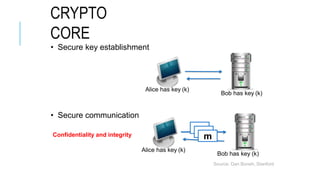
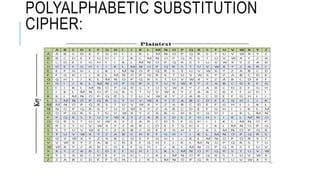
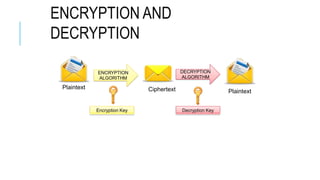
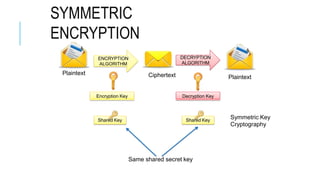
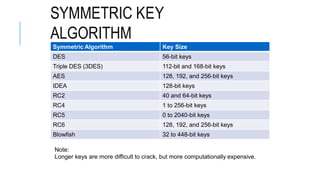
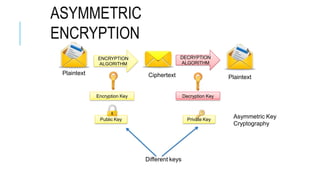
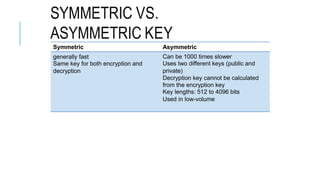
Chapter 3 of the document provides an overview of cryptography, discussing symmetric and asymmetric key techniques, and their applications in secure communication. It explains key concepts such as encryption, decryption, and the types of ciphers including substitution and transposition ciphers. The chapter also covers the benefits and challenges of various encryption algorithms and the distinction between symmetric and asymmetric cryptography.