Unix logging
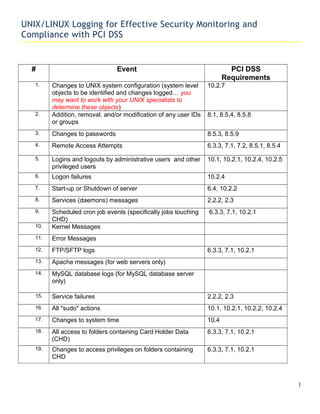
- 1. UNIX/LINUX Logging for Effective Security Monitoring and Compliance with PCI DSS # Event PCI DSS Requirements 1. Changes to UNIX system configuration (system level objects to be identified and changes logged… you may want to work with your UNIX specialists to determine these objects) 10.2.7 2. Addition, removal, and/or modification of any user IDs or groups 8.1, 8.5.4, 8.5.8 3. Changes to passwords 8.5.3, 8.5.9 4. Remote Access Attempts 6.3.3, 7.1, 7.2, 8.5.1, 8.5.4 5. Logins and logouts by administrative users and other privileged users 10.1, 10.2.1, 10.2.4, 10.2.5 6. Logon failures 10.2.4 7. Start-up or Shutdown of server 6.4, 10.2.2 8. Services (daemons) messages 2.2.2, 2.3 9. Scheduled cron job events (specifically jobs touching CHD) 6.3.3, 7.1, 10.2.1 10. Kernel Messages 11. Error Messages 12. FTP/SFTP logs 6.3.3, 7.1, 10.2.1 13. Apache messages (for web servers only) 14. MySQL database logs (for MySQL database server only) 15. Service failures 2.2.2, 2.3 16. All "sudo" actions 10.1, 10.2.1, 10.2.2, 10.2.4 17. Changes to system time 10.4 18. All access to folders containing Card Holder Data (CHD) 6.3.3, 7.1, 10.2.1 19. Changes to access privileges on folders containing CHD 6.3.3, 7.1, 10.2.1 1
- 2. UNIX/LINUX Logging for Effective Security Monitoring and Compliance with PCI DSS # Event PCI DSS Requirements 20. All access to files containing CHD 6.3.3, 7.1, 10.2.1 21. Changes to access privileges on files containing CHD 6.3.3, 7.1, 10.2.1 22. Creation or deletion of files in folders containing CHD 10.2.1 Note: This is only a suggested list and by no means a complete one. • Created by RisknCompliance Consulting Group http://rnc2.com on June 1st , 2010; Read the related blog here. • Distributed under the license terms at http://creativecommons.org/licenses/by/3.0/. 2
