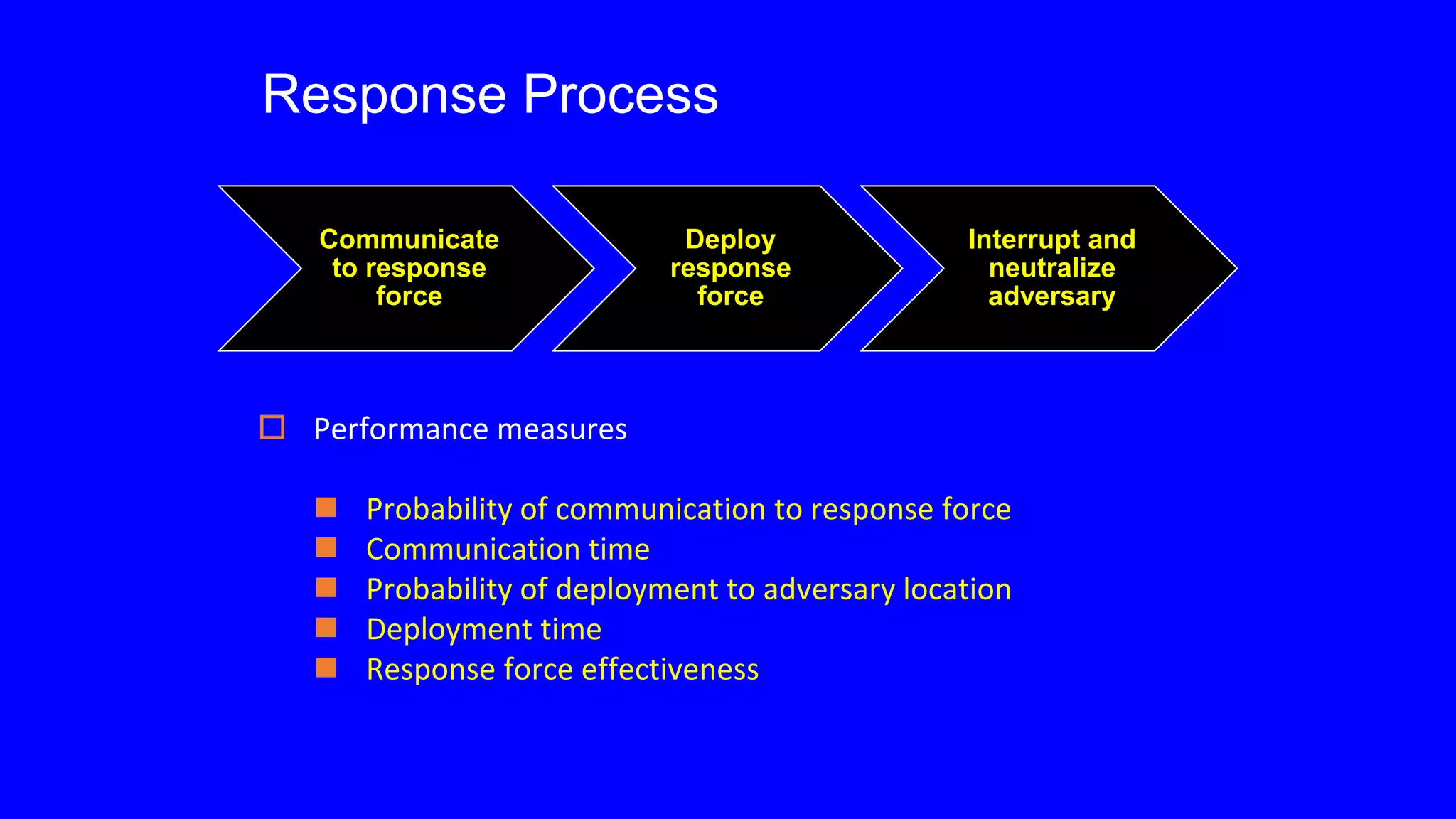
This document discusses the concept of physical protection and security. It outlines the basic functions of a physical protection system (PPS) as detection, delay, and response. The key principle is that the PPS response time must be less than the adversary's remaining task time after detection. Effective PPS design incorporates strategies like balanced protection across multiple paths, protection in depth through sequential barriers, and reliability through redundancy.