Embed presentation
Download as PDF, PPTX




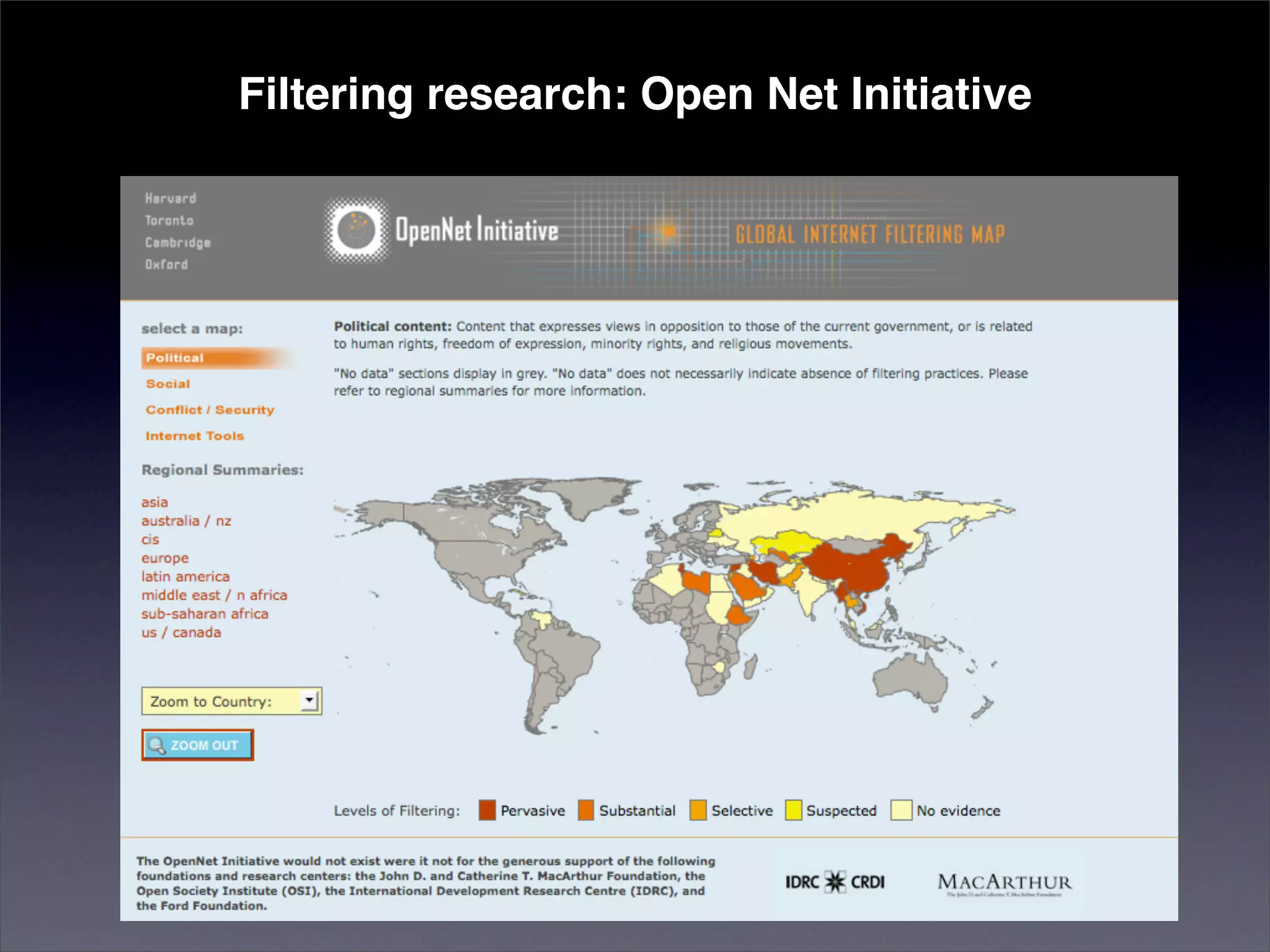
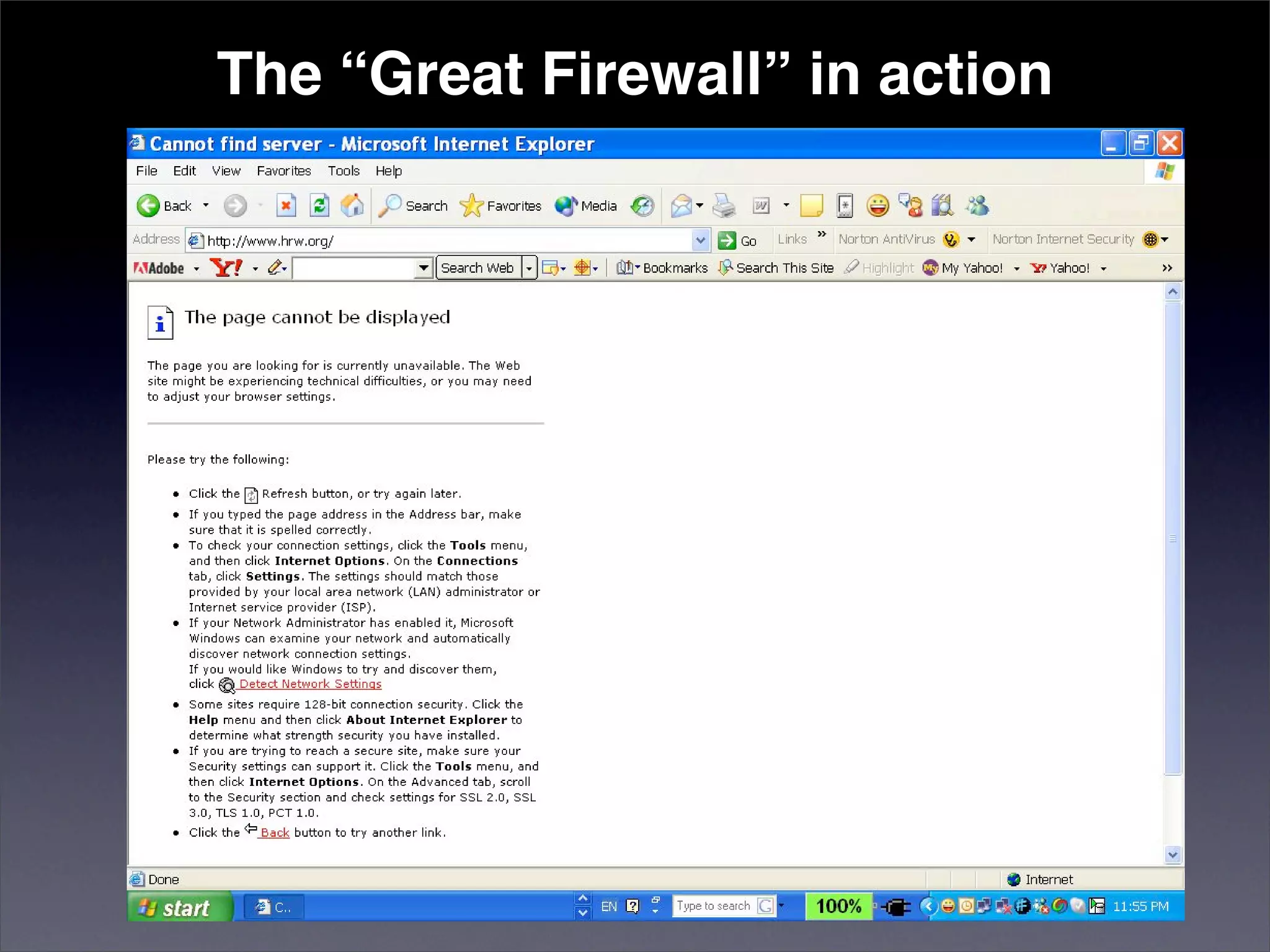
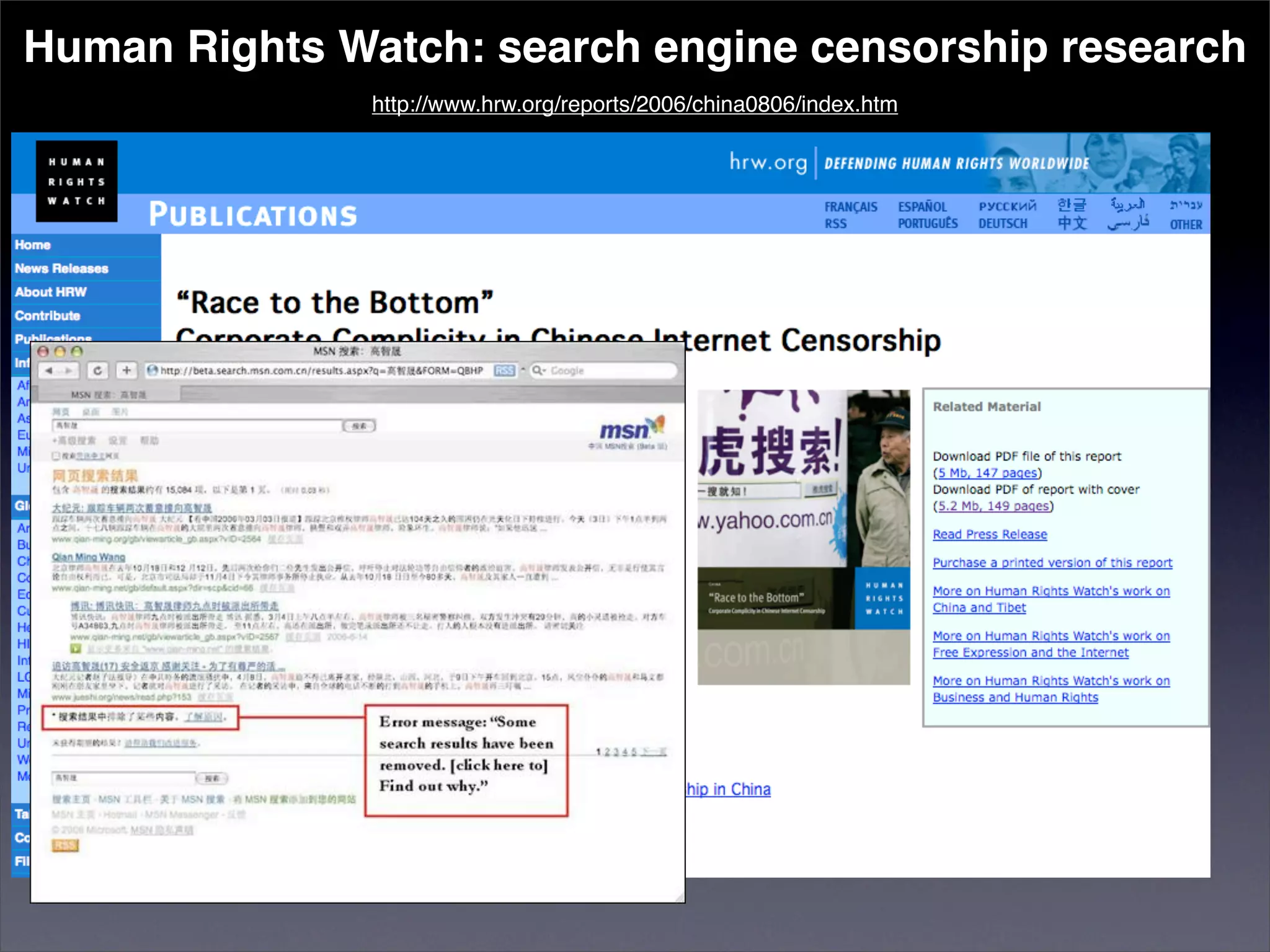
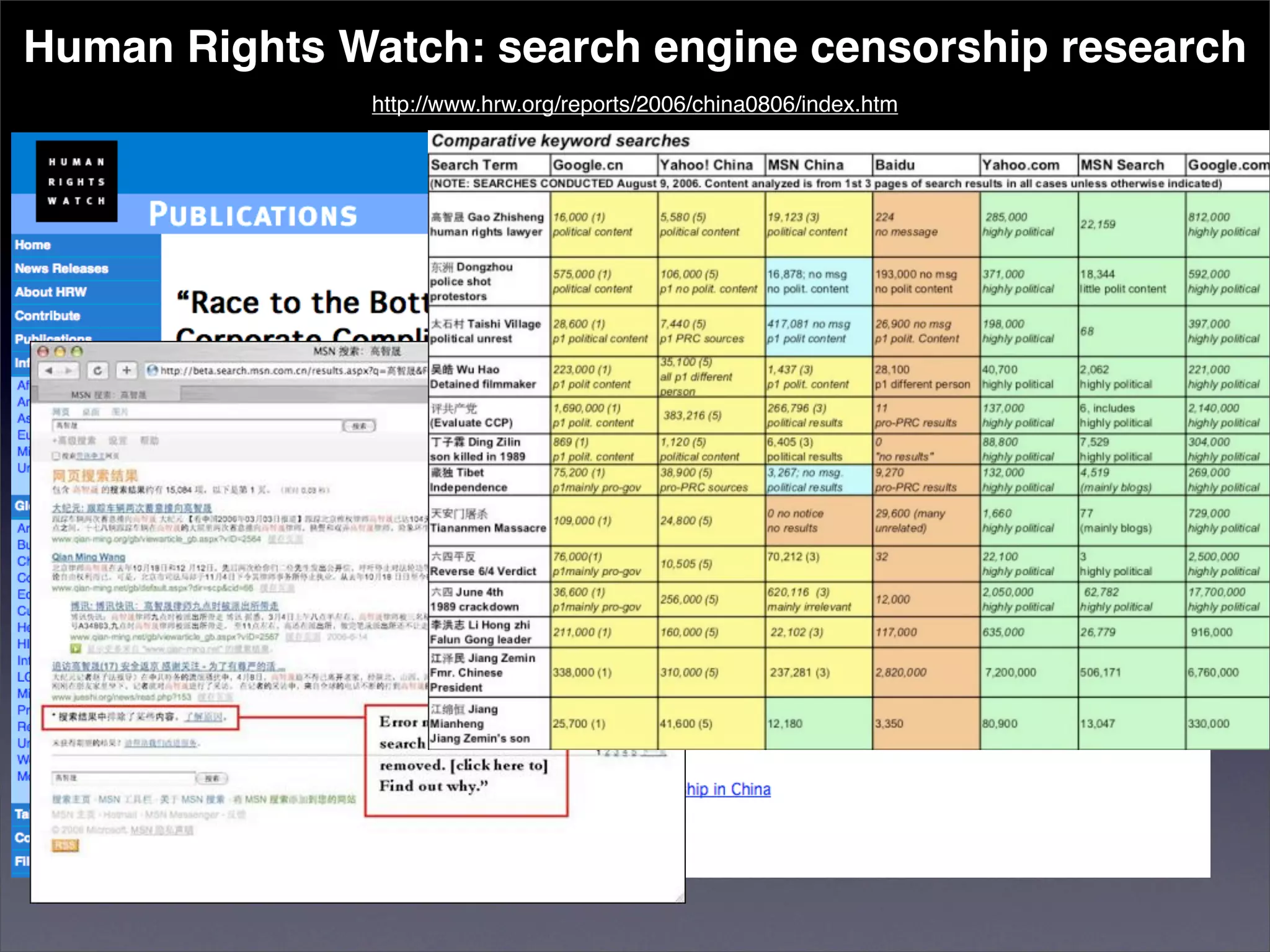
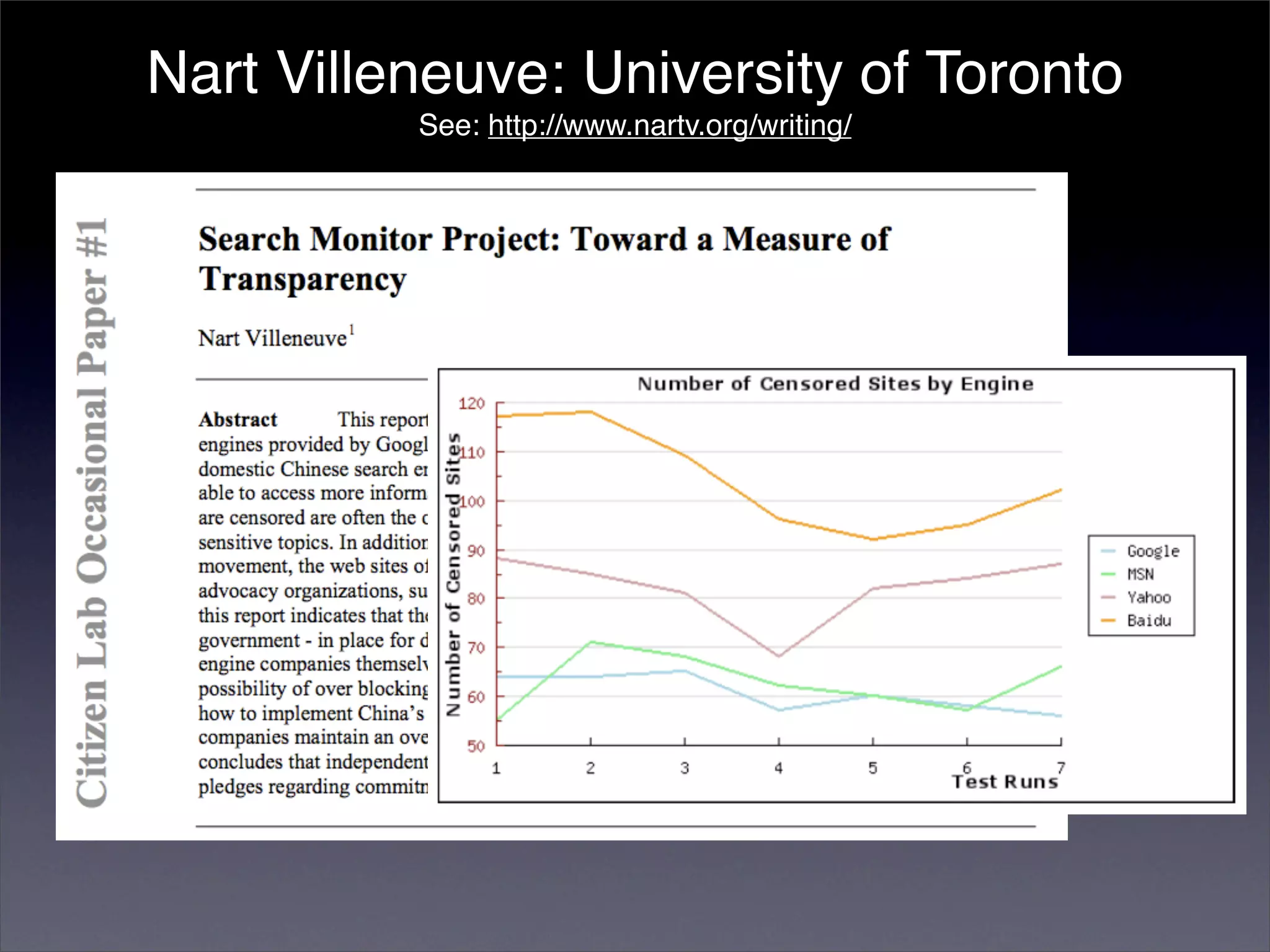
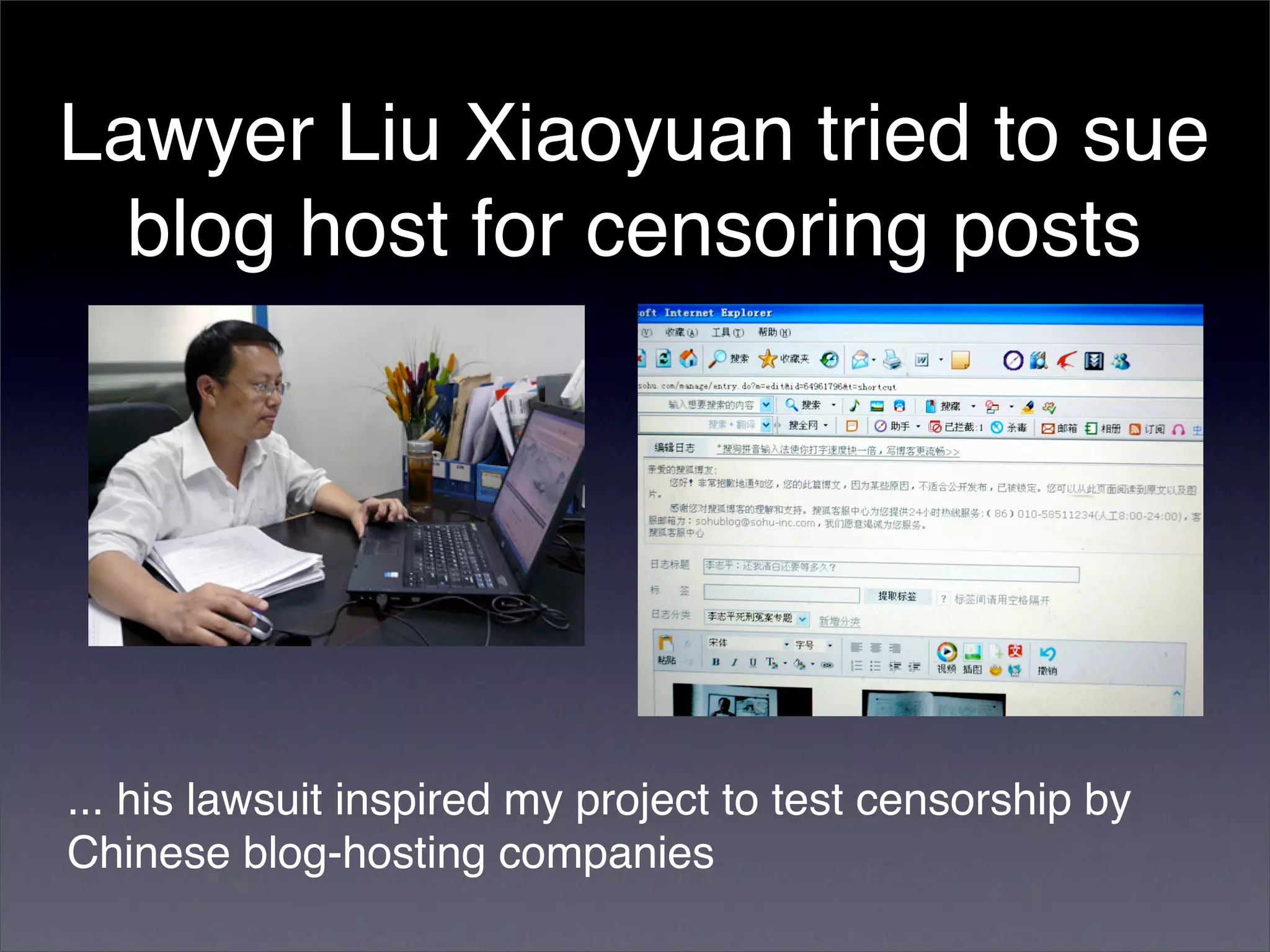
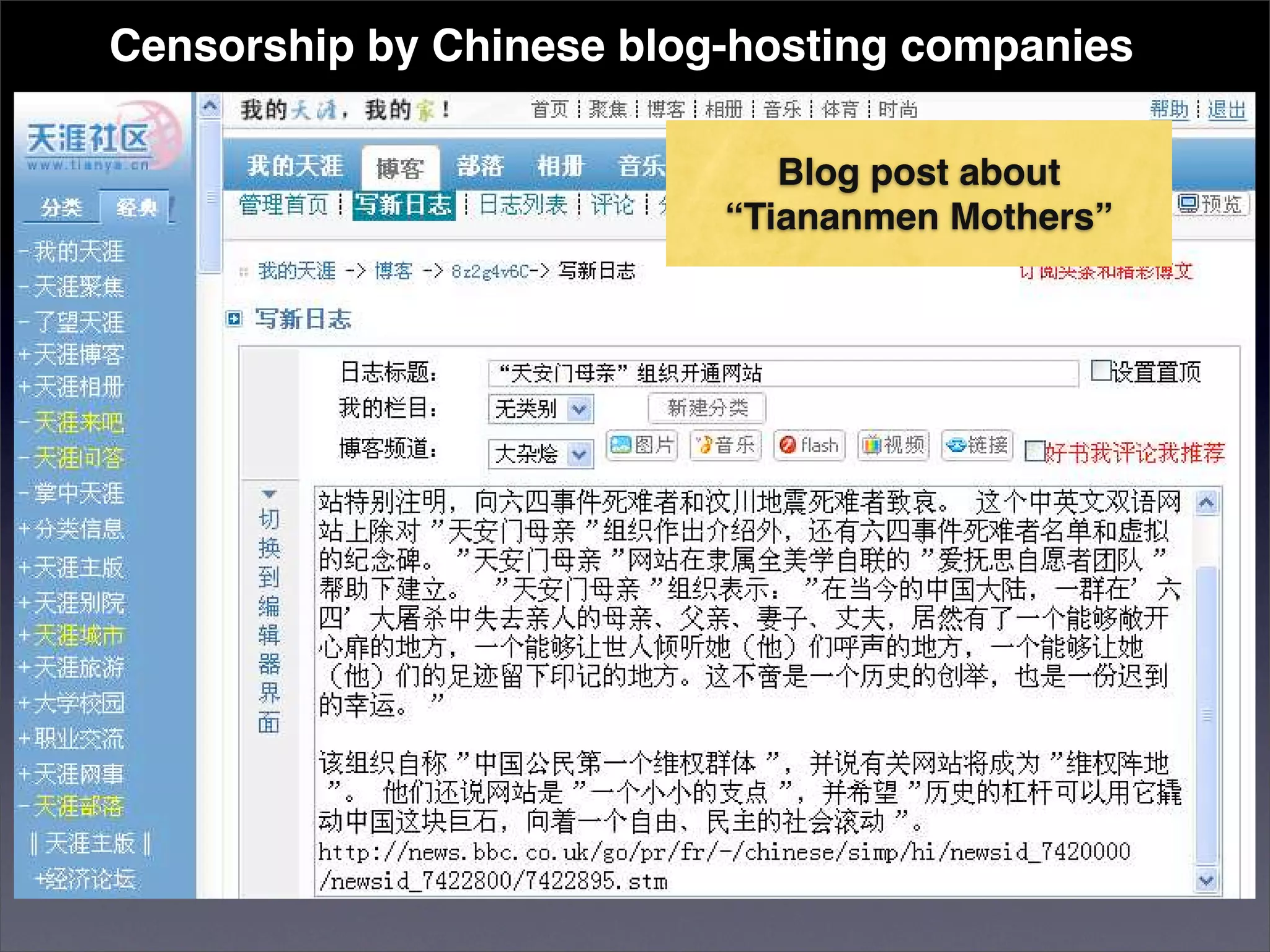
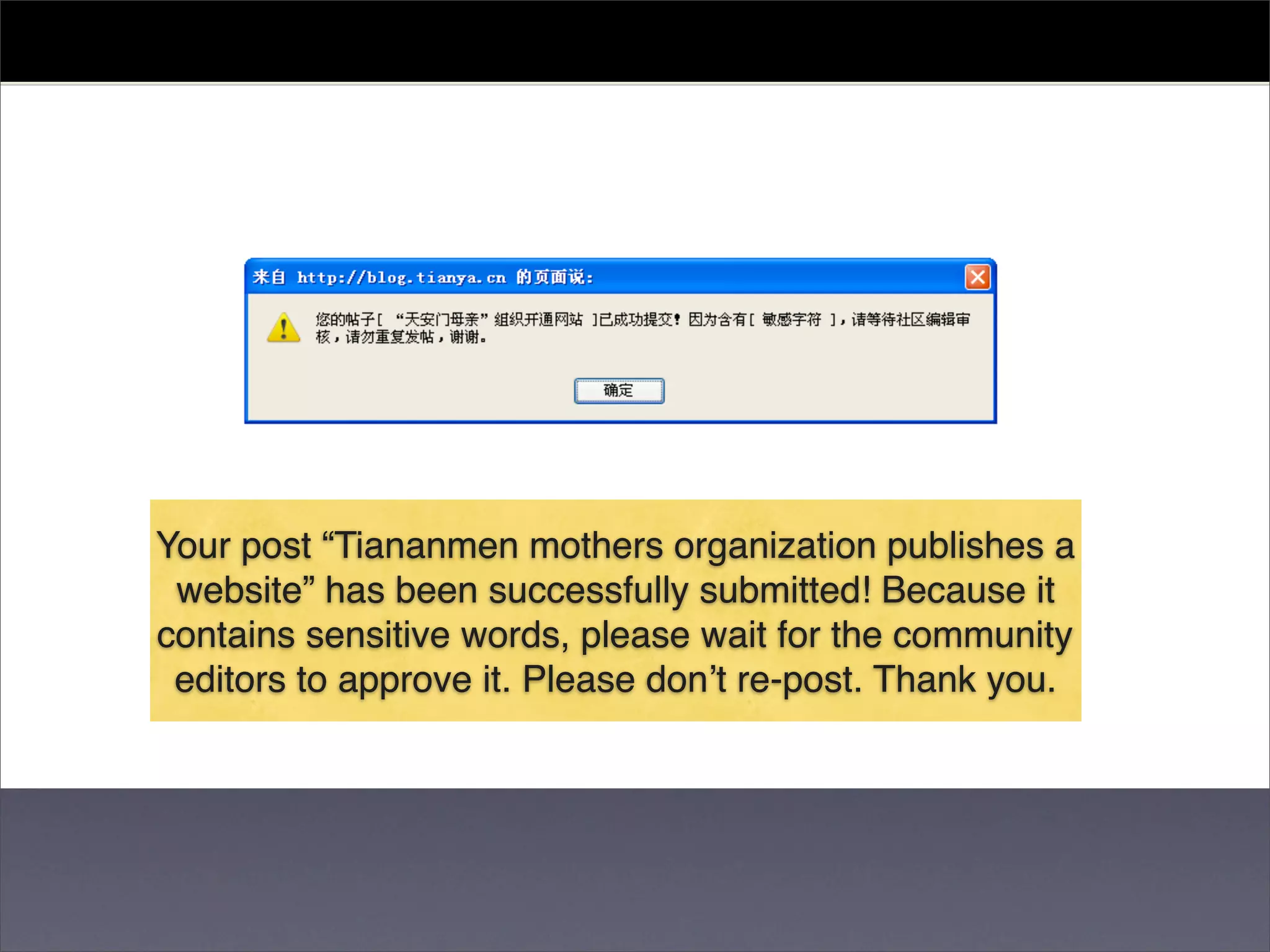

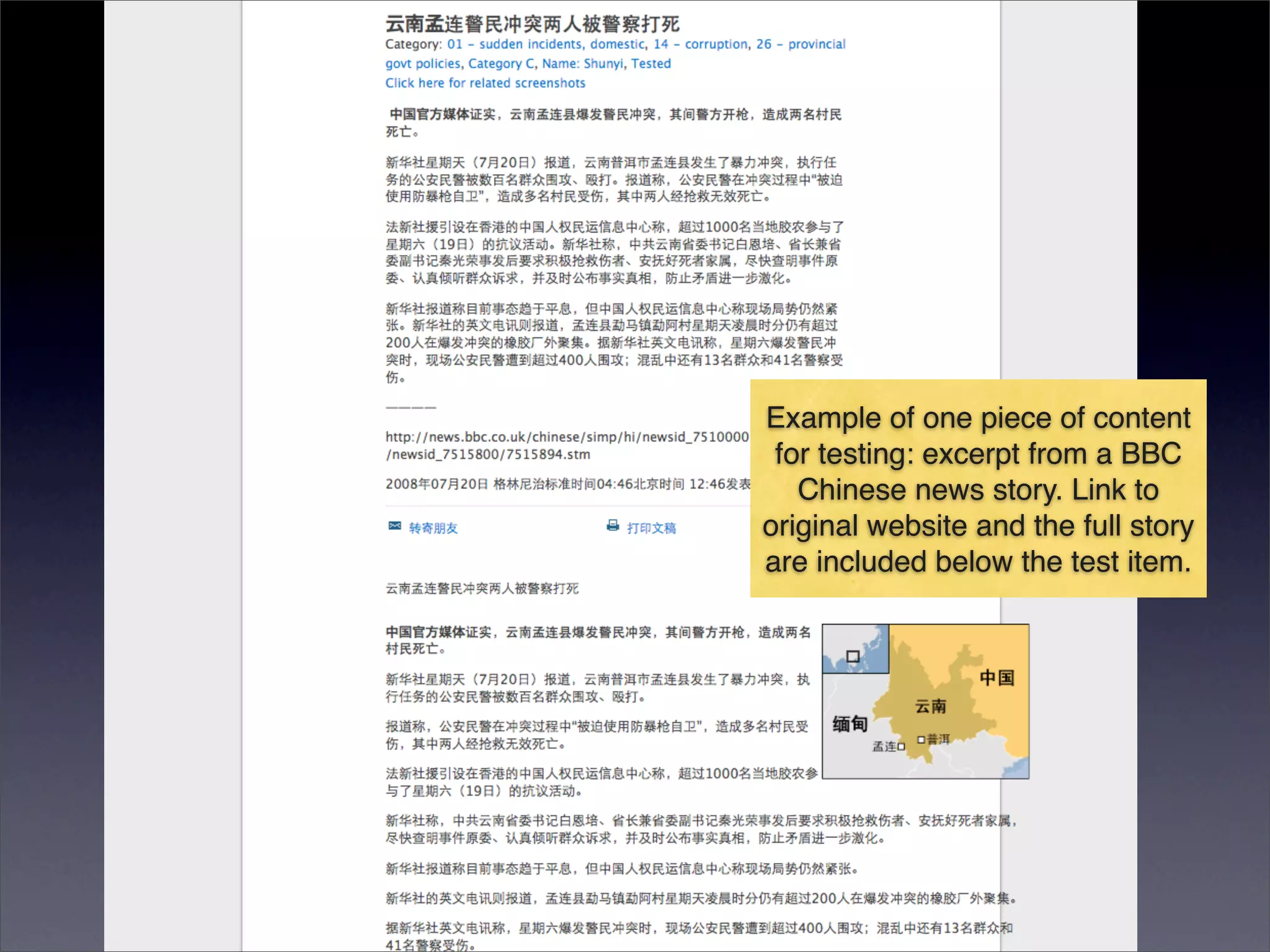
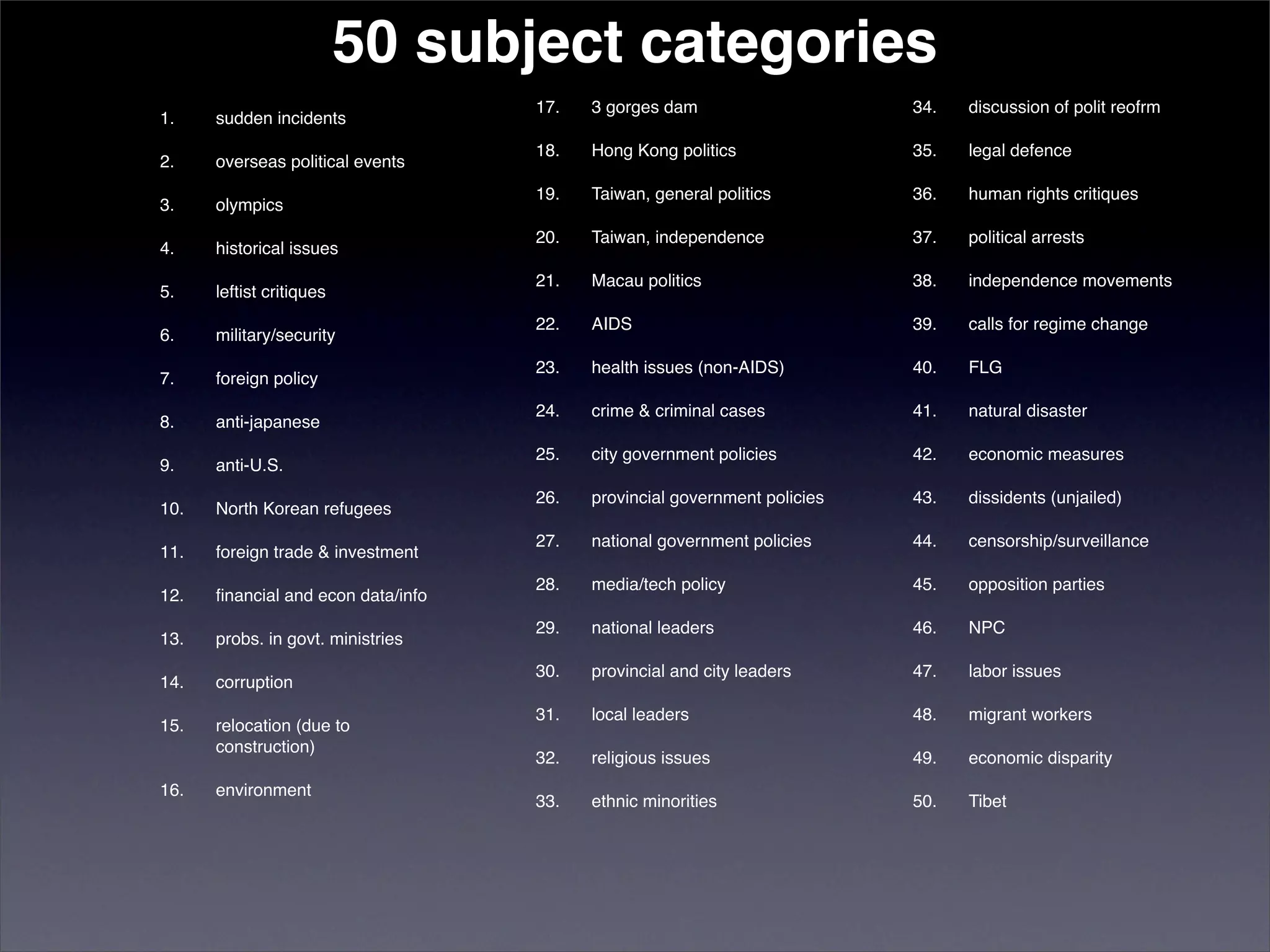
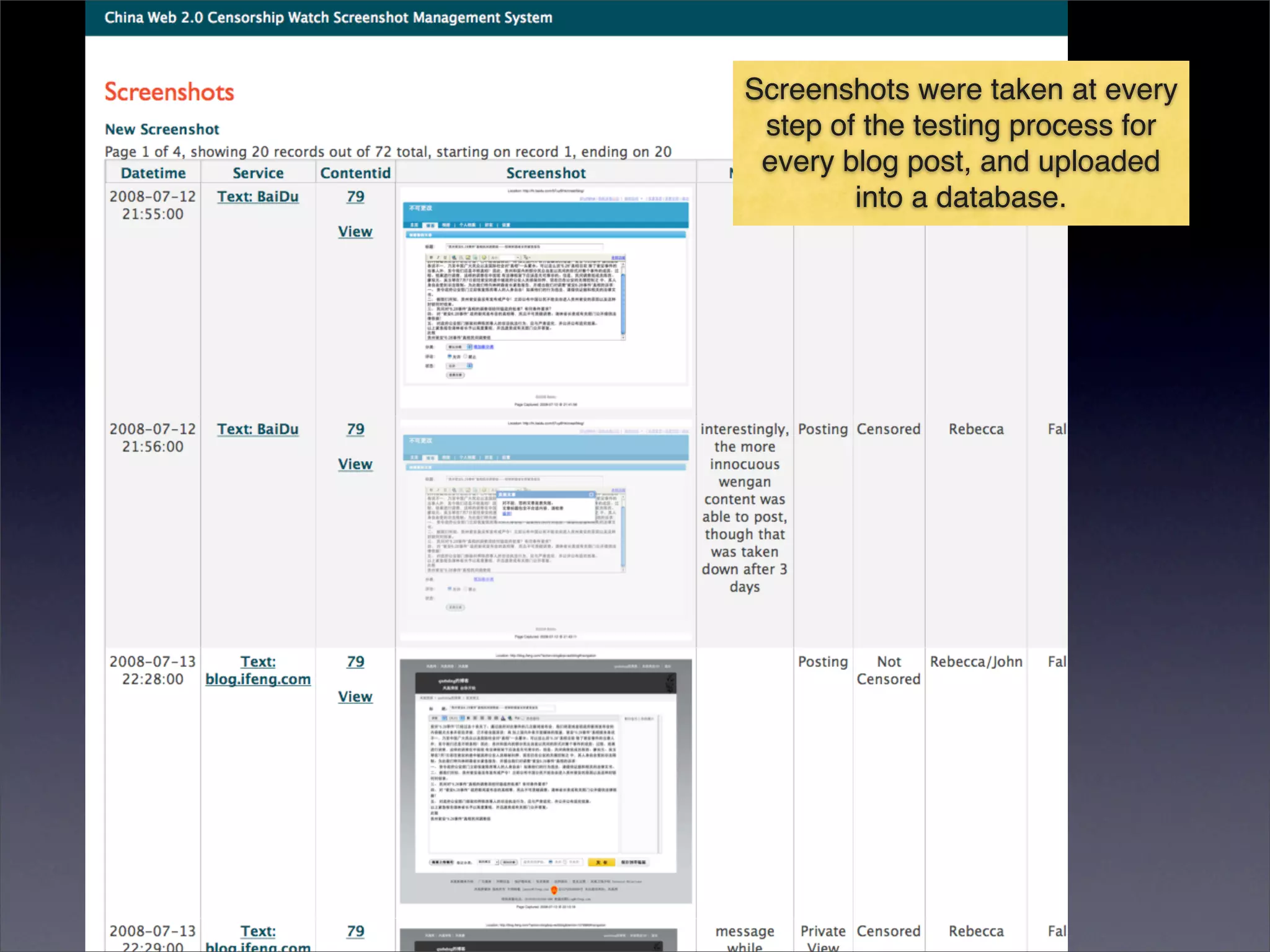
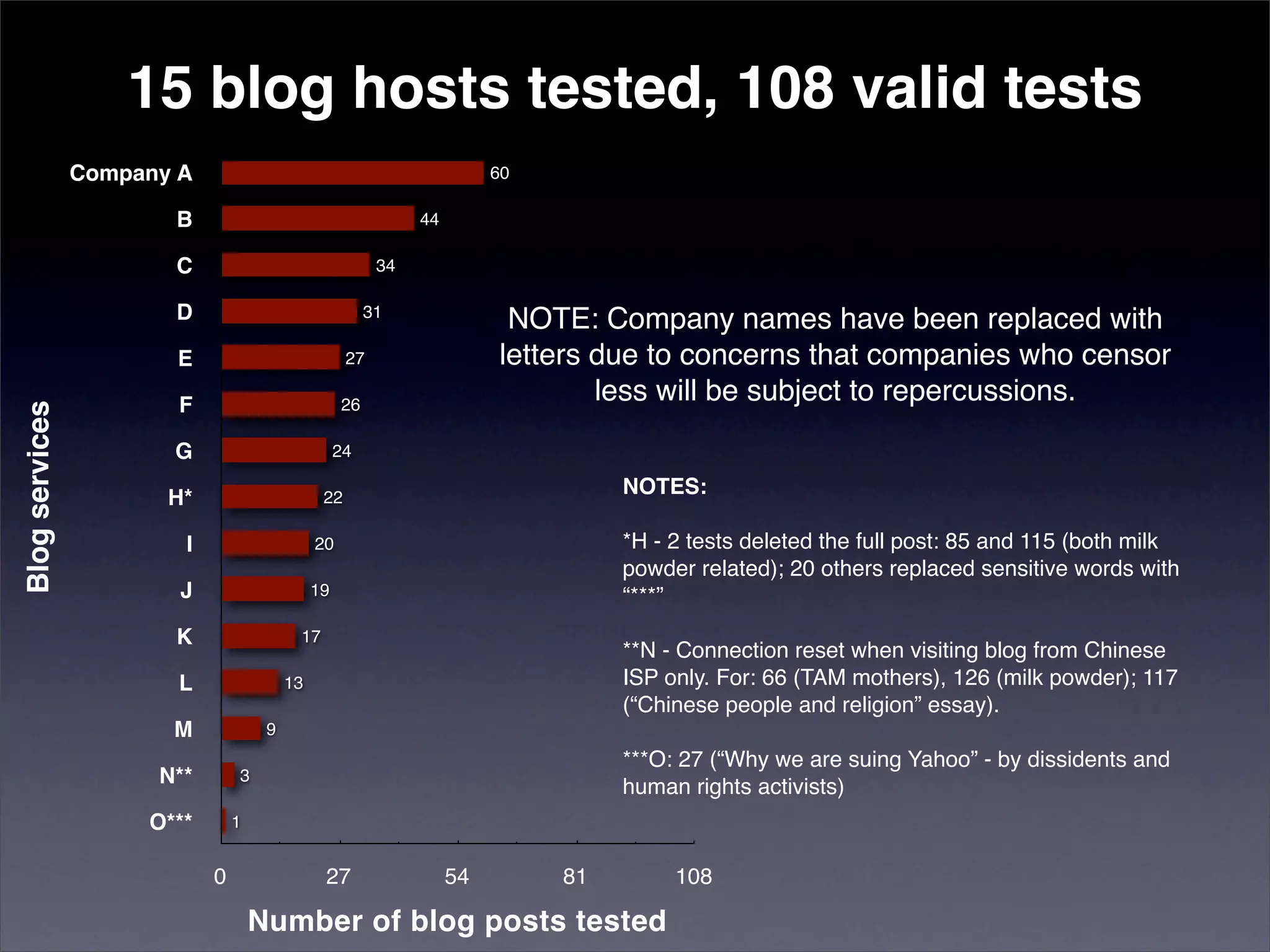
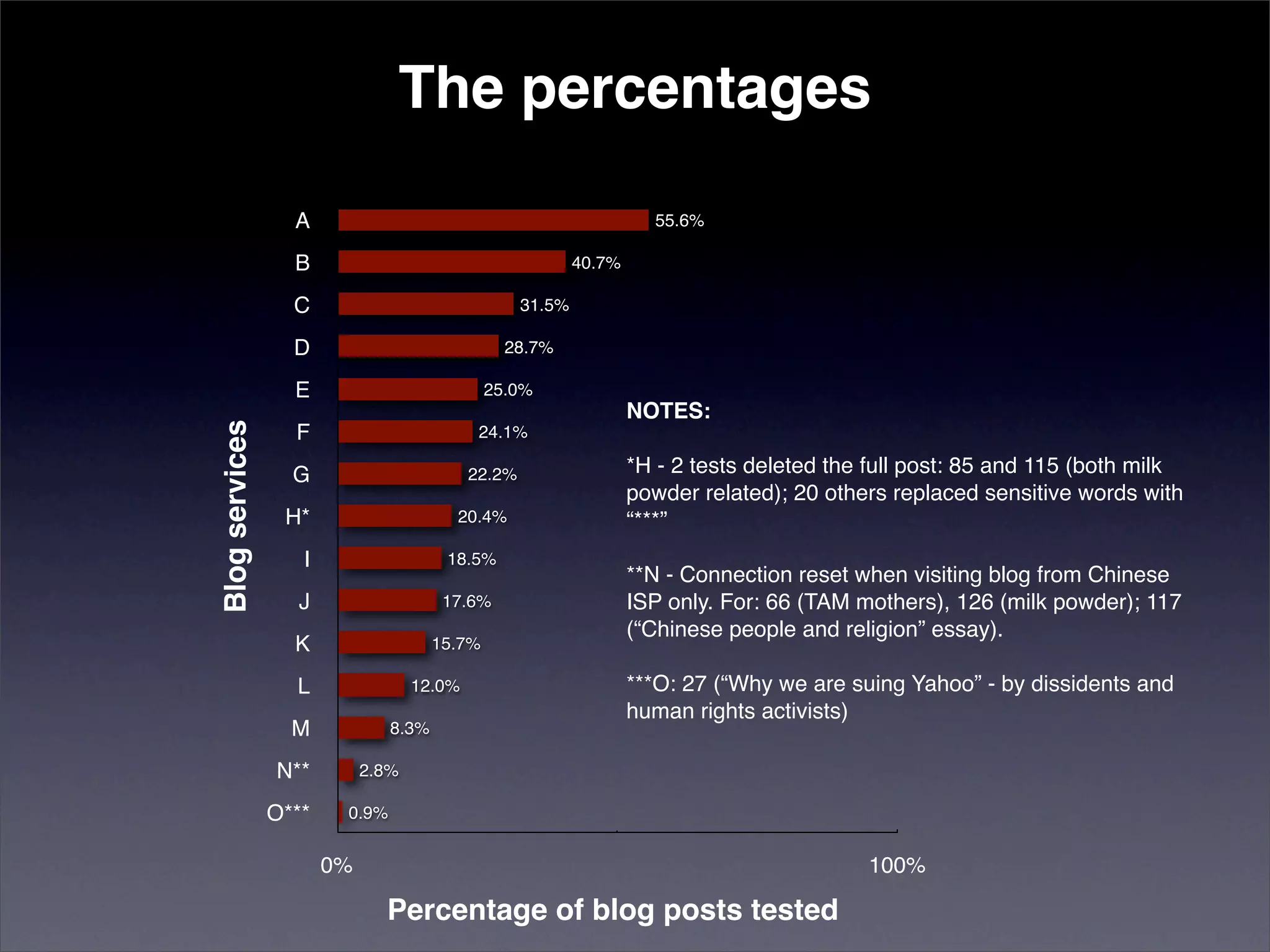
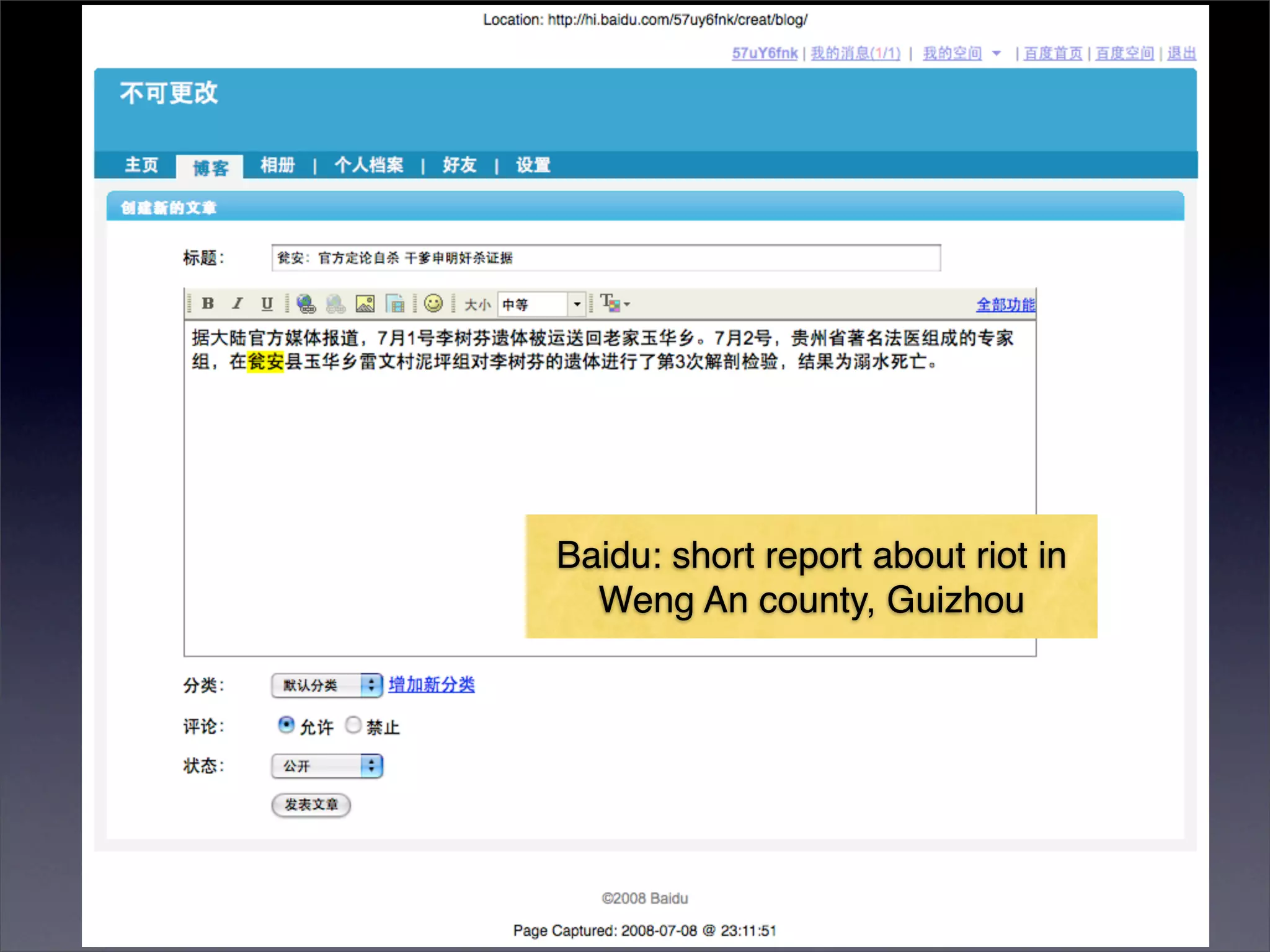
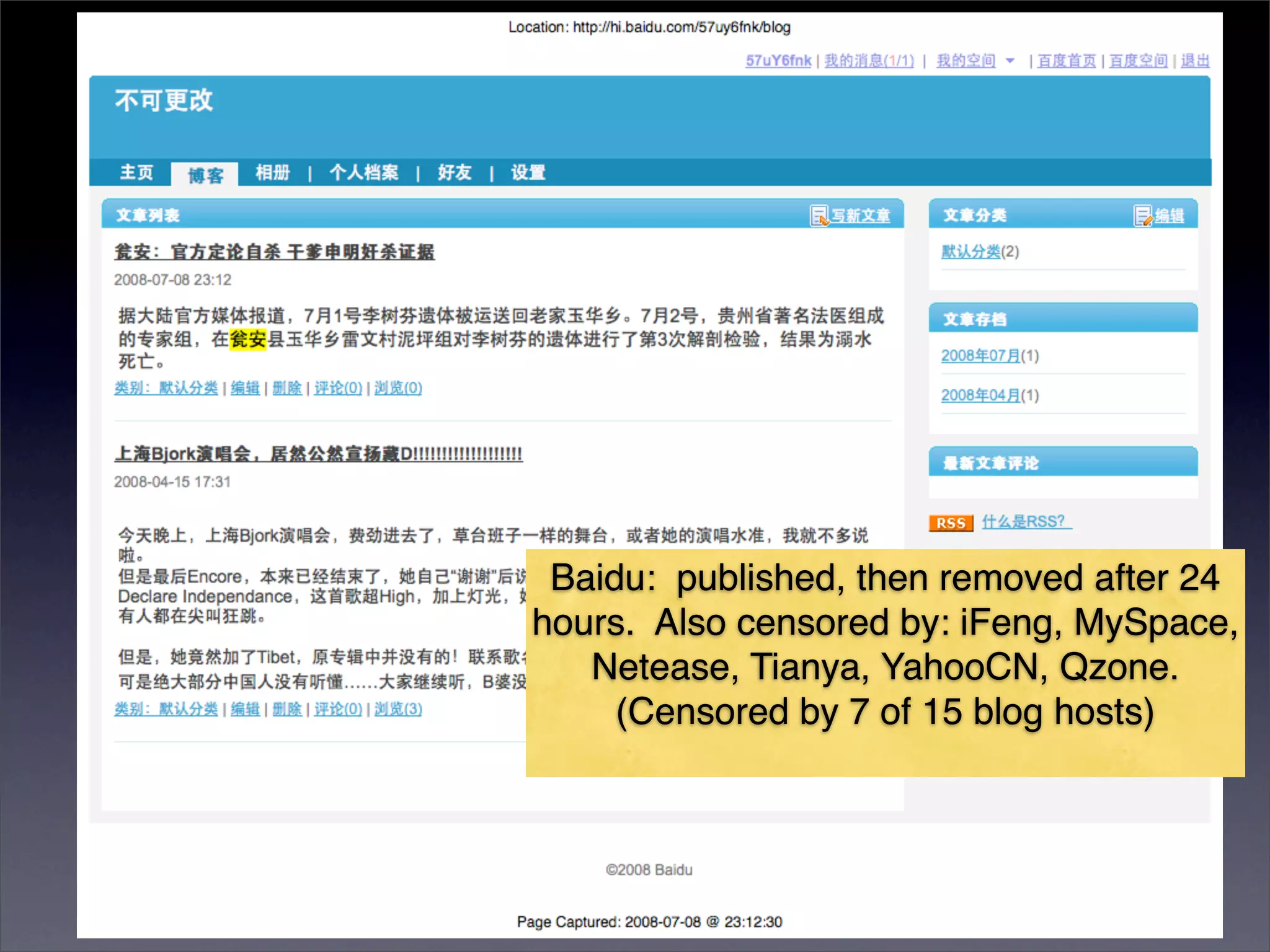
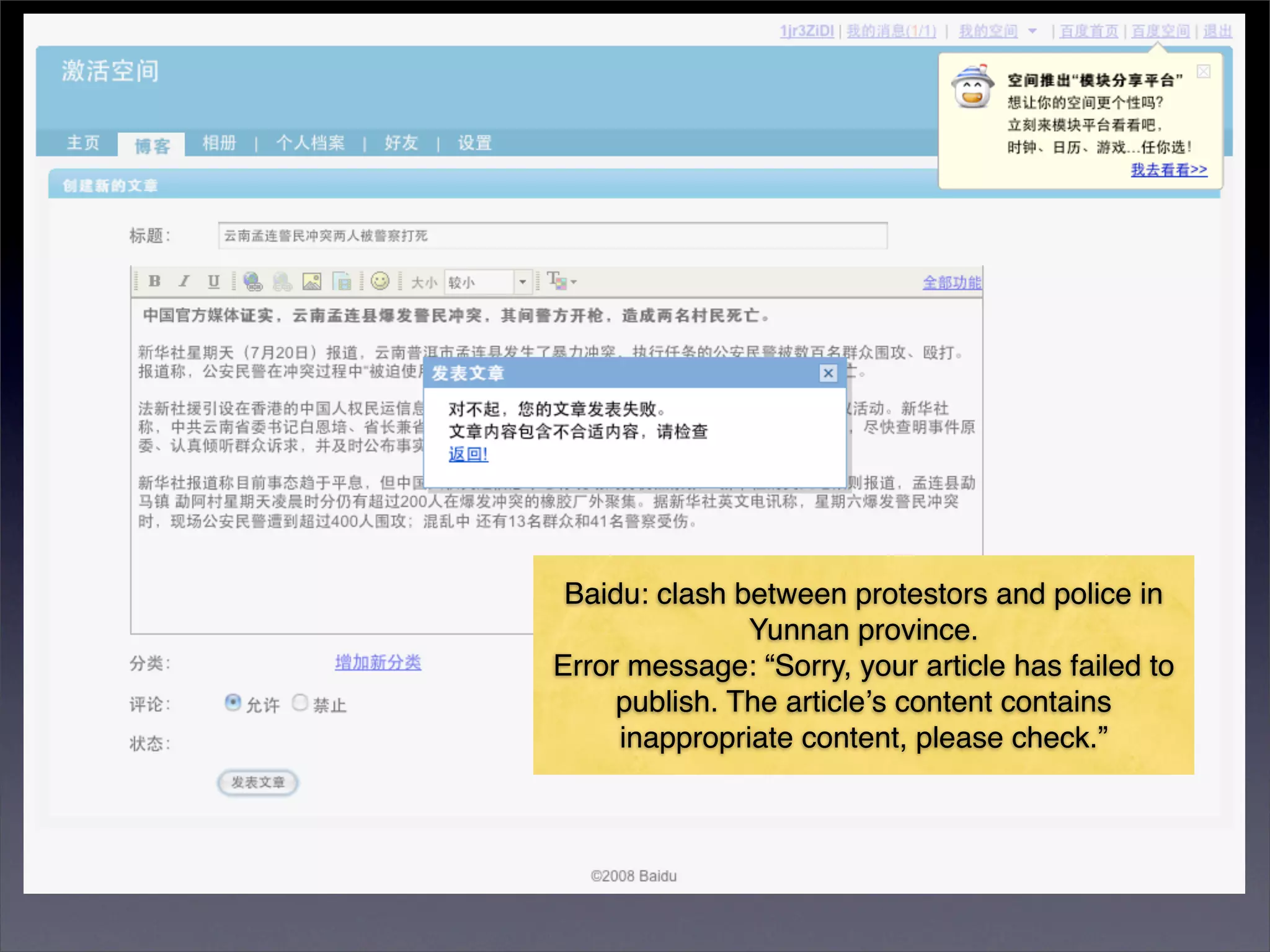
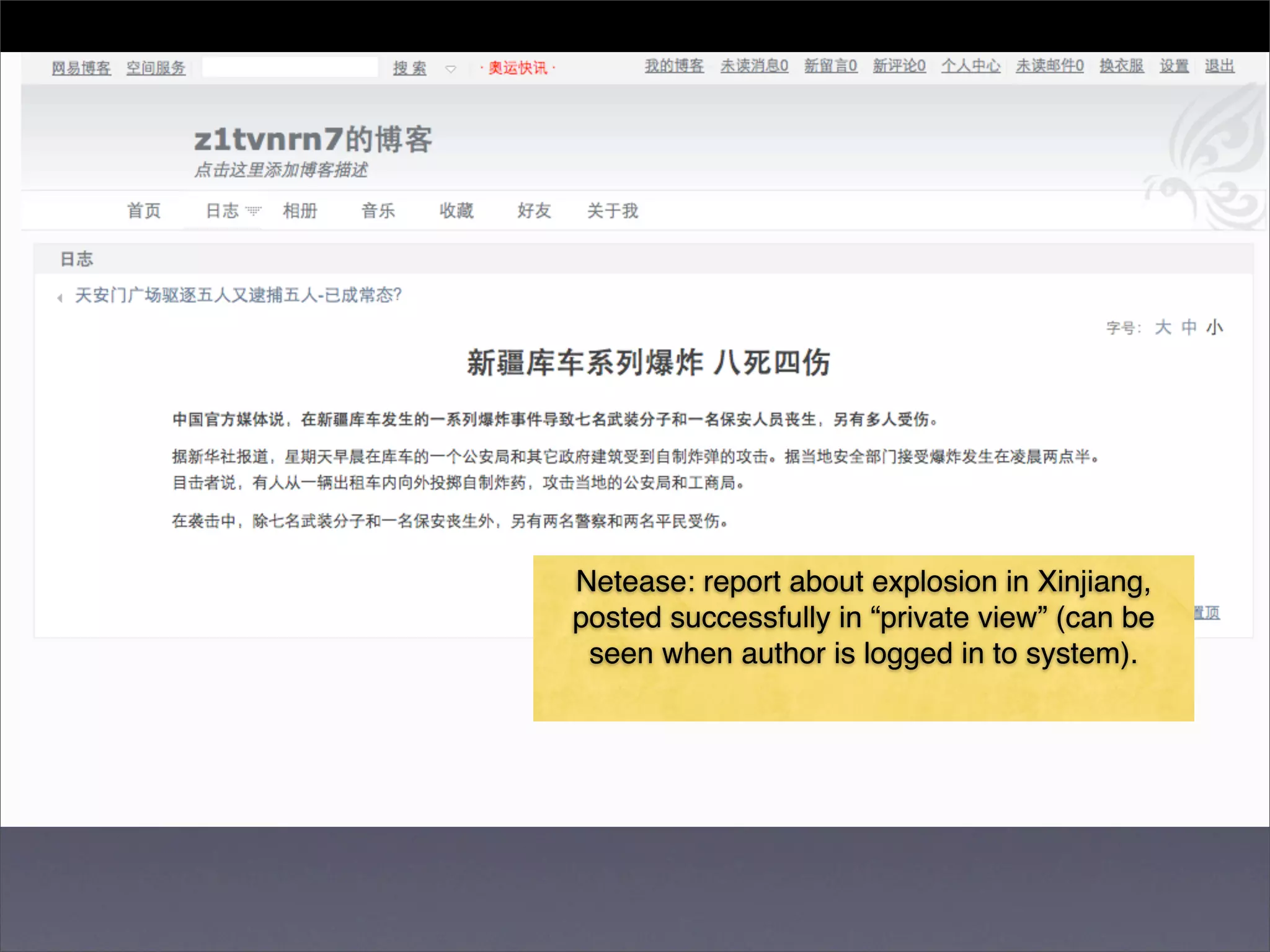
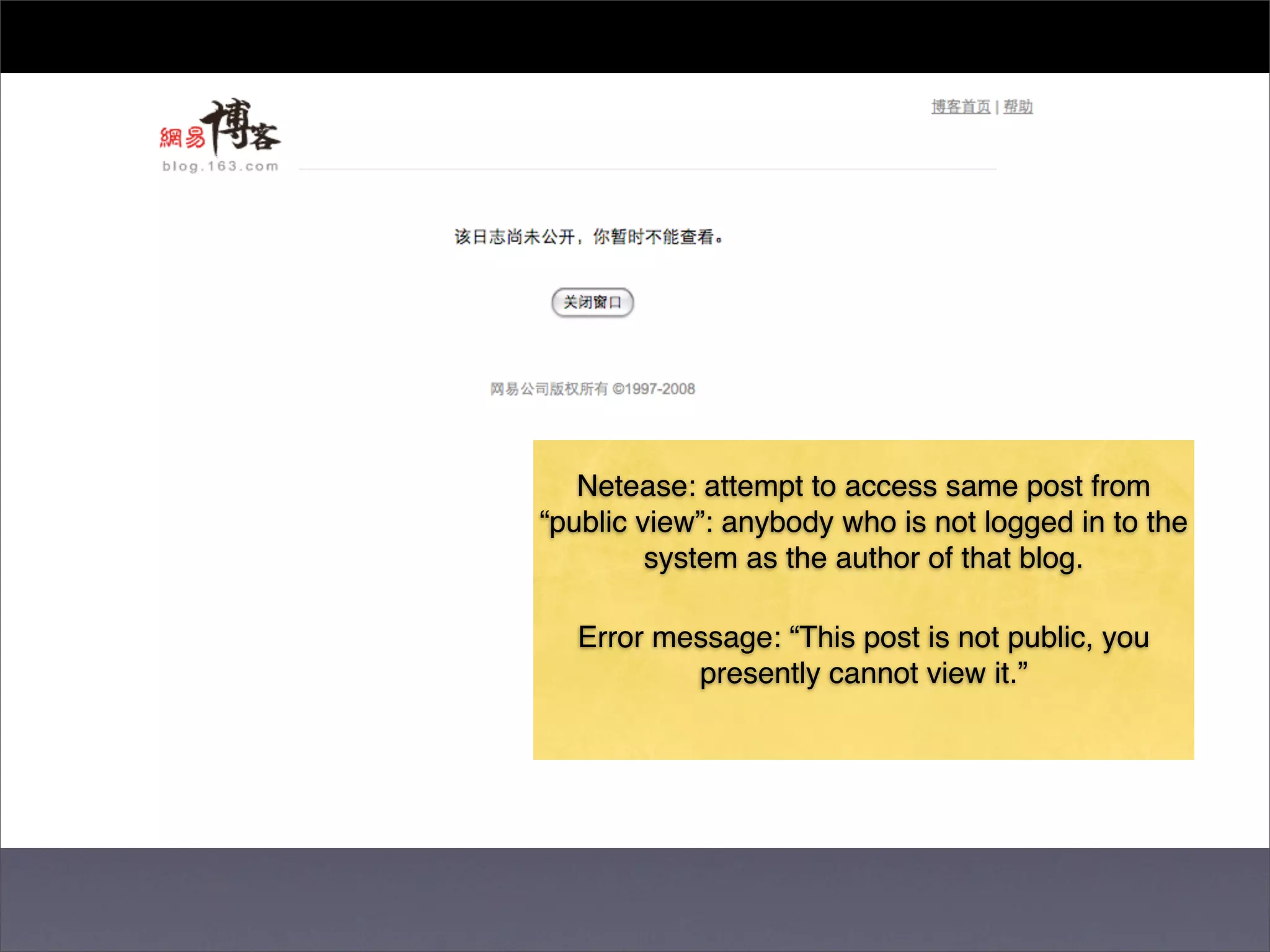
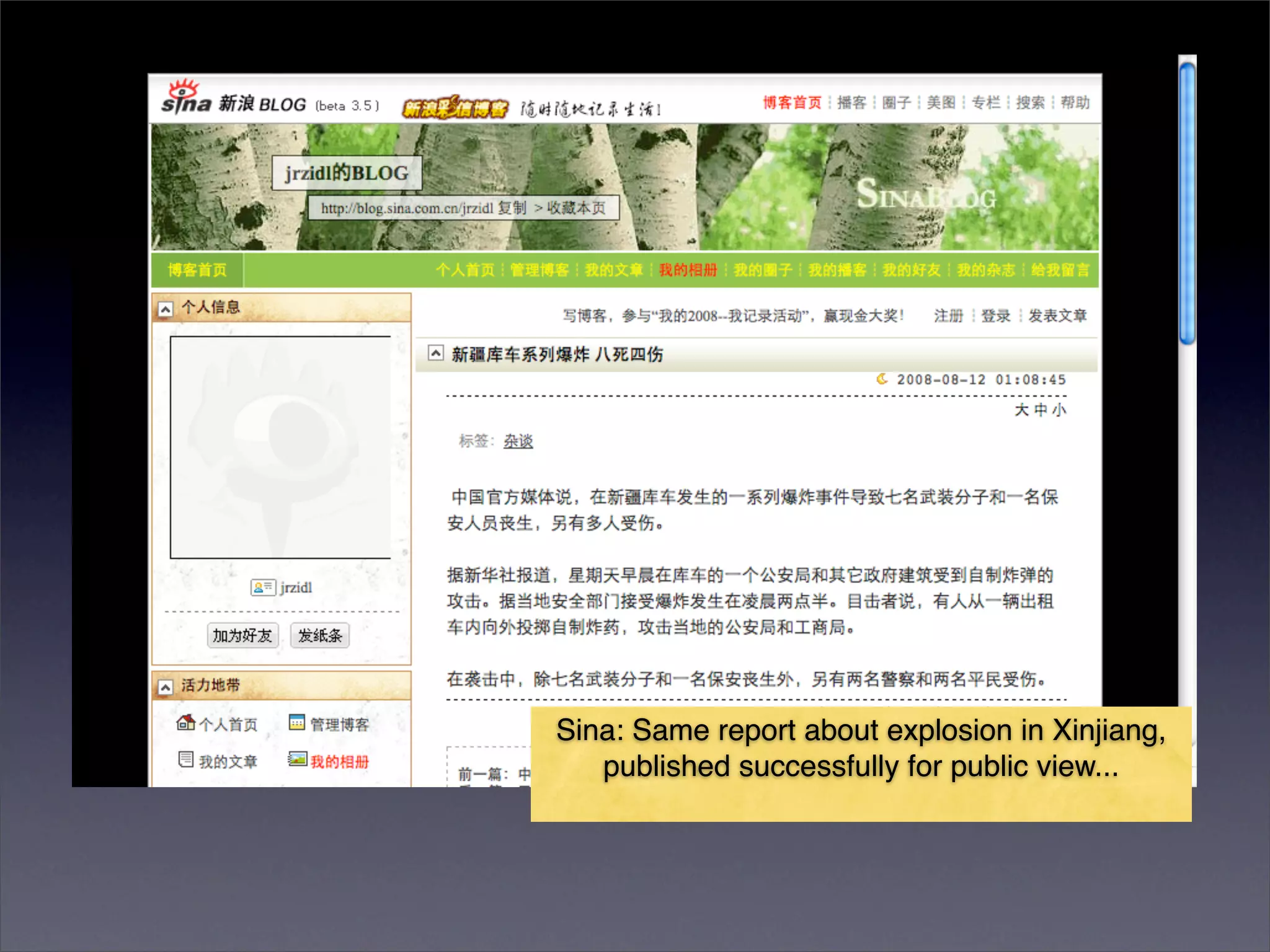
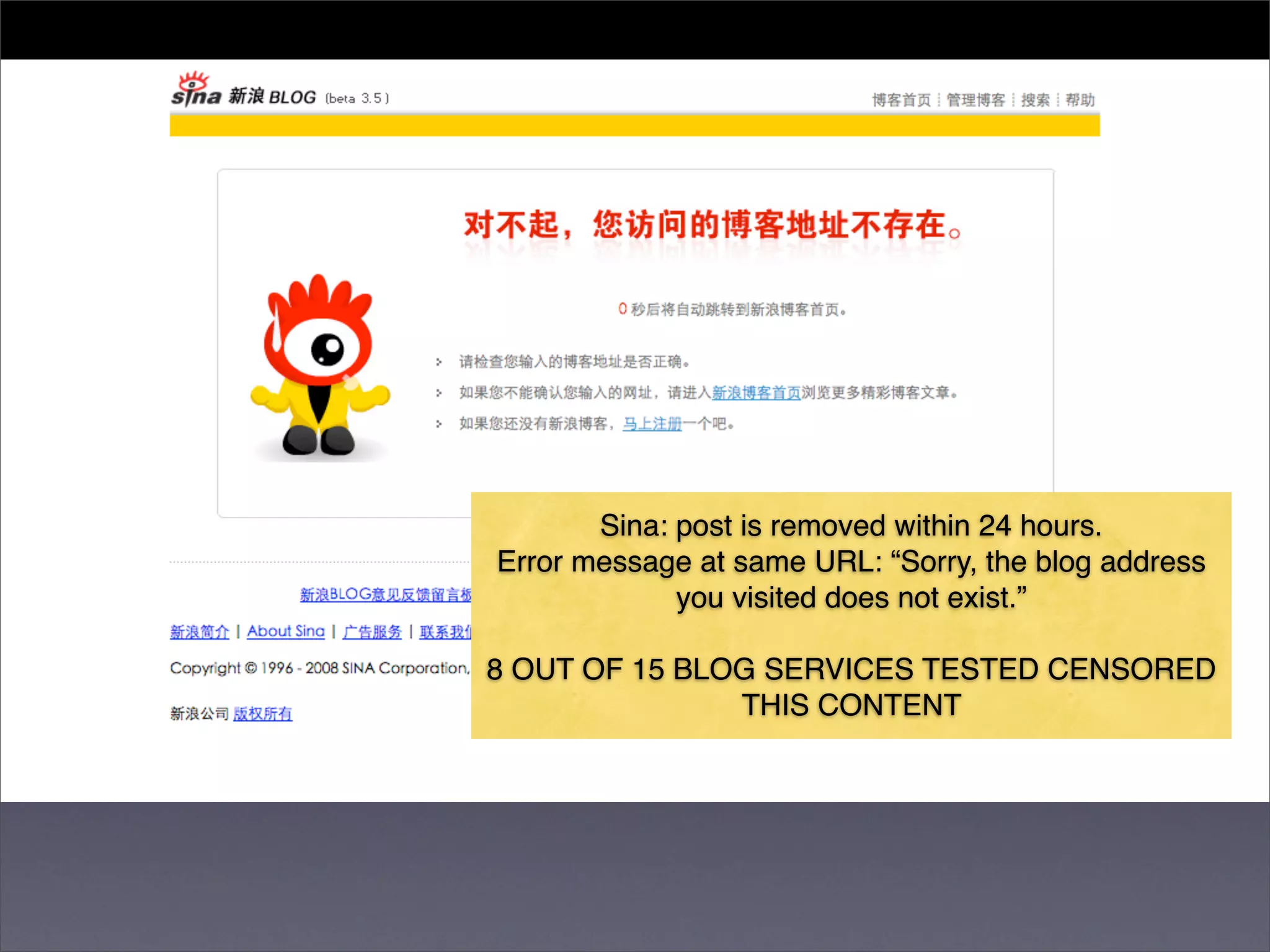
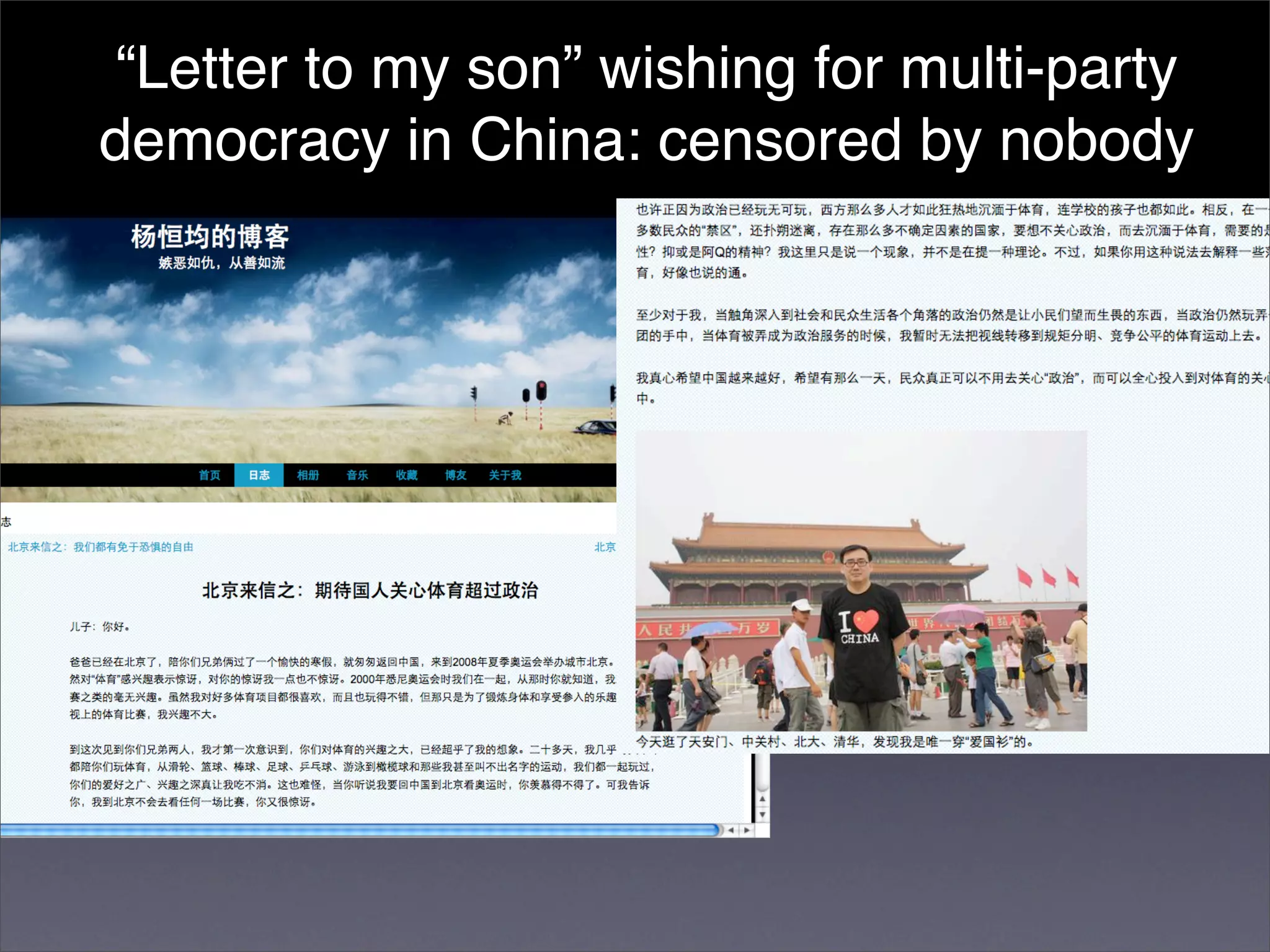
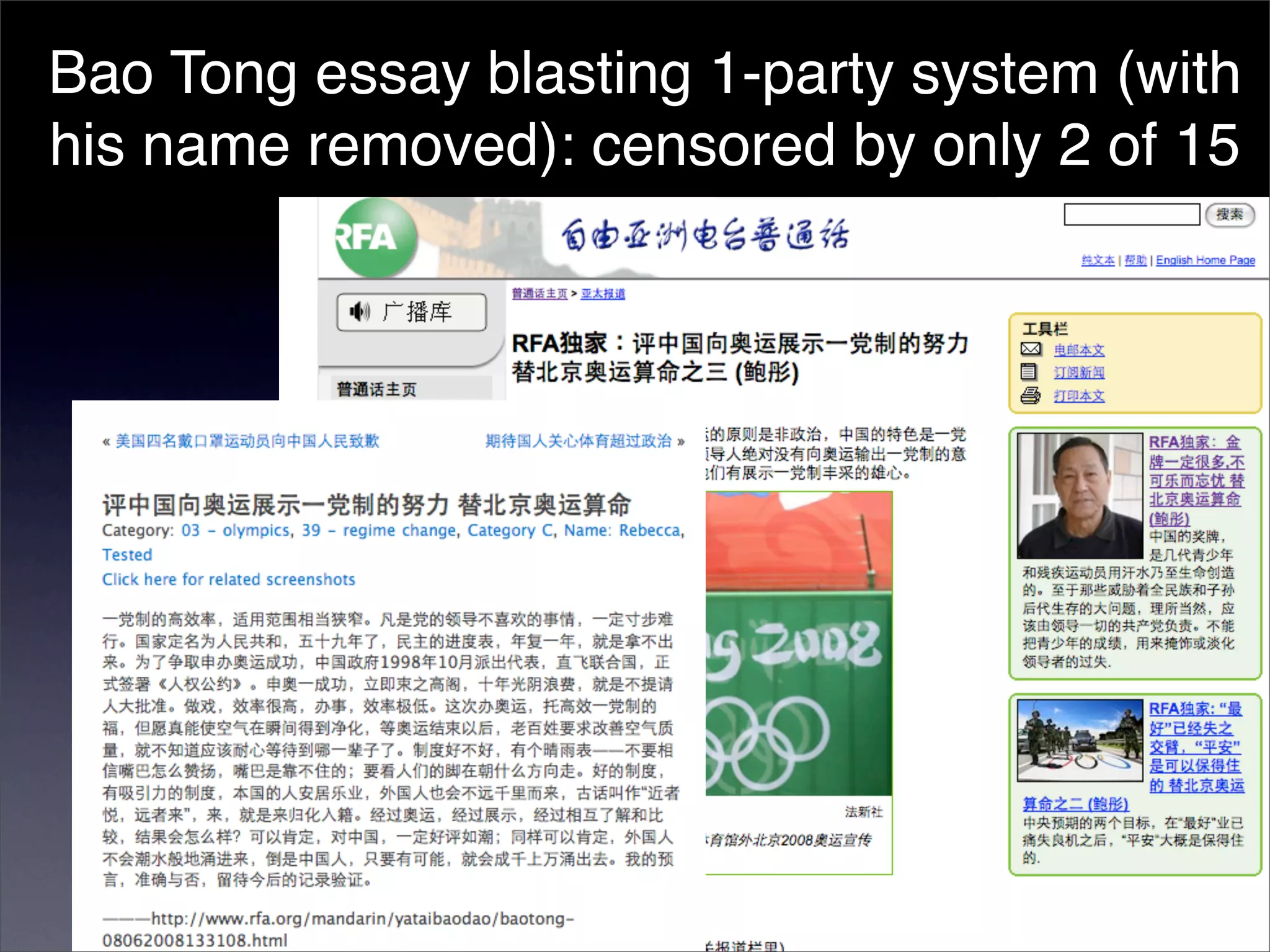
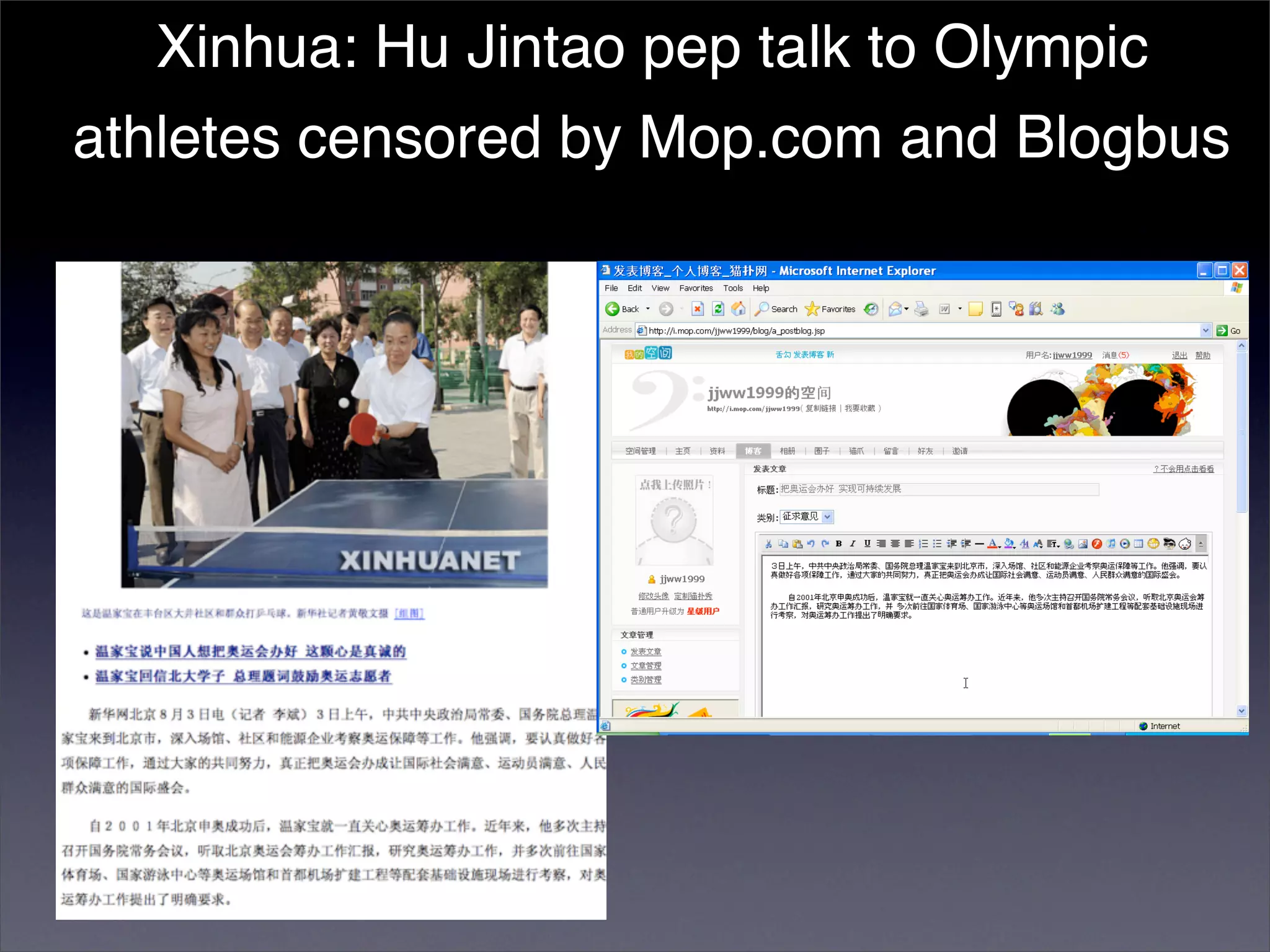
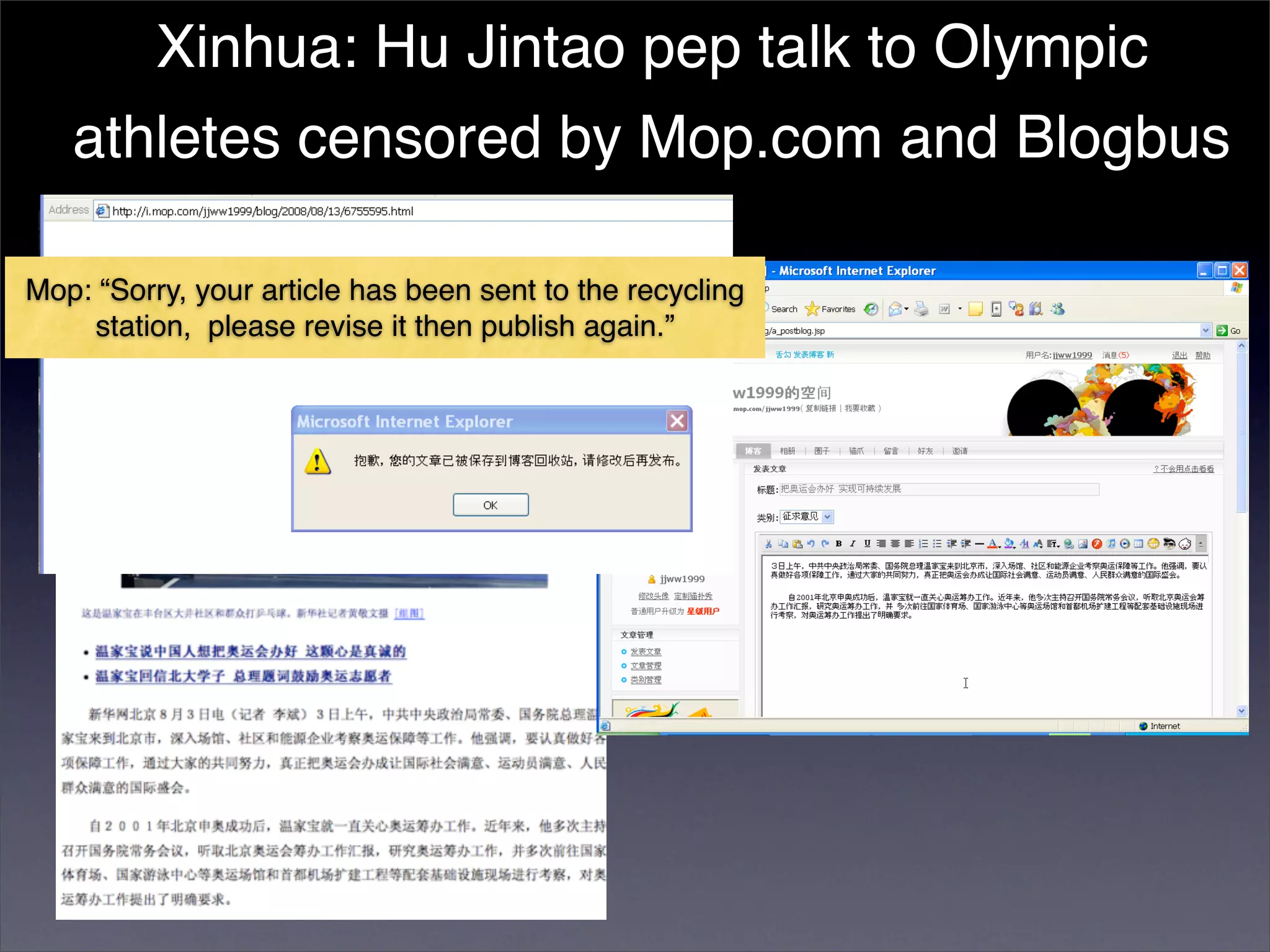
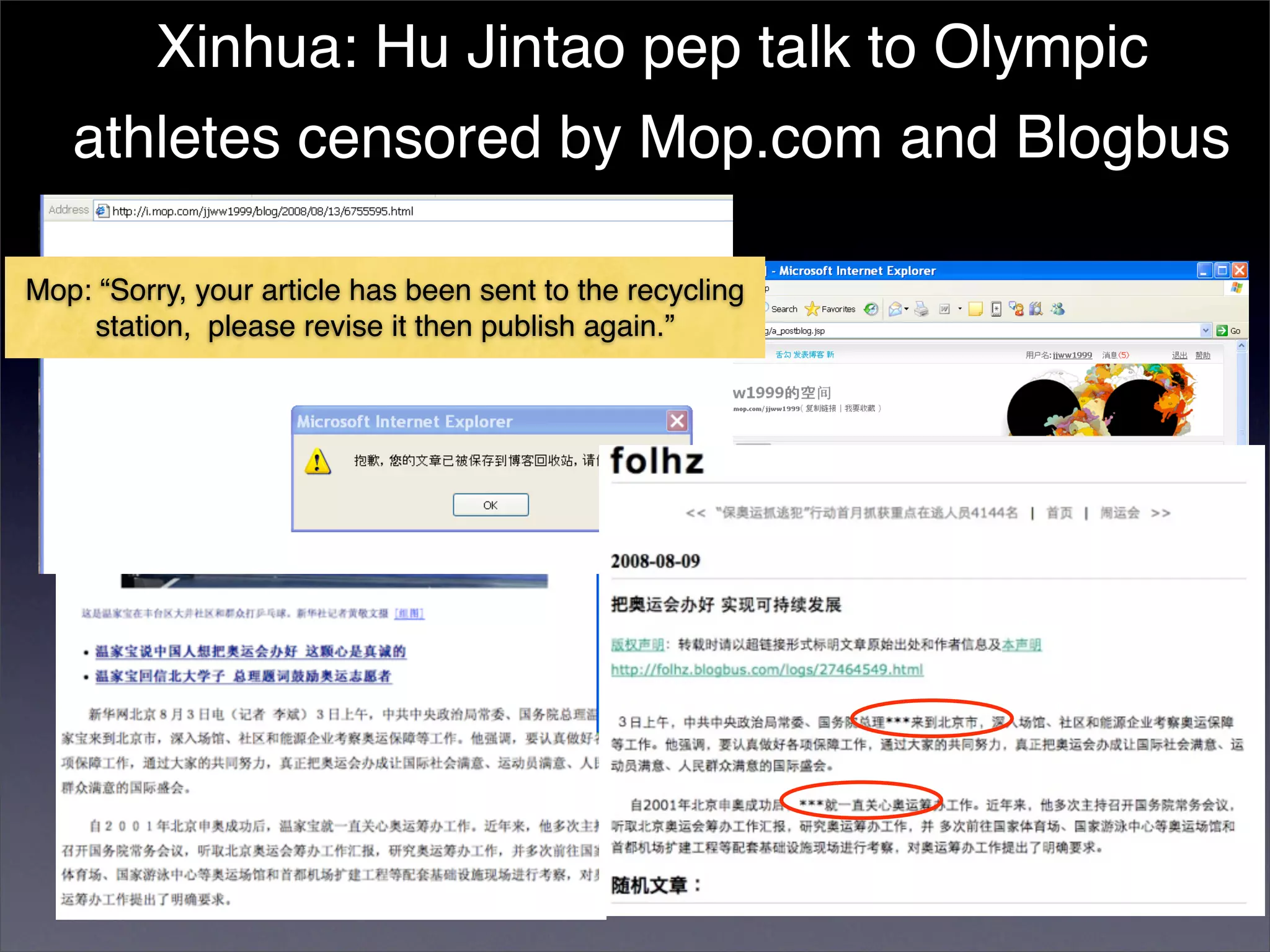




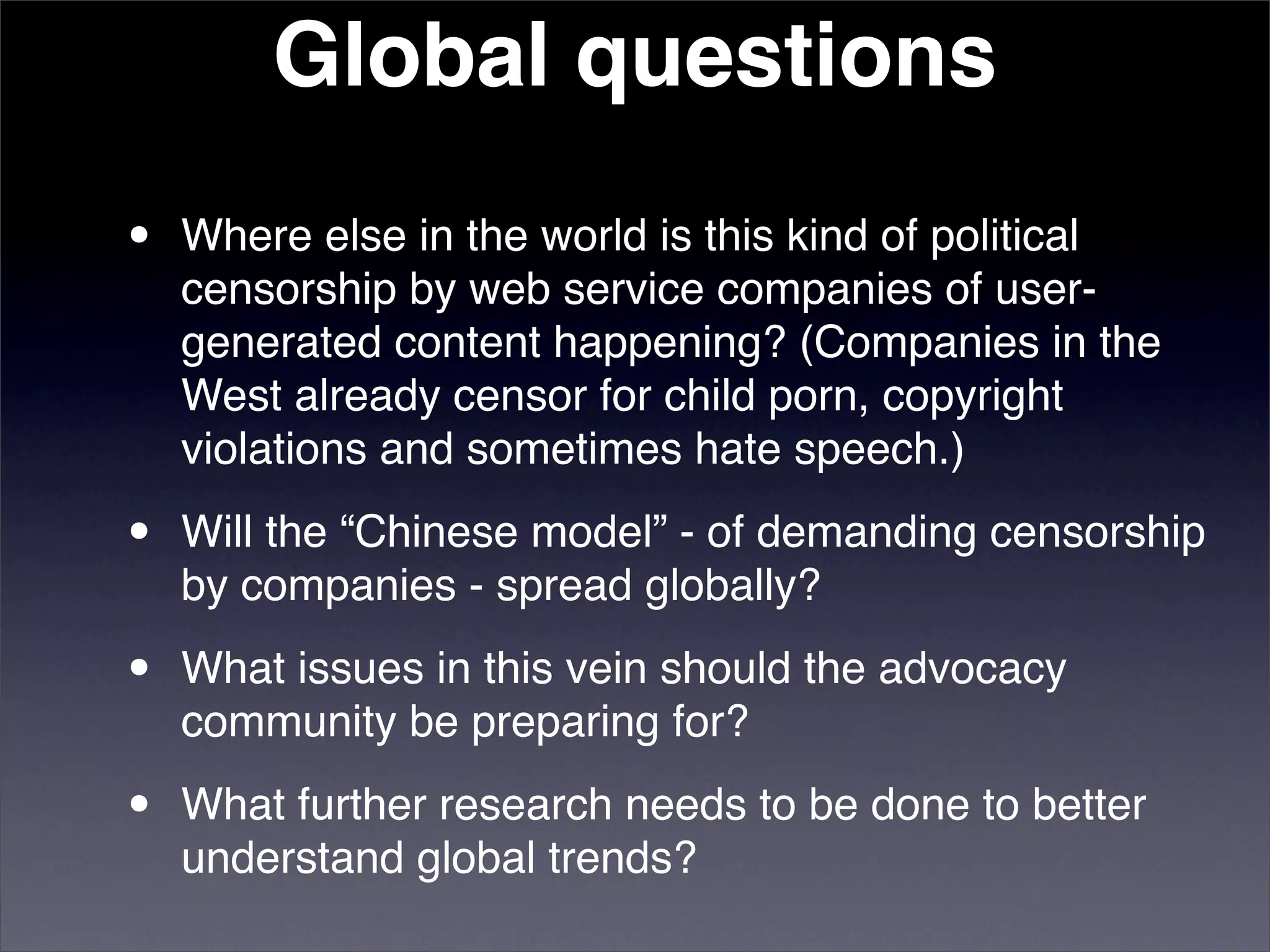

The document discusses two categories of internet censorship in China: filtering of external websites and deletion of content on domestic platforms. It highlights inconsistencies in censorship by various blog hosting companies and the influence of local government on their operations. Additionally, it calls for more extensive research into domestic web censorship and encourages strategies for activists to navigate and educate others on the complexities of information dissemination in China.




































