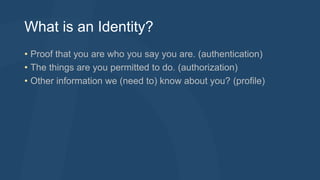
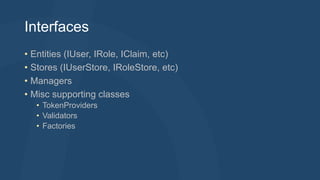
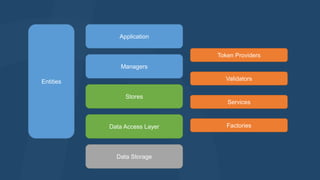
The document discusses the history and goals of identity management in ASP.NET. It describes earlier approaches like ASP.NET providers which were dependent on SQL Server and difficult to extend. The current ASP.NET Identity 2.1 aims to be usable across ASP.NET, easily extensible, persistence agnostic, testable, and support roles, claims and third-party authentication. It has interfaces, stores, managers and other classes to manage user identities and authentication in a modular way.