Attachments
•Download as DOCX, PDF•
0 likes•130 views
E-mail attachments allow files like documents and images to be sent along with an e-mail message, providing a simple way to share files privately with recipients. While attachments are useful for sharing important files, they can pose security risks and privacy issues depending on the file type. Common file formats vary in their editability, compatibility across platforms, security, size, and whether they require proprietary software, with plain text and PDF generally being more secure and free options.
Report
Share
Report
Share
Recommended
Business Formatting

Tutorial on the different types of workplace documents and how to format them properly!
A Call to Patents

A Call to Patents:
A look at the current state of patents held by social media and technological companies.
The intellectual property of social media businesses has seen a rise in the acquisition of patents. For such a fast growing industry, will this “arming” of corporate enterprises and the verdict of one monstrous case determine what could be a legal onslaught within the technological industry?
Recommended
Business Formatting

Tutorial on the different types of workplace documents and how to format them properly!
A Call to Patents

A Call to Patents:
A look at the current state of patents held by social media and technological companies.
The intellectual property of social media businesses has seen a rise in the acquisition of patents. For such a fast growing industry, will this “arming” of corporate enterprises and the verdict of one monstrous case determine what could be a legal onslaught within the technological industry?
Financial Results Icons for PowerPoint

Source http://www.poweredtemplate.com/powerpoint-diagrams-charts/ppt-powerpoint-icons/00141/0/index.html
Open nebula froscon

Slides from the OpenNebula presentation at FrOSCon 2012, 25th August 2012. Sankt Augustin, Germany
Sametime Introduction

An overview of the different products under the Sametime brand, including Sametime Limited, Sametime Entry, Sametime Standard, Sametime Advanced, Sametime Unified Telephony (SUT), Sametime Meetings (now Lotus Live Meetings)
Tackling the inappropriate use of psycho-active medication in Scotland

Dr Stella Clark, Medical Director,
Primary Care, NHS Fife; Clinical lead for Mental Health Services, NHS 24
Presentation from Alzheimer Scotland conference 2011 - Creating Better Dementia Care.
More Related Content
Viewers also liked
Financial Results Icons for PowerPoint

Source http://www.poweredtemplate.com/powerpoint-diagrams-charts/ppt-powerpoint-icons/00141/0/index.html
Open nebula froscon

Slides from the OpenNebula presentation at FrOSCon 2012, 25th August 2012. Sankt Augustin, Germany
Sametime Introduction

An overview of the different products under the Sametime brand, including Sametime Limited, Sametime Entry, Sametime Standard, Sametime Advanced, Sametime Unified Telephony (SUT), Sametime Meetings (now Lotus Live Meetings)
Tackling the inappropriate use of psycho-active medication in Scotland

Dr Stella Clark, Medical Director,
Primary Care, NHS Fife; Clinical lead for Mental Health Services, NHS 24
Presentation from Alzheimer Scotland conference 2011 - Creating Better Dementia Care.
Viewers also liked (16)
Tackling the inappropriate use of psycho-active medication in Scotland

Tackling the inappropriate use of psycho-active medication in Scotland
Similar to Attachments
Electronic mail

this is very good and easy to understand the basic things about electronic mail or simply e-mail. You can see the definition of e-mail, features and format of e-mail, email address and mail user agent and its sources.
Similar to Attachments (8)
EMP_3rd_Quarter_Week_4_Module_on_Developing_ICT_using_MS_Word.pdf

EMP_3rd_Quarter_Week_4_Module_on_Developing_ICT_using_MS_Word.pdf
More from Abraham Bautista (12)
Attachments
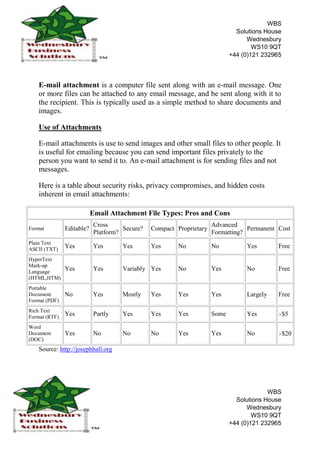
- 1. -6000757334885-409575-1418590<br />E-mail attachment is a computer file sent along with an e-mail message. One or more files can be attached to any email message, and be sent along with it to the recipient. This is typically used as a simple method to share documents and images. <br />Use of Attachments<br />E-mail attachments is use to send images and other small files to other people. It is useful for emailing because you can send important files privately to the person you want to send it to. An e-mail attachment is for sending files and not messages.<br />Here is a table about security risks, privacy compromises, and hidden costs inherent in email attachments:<br />Email Attachment File Types: Pros and ConsFormatEditable?Cross Platform?Secure?CompactProprietaryAdvanced Formatting?PermanentCostPlain Text ASCII (TXT)YesYesYesYesNoNoYesFreeHyperText Mark-up Language (HTML,HTM)YesYesVariably YesNoYesNoFreePortable Document Format (PDF)NoYesMostlyYesYesYesLargelyFreeRich Text Format (RTF)YesPartlyYesYesYesSomeYes>$5Word Document (DOC)YesNoNoNoYesYesNo>$20<br />Source: http://josephhall.org<br />