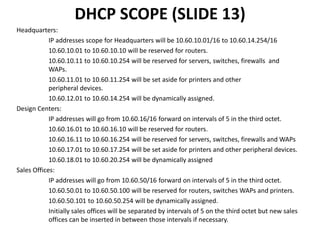
ABC Worldwide is a leading video editing and advertising company headquartered in San Francisco with 6 worldwide design centers and over 1500 employees. It was founded in 2014 by a group of friends and has annual sales of $450 million. The company provides corporate videos, commercials, films and web services.
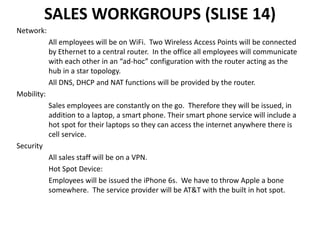
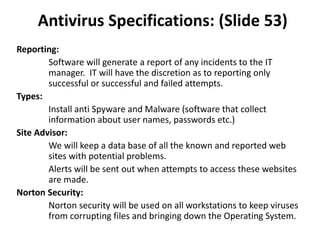
The document then describes ABC Worldwide's network infrastructure which includes redundancy, separation of networks, high speed connectivity, and scalability. It discusses the wide area network connecting the headquarters to design centers around the world, as well as security measures like firewalls, virtual private networks and quarantining of testing systems. Sales teams are provided laptops, smartphones and wireless access to maintain mobility.