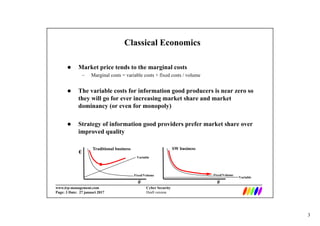
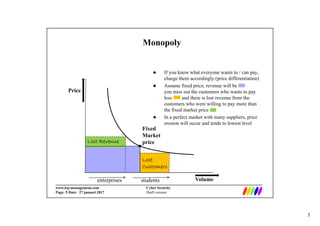
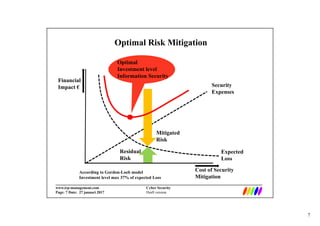
This document discusses cyber security economics and the market for security services/products. It notes that information goods have high fixed costs and near zero variable costs, so providers focus on growth and market dominance. This can lead to asymmetric incentives and quality issues as buyers cannot assess security software quality. The market for security services is also a battlefield for market dominance where providers prioritize market share over quality once dominant. Optimal risk mitigation involves balancing security expenses against expected losses from risks. Metrics for security include controls, vulnerabilities, incidents and losses, but many are difficult to measure deterministically.