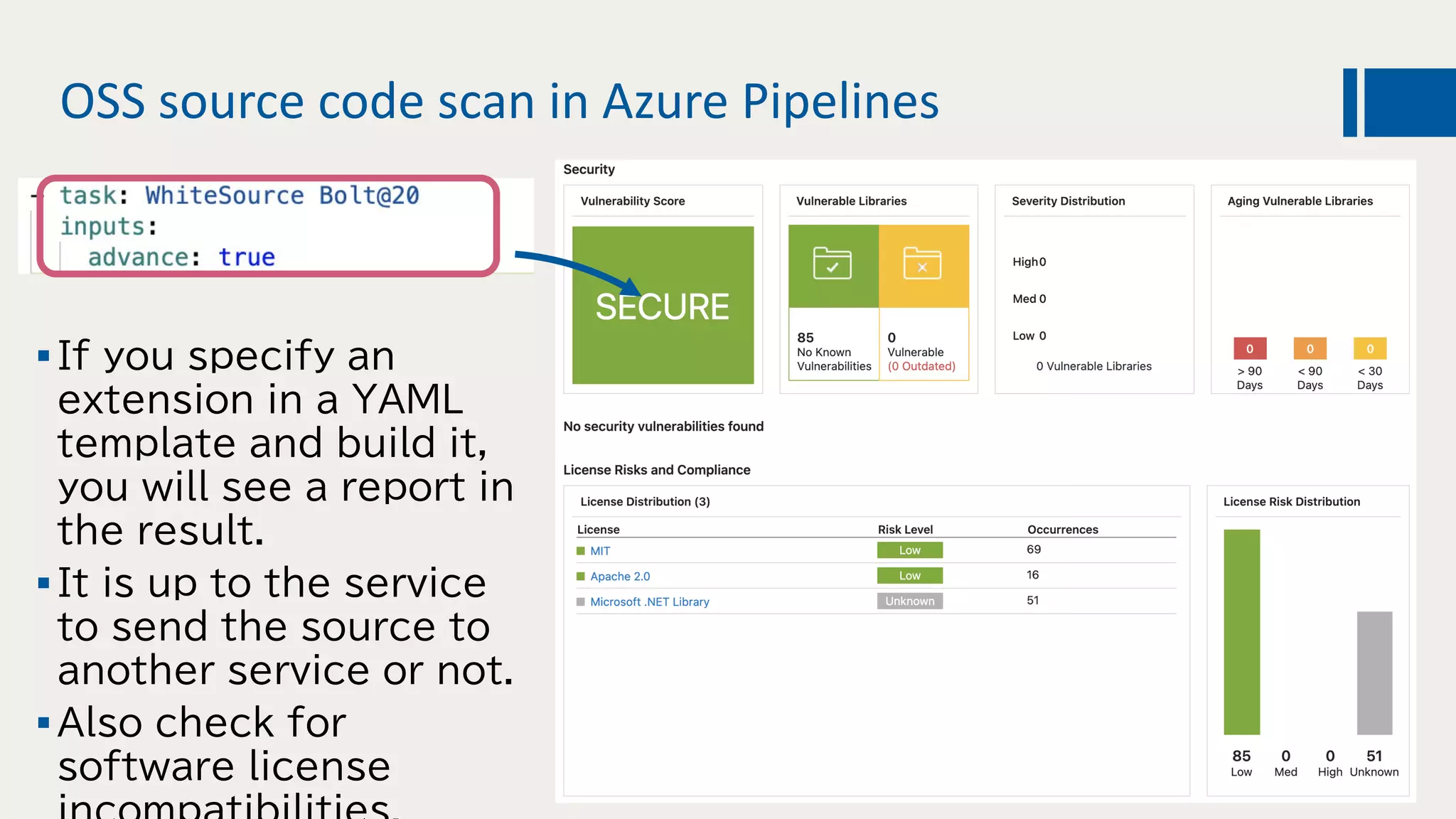
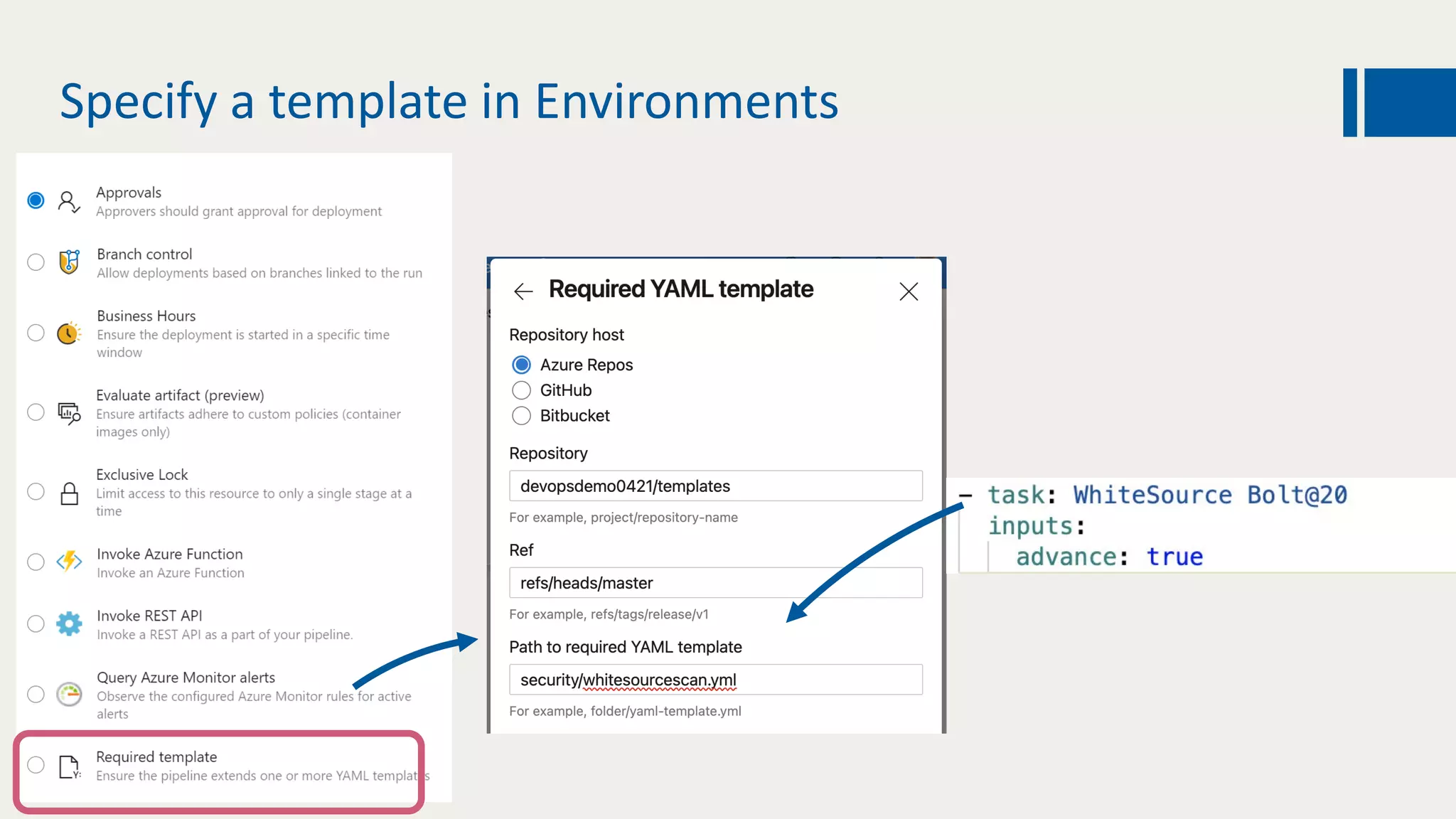
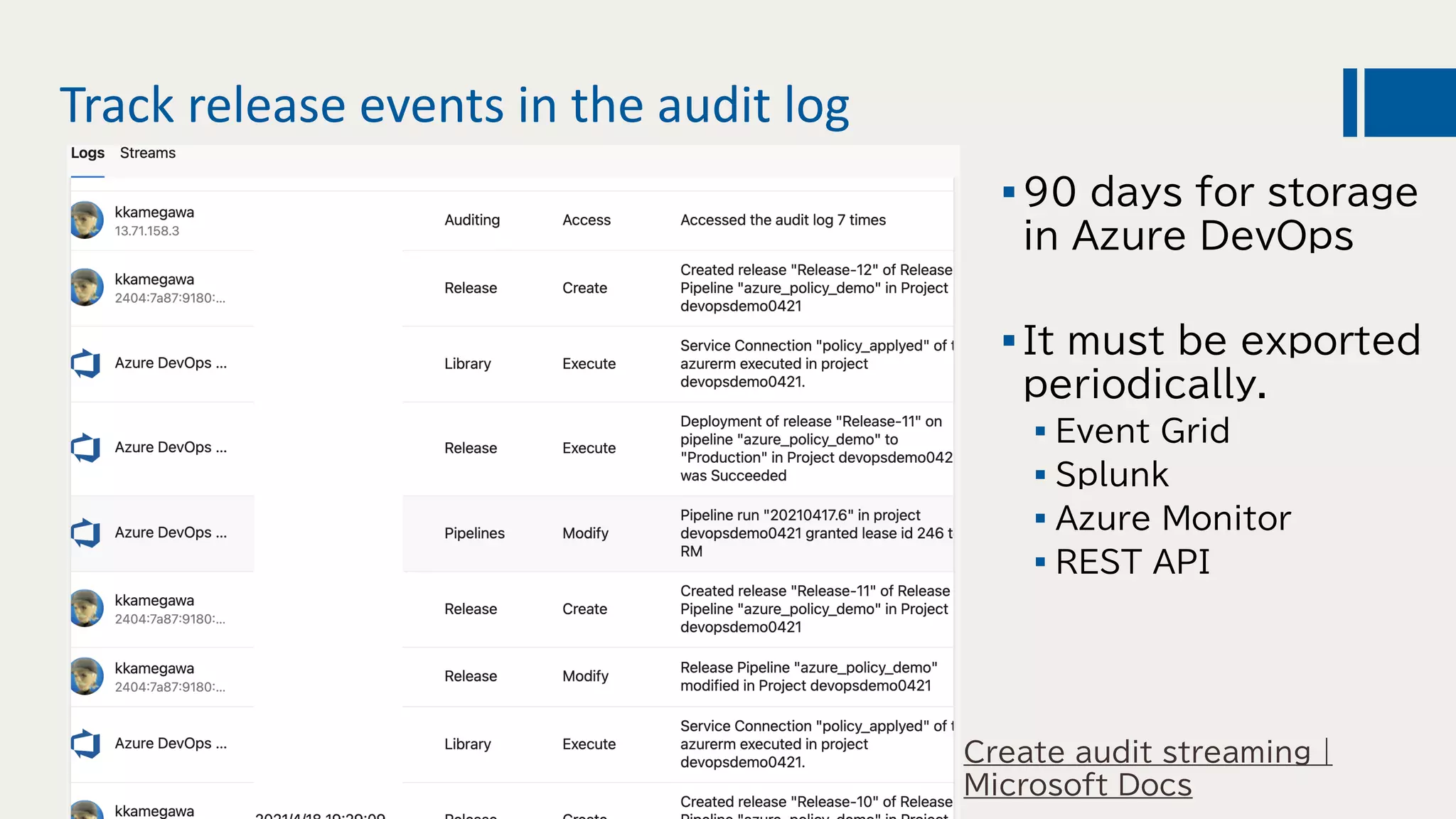
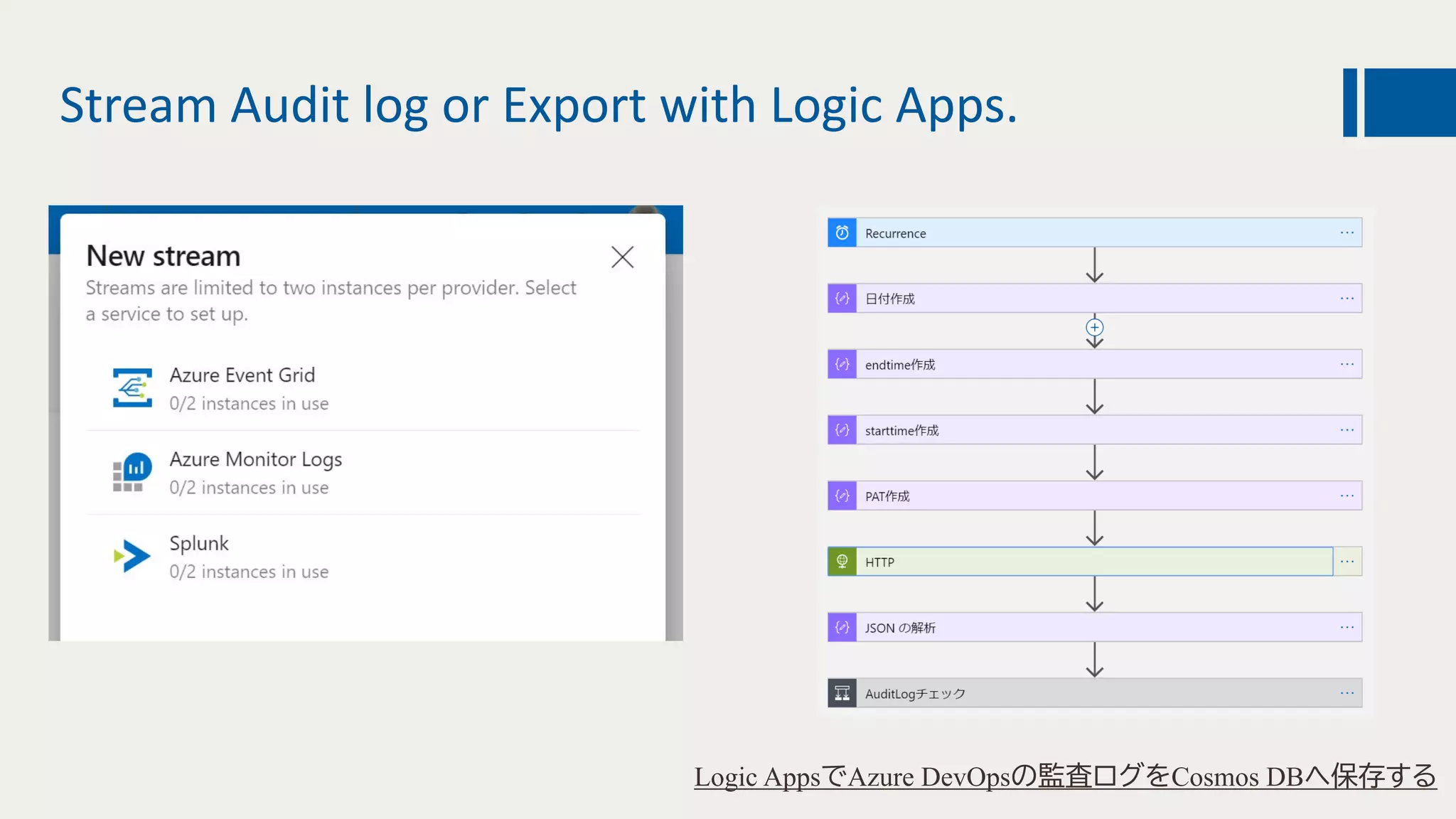
This document discusses using DevOps and security/compliance features in Azure to ensure automated deployments follow rules and policies. It recommends using Azure Pipelines and Azure Policy to check for policy compliance during deployment and deny deployment if policies are not met. It also suggests using extensions to scan for vulnerabilities and license issues, and tracking deployments in the audit log or exporting it to other services like Logic Apps for record keeping.