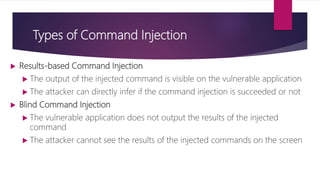
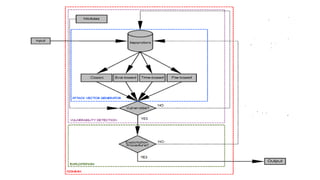
This document provides an overview of Commix, an open source tool for exploiting and testing for command injection vulnerabilities. It begins with an introduction to command injection attacks and why they occur. It then discusses the different types of command injection, including results-based and blind command injection techniques. The document outlines Commix's architecture, features, and modules. It concludes with recommendations for command injection testbeds and references for further information.