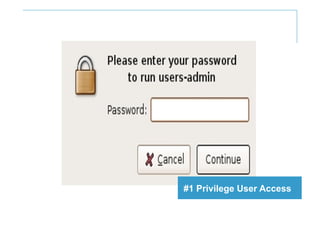
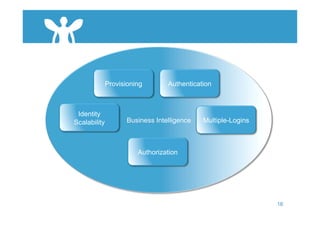
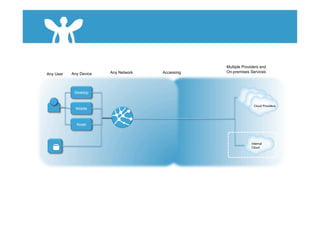
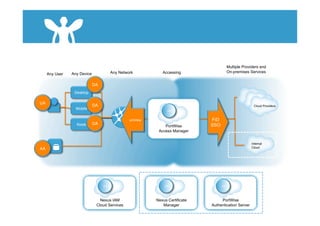
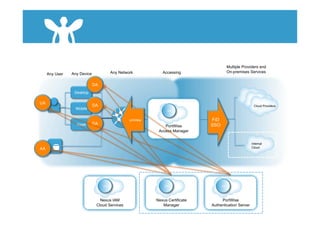
The document discusses cloud security and introduces the Nexus Cloud Security Model. It identifies some key aspects of cloud security such as privilege user access, regulatory compliance, data location, data segregation, recovery, long-term viability, and audit/investigation. The document also discusses challenges in identity and access management (IAM) when accessing cloud services and internal systems from any device on any network.