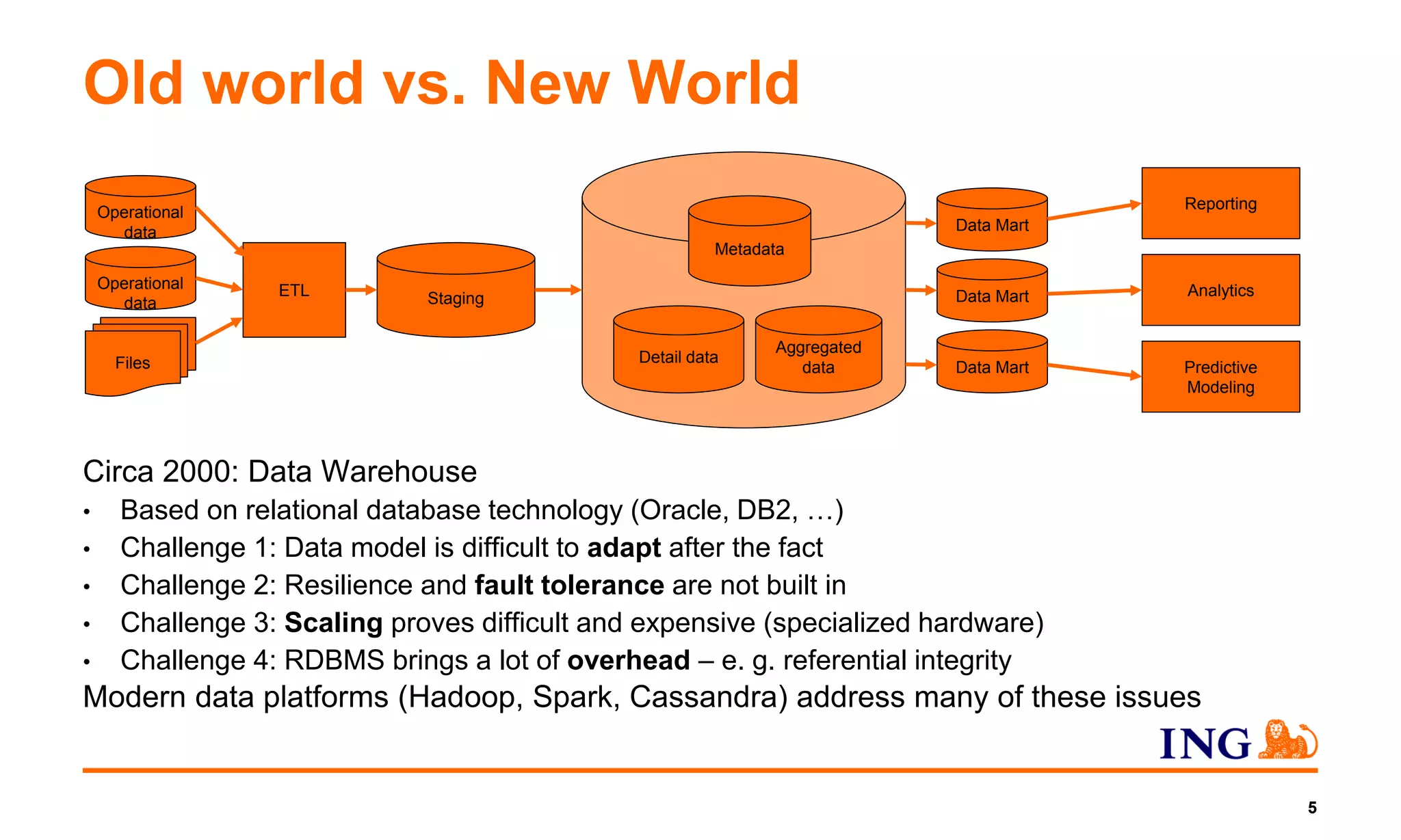
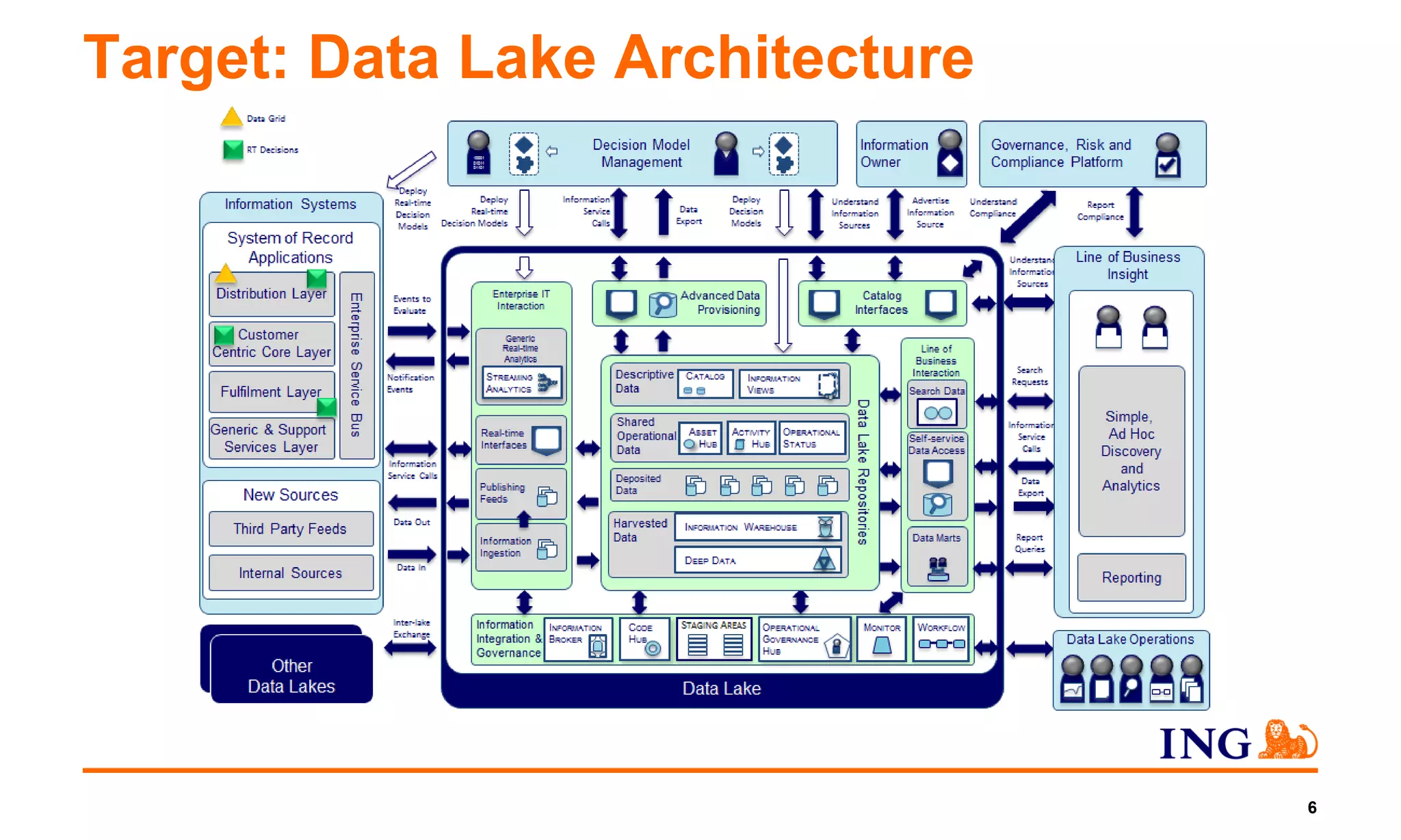
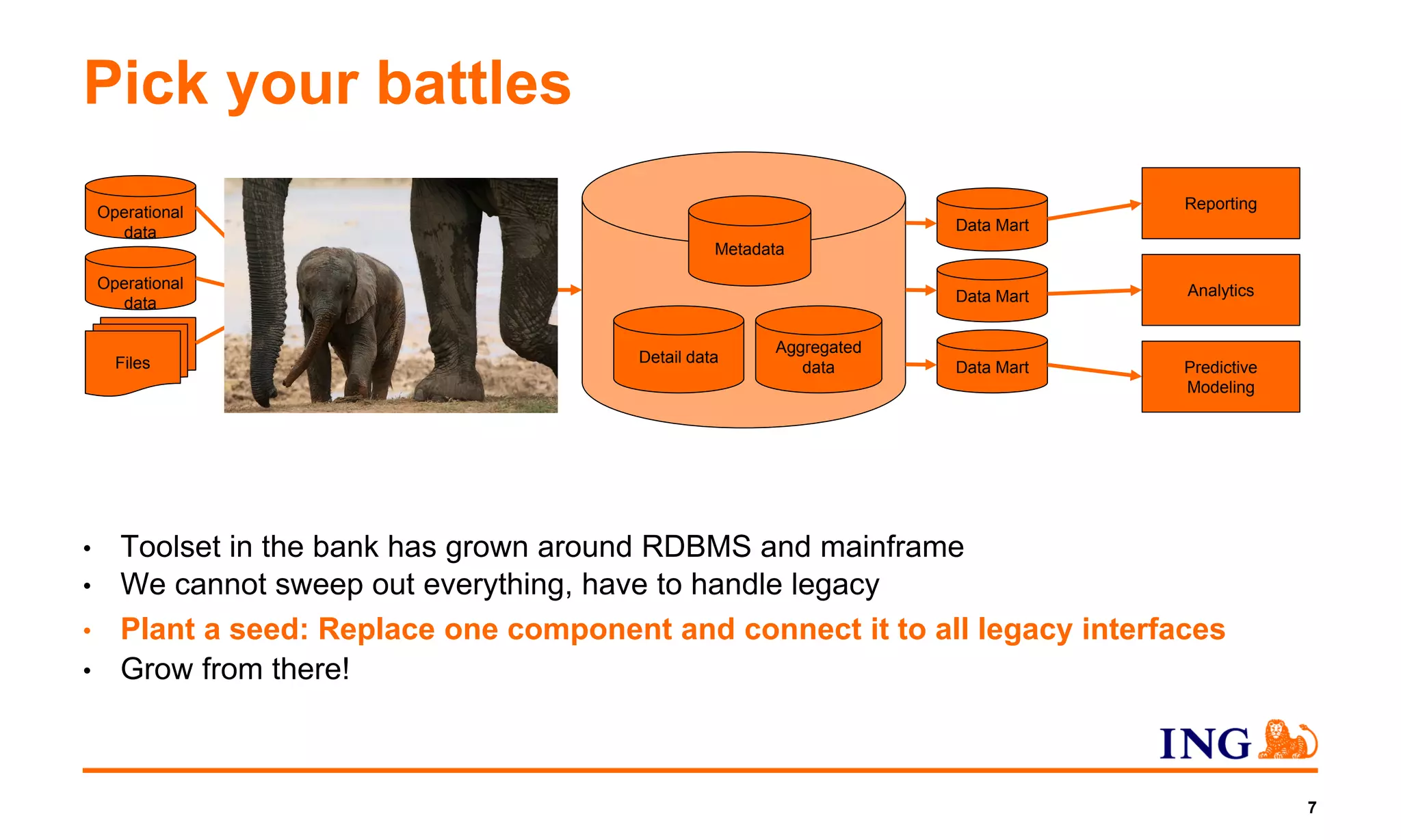
1) The document discusses ING NL's efforts to integrate all of its data sources into a single data lake platform using open source software like Hadoop where possible.
2) It focuses on one part of creating a data lake archive to collect, securely store, and make data available to analytical applications in a unified format.
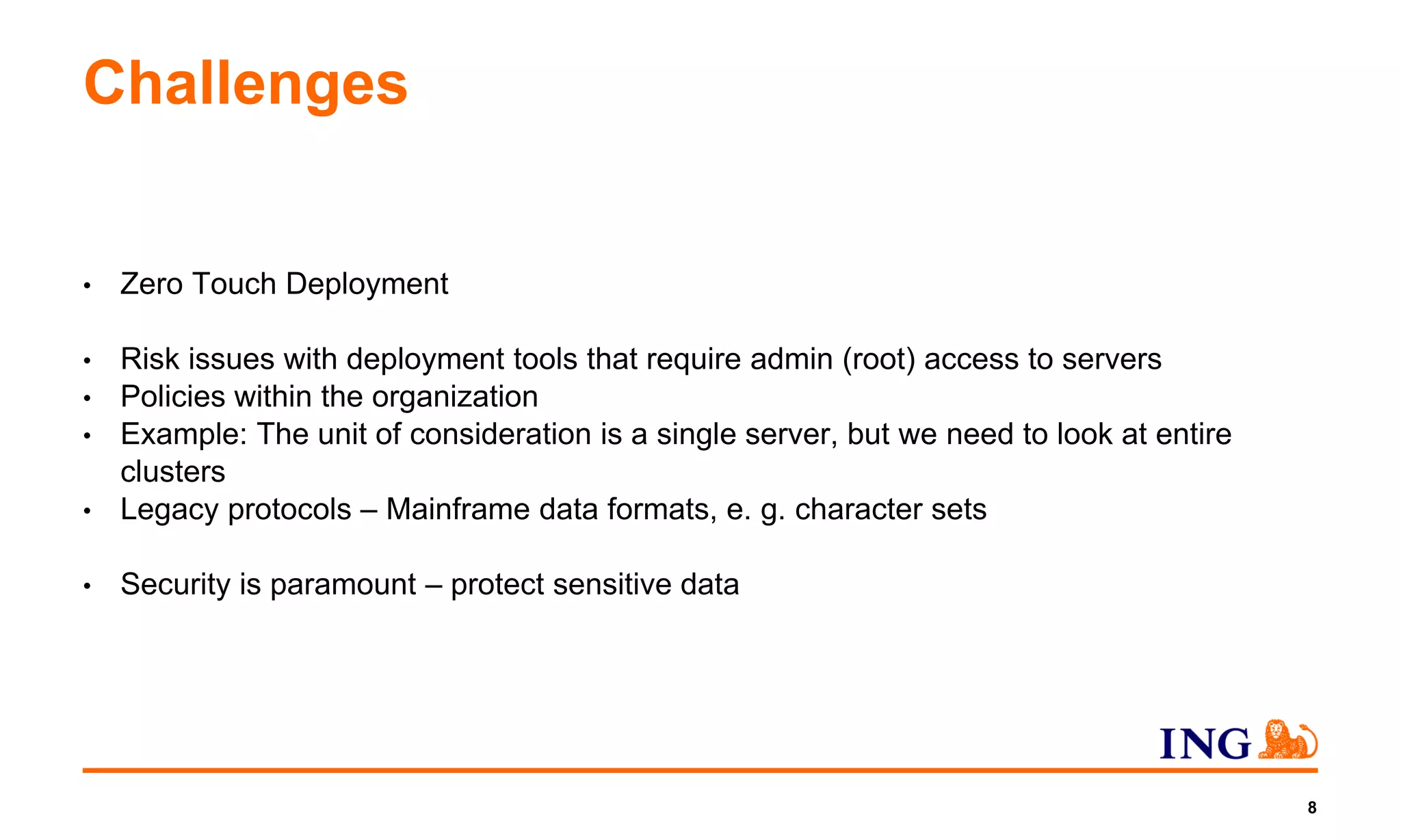
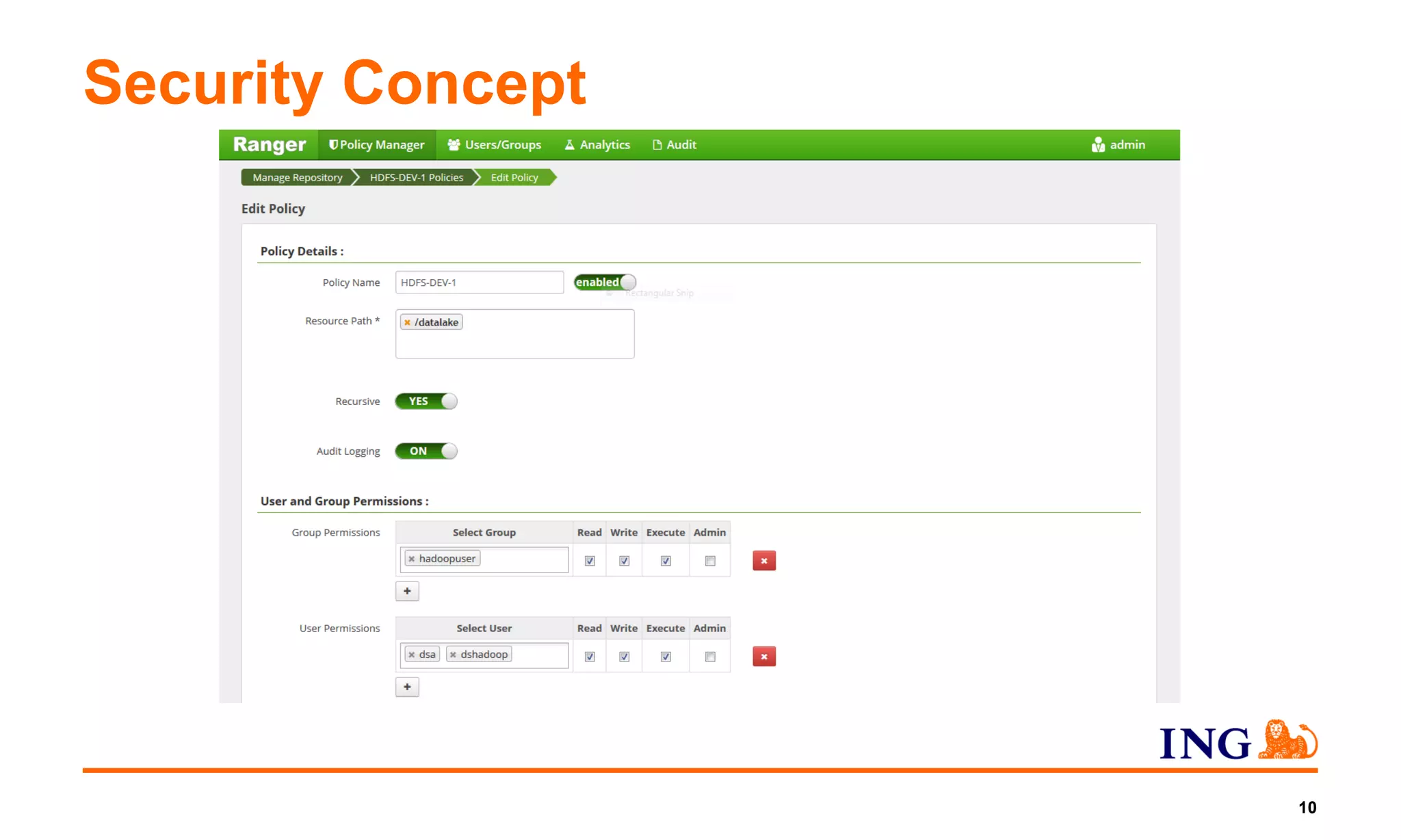
3) Challenges discussed include replacing legacy systems, addressing policies and security requirements, and ensuring agile delivery through interdisciplinary cooperation.