This document provides information about breaking the FEAL 4.3 block cipher that was used in the CRYPT0 300 challenge of the CSAW CTF 2014 quals. It describes using differential cryptanalysis to find the encryption subkeys (K0-K5) by analyzing the differences in plaintext and ciphertext pairs. It includes code examples of analyzing differential values at each round to iteratively determine each subkey value. After determining all subkeys, the document shows how to decrypt the flag values and obtain the final flag.


![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
DIFFERENTIAL VALUE
In [1]: import array
In [2]: %paste
def rot3(x):
return ((x<<3)|(x>>5))&0xff
def gBox(a,b,mode):
return rot3((a+b+mode)%256)
def fBox(plain):
(snip.)
In [3]: x1 = array.array("B", "80800000".decode("hex"))
In [4]: fBox(x1)
Out[4]: [10, 64, 8, 68]
In [5]: x2 = array.array("B", "00000000".decode("hex"))
In [6]: fBox(x2)
Out[6]: [10, 64, 8, 64]
In [7]: for a, b in zip(fBox(x1), fBox(x2)):
print a ^ b,
....:
0 0 0 4 ΔY = 0x00000004](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-6-320.jpg)

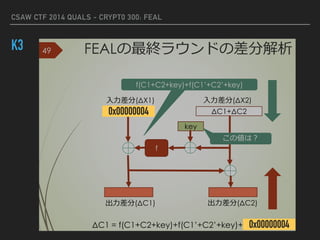
![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
K3
k3 = None
if k3 == None:
print "[*] start k3 attack"
p1, p2, c1, c2, dc1, dc2, dcL, dcR = get_dataset(f, n,
array.array(“B”,"8080000080800000".decode("hex")))
for k3 in xrange(65536):
k3 = array.array("B", "%04x"%k3)
for i in xrange(n):
if dcL[i] != list_xor(
list_xor(
fBox(list_xor(dc1[i], k3)),
fBox(list_xor(dc2[i], k3))),
array("B", “00000004”.decode("hex"))
):
break
else:
print "[*] found k3: %s" % "".join(map(chr, k3))
break
else:
print "[!] could not find k3"
return
SUBKEY is hex string
Multiple candidates will be find
if you use few plainest sets](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-9-320.jpg)
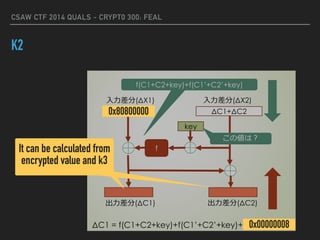
![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
K2
for i in xrange(n):
c1L = list_xor(c1[i][:4], c1[i][4:])
c1R = list_xor(c1[i][:4],
fBox(list_xor(k3, list_xor(c1[i][4:], c1[i][:4]))))
c2L = list_xor(c2[i][:4], c2[i][4:])
c2R = list_xor(c2[i][:4],
fBox(list_xor(k3, list_xor(c2[i][4:], c2[i][:4]))))
c1[i] = c1L + c1R
c2[i] = c2L + c2R
dcL[i] = list_xor(c1L, c2L)
for k2 in xrange(65536):
k2 = array.array("B", "%04x"%k2)
for i in xrange(n):
if dcL[i] != list_xor(
list_xor(
fBox(list_xor(c1[i][4:], k2)),
fBox(list_xor(c2[i][4:], k2))),
array("B", "80800000".decode("hex"))):
break
else:
print "[*] found k2: %s" % "".join(map(chr, k2))
break
else:
print "[!] could not find k2"
return
Calculate ΔC1, ΔC2 using k3](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-11-320.jpg)


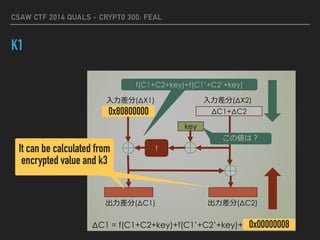
![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
K1
p1, p2, c1, c2, dc1, dc2, dcL, dcR = get_dataset(f, n,
array.array("B","0000000040000000".decode("hex")))
for i in xrange(n):
c1L = list_xor(c1[i][:4], c1[i][4:])
c1R = list_xor(c1[i][:4],
fBox(list_xor(k3, list_xor(c1[i][4:], c1[i][:4]))))
c2L = list_xor(c2[i][:4], c2[i][4:])
c2R = list_xor(c2[i][:4],
fBox(list_xor(k3, list_xor(c2[i][4:], c2[i][:4]))))
c1[i] = c1L + c1R
c2[i] = c2L + c2R
dcL[i] = list_xor(c1L, c2L)
c1L = c1[i][4:]
c1R = list_xor(c1[i][:4], fBox(list_xor(k2, c1[i][4:])))
c2L = c2[i][4:]
c2R = list_xor(c2[i][:4], fBox(list_xor(k2, c2[i][4:])))
c1[i] = c1L + c1R
c2[i] = c2L + c2R
dcL[i] = list_xor(c1L, c2L)
for k1 in xrange(65536):
k1 = array.array("B", "%04x"%k1)
for i in xrange(n):
if dcL[i] != list_xor(
list_xor(
fBox(list_xor(c1[i][4:], k2)),
fBox(list_xor(c2[i][4:], k2))),
array("B", "80800000".decode("hex"))):](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-15-320.jpg)

![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
K0
for i in xrange(n):
c1L = c1[i][4:]
c1R = list_xor(c1[i][:4], fBox(list_xor(k1, c1[i][4:])))
c2L = c2[i][4:]
c2R = list_xor(c2[i][:4], fBox(list_xor(k1, c2[i][4:])))
c1[i] = c1L + c1R
c2[i] = c2L + c2R
dcL[i] = list_xor(c1L, c2L)
for k0 in xrange(65536):
k0 = array.array("B", "%04x"%k0)
for i in xrange(n):
if dcL[i] != list_xor(fBox(list_xor(c1[i][4:], k0)),
fBox(list_xor(c2[i][4:], k0))):
break
else:
print "[*] found k0: %s" % "".join(map(chr, k0))
break
else:
print "[!] could not find k0"
return](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-17-320.jpg)
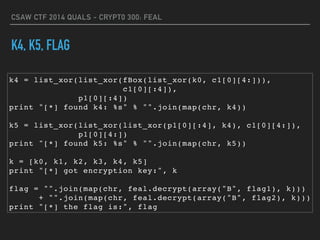
![CSAW CTF 2014 QUALS - CRYPT0 300: FEAL
K4, K5, FLAG
k4 = list_xor(list_xor(fBox(list_xor(k0, c1[0][4:])),
c1[0][:4]),
p1[0][:4])
print "[*] found k4: %s" % "".join(map(chr, k4))
k5 = list_xor(list_xor(list_xor(p1[0][:4], k4), c1[0][4:]),
p1[0][4:])
print "[*] found k5: %s" % "".join(map(chr, k5))
k = [k0, k1, k2, k3, k4, k5]
print "[*] got encryption key:", k
flag = "".join(map(chr, feal.decrypt(array("B", flag1), k)))
+ "".join(map(chr, feal.decrypt(array("B", flag2), k)))
print "[*] the flag is:", flag](https://image.slidesharecdn.com/csaw2014crypto300-160130141502/85/FEAL-CSAW-CTF-2014-Quals-Crypto300-18-320.jpg)