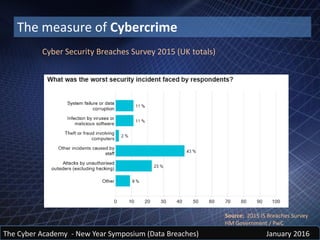
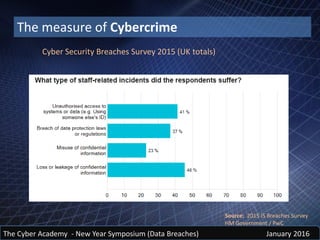
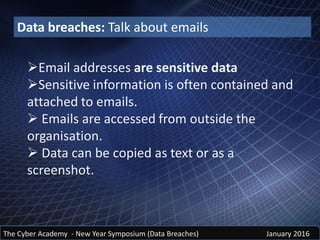
The document discusses insider threats and data breaches. It notes that insiders are often the source of initial data leaks, though they may not be responsible for catastrophic breaches. It examines past data leaks and the people responsible, such as Bradley Manning, Hervé Falciani, and Edward Snowden. The cost of cybercrime and data breaches is immense and increasing yearly. However, the full cost is difficult to measure due to unreported incidents and indirect costs. Common sources of data breaches are theft of equipment or data, mobile devices, removable media, email, and social media oversharing of information. Social engineering techniques like phishing, spear phishing, and whaling are effective because they use personal data obtained