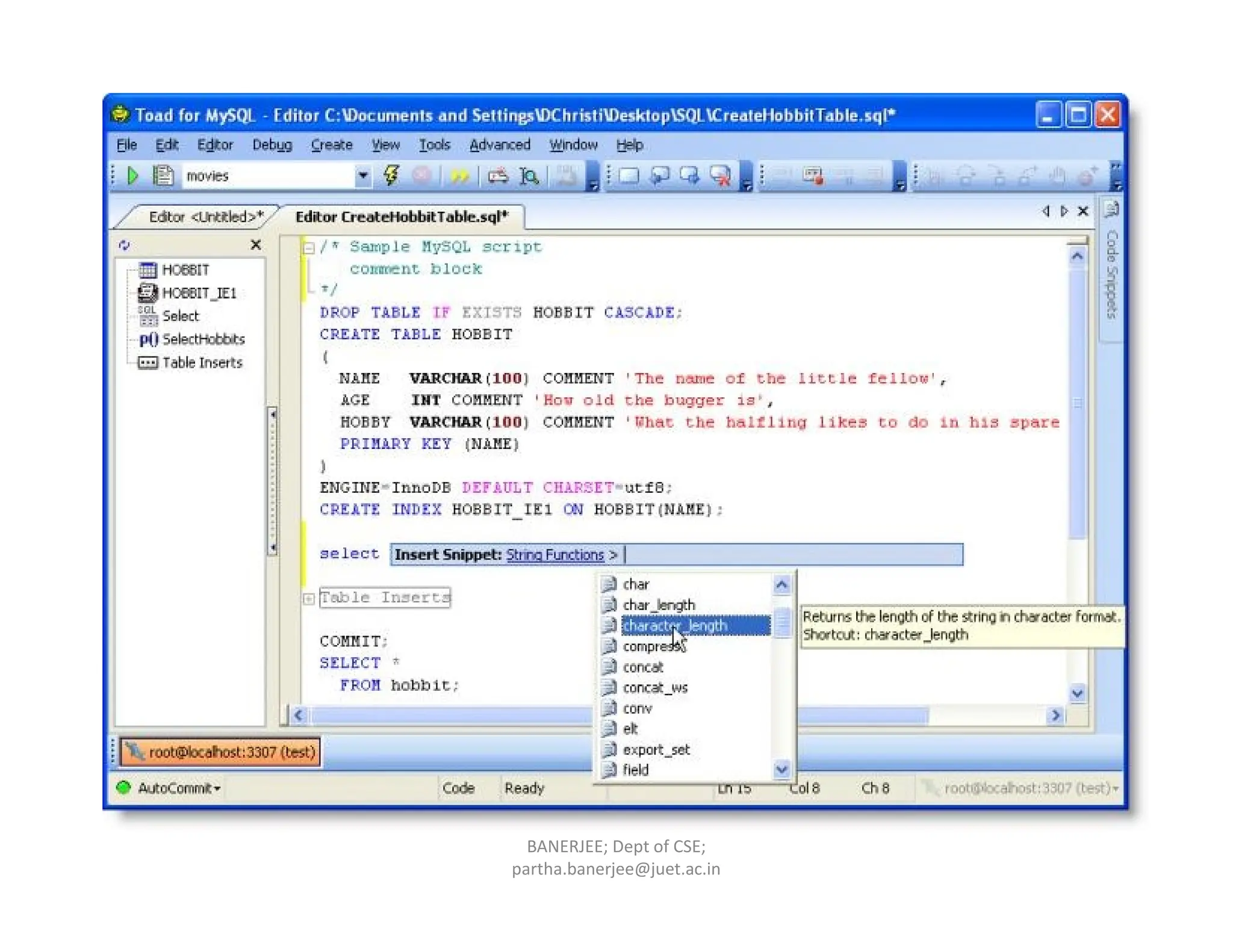
The document provides an overview of various database systems, their models, and languages used for data definition and manipulation. It outlines models such as inverted file, flat, multidimensional, semistructured, and relational models, as well as the role of Data Definition Language (DDL), Data Manipulation Language (DML), and other associated languages. It also discusses key constraints like primary, foreign, and unique keys in the context of database management.