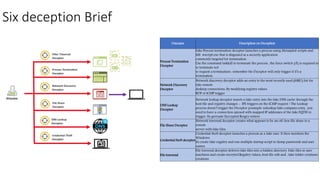
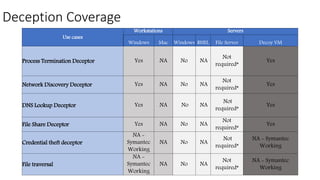
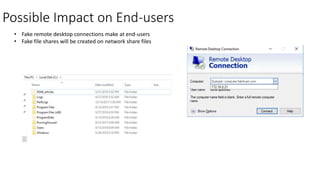
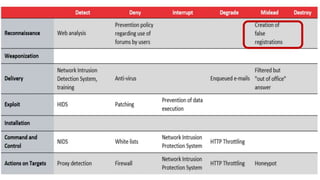
The document describes six deception techniques used by Symantec deception tools: 1) Process termination deceptor disguises a security process to trigger when terminated, 2) Network discovery deceptor adds fake remote desktop connections to trigger on discovery, 3) DNS lookup deceptor inserts fake DNS entries to trigger on lookups, 4) File share deceptor creates apparent off-box file shares to trigger on access, 5) Credential theft deceptor launches a fake user to monitor for password dumping, and 6) File traversal deceptor delivers fake files to hidden directories to trigger on access. However, the deceptions may be easily detected by hackers and could negatively impact threat hunting and forensic analysis by generating noisy anomalous activity that obscures real threats.