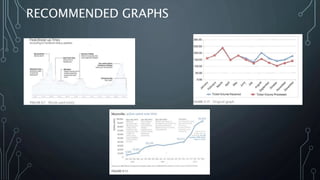
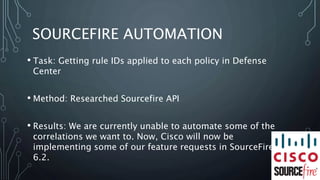
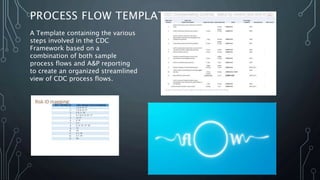
This document outlines objectives for improving a cyber defense framework. It includes mapping critical security controls to existing controls, evaluating additional controls, and recommending improved data visualizations. The objectives are to document validation methods for controls, suggest new visualization approaches like multi-level doughnut graphs, and create a process flow template based on audit reports. Automating some tasks in the Sourcefire tool was explored but certain correlations cannot yet be automated. Overall, the experience provided insight into the framework and opportunities for more defined objectives and scope, specific deliverables, and regular communication were identified.