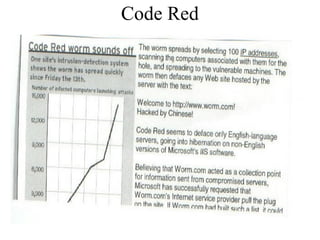
The document discusses the growing problem of cyber attacks and vulnerabilities. It notes recent major attacks and that cyber infrastructure and most users have limited understanding of networks and security. There are no comprehensive plans to educate the public on these issues. The causes of attacks range from revenge to terrorism to business espionage. Tracking attackers is challenging as there is little reporting of intrusions and many originate from insiders. The social consequences include psychological effects, moral decay, loss of privacy and trust as attacks become more common and accepted.