Embed presentation
Download to read offline

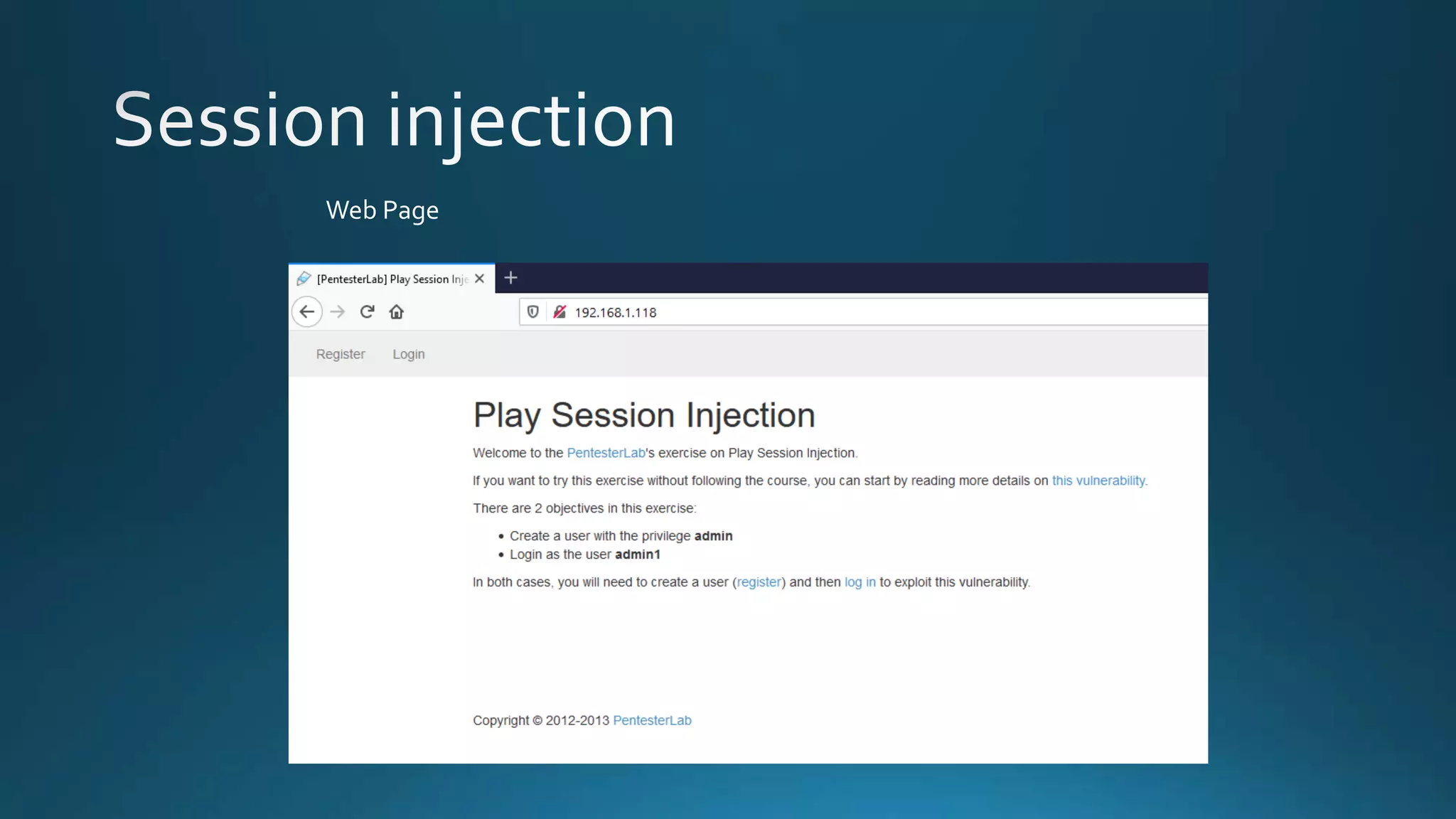



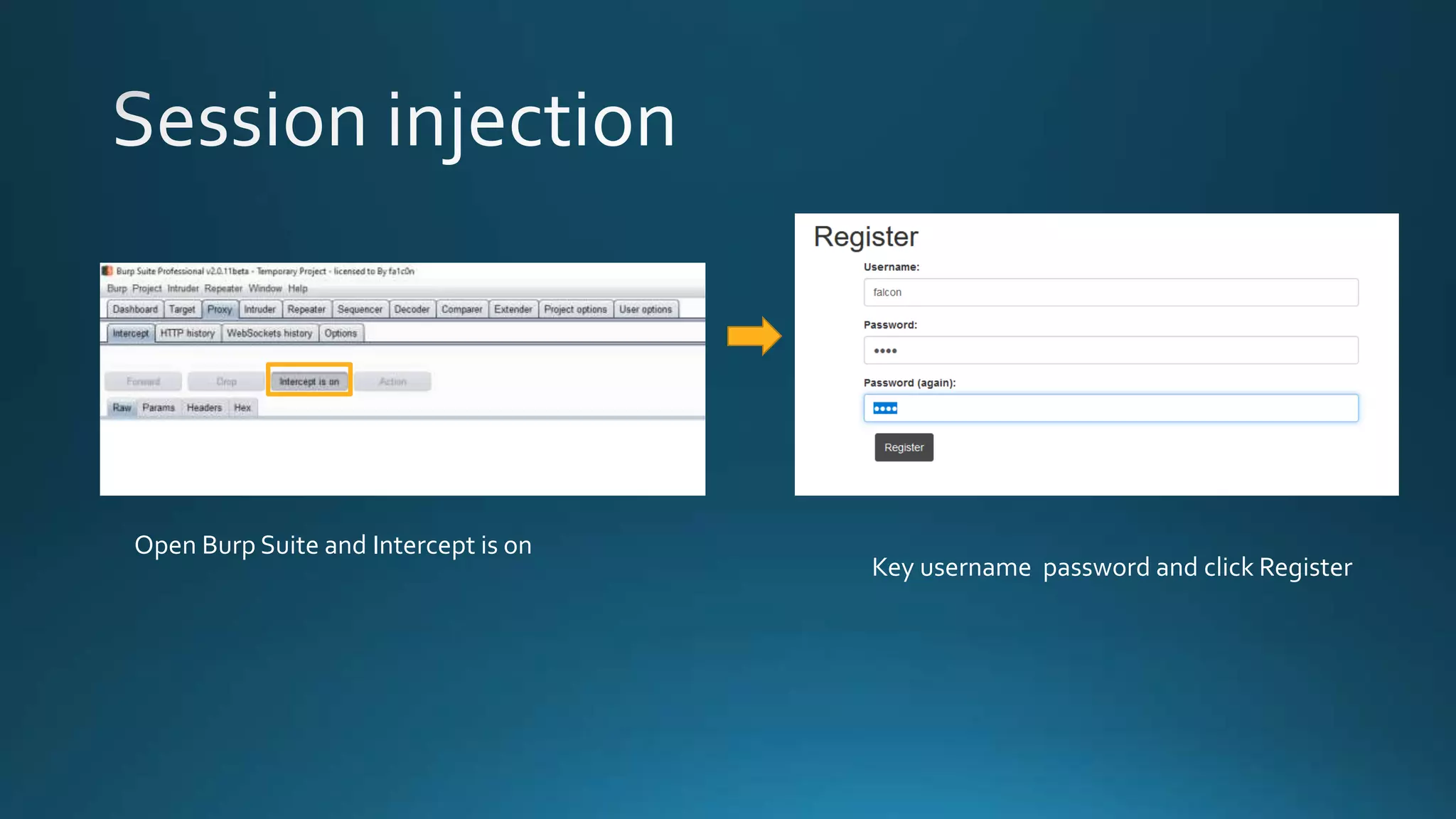

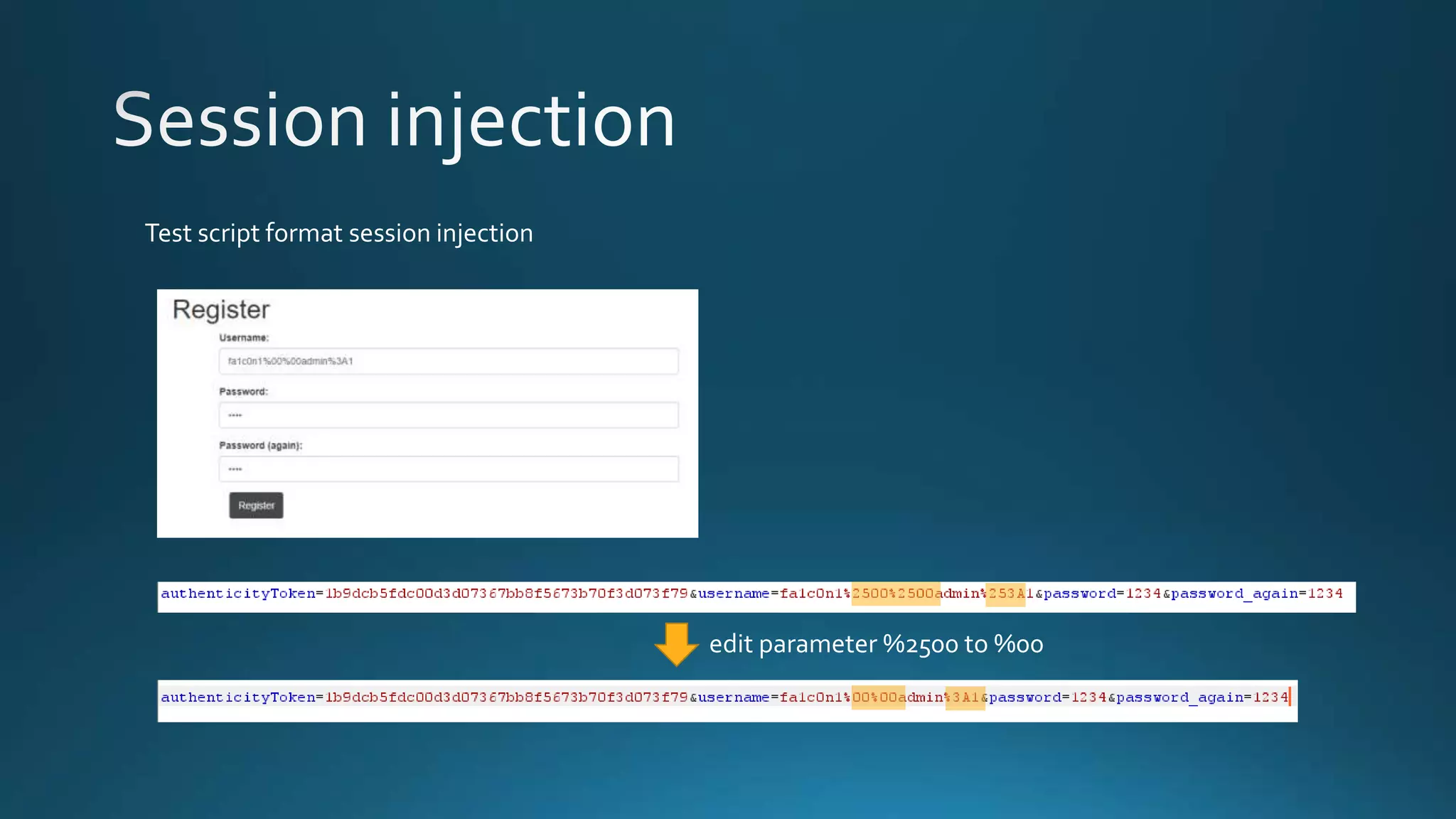










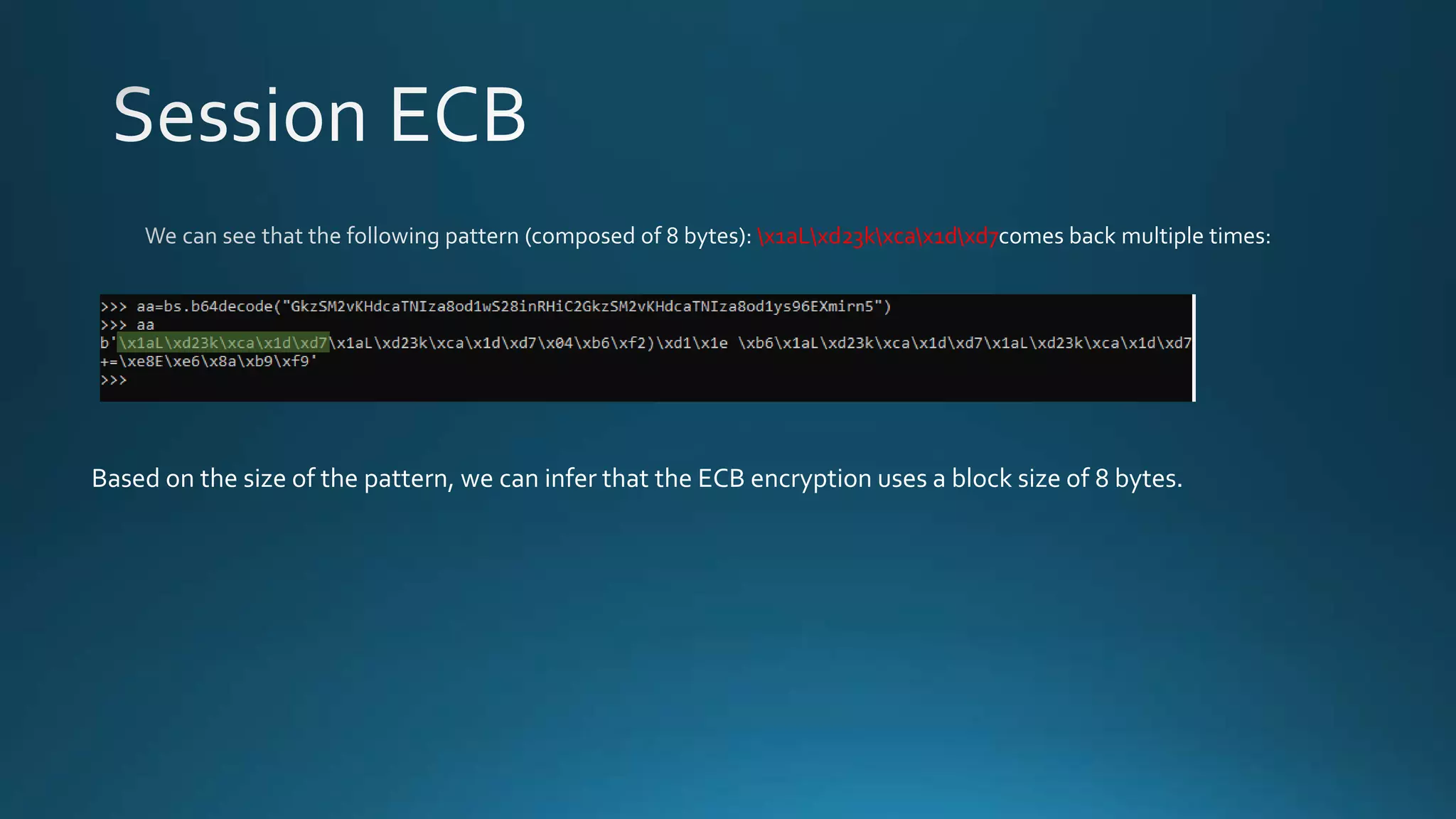





The document discusses detecting and decrypting an encrypted cookie value. It notes the cookie appears to be URI-encoded and base64-encoded. Decrypting the cookie reveals a repeating pattern indicating encryption with ECB cipher and 8-byte block size. By modifying the username and removing the first 8 bytes, a new encoded cookie value can be generated.























