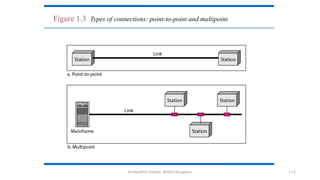
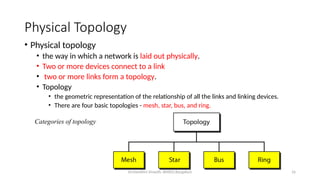
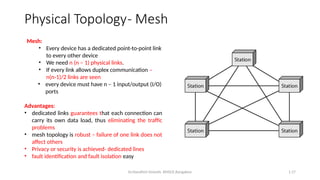
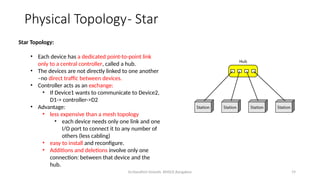
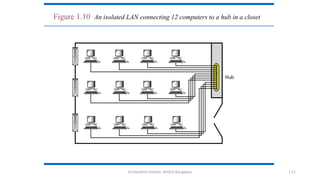
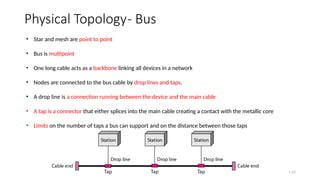
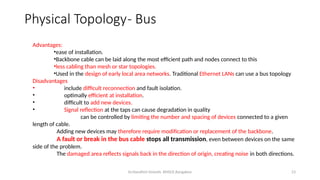
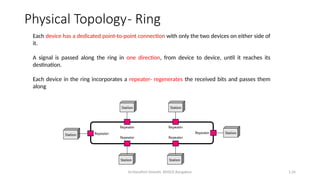
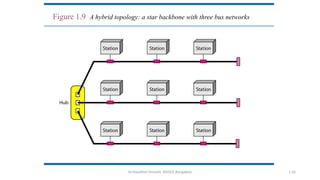
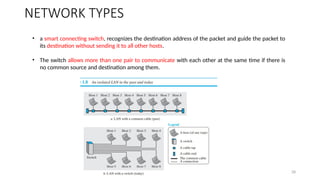
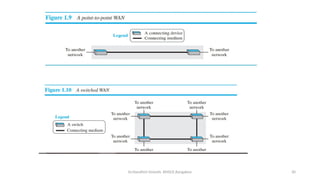
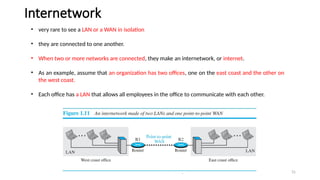
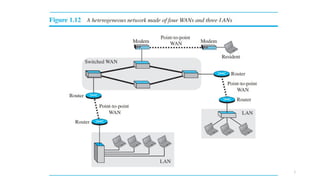
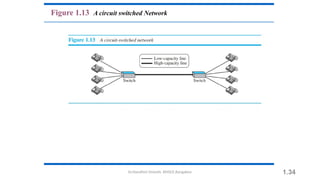
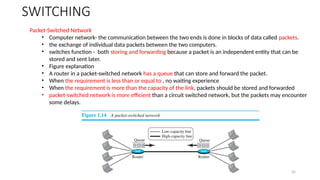
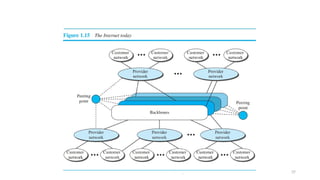
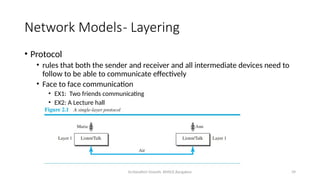
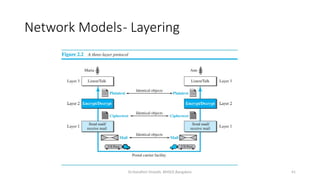
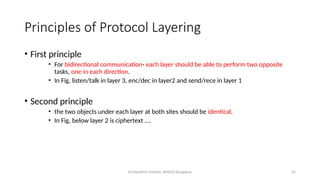
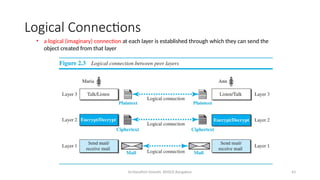
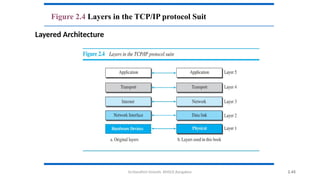
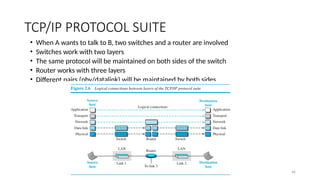
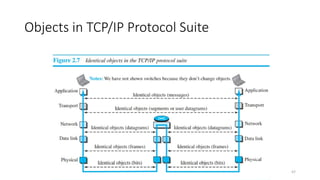
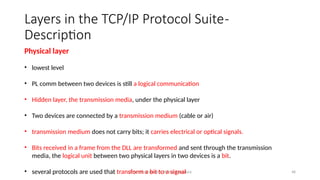
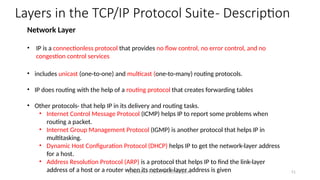
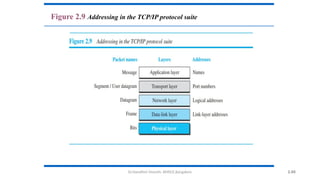
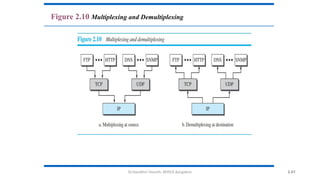
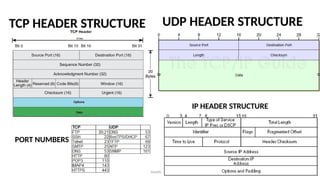
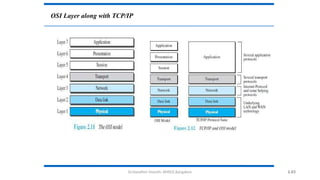
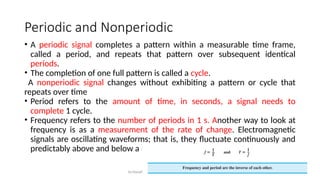
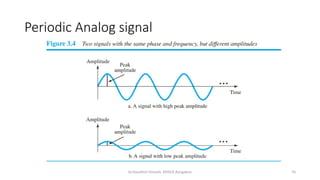
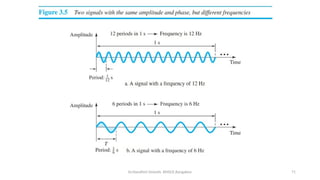
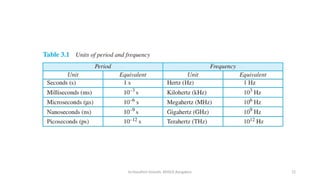
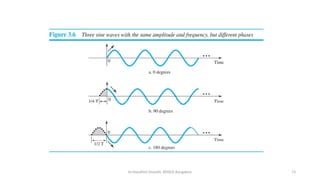
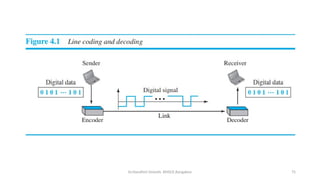
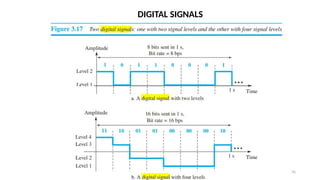
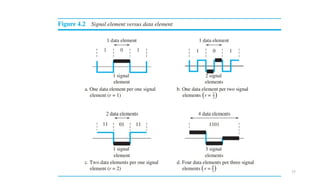
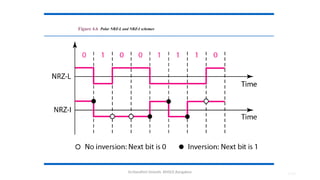
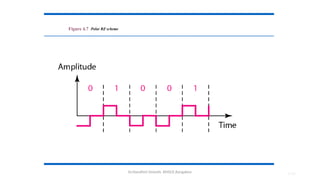
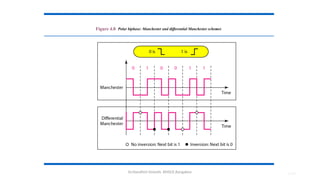
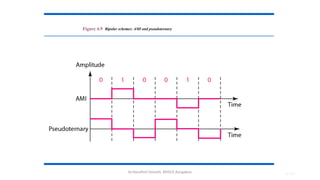
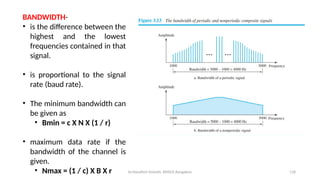
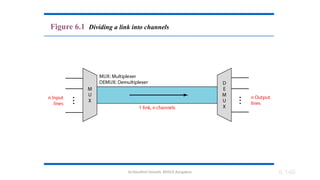
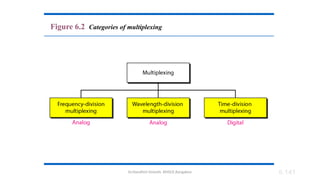
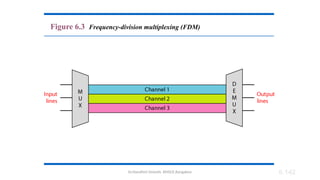
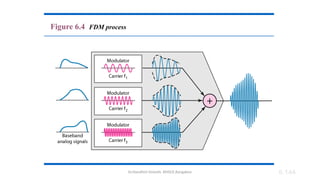
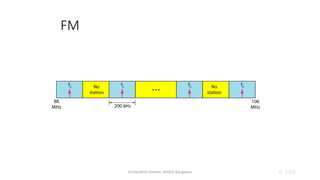
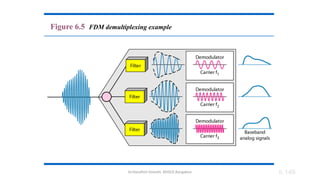
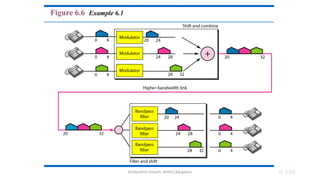
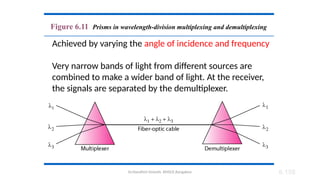
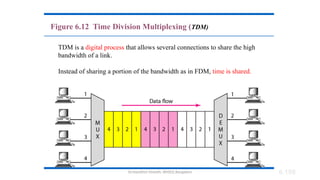
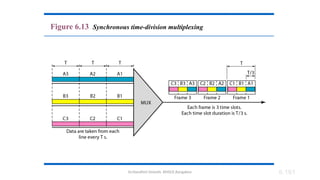
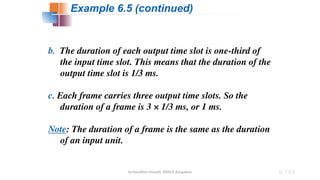
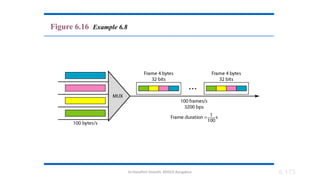
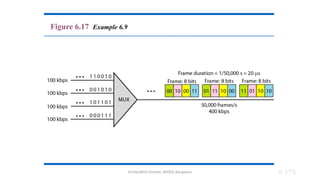
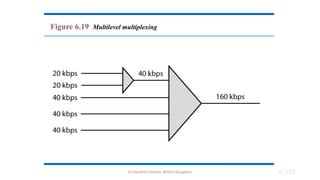
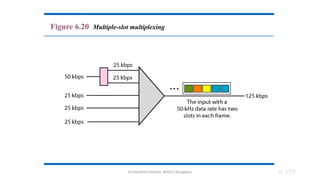
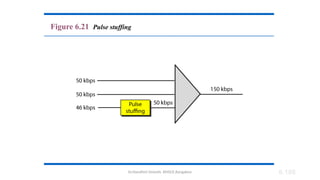
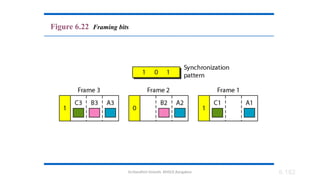
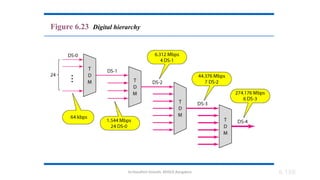
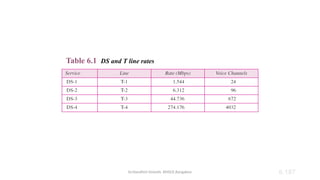
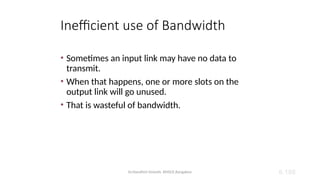
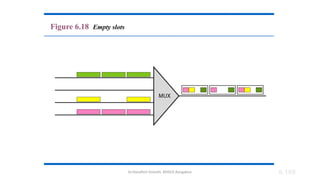
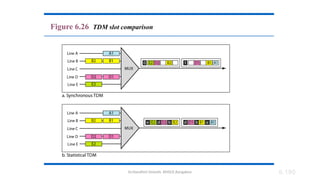
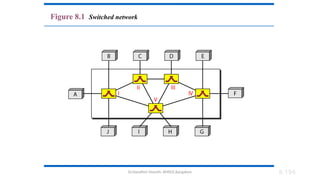
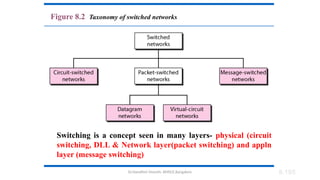
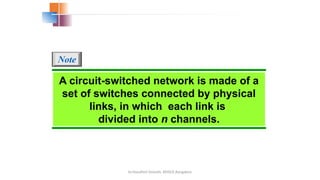
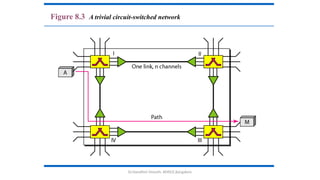
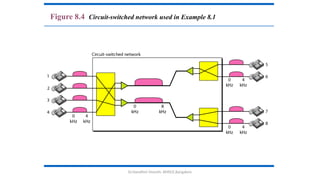
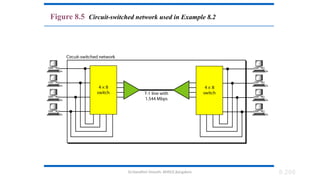
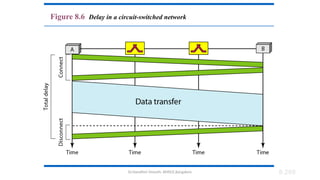
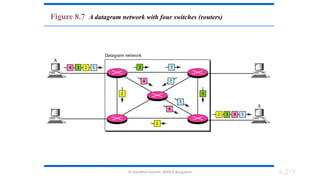
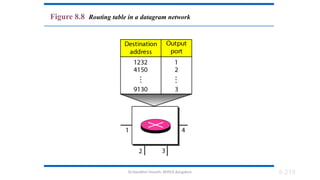
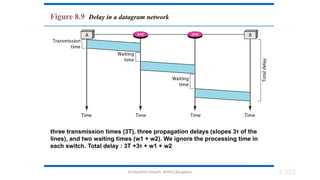
The document outlines the fundamentals of data communications and computer networks, describing key components, data representation, data flow, and network topologies. Characteristics affecting data communication include delivery, accuracy, timeliness, and jitter, while different topologies such as mesh, star, bus, and ring are discussed in terms of their advantages and disadvantages. Additionally, it differentiates between local area networks (LANs) and wide area networks (WANs), highlighting their respective scopes and ownership.