The document proposes a new network for Corporation Techs, a large distribution company. Key points of the proposal include:
- Establishing better network access and control to keep networks safe and profitable for the 4000+ employee, 7 city, 6 country company.
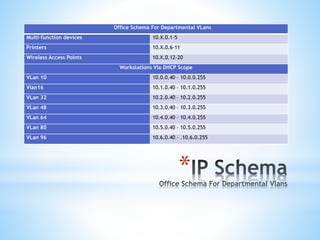
- Creating VLANs for different departments, a DMZ, and VPN for remote users. Wireless access will be on a separate network with 802.11ac and encryption.
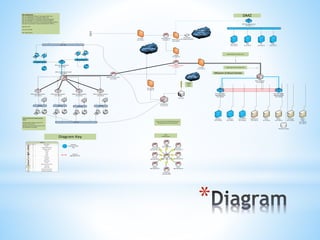
- The network will include firewalls, switches, and routers to separate traffic and improve security, performance and redundancy. Core equipment will connect regional offices to allow for communication and file sharing.