Logging Database Activity for PCI Compliance
•Download as DOCX, PDF•
0 likes•381 views
Logging of Databases for Effective Security Monitoring and Compliance with PCI DSS outlines 9 key database events that should be logged to comply with PCI DSS requirements, including: 1) additions, removals, or modifications of user IDs; 2) changes to passwords or privileges; 3) changes to system-level objects; 4) individual access to cardholder data; 5) starting and stopping databases; 6) user logins and logouts; 7) failed logon attempts; and 9) clearing of audit trails. The document provides a suggested list of important database logging events for PCI compliance and effective security monitoring.
Report
Share
Report
Share
Recommended
More Related Content
What's hot
What's hot (6)
Similar to Logging Database Activity for PCI Compliance
Similar to Logging Database Activity for PCI Compliance (20)
DataStax | Best Practices for Securing DataStax Enterprise (Matt Kennedy) | C...

DataStax | Best Practices for Securing DataStax Enterprise (Matt Kennedy) | C...
Analysis of Various Attributes to Have a Secure Database

Analysis of Various Attributes to Have a Secure Database
Supporting Privacy Protection In Personalized Web Search

Supporting Privacy Protection In Personalized Web Search
IRJET- Analysis of using Software Defined and Service Coherence Approach

IRJET- Analysis of using Software Defined and Service Coherence Approach
KP Partners: DataStax and Analytics Implementation Methodology

KP Partners: DataStax and Analytics Implementation Methodology
IRJET - Scrutinize the Utility of Preserved Data with Privacy

IRJET - Scrutinize the Utility of Preserved Data with Privacy
Recently uploaded
Top Rated Pune Call Girls Talegaon Dabhade ⟟ 6297143586 ⟟ Call Me For Genuin...

Top Rated Pune Call Girls Talegaon Dabhade ⟟ 6297143586 ⟟ Call Me For Genuin...Call Girls in Nagpur High Profile
Recently uploaded (10)
Best VIP Call Girls Noida Sector 51 Call Me: 8448380779

Best VIP Call Girls Noida Sector 51 Call Me: 8448380779
The 15 Minute Breakdown: 2024 Beauty Marketing Study

The 15 Minute Breakdown: 2024 Beauty Marketing Study
Best VIP Call Girls Noida Sector 50 Call Me: 8448380779

Best VIP Call Girls Noida Sector 50 Call Me: 8448380779
Best VIP Call Girls Noida Sector 55 Call Me: 8448380779

Best VIP Call Girls Noida Sector 55 Call Me: 8448380779
Film= Dubai Call Girls O525547819 Call Girls Dubai Whsatapp

Film= Dubai Call Girls O525547819 Call Girls Dubai Whsatapp
The 15 Minute Breakdown: 2024 Beauty Marketing Study

The 15 Minute Breakdown: 2024 Beauty Marketing Study
Dubai Call Girls O525547&19 (Asii) Call Girls Dubai

Dubai Call Girls O525547&19 (Asii) Call Girls Dubai
Indian Call Girl In Dubai #$# O5634O3O18 #$# Dubai Call Girl

Indian Call Girl In Dubai #$# O5634O3O18 #$# Dubai Call Girl
Top Rated Pune Call Girls Talegaon Dabhade ⟟ 6297143586 ⟟ Call Me For Genuin...

Top Rated Pune Call Girls Talegaon Dabhade ⟟ 6297143586 ⟟ Call Me For Genuin...
Logging Database Activity for PCI Compliance
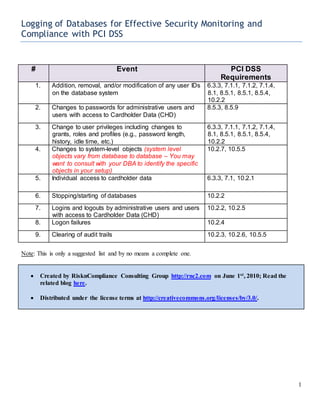
- 1. Logging of Databases for Effective Security Monitoring and Compliance with PCI DSS 1 # Event PCI DSS Requirements 1. Addition, removal, and/or modification of any user IDs on the database system 6.3.3, 7.1.1, 7.1.2, 7.1.4, 8.1, 8.5.1, 8.5.1, 8.5.4, 10.2.2 2. Changes to passwords for administrative users and users with access to Cardholder Data (CHD) 8.5.3, 8.5.9 3. Change to user privileges including changes to grants, roles and profiles (e.g., password length, history, idle time, etc.) 6.3.3, 7.1.1, 7.1.2, 7.1.4, 8.1, 8.5.1, 8.5.1, 8.5.4, 10.2.2 4. Changes to system-level objects (system level objects vary from database to database – You may want to consult with your DBA to identify the specific objects in your setup) 10.2.7, 10.5.5 5. Individual access to cardholder data 6.3.3, 7.1, 10.2.1 6. Stopping/starting of databases 10.2.2 7. Logins and logouts by administrative users and users with access to Cardholder Data (CHD) 10.2.2, 10.2.5 8. Logon failures 10.2.4 9. Clearing of audit trails 10.2.3, 10.2.6, 10.5.5 Note: This is only a suggested list and by no means a complete one. Created by RisknCompliance Consulting Group http://rnc2.com on June 1st, 2010; Read the related blog here. Distributed under the license terms at http://creativecommons.org/licenses/by/3.0/.
