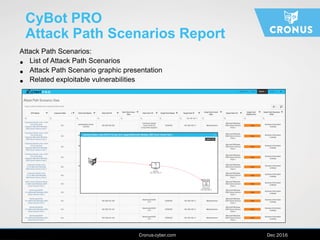
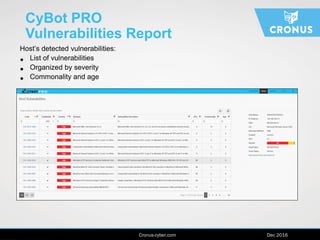
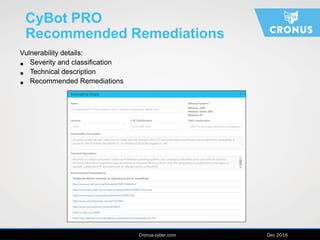
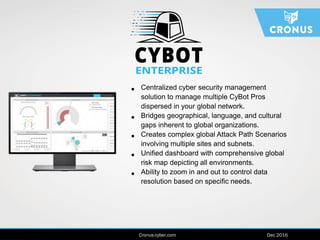
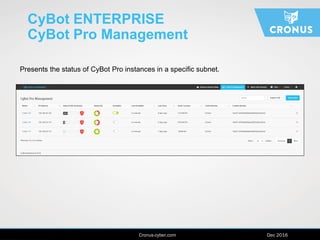
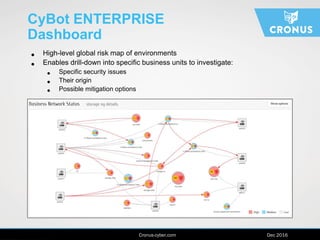
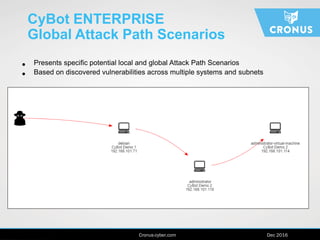
The document describes the Cybot suite from Cronus Cyber, a patented machine-based penetration testing software that evaluates organizational resilience against cyber threats and mitigates sophisticated attacks. It offers two products: Cybot Pro for individual asset scanning and Cybot Enterprise for centralized management across global networks, providing dynamic risk mapping and real-time vulnerability analysis. The solution enables continuous penetration testing and helps organizations prioritize security investments effectively.