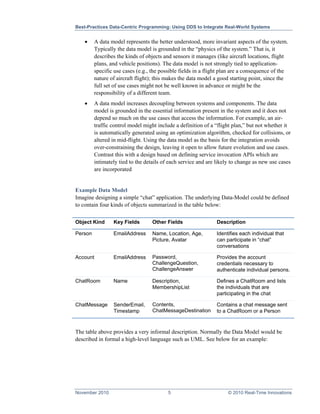
The document discusses best practices for data-centric programming using the Data Distribution Service (DDS) to integrate complex, real-world systems that interact with physical environments, like air traffic control and robotic systems. It emphasizes the importance of defining a robust data model and outlines guidelines for effective DDS implementation, including using keyed topics, managing system quality of service (QoS), and creating modular architectures. Overall, the whitepaper advocates for a standardized, modular approach to enhance interoperability and simplify integration across diverse technologies and platforms.