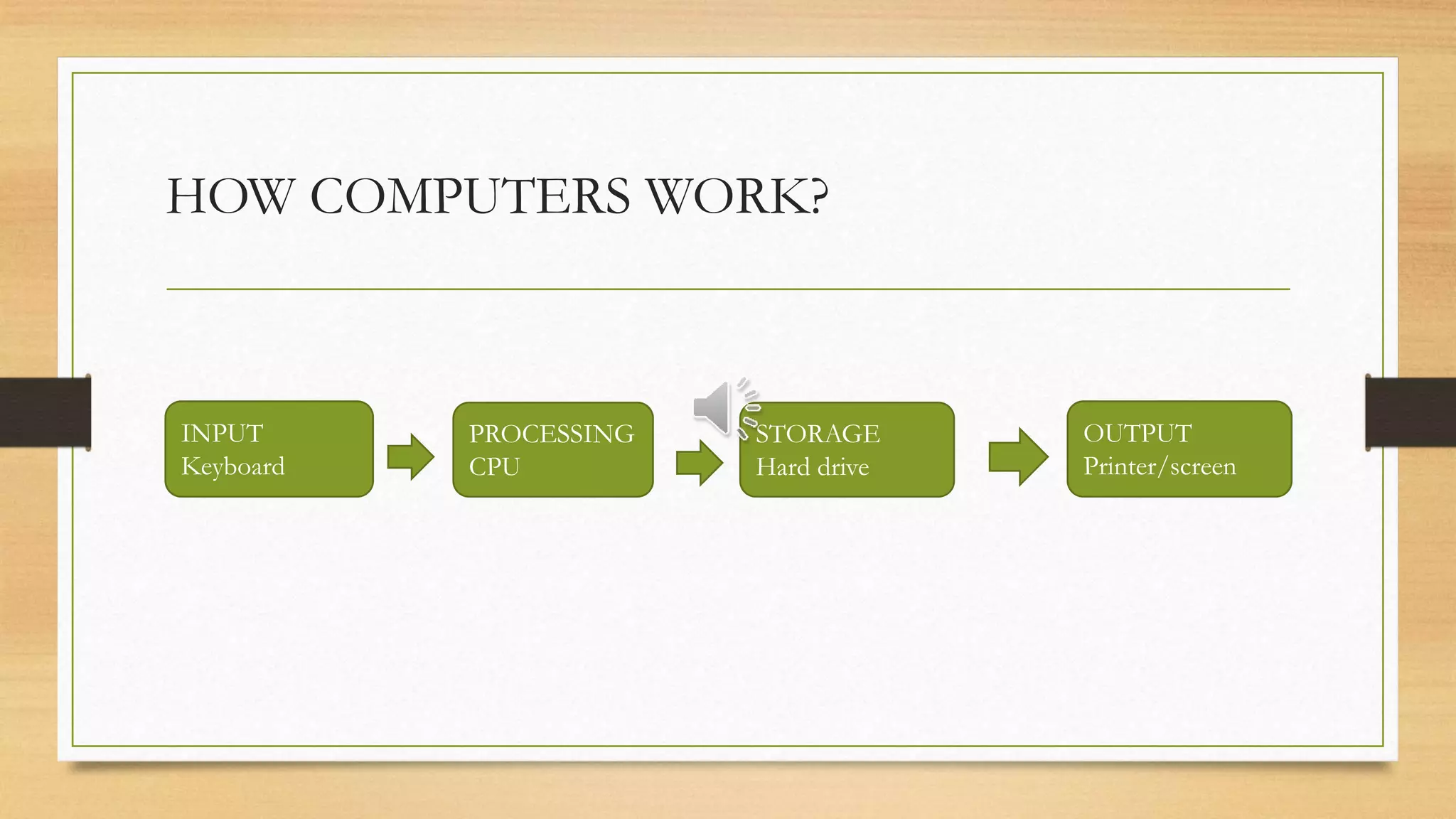
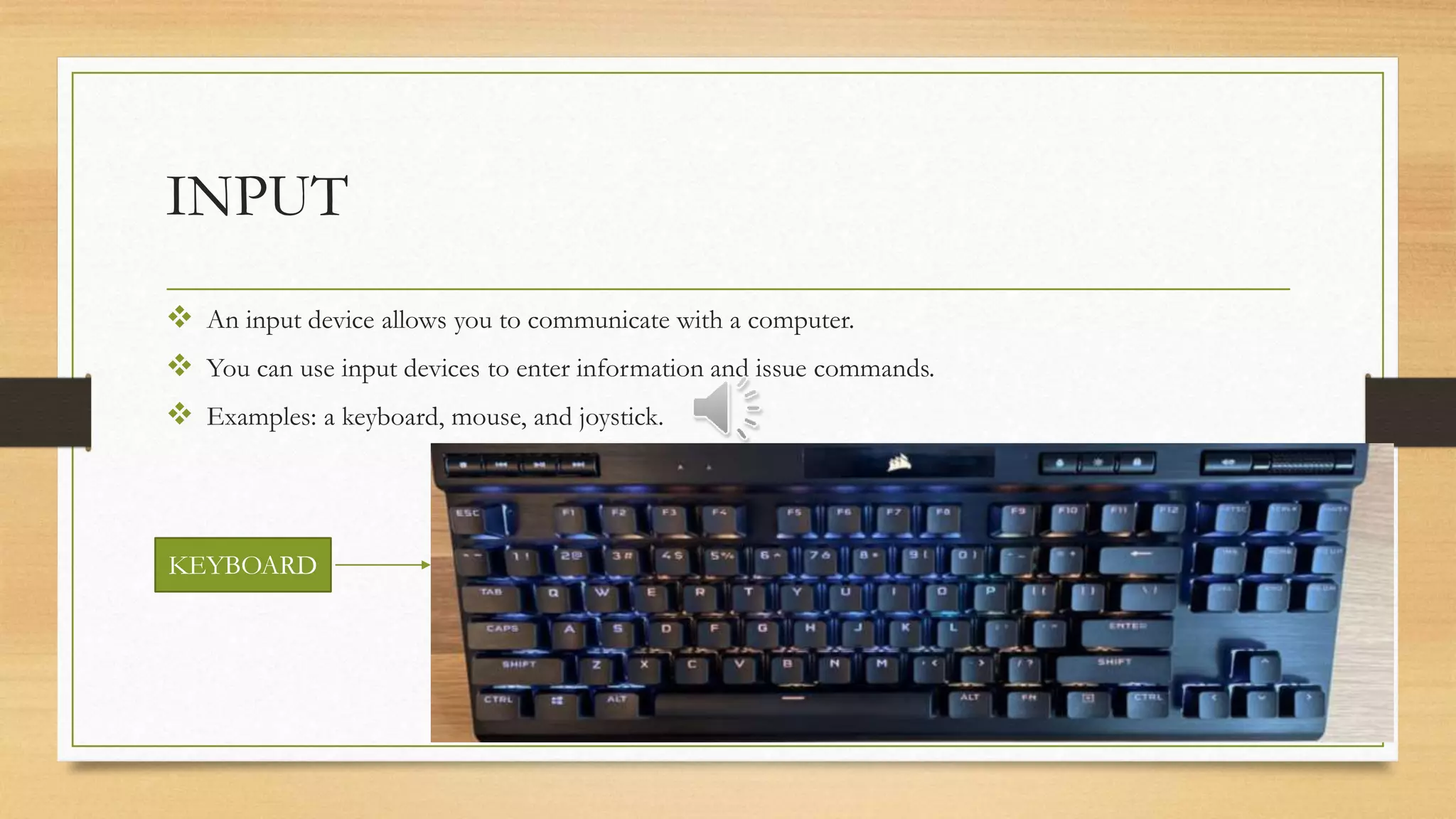
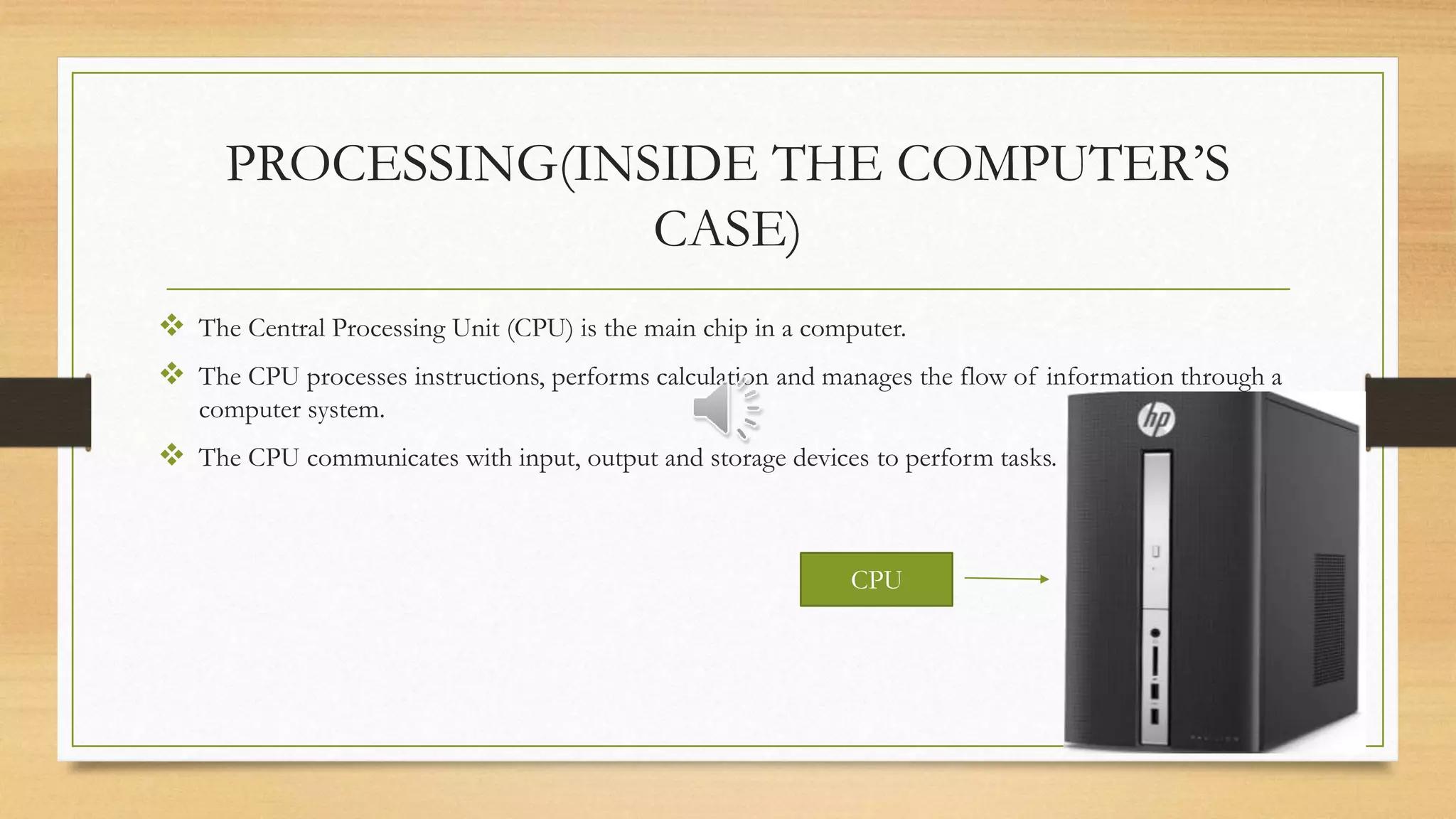
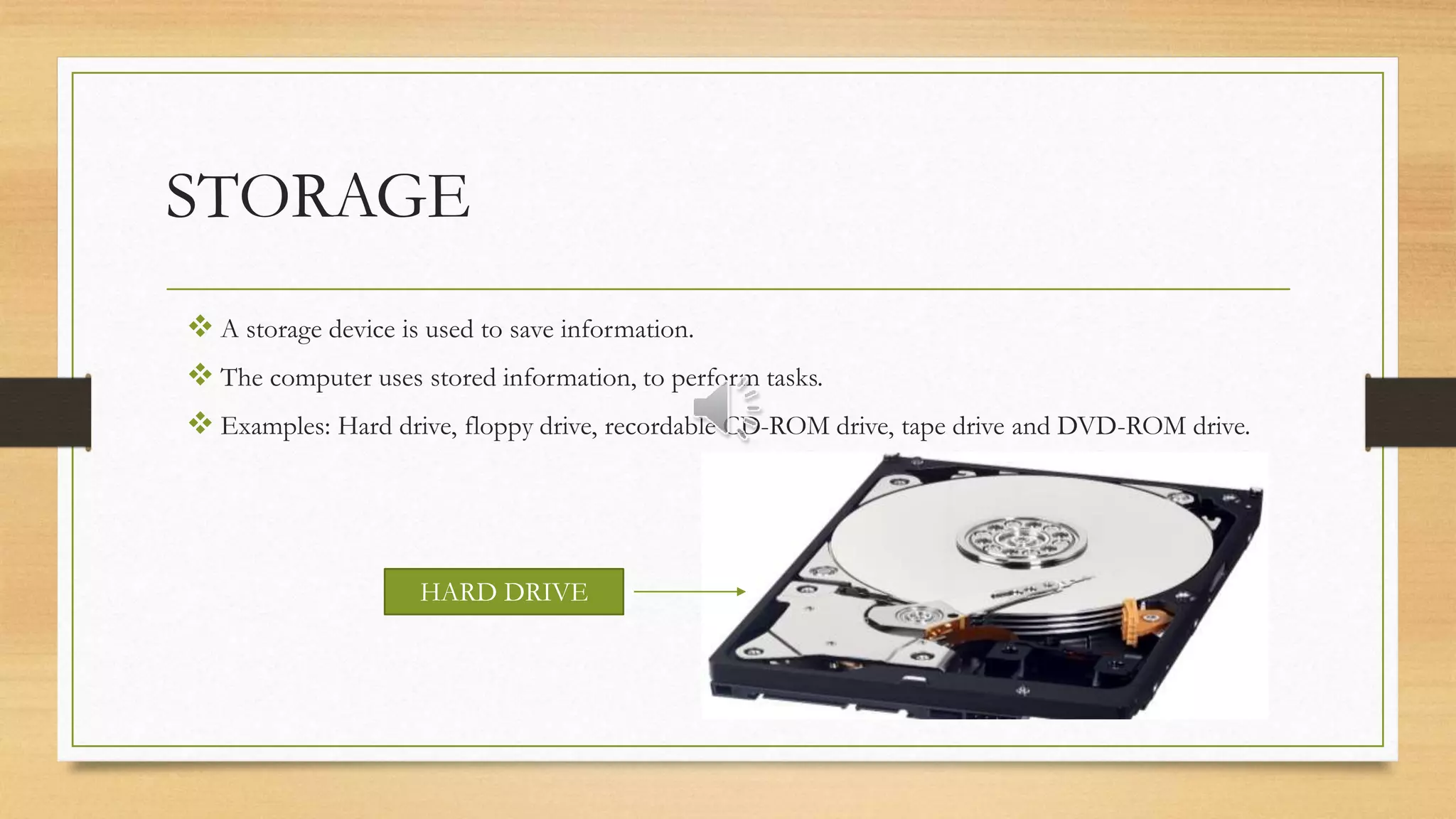
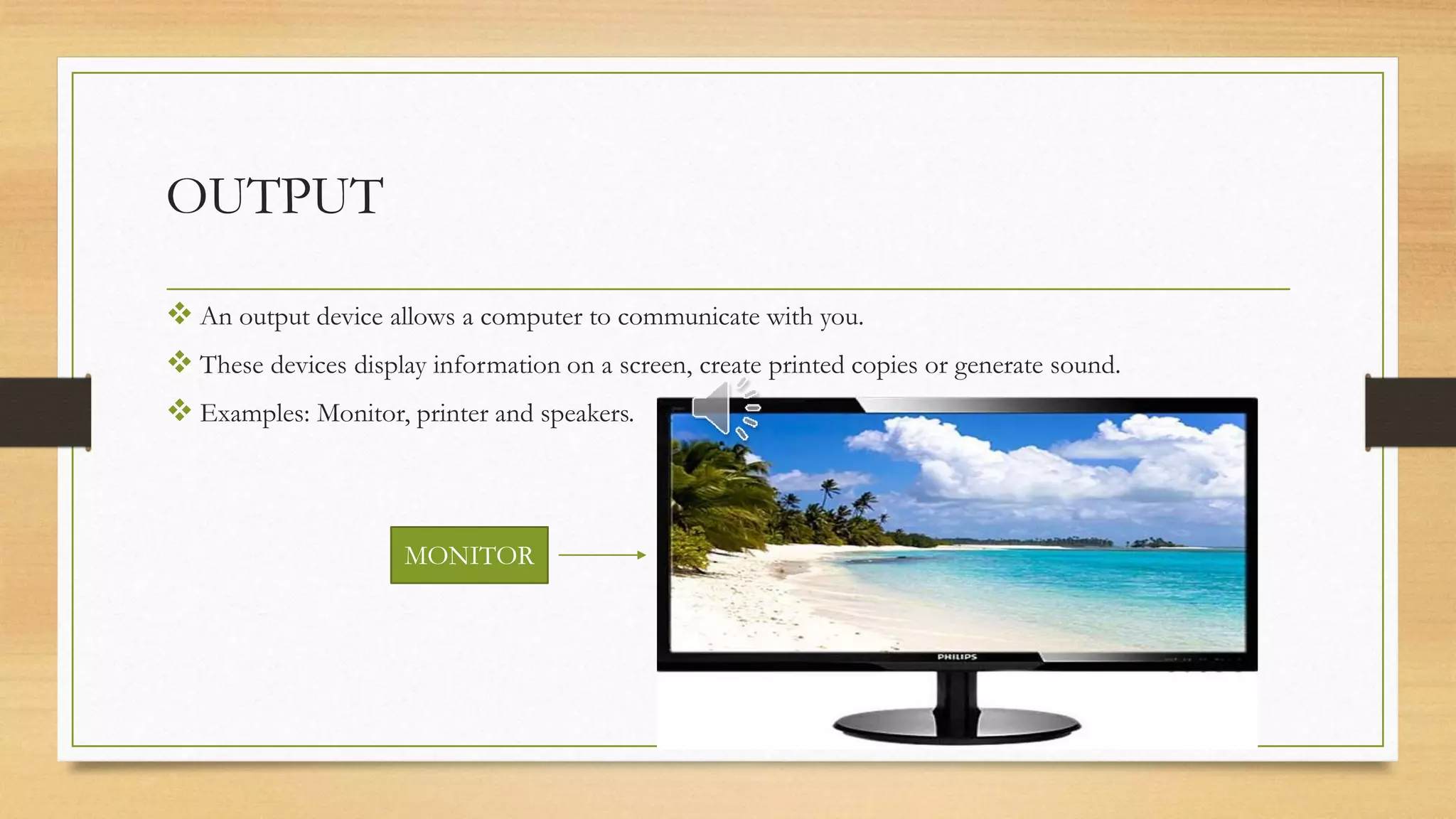
The document provides an overview of computers, defining them as electronic devices that input, process, and output data. It highlights how computers work, their advantages such as speed, accuracy, and storage, as well as disadvantages including health issues, cybersecurity threats, and environmental impacts. Additionally, it emphasizes the role of input, processing (CPU), storage, and output devices in a computer system.