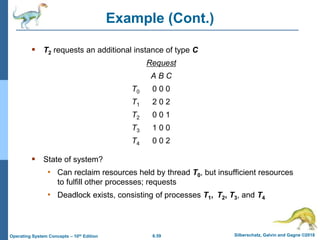
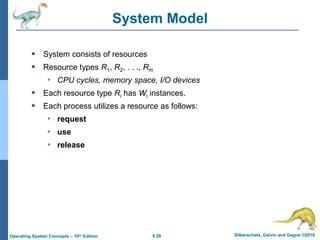
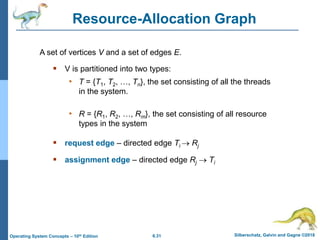
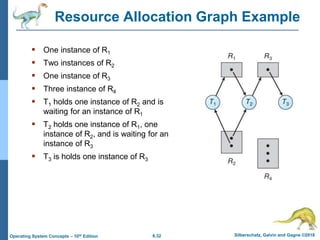
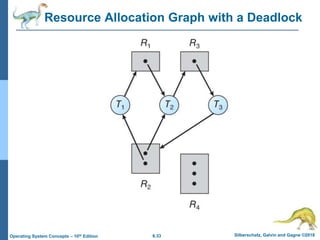
This document summarizes key concepts from Chapter 4 of the textbook "Operating System Concepts - 10th Edition" by Silberschatz, Galvin and Gagne:
1) It introduces the critical section problem which occurs when multiple processes need exclusive access to shared resources, and describes three requirements (mutual exclusion, progress, and bounded waiting) for solving this problem.
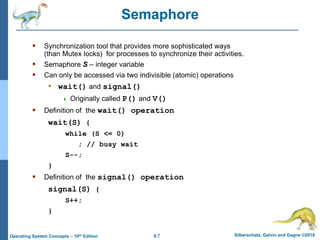
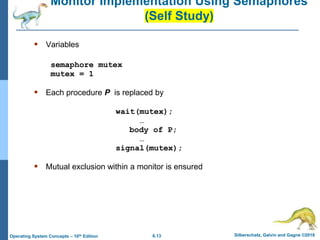
2) It discusses different synchronization techniques for solving the critical section problem including mutex locks, semaphores, and monitors. Semaphores provide a more sophisticated way than mutex locks for processes to synchronize activities.
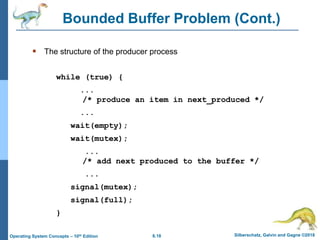
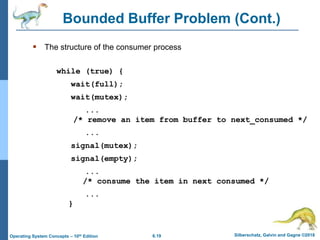
3) It presents three classical problems used to test synchronization schemes - the bounded buffer problem, readers-writers problem, and

















![6.24 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Dining-Philosophers Problem
N philosophers’ sit at a round table with a bowel of rice in the middle.
They spend their lives alternating thinking and eating.
They do not interact with their neighbors.
Occasionally try to pick up 2 chopsticks (one at a time) to eat from bowl
• Need both to eat, then release both when done
In the case of 5 philosophers, the shared data
Bowl of rice (data set)
Semaphore chopstick [5] initialized to 1](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-24-320.jpg)
![6.25 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Dining-Philosophers Problem Algorithm
Semaphore Solution
The structure of Philosopher i :
while (true){
wait (chopstick[i] );
wait (chopStick[ (i + 1) % 5] );
/* eat for awhile */
signal (chopstick[i] );
signal (chopstick[ (i + 1) % 5] );
/* think for awhile */
}
What is the problem with this algorithm?](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-25-320.jpg)













![6.46 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Data Structures for the Banker’s Algorithm
Available: Vector of length m. If available [j] = k, there are k
instances of resource type Rj available
Max: n x m matrix. If Max [i,j] = k, then process Ti may request at
most k instances of resource type Rj
Allocation: n x m matrix. If Allocation[i,j] = k then Ti is currently
allocated k instances of Rj
Need: n x m matrix. If Need[i,j] = k, then Ti may need k more
instances of Rj to complete its task
Need [i,j] = Max[i,j] – Allocation [i,j]
Let n = number of processes, and m = number of resources types.](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-46-320.jpg)
![6.47 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Safety Algorithm
1. Let Work and Finish be vectors of length m and n, respectively.
Initialize:
Work = Available
Finish [i] = false for i = 0, 1, …, n- 1
2. Find an i such that both:
(a) Finish [i] = false
(b) Needi Work
If no such i exists, go to step 4
3. Work = Work + Allocationi
Finish[i] = true
go to step 2
4. If Finish [i] == true for all i, then the system is in a safe state](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-47-320.jpg)
![6.48 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Resource-Request Algorithm for Process Pi
Requesti = request vector for process Ti. If Requesti [j] = k then
process Ti wants k instances of resource type Rj
1. If Requesti Needi go to step 2. Otherwise, raise error
condition, since process has exceeded its maximum claim
2. If Requesti Available, go to step 3. Otherwise Ti must wait,
since resources are not available
3. Pretend to allocate requested resources to Ti by modifying the
state as follows:
Available = Available – Requesti;
Allocationi = Allocationi + Requesti;
Needi = Needi – Requesti;
• If safe the resources are allocated to Ti
• If unsafe Ti must wait, and the old resource-allocation state
is restored](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-48-320.jpg)
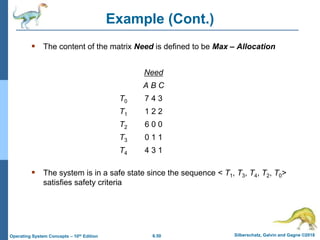



![6.55 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Several Instances of a Resource Type
Available: A vector of length m indicates the number of available
resources of each type
Allocation: An n x m matrix defines the number of resources of
each type currently allocated to each thread.
Request: An n x m matrix indicates the current request of each
thread. If Request [i][j] = k, then thread Ti is requesting k more
instances of resource type Rj.](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-55-320.jpg)
![6.56 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Detection Algorithm
1. Let Work and Finish be vectors of length m and n, respectively
Initialize:
a) Work = Available
b) For i = 1,2, …, n, if Allocationi 0, then
Finish[i] = false; otherwise, Finish[i] = true
2. Find an index i such that both:
a) Finish[i] == false
b) Requesti Work
If no such i exists, go to step 4](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-56-320.jpg)
![6.57 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Detection Algorithm (Cont.)
3. Work = Work + Allocationi
Finish[i] = true
go to step 2
4. If Finish[i] == false, for some i, 1 i n, then the system is in
deadlock state. Moreover, if Finish[i] == false, then Ti is
deadlocked
Algorithm requires an order of O(m x n2) operations to detect
whether the system is in deadlocked state](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-57-320.jpg)
![6.58 Silberschatz, Galvin and Gagne ©2018
Operating System Concepts – 10th Edition
Example of Detection Algorithm
Five threads T0 through T4; three resource types
A (7 instances), B (2 instances), and C (6 instances)
Snapshot at time T0:
Allocation Request Available
A B C A B C A B C
T0 0 1 0 0 0 0 0 0 0
T1 2 0 0 2 0 2
T2 3 0 3 0 0 0
T3 2 1 1 1 0 0
T4 0 0 2 0 0 2
Sequence <T0, T2, T3, T1, T4> will result in Finish[i] = true for all i](https://image.slidesharecdn.com/chapter4-231014005804-4b9c4112/85/chapter4-pptx-58-320.jpg)