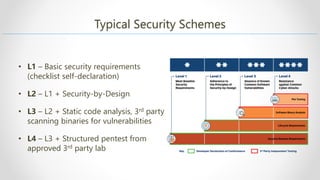
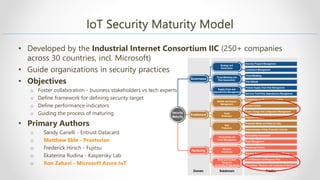
The document outlines a session on Azure security for developers, emphasizing that security goes beyond just tools and involves obtaining security certification through audits. It details a security maturity model developed by the Industrial Internet Consortium, along with Azure Security Benchmark guidelines for improving the security of workloads and services on Azure. Additionally, it provides resources and links for further exploration of security practices and frameworks in the context of Azure.