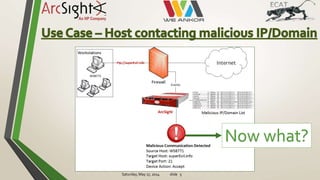
The document discusses the need to quickly investigate security alerts from across a network. It proposes automatically deploying agents across systems to scan for suspicious modules in real time. This would allow starting investigations within seconds of an alert, collecting evidence from any host, and getting actionable data to respond. The system would then automatically detect and react to potentially infected modules.