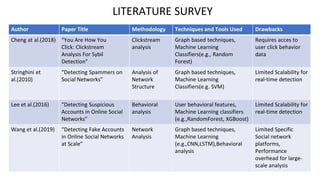
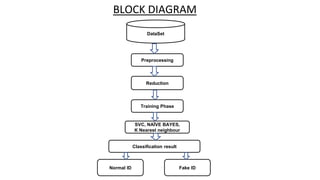
The document presents a project from Sri Venkateswara College focusing on using advanced machine learning methods to detect fake accounts and images on digital media. The proposed system enhances existing methodologies by integrating dynamic features, real-time detection, and improved classification models to address limitations such as data imbalance and privacy concerns. The ultimate goal is to bolster online trust and mitigate misinformation across various applications, including social media and cybersecurity.












![6. A.Rössler, D.Cozzolino, L.Verdoliva, C. Riess, J. Thies, and M. Niessner,
‘‘FaceForensics++:Learningtodetectmanipulatedfacialimages,’’inProc. IEEE/CVF Int. Conf. Comput. Vis.
(ICCV), Oct. 2019, pp. 1–11.
7. R. Rombach, A. Blattmann, D. Lorenz, P. Esser, and B. Ommer, ‘‘High-resolution image synthesis with latent
diffusion models,’’ in Proc. IEEE/CVF Conf. Com
8. N. Dufour, A. Gully, P. Karlsson, A. V. Vorbyov, T. Leung, J. Childs, and C. Bregler, ‘‘DeepFakes detection
dataset by Google & Jigsaw,’’ Google, USA, 2019. [Online]. Available: https://blog.research.google/
2019/09/contributing-data-to-deepfake-detection.html?m=1](https://image.slidesharecdn.com/b13firstreview21-240720131911-8ee86978/85/B13-FIRST-REVIEW-2-1-pdf-advanced-machine-learning-15-320.jpg)
